From a89abdf793550ce0af2ade0cf18b9db685986efa Mon Sep 17 00:00:00 2001
From: Yuval Hayun <70104171+YuvHayun@users.noreply.github.com>
Date: Sun, 18 Feb 2024 13:14:35 +0200
Subject: [PATCH 001/272] update tanium v2 readme (#32975)
---
Packs/Tanium/Integrations/Tanium_v2/README.md | 4 ++--
1 file changed, 2 insertions(+), 2 deletions(-)
diff --git a/Packs/Tanium/Integrations/Tanium_v2/README.md b/Packs/Tanium/Integrations/Tanium_v2/README.md
index 53ec90bf84df..afff0db4017a 100644
--- a/Packs/Tanium/Integrations/Tanium_v2/README.md
+++ b/Packs/Tanium/Integrations/Tanium_v2/README.md
@@ -59,7 +59,7 @@ The integration was tested with 4.x version of Tanium Threat Response, and is co
OAuth 2.0 Authentication - To use OAuth 2.0 follow the next steps:
- Follow the instructions here Follow the instructions here Paste the generated API Token into the API Token parameter in the instance configuration, and leave the username
and password fields empty.
Click the Test button to validate the instance configuration.
@@ -74,7 +74,7 @@ The integration was tested with 4.x version of Tanium Threat Response, and is co
the api_token_expiration_in_days global setting (minimum value is 1), or include a value with the expire_in_days field when you create the token.
To edit a global setting in the Tanium platform, go to Administration -> Global
Settings and search for the setting you would like to edit.
- For more information see the Tanium documentation
+ For more information see the Tanium documentation
Commands
From a17d9499d917561defe4e6c1701e3eabd173e5ae Mon Sep 17 00:00:00 2001
From: Yehuda Rosenberg <90599084+RosenbergYehuda@users.noreply.github.com>
Date: Sun, 18 Feb 2024 14:47:05 +0200
Subject: [PATCH 002/272] Revert "YR/Handle long running pipelines, and commits
with no pipelines/CIAC-9386 (#32462)" (#32974)
This reverts commit 29aa622d6aebb5b27f5eec510caa3ee90a2f25c8.
Co-authored-by: Michael Yochpaz <8832013+MichaelYochpaz@users.noreply.github.com>
---
Tests/scripts/common.py | 180 +++---------------
Tests/scripts/gitlab_slack_notifier.py | 58 ++----
.../infrastructure_tests/common_test.py | 152 ++-------------
3 files changed, 60 insertions(+), 330 deletions(-)
diff --git a/Tests/scripts/common.py b/Tests/scripts/common.py
index fd8a58baddff..dc6aabdf9d8b 100644
--- a/Tests/scripts/common.py
+++ b/Tests/scripts/common.py
@@ -12,7 +12,6 @@
from Tests.scripts.utils import logging_wrapper as logging
from gitlab.v4.objects.pipelines import ProjectPipeline
from gitlab.v4.objects.commits import ProjectCommit
-from itertools import pairwise
CONTENT_NIGHTLY = 'Content Nightly'
@@ -258,9 +257,9 @@ def get_pipelines_and_commits(gitlab_client: Gitlab, project_id,
return pipelines, commits
-def get_person_in_charge(commit: ProjectCommit) -> tuple[str, str, str] | tuple[None, None, None]:
+def get_person_in_charge(commit):
"""
- Returns the name of the person in charge of the commit, the PR link and the beginning of the PR name.
+ Returns the name, email, and PR link for the author of the provided commit.
Args:
commit: The Gitlab commit object containing author info.
@@ -268,63 +267,55 @@ def get_person_in_charge(commit: ProjectCommit) -> tuple[str, str, str] | tuple[
Returns:
name: The name of the commit author.
pr: The GitHub PR link for the Gitlab commit.
- beginning_of_pr_name: The beginning of the PR name.
