-
-
Notifications
You must be signed in to change notification settings - Fork 402
FS_Process_VMemD
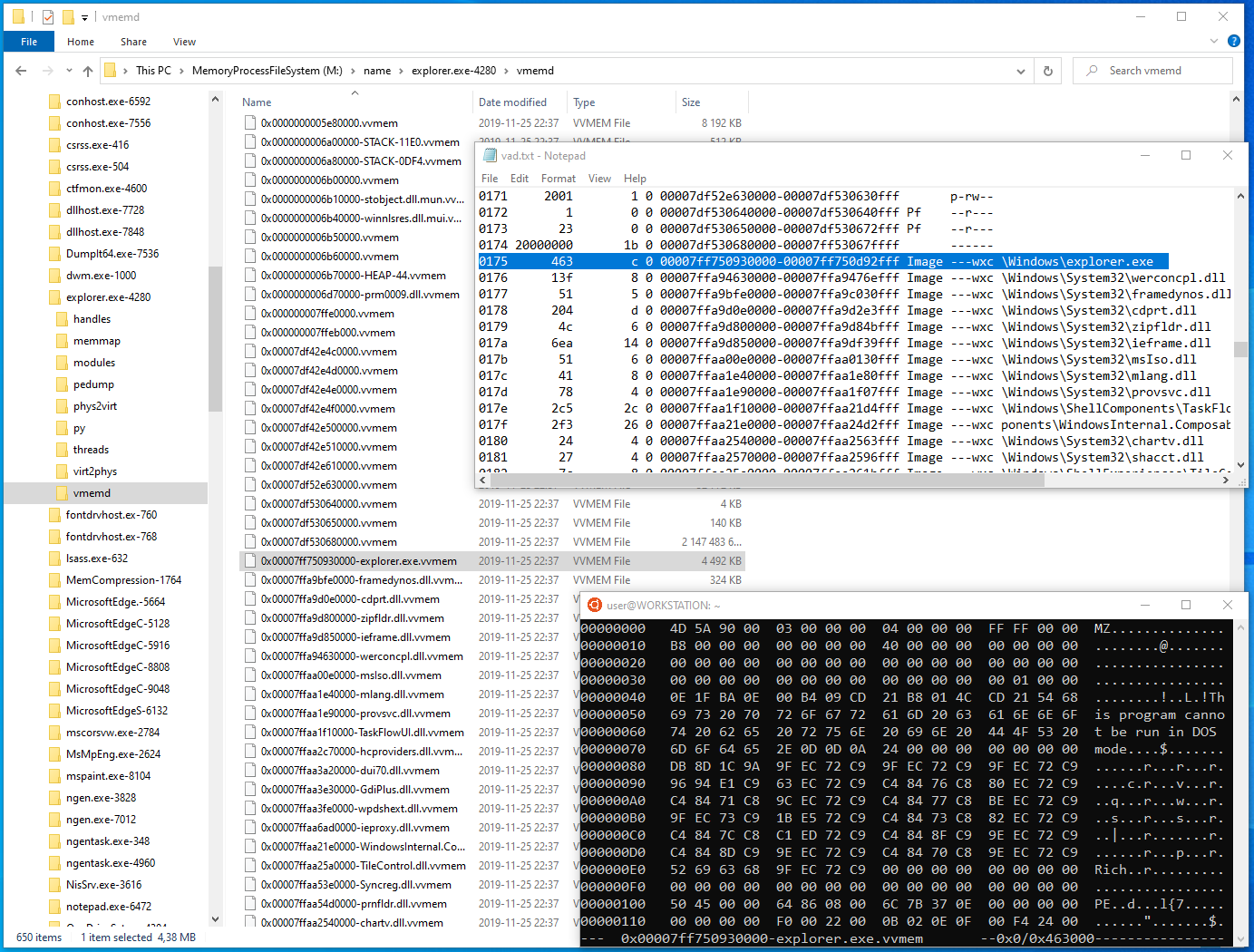
The directory vmemd exists as a sub-directory in each process directory.
The directory contains files of virtual memory according to the process memory map. Each file maps towards a memory map entry. Primarily entries from the virtual address descriptor (VAD) memory map are used. If a memory entry exists in the hardware page table map (PTE) but not in the VAD memory map it will also be displayed.
A file may consist of one or more contiguous virtual memory pages. Please note that often not all pages are allocated towards physical pages. They may also be unmapped, mapped towards a page file or mapped towards compressed virtual memory. If a page is unreadable it will be zero padded.
The Memory Process File System will use tag information in the memory map, such as module/.dll name, and include it in file names should such information exist.
The files in the vmemd directory does not allow read/write past the end of file even if virtual memory with different page permissions should exist contiguously in virtual memory after the end of the file.
Files are writable if a write-capable memory acquisition device is used.
The example below shows hex editing of the file 0x00007ff750930000-explorer.exe.vvmem - when looking at the process memory map file the hex edited file maps perfectly towards the virtual memory page containing the PE(MZ) header of the cmd.exe module in the cmd.exe process.
The vmemd sub-directory is implemented as a separate native C-code plugin. The plugin m_vmemd.dll is located in the plugins directory that exists as a sub-directory to the directory of MemProcFS.exe. Well documented source code exists in the m_vmemd project in the Visual Studio solution.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