-
Notifications
You must be signed in to change notification settings - Fork 164
How To Create an App Control Supplemental Policy
Base policies that have the Enabled:Allow Supplemental Policies rule option can be extended with supplemental policies. Supplemental policies can be used to expand the scope of a base policy without modifying the base policy itself. This allows you to create a base policy that is shared across multiple devices and then create supplemental policies that are specific to individual devices or groups of devices.
You can have as many supplemental policies as you need, but each supplemental policy can only be associated with one base policy.
Tip
How to differentiate between base and supplemental policies:
The values of PolicyID and BasePolicyID fields in a base policy are the same, but in a supplemental policy, the BasePolicyID field contains the PolicyID of the base policy it is associated with.
There are other signs that indicate if a policy is a base or supplemental policy. A supplemental policy can only contain allow rules. A supplemental policy can only have a subset of the rule options.
Use the System Information page in the AppControl Manager to view all of the deployed policies and see which ones are base or supplemental.
When it comes to signing, if the base policy is signed, then the supplemental policy must be signed too and vise versa.
Assuming you've already deployed a base policy, you can create a supplemental policy by navigating to the Create Supplemental Policy Page.
In the Files and Folders section, browse for your base policy's XML file. Enter a descriptive name for the supplemental policy that will be created and browse for files and/or folder to scan. If you select folders, they will be scanned recursively, meaning any file in the sub-folders will also be included in the scan.
The default level is set to File Publisher but you can change it to another level that meets your needs.
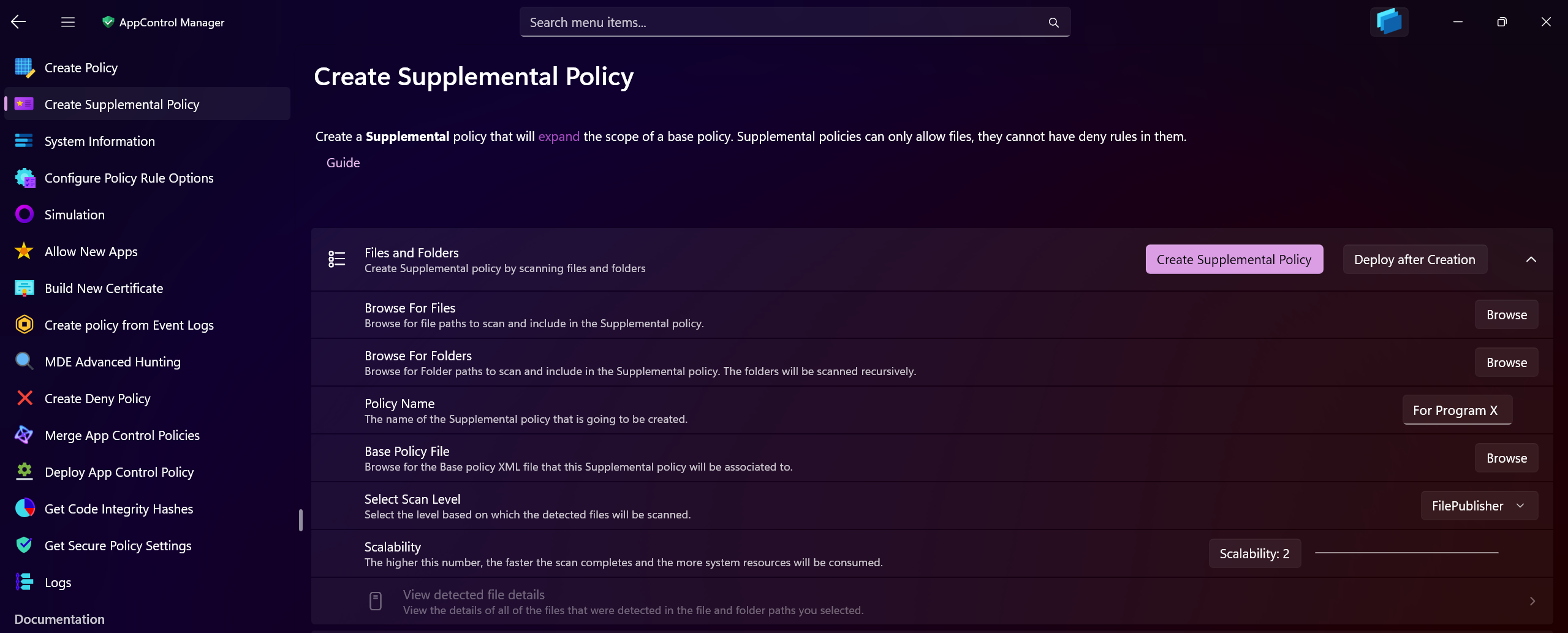
After you've submitted the necessary details, press the Create Supplemental Policy button. The scan will begin and you will be able to view the progress in real time. If you toggle the Deploy After Creation button, the policy will be automatically deployed on the local system, otherwise the XML file will just be created.
