-
-
Notifications
You must be signed in to change notification settings - Fork 404
FS_Forensic_Ntfs
The directory forensic/ntfs exists as a sub-directory to the file system root.
The directory is hidden by default. It will appear once forensic mode has been started and processing is completed.
The directory contains a best-efford reconstructed file system reconstructed from NTFS MFT entries located in physical memory. If the files are small enough contents may reside within the NTFS MFT and may be recoverable by opening the file.
The file ntfs_files.txt contains a complete record of the recovered NTFS MFT enties and their path. It's also possible to view the recovered files by clicking around in the sub-folders. Please note that the reconstruction is a best-efford reconstruction and may contain errors as well as missing files and folders.
Each folder contains a special meta-data folder named _$INFO. The _$INFO folder contains a directory populated with metadata information about the NTFS MFT record. The metadata files are:
| File | Description |
|---|---|
| mftinfo.txt | Information in easy-to-read format about the MFT entry. |
| mftdata.mem | The 1024 byte long MFT record. |
| mftfile.bin | The file representation, if file and data recoverable. |
The file ntfs_files.txt have the following format:
# PHYS_ADDR RECID TIME_CREATE TIME_MODIFY SIZE AVAIL DIR PATH
====== ========= ===== ================================================= ==== ===== === ============
21348 4273f4000 1e3d4 2018-10-11 13:50:41 UTC : 2019-03-29 15:37:47 UTC 0 0 D \.\Windows\Prefetch
21349 5c916800 5bf76 2019-03-29 14:43:19 UTC : 2019-03-29 14:43:19 UTC 0 0 \.\Windows\Prefetch\WMIADAP.EXE-F8DFDFA2.pf
2134a 411e0400 1cf5 2019-03-29 10:08:11 UTC : 2019-03-29 15:25:48 UTC 0 0 \.\Windows\Prefetch\SVCHOST.EXE-F78C68D4.pf
...
3ddae 1e9966000 128a4 2019-01-16 13:43:50 UTC : 2019-01-16 13:43:50 UTC 15b 15b \ORPHAN\AckPacket.java
3ddaf 1e9966400 128a5 2019-01-16 13:43:50 UTC : 2019-01-16 13:43:50 UTC 0 0 D \ORPHAN\csi
3ddb0 1e9966800 128a6 2019-01-16 13:43:50 UTC : 2019-01-16 13:43:50 UTC 103 103 \ORPHAN\csi\InactivePacket.java
Files in the forensic/ntfs directory and its sub-directories are read-only.
The example shows browsing of the user desktop folder, as well as listings of the files in the file ntfs_files.txt.
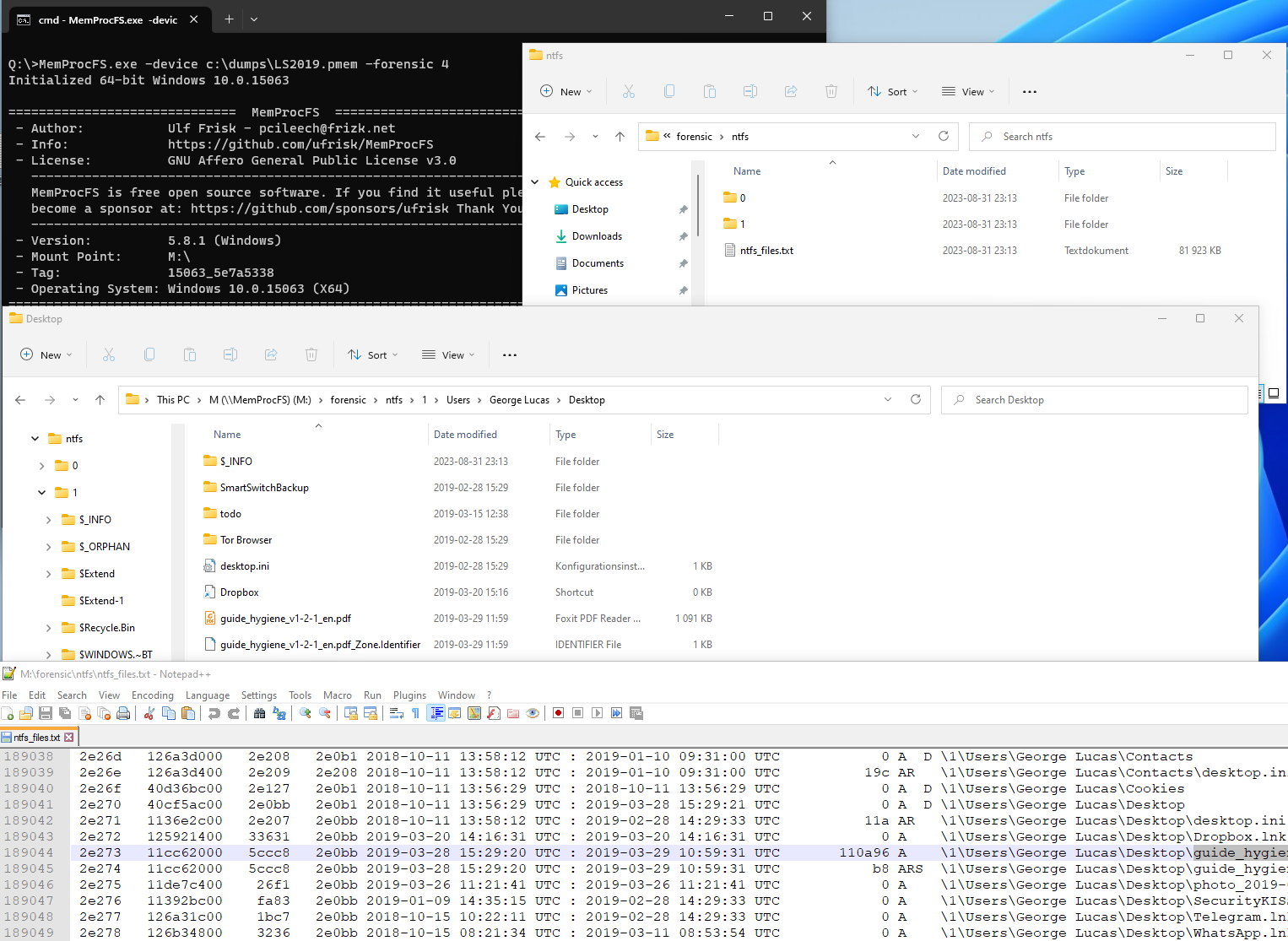
The forensic/ntfs sub-directory is implemented as a built-in native C-code plugin. The plugin source is located in the file m_fc_ntfs.c in the vmm project.
Sponsor PCILeech and MemProcFS:
PCILeech and MemProcFS is free and open source!
I put a lot of time and energy into PCILeech and MemProcFS and related research to make this happen. Some aspects of the projects relate to hardware and I put quite some money into my projects and related research. If you think PCILeech and/or MemProcFS are awesome tools and/or if you had a use for them it's now possible to contribute by becoming a sponsor!
If you like what I've created with PCIleech and MemProcFS with regards to DMA, Memory Analysis and Memory Forensics and would like to give something back to support future development please consider becoming a sponsor at: https://github.com/sponsors/ufrisk
Thank You 💖