"""
name = commit.author_name
# pr number is always the last id in the commit title, starts with a number sign, may or may not be in parenthesis.
pr_number = commit.title.split("#")[-1].strip("()")
- beginning_of_pr_name = commit.title[:20] + "..."
if pr_number.isnumeric():
pr = f"https://github.com/demisto/content/pull/{pr_number}"
- return name, pr, beginning_of_pr_name
+ return name, pr
else:
- return None, None, None
+ return None, None
-def are_pipelines_in_order(pipeline_a: ProjectPipeline, pipeline_b: ProjectPipeline) -> bool:
+def are_pipelines_in_order(current_pipeline: ProjectPipeline, previous_pipeline: ProjectPipeline) -> bool:
"""
- Check if the pipelines are in the same order of their commits.
+ This function checks if the current pipeline was created after the previous pipeline, to avoid rare conditions
+ that pipelines are not in the same order as the commits.
Args:
- pipeline_a: The first pipeline object.
- pipeline_b: The second pipeline object.
+ current_pipeline: The current pipeline object.
+ previous_pipeline: The previous pipeline object.
Returns:
bool
"""
- pipeline_a_timestamp = parser.parse(pipeline_a.created_at)
- pipeline_b_timestamp = parser.parse(pipeline_b.created_at)
- return pipeline_a_timestamp > pipeline_b_timestamp
+ previous_pipeline_timestamp = parser.parse(previous_pipeline.created_at)
+ current_pipeline_timestamp = parser.parse(current_pipeline.created_at)
+ return current_pipeline_timestamp > previous_pipeline_timestamp
-def is_pivot(current_pipeline: ProjectPipeline, pipeline_to_compare: ProjectPipeline) -> bool | None:
+def is_pivot(current_pipeline: ProjectPipeline, previous_pipeline: ProjectPipeline) -> bool | None:
"""
Is the current pipeline status a pivot from the previous pipeline status.
Args:
current_pipeline: The current pipeline object.
- pipeline_to_compare: a pipeline object to compare to.
+ previous_pipeline: The previous pipeline object.
Returns:
True status changed from success to failed
False if the status changed from failed to success
None if the status didn't change or the pipelines are not in order of commits
"""
- in_order = are_pipelines_in_order(pipeline_a=current_pipeline, pipeline_b=pipeline_to_compare)
+ in_order = are_pipelines_in_order(current_pipeline, previous_pipeline)
if in_order:
- if pipeline_to_compare.status == 'success' and current_pipeline.status == 'failed':
+ if previous_pipeline.status == 'success' and current_pipeline.status == 'failed':
return True
- if pipeline_to_compare.status == 'failed' and current_pipeline.status == 'success':
+ if previous_pipeline.status == 'failed' and current_pipeline.status == 'success':
return False
return None
def get_reviewer(pr_url: str) -> str | None:
- """
- Get the first reviewer who approved the PR.
- Args:
- pr_url: The URL of the PR.
- Returns:
- The name of the first reviewer who approved the PR.
- """
approved_reviewer = None
try:
# Extract the owner, repo, and pull request number from the URL
@@ -346,14 +337,6 @@ def get_reviewer(pr_url: str) -> str | None:
def get_slack_user_name(name: str | None, name_mapping_path: str) -> str:
- """
- Get the slack user name for a given Github name.
- Args:
- name: The name to convert.
- name_mapping_path: The path to the name mapping file.
- Returns:
- The slack user name.
- """
with open(name_mapping_path) as map:
mapping = json.load(map)
# If the name is the name of the 'docker image update bot' reviewer - return the owner of that bot.
@@ -364,131 +347,30 @@ def get_slack_user_name(name: str | None, name_mapping_path: str) -> str:
def get_commit_by_sha(commit_sha: str, list_of_commits: list[ProjectCommit]) -> ProjectCommit | None:
- """
- Get a commit by its SHA.
- Args:
- commit_sha: The SHA of the commit.