You can customize the XML file further using different pages and features of the AppControl Manager.
Q: What happens if you create a supplemental policy with the same name as an existing one?
A: Although not recommended as it will make it hard to differentiate between the two in System Information, you can create a supplemental policy with the same name as an existing one. It won't overwrite the existing one as they will still have different PolicyIDs.
Q: What if you create a supplemental policy for an app and then that app is updated?
A: It all depends on the level you selected for the supplemental policy. If you selected File Publisher or Publisher, then the policy will still apply to the updated app as long as it is signed by the same publisher. If you selected Hash, then the policy will no longer apply to the updated app as the binaries are changed. You will have to scan the new binaries and create a new supplemental policy for them and preferably remove the old one.
- Create AppControl Policy
- Create Supplemental Policy
- System Information
- Configure Policy Rule Options
- Simulation
- Allow New Apps
- Build New Certificate
- Create Policy From Event Logs
- Create Policy From MDE Advanced Hunting
- Create Deny Policy
- Merge App Control Policies
- Deploy App Control Policy
- Get Code Integrity Hashes
- Get Secure Policy Settings
- Update
- Sidebar
- Introduction
- How To Generate Audit Logs via App Control Policies
- How To Create an App Control Supplemental Policy
- The Strength of Signed App Control Policies
- App Control Notes
- How to use Windows Server to Create App Control Code Signing Certificate
- Fast and Automatic Microsoft Recommended Driver Block Rules updates
- App Control policy for BYOVD Kernel mode only protection
- EKUs in App Control for Business Policies
- App Control Rule Levels Comparison and Guide
- Script Enforcement and PowerShell Constrained Language Mode in App Control Policies
- How to Use Microsoft Defender for Endpoint Advanced Hunting With App Control
- App Control Frequently Asked Questions (FAQs)
- Create Bootable USB flash drive with no 3rd party tools
- Event Viewer
- Group Policy
- How to compact your OS and free up extra space
- Hyper V
- Overrides for Microsoft Security Baseline
- Git GitHub Desktop and Mandatory ASLR
- Signed and Verified commits with GitHub desktop
- About TLS, DNS, Encryption and OPSEC concepts
- Things to do when clean installing Windows
- Comparison of security benchmarks
- BitLocker, TPM and Pluton | What Are They and How Do They Work
- How to Detect Changes in User and Local Machine Certificate Stores in Real Time Using PowerShell
- Cloning Personal and Enterprise Repositories Using GitHub Desktop
- Only a Small Portion of The Windows OS Security Apparatus
- Rethinking Trust: Advanced Security Measures for High‐Stakes Systems
- Clean Source principle, Azure and Privileged Access Workstations
- How to Securely Connect to Azure VMs and Use RDP
- Basic PowerShell tricks and notes
- Basic PowerShell tricks and notes Part 2
- Basic PowerShell tricks and notes Part 3
- Basic PowerShell tricks and notes Part 4
- Basic PowerShell tricks and notes Part 5
- How To Access All Stream Outputs From Thread Jobs In PowerShell In Real Time
- PowerShell Best Practices To Follow When Coding
- How To Asynchronously Access All Stream Outputs From Background Jobs In PowerShell
- Powershell Dynamic Parameters and How to Add Them to the Get‐Help Syntax
- RunSpaces In PowerShell
- How To Use Reflection And Prevent Using Internal & Private C# Methods in PowerShell
