-
Notifications
You must be signed in to change notification settings - Fork 163
Create App Control Policy
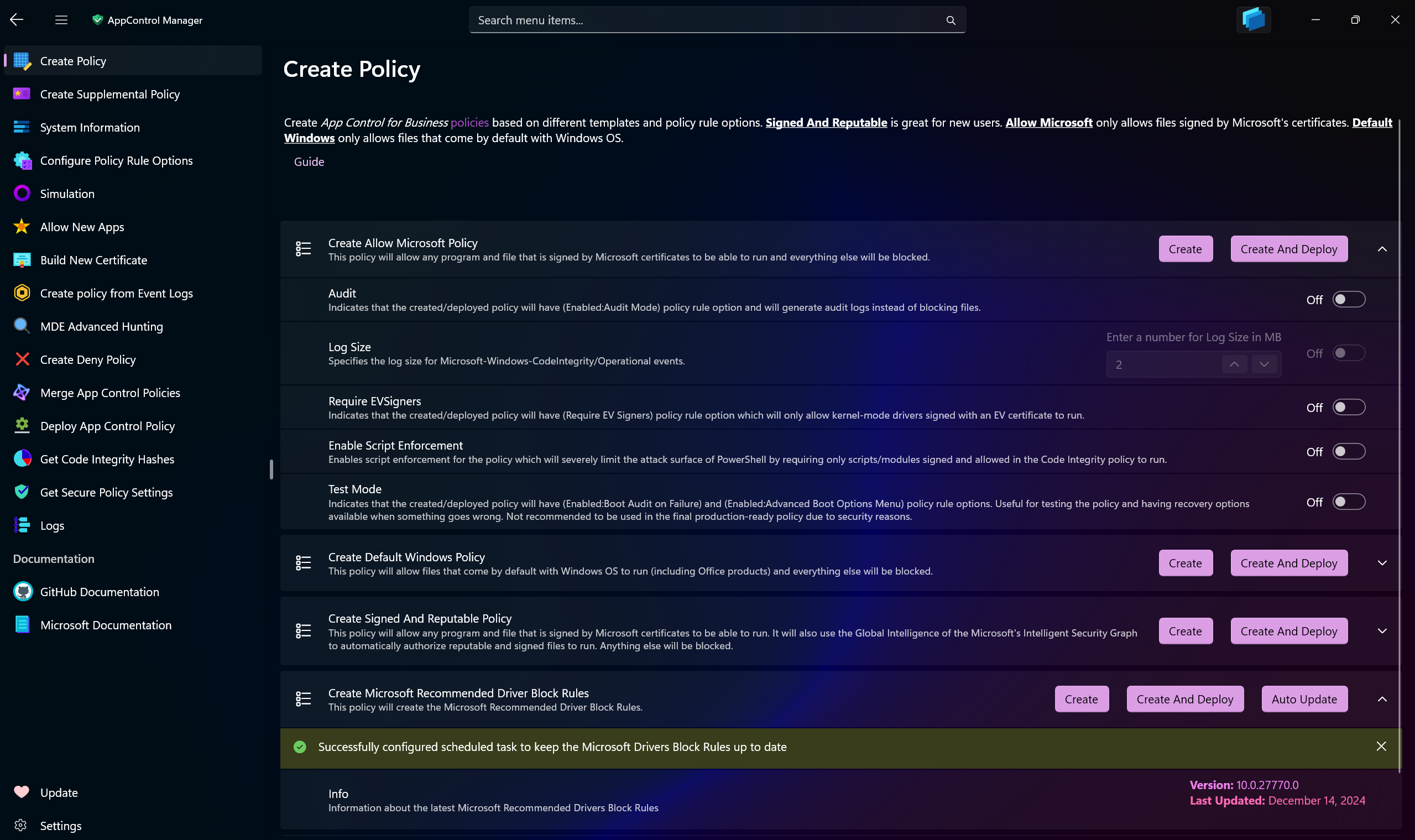
Use AppControl Manager to create new App Control policies based on the default templates.
-
Allow Microsoft: Only allows files signed by Microsoft certificates to run on the system.
-
Default Windows: Only allows files that come by default with Windows OS to run on the system.
-
Signed And Reputable: Allows files signed by Microsoft certificates to run, it also utilizes the Intelligent Security Graph to allow files that are reputable and safe.