- list_of_commits: A list of commits.
- Returns:
- The commit object.
- """
return next((commit for commit in list_of_commits if commit.id == commit_sha), None)
def get_pipeline_by_commit(commit: ProjectCommit, list_of_pipelines: list[ProjectPipeline]) -> ProjectPipeline | None:
- """
- Get a pipeline by its commit.
- Args:
- commit: The commit object.
- list_of_pipelines: A list of pipelines.
- Returns:
- The pipeline object.
- """
return next((pipeline for pipeline in list_of_pipelines if pipeline.sha == commit.id), None)
-def create_shame_message(suspicious_commits: list[ProjectCommit],
- pipeline_changed_status: bool, name_mapping_path: str) -> tuple[str, str, str, str] | None:
+def create_shame_message(current_commit: ProjectCommit,
+ pipeline_changed_status: bool, name_mapping_path: str) -> tuple[str, str, str] | None:
"""
- Create a shame message for the person in charge of the commit, or for multiple people in case of multiple suspicious commits.
- Args:
- suspicious_commits: A list of suspicious commits.
- pipeline_changed_status: A boolean indicating if the pipeline status changed.
- name_mapping_path: The path to the name mapping file.
- Returns:
- A tuple of strings containing the message, the person in charge, the PR link and the color of the message.
+ Create a shame message for the person in charge of the commit.
"""
- hi_and_status = person_in_charge = in_this_pr = color = ""
- for suspicious_commit in suspicious_commits:
- name, pr, beginning_of_pr = get_person_in_charge(suspicious_commit)
- if name and pr and beginning_of_pr:
- if name == CONTENT_BOT:
- name = get_reviewer(pr)
- name = get_slack_user_name(name, name_mapping_path)
- msg = "broken" if pipeline_changed_status else "fixed"
- color = "danger" if pipeline_changed_status else "good"
- emoji = ":cry:" if pipeline_changed_status else ":muscle:"
- if suspicious_commits.index(suspicious_commit) == 0:
- hi_and_status = f"Hi, The build was {msg} {emoji} by:"
- person_in_charge = f"@{name}"
- in_this_pr = f" That was done in this PR: {slack_link(pr, beginning_of_pr)}"
-
- else:
- person_in_charge += f" or @{name}"
- in_this_pr = ""
-
- return (hi_and_status, person_in_charge, in_this_pr, color) if hi_and_status and person_in_charge and color else None
+ name, pr = get_person_in_charge(current_commit)
+ if name and pr:
+ if name == CONTENT_BOT:
+ name = get_reviewer(pr)
+ name = get_slack_user_name(name, name_mapping_path)
+ msg = "broke" if pipeline_changed_status else "fixed"
+ color = "danger" if pipeline_changed_status else "good"
+ emoji = ":cry:" if pipeline_changed_status else ":muscle:"
+ return (f"Hi @{name}, You {msg} the build! {emoji} ",
+ f" That was done in this {slack_link(pr,'PR.')}", color)
+ return None
def slack_link(url: str, text: str) -> str:
- """
- Create a slack link.
- Args:
- url: The URL to link to.
- text: The text to display.
- Returns:
- The slack link.
- """
return f"<{url}|{text}>"
-
-
-def was_message_already_sent(commit_index: int, list_of_commits: list, list_of_pipelines: list) -> bool:
- """
- Check if a message was already sent for newer commits, this is possible if pipelines of later commits,
- finished before the pipeline of the current commit.
- Args:
- commit_index: The index of the current commit.
- list_of_commits: A list of commits.
- list_of_pipelines: A list of pipelines.
