❤️💕💕CS自学指南,大学教育无论是深度还是广度都没有办法支撑我们的职业素养,这个板块算是自己在CS学习中额外补充和记录的。个人博客:http://nsddd.top
[TOC]
💡 Most installations of golangci-lint are performed for CI.
Static analysis, also called static code analysis, is a method of computer program debugging that is done by examining the code without executing the program. The process provides an understanding of the code structure and can help ensure that the code adheres to industry standards. Static analysis is used in software engineering by software development and quality assurance teams. Automated tools can assist programmers and developers in carrying out static analysis. The software will scan all code in a project to check for vulnerabilities while validating the code.
Static analysis is generally good at finding coding issues such as:
- Programming errors
- Coding standard violations
- Undefined values
- Syntax violations
- Security vulnerabilities
The static analysis process is also useful for addressing weaknesses in source code that could lead to buffer overflows -- a common software vulnerability.
The static analysis process is relatively simple, as long as it's automated. Generally, static analysis occurs before software testing in early development. In the DevOps development practice, it will occur in the create phases.
Once the code is written, a static code analyzer should be run to look over the code. It will check against defined coding rules from standards or custom predefined rules. Once the code is run through the static code analyzer, the analyzer will have identified whether or not the code complies with the set rules. It is sometimes possible for the software to flag false positives, so it is important for someone to go through and dismiss any. Once false positives are waived, developers can begin to fix any apparent mistakes, generally starting from the most critical ones. Once the code issues are resolved, the code can move on to testing through execution.
Without having code testing tools, static analysis will take a lot of work, since humans will have to review the code and figure out how it will behave in runtime environments. Therefore, it's a good idea to find a tool that automates the process. Getting rid of any lengthy processes will make for a more efficient work environment.
There are several static analysis methods an organization could use, which include:
- Control analysis -- focuses on the control flow in a calling structure. For example, a control flow could be a process, function, method or in a subroutine.
- Data analysis -- makes sure defined data is properly used while also making sure data objects are properly operating.
- Fault/failure analysis -- analyzes faults and failures in model components.
- Interface analysis -- verifies simulations to check the code and makes sure the interface fits into the model and simulation.
In a broader sense, with less official categorization, static analysis can be broken into formal, cosmetic, design properties, error checking and predictive categories. Formal meaning if the code is correct; cosmetic meaning if the code syncs up with style standards; design properties meaning the level of complexities; error checking which looks for code violations; and predictive, which asks how code will behave when run.
We recommend using our GitHub Action for running golangci-lint in CI for GitHub projects. It's fast and uses smart caching inside and it can be much faster than the simple binary installation.
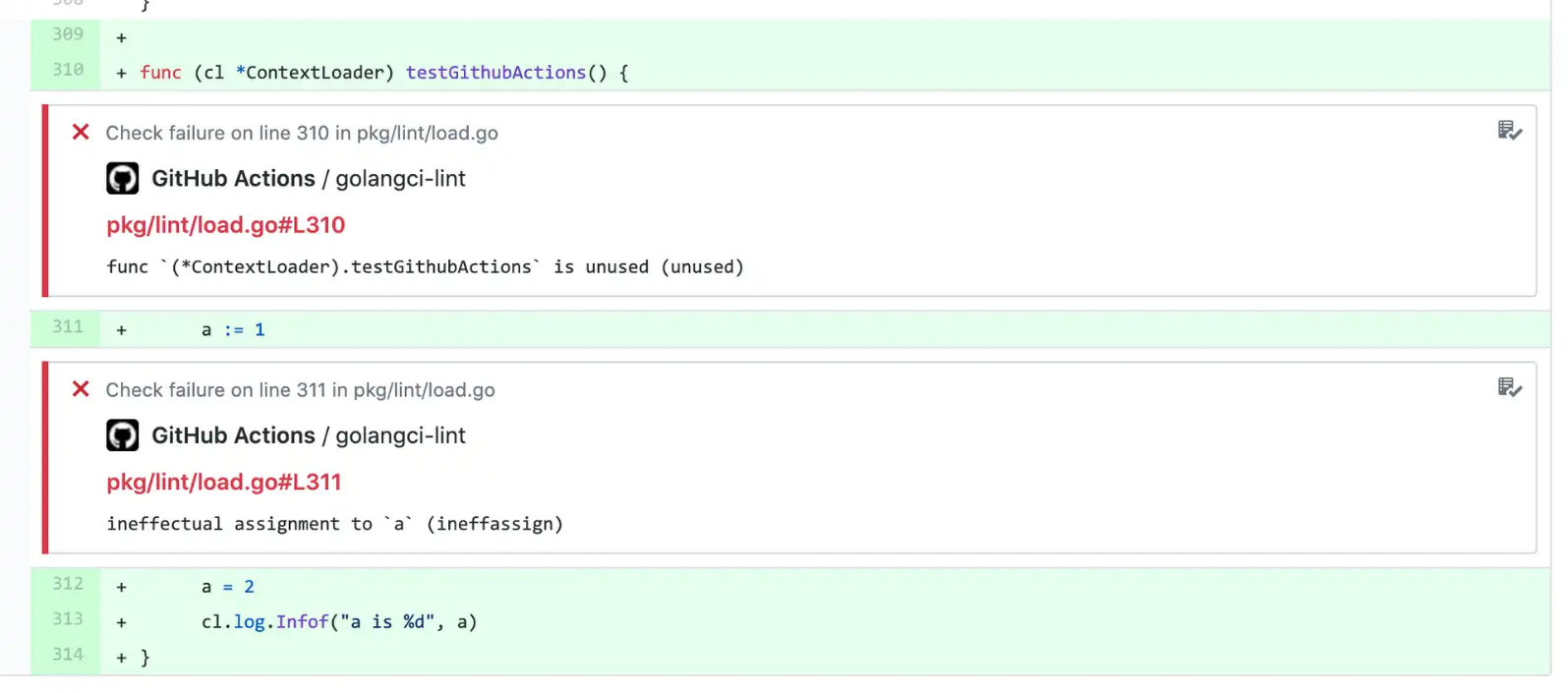
Also, the action creates GitHub annotations for found issues: you don't need to dig into build log to see found by golangci-lint issues:
It's important to have reproducible CI: don't start to fail all builds at the same time. With golangci-lint this can happen if you use option --enable-all and a new linter is added or even without --enable-all when one upstream linter is upgraded.