-
Microsoft Recommended Block Rules: It will download the latest Microsoft Recommended (User-Mode) block rules from the official source and create an App Control policy.
-
Microsoft Recommended Driver Block Rules: It will download the latest Microsoft Recommended (Kernel-Mode) block rules from the official source and create an App Control policy.
- Auto update: It will create a scheduled task on the system that will check every week for the latest Microsoft Recommended block rules and update the policy automatically. Please refer to this page for more info.
Deploying any of them is optional. You can create the policies and then deploying them on remote systems using Intune or other methods.
There are different settings and options you can use to fine tune the policy according to your requirements.
-
Audit: When a policy has Audit mode turned on for it, it will only log the events and not block any files from running.
-
Log Size: You can configure the max capacity of the
Code Integrity/Operationallog size. It is recommended to increase it from the default1MBcapacity if you want to begin auditing for App Control events. When the capacity is reached, the log will overwrite the oldest events. -
Require EVSigners: When this setting is enabled, the policy will only allow files signed by Extended Validation (EV) certificates to run on the system.
-
Enable Script Enforcement: When this setting is enabled, the policy will only allow PowerShell scripts or modules that are signed and their signing certificates are allowed in an App Control policy to run. This greatly reduces the attack surface from the Windows script hosts.
-
Test Mode: Boot Options Menu, such as Safe mode, is disabled for all App Control policies by default. Using Test Mode will allow access to it. It will also automatically enable the
Auditmode for the policy in case of a failure in a driver that is critical to system boot. It's only recommended to use this setting in a test environment and not in production due to security reasons.
- Create AppControl Policy
- Create Supplemental Policy
- System Information
- Configure Policy Rule Options
- Simulation
- Allow New Apps
- Build New Certificate
- Create Policy From Event Logs
- Create Policy From MDE Advanced Hunting
- Create Deny Policy
- Merge App Control Policies
- Deploy App Control Policy
- Get Code Integrity Hashes
- Get Secure Policy Settings
- Update
- Sidebar
- Introduction
- App Control for Lightly Managed Devices
- App Control for Fully managed device - Variant 1
- App Control for Fully managed device - Variant 2
- App Control for Fully managed device - Variant 3
- App Control for Fully managed device - Variant 4
- App Control Notes
- How to Create and Deploy a Signed App Control Policy
- Fast and Automatic Microsoft Recommended Driver Block Rules updates
- App Control policy for BYOVD Kernel mode only protection
- EKUs in App Control for Business Policies
- App Control Rule Levels Comparison and Guide
- Script Enforcement and PowerShell Constrained Language Mode in App Control Policies
- How to Use Microsoft Defender for Endpoint Advanced Hunting With App Control
- App Control Frequently Asked Questions (FAQs)
- Create Bootable USB flash drive with no 3rd party tools
- Event Viewer
- Group Policy
- How to compact your OS and free up extra space
- Hyper V
- Overrides for Microsoft Security Baseline
- Git GitHub Desktop and Mandatory ASLR
- Signed and Verified commits with GitHub desktop
- About TLS, DNS, Encryption and OPSEC concepts
- Things to do when clean installing Windows
- Comparison of security benchmarks
- BitLocker, TPM and Pluton | What Are They and How Do They Work
- How to Detect Changes in User and Local Machine Certificate Stores in Real Time Using PowerShell
- Cloning Personal and Enterprise Repositories Using GitHub Desktop
- Only a Small Portion of The Windows OS Security Apparatus
- Rethinking Trust: Advanced Security Measures for High‐Stakes Systems
- Clean Source principle, Azure and Privileged Access Workstations
- How to Securely Connect to Azure VMs and Use RDP
- Basic PowerShell tricks and notes
- Basic PowerShell tricks and notes Part 2
- Basic PowerShell tricks and notes Part 3
- Basic PowerShell tricks and notes Part 4
- Basic PowerShell tricks and notes Part 5
- How To Access All Stream Outputs From Thread Jobs In PowerShell In Real Time
- PowerShell Best Practices To Follow When Coding
- How To Asynchronously Access All Stream Outputs From Background Jobs In PowerShell
- Powershell Dynamic Parameters and How to Add Them to the Get‐Help Syntax
- RunSpaces In PowerShell
- How To Use Reflection And Prevent Using Internal & Private C# Methods in PowerShell