- Returns:
-
- """
- for previous_commit, current_commit in pairwise(reversed(list_of_commits[:commit_index])):
- current_pipeline = get_pipeline_by_commit(current_commit, list_of_pipelines)
- previous_pipeline = get_pipeline_by_commit(previous_commit, list_of_pipelines)
- # in rare cases some commits have no pipeline
- if current_pipeline and previous_pipeline and (is_pivot(current_pipeline, previous_pipeline) is not None):
- return True
- return False
-
-
-def get_nearest_newer_commit_with_pipeline(list_of_pipelines: list[ProjectPipeline], list_of_commits: list[ProjectCommit],
- current_commit_index: int) -> tuple[ProjectPipeline, list] | tuple[None, None]:
- """
- Get the nearest newer commit that has a pipeline.
- Args:
- list_of_pipelines: A list of pipelines.
- list_of_commits: A list of commits.
- current_commit_index: The index of the current commit.
- Returns:
- A tuple of the nearest pipeline and a list of suspicious commits that have no pipelines.
- """
- suspicious_commits = []
- for index in reversed(range(0, current_commit_index - 1)):
- next_commit = list_of_commits[index]
- suspicious_commits.append(list_of_commits[index + 1])
- next_pipeline = get_pipeline_by_commit(next_commit, list_of_pipelines)
- if next_pipeline:
- return next_pipeline, suspicious_commits
- return None, None
-
-
-def get_nearest_older_commit_with_pipeline(list_of_pipelines: list[ProjectPipeline], list_of_commits: list[ProjectCommit],
- current_commit_index: int) -> tuple[ProjectPipeline, list] | tuple[None, None]:
- """
- Get the nearest oldest commit that has a pipeline.
- Args:
- list_of_pipelines: A list of pipelines.
- list_of_commits: A list of commits.
- current_commit_index: The index of the current commit.
- Returns:
- A tuple of the nearest pipeline and a list of suspicious commits that have no pipelines.
- """
- suspicious_commits = []
- for index in range(current_commit_index, len(list_of_commits) - 1):
- previous_commit = list_of_commits[index + 1]
- suspicious_commits.append(list_of_commits[index])
- previous_pipeline = get_pipeline_by_commit(previous_commit, list_of_pipelines)
- if previous_pipeline:
- return previous_pipeline, suspicious_commits
- return None, None
diff --git a/Tests/scripts/gitlab_slack_notifier.py b/Tests/scripts/gitlab_slack_notifier.py
index fb2354c92a24..eca50e9e9136 100644
--- a/Tests/scripts/gitlab_slack_notifier.py
+++ b/Tests/scripts/gitlab_slack_notifier.py
@@ -25,8 +25,7 @@
replace_escape_characters
from Tests.scripts.github_client import GithubPullRequest
from Tests.scripts.common import get_pipelines_and_commits, is_pivot, get_commit_by_sha, get_pipeline_by_commit, \
- create_shame_message, slack_link, was_message_already_sent, get_nearest_newer_commit_with_pipeline, \
- get_nearest_older_commit_with_pipeline
+ create_shame_message, slack_link
from Tests.scripts.test_modeling_rule_report import calculate_test_modeling_rule_results, \
read_test_modeling_rule_to_jira_mapping, get_summary_for_test_modeling_rule, TEST_MODELING_RULES_TO_JIRA_TICKETS_CONVERTED
from Tests.scripts.test_playbooks_report import read_test_playbook_to_jira_mapping, TEST_PLAYBOOKS_TO_JIRA_TICKETS_CONVERTED
@@ -361,7 +360,7 @@ def construct_slack_msg(triggering_workflow: str,
pipeline_url: str,
pipeline_failed_jobs: list[ProjectPipelineJob],
pull_request: GithubPullRequest | None,
- shame_message: tuple[str, str, str, str] | None) -> tuple[list[dict[str, Any]], list[dict[str, Any]]]:
+ shame_message: tuple[str, str, str] | None) -> tuple[list[dict[str, Any]], list[dict[str, Any]]]:
# report failing jobs
content_fields = []
@@ -442,9 +441,9 @@ def construct_slack_msg(triggering_workflow: str,
title += title_append
slack_msg_start = []
if shame_message:
- hi_and_status, person_in_charge, in_this_pr, shame_color = shame_message
+ shame_title, shame_value, shame_color = shame_message
slack_msg_start.append({
- "title": f"{hi_and_status}\n{person_in_charge}\n{in_this_pr}",
+ "title": f"{shame_title}\n{shame_value}",
"color": shame_color
})
return slack_msg_start + [{
@@ -562,53 +561,32 @@ def main():
pipeline_url, pipeline_failed_jobs = collect_pipeline_data(gitlab_client, project_id, pipeline_id)
shame_message = None
- computed_slack_channel = "dmst-build-test"
if options.current_branch == DEFAULT_BRANCH and triggering_workflow == CONTENT_MERGE:
- # Check if the current commit's pipeline differs from the previous one. If the previous pipeline is still running,
- # compare the next build. For commits without pipelines, compare the current one to the nearest commit with a
- # pipeline and all those in between, marking them as suspicious.