Here is the recommended way to install golangci-lint v1.51.2:
# binary will be $(go env GOPATH)/bin/golangci-lint
curl -sSfL https://raw.githubusercontent.com/golangci/golangci-lint/master/install.sh | sh -s -- -b $(go env GOPATH)/bin v1.51.2
# or install it into ./bin/
curl -sSfL https://raw.githubusercontent.com/golangci/golangci-lint/master/install.sh | sh -s v1.51.2
# In alpine linux (as it does not come with curl by default)
wget -O- -nv https://raw.githubusercontent.com/golangci/golangci-lint/master/install.sh | sh -s v1.51.2
golangci-lint --versionIt is advised that you periodically update the version of golangci-lint as the project is under active development and is constantly being improved. For any problems with golangci-lint, check out recent GitHub issues and update if needed.
# binary will be $(go env GOPATH)/bin/golangci-lint
curl -sSfL https://raw.githubusercontent.com/golangci/golangci-lint/master/install.sh | sh -s -- -b $(go env GOPATH)/bin v1.51.2
golangci-lint --versionOn Windows, you can run the above commands with Git Bash, which comes with Git for Windows.
docker run --rm -v $(pwd):/app -w /app golangci/golangci-lint:v1.51.2 golangci-lint run -vPreserving cache between consecutive runs:
docker run --rm -v $(pwd):/app -v ~/.cache/golangci-lint/v1.51.2:/root/.cache -w /app golangci/golangci-lint:v1.51.2 golangci-lint run -vColored output:
docker run -t --rm -v $(pwd):/app -w /app golangci/golangci-lint:v1.51.2 golangci-lint run -vTo run golangci-lint execute:
golangci-lint runIt's an equivalent of executing:
golangci-lint run ./...
You can choose which directories and files to analyze:
golangci-lint run dir1 dir2/... dir3/file1.go
Directories are NOT analyzed recursively. To analyze them recursively append /... to their path.
GolangCI-Lint can be used with zero configuration. By default the following linters are enabled:
$ golangci-lint help linters
Enabled by default linters:
errcheck: Errcheck is a program for checking for unchecked errors in go programs. These unchecked errors can be critical bugs in some cases [fast: false, auto-fix: false]
gosimple (megacheck): Linter for Go source code that specializes in simplifying code [fast: false, auto-fix: false]
govet (vet, vetshadow): Vet examines Go source code and reports suspicious constructs, such as Printf calls whose arguments do not align with the format string [fast: false, auto-fix: false]
ineffassign: Detects when assignments to existing variables are not used [fast: true, auto-fix: false]
staticcheck (megacheck): It's a set of rules from staticcheck. It's not the same thing as the staticcheck binary. The author of staticcheck doesn't support or approve the use of staticcheck as a library inside golangci-lint. [fast: false, auto-fix: false]
typecheck: Like the front-end of a Go compiler, parses and type-checks Go code [fast: false, auto-fix: false]
unused (megacheck): Checks Go code for unused constants, variables, functions and types [fast: false, auto-fix: false]and the following linters are disabled by default:
$ golangci-lint help lintersPass -E/--enable to enable linter and -D/--disable to disable:
golangci-lint run --disable-all -E errcheckRecommended settings for VS Code are:
"go.lintTool": "golangci-lint",
"go.lintFlags": [
"--fast"
]Using it in an editor without --fast can freeze your editor. Golangci-lint automatically discovers .golangci.yml config for edited file: you don't need to configure it in VS Code settings.
There is a plugin for SublimeLinter.
To see a list of supported linters and which linters are enabled/disabled:
golangci-lint help linters