-
-
Notifications
You must be signed in to change notification settings - Fork 402
FS_Forensic_Timeline
The directory forensic/timeline exists as a sub-directory to the file system root.
The directory is hidden by default. It will appear once forensic mode has been started and processing is completed.
The directory contains various system artifacts ordered by time stamp in timelines. Currently timelines are shown in text format. A JSON data format is planned for the future but not yet implemented.
The files in the forensic/timeline directory are listed in the table below:
| File | Description |
|---|---|
| timeline/timeline_all.txt | All timelining information bundled into a single file. |
| timeline/timeline_net.txt | Network connection timeline. |
| timeline/timeline_ntfs.txt | NTFS MFT timeline. |
| timeline/timeline_process.txt | Process timeline. |
| timeline/timeline_registry.txt | Registry timeline. |
| timeline/timeline_thread.txt | Thread timeline. |
| timeline/timeline_[...].txt | Additional timelines generated by plugins. |
Files in the forensic/timeline directory are read-only.
The timeline have the following format:
DATE TYPE ACTION PID NUM HEX DESC
======================= ==== ====== ==== ==== ================ =================================
2019-03-29 15:42:08 UTC PROC DEL 4376 540 ffffcf00cbad7080 backgroundTask [*] backgroundTask
2019-03-29 15:40:38 UTC PROC CRE 5968 48 ffffcf00cec0e080 svchost.exe [*LOCAL SERVICE] \Device\HarddiskVolume2\Windows\System32\svchost.exe
2019-03-29 15:40:38 UTC PROC CRE 4376 540 ffffcf00cbad7080 backgroundTask [*] backgroundTask
The column ACTION may take the following values: CRE = Create/Start, MOD = Modify, RD = Read, DEL = Delete/Stop.
The columns NUM, HEX and DESC have different meaning depending on the type. A few examples are listed in the table below:
| Type | NUM | HEX |
|---|---|---|
| KObj | Object address | |
| Net | Object address | |
| NTFS | File size | MFT record physical address |
| PROC | Parent PID | EPROCESS address |
| THREAD | TID (Thread ID) | ETHREAD address |
The example shows the timeline directory containing timelines. The process timeline is open in notepad and the combined all timeline is open in notepad++.
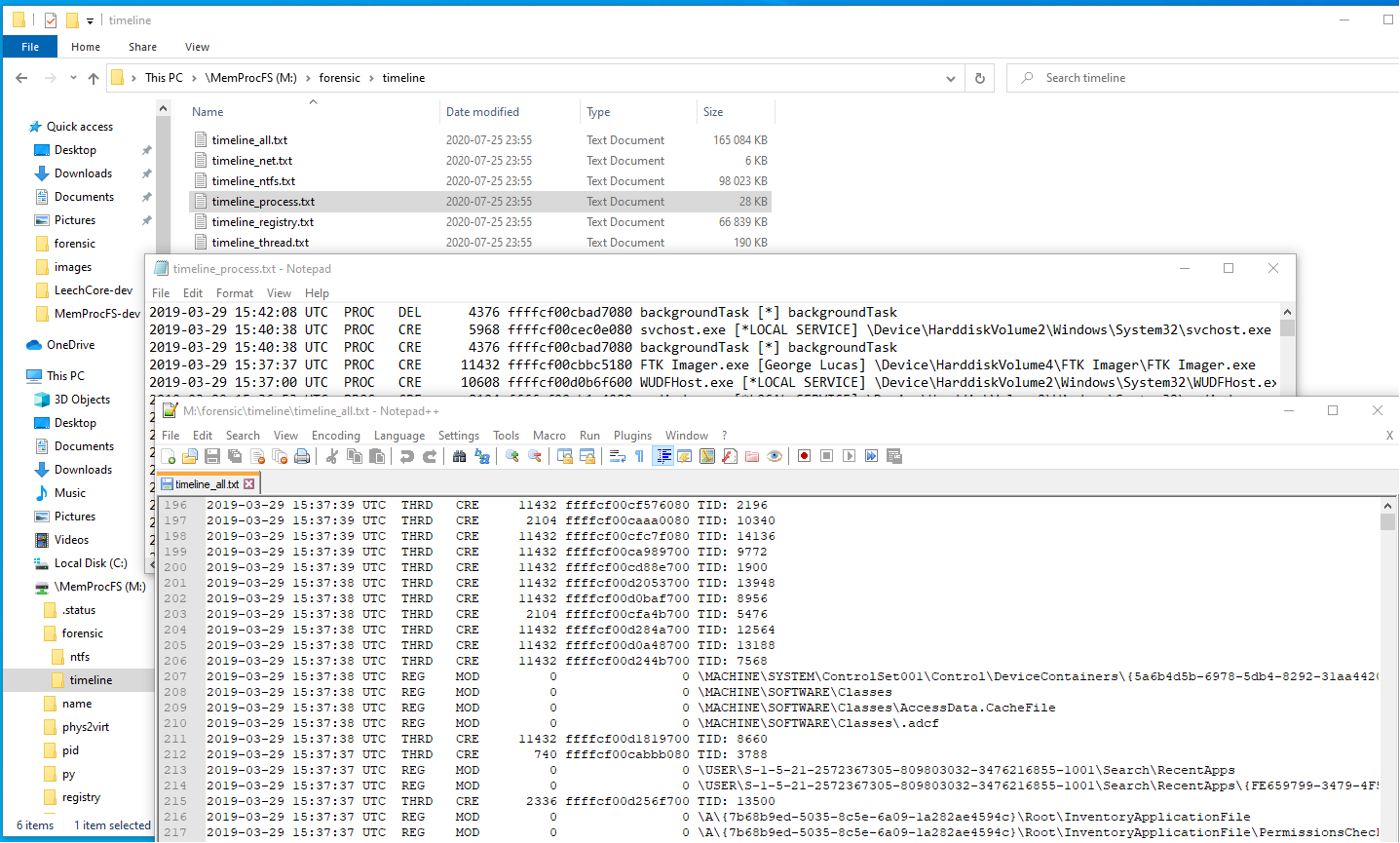
The forensic/timeline sub-directory is implemented as a built-in native C-code plugin. The plugin source is located in the file modules/m_fc_timeline.c in the vmm project. It's possible for plugins to generate a timeline of their own by implementing the pfnTimeline callback function. An example of such a plugin is the networking plugin found in m_sysinfo_net.c in the vmm project.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