+ # We check if the previous build failed and this one passed, or wise versa.
list_of_pipelines, list_of_commits = get_pipelines_and_commits(gitlab_client=gitlab_client,
project_id=project_id, look_back_hours=LOOK_BACK_HOURS)
current_commit = get_commit_by_sha(commit_sha, list_of_commits)
if current_commit:
current_commit_index = list_of_commits.index(current_commit)
-
# If the current commit is the last commit in the list, there is no previous commit,
# since commits are in ascending order
- # or if we already sent a shame message for newer commits, we don't want to send another one for older commits.
- if (current_commit_index != len(list_of_commits) - 1
- and not was_message_already_sent(current_commit_index, list_of_commits, list_of_pipelines)):
+ if current_commit_index != len(list_of_commits) - 1:
+ previous_commit = list_of_commits[current_commit_index + 1]
current_pipeline = get_pipeline_by_commit(current_commit, list_of_pipelines)
-
- # looking backwards until we find a commit with a pipeline to compare with
- previous_pipeline, suspicious_commits = get_nearest_older_commit_with_pipeline(
- list_of_pipelines, list_of_commits, current_commit_index)
- if previous_pipeline and suspicious_commits and current_pipeline:
- pipeline_changed_status = is_pivot(current_pipeline=current_pipeline,
- pipeline_to_compare=previous_pipeline)
-
+ previous_pipeline = get_pipeline_by_commit(previous_commit, list_of_pipelines)
+ if current_pipeline and previous_pipeline:
+ pipeline_changed_status = is_pivot(current_pipeline, previous_pipeline)
logging.info(
- f"Checking pipeline id: {current_pipeline.id}, of commit: {current_commit.title}, "
- f"after comparing with pipeline id: {previous_pipeline.id},"
- f"the change status is: {pipeline_changed_status}")
-
- if pipeline_changed_status is None and current_commit_index > 0:
- # looking_forward until we find a commit with a pipeline to compare with
- next_pipeline, suspicious_commits = get_nearest_newer_commit_with_pipeline(
- list_of_pipelines, list_of_commits, current_commit_index)
-
- if next_pipeline and suspicious_commits:
- pipeline_changed_status = is_pivot(current_pipeline=next_pipeline,
- pipeline_to_compare=current_pipeline)
- logging.info(
- f" after comparing with pipeline id: {next_pipeline.id},"
- f"the change status is: {pipeline_changed_status}")
-
+ f"Checking pipeline {current_pipeline}, the commit is {current_commit} "
+ f"and the pipeline change status is: {pipeline_changed_status}"
+ )
if pipeline_changed_status is not None:
- shame_message = create_shame_message(suspicious_commits, pipeline_changed_status, # type: ignore
- options.name_mapping_path)
+ shame_message = create_shame_message(
+ current_commit, pipeline_changed_status, options.name_mapping_path
+ )
computed_slack_channel = "test_slack_notifier_when_master_is_broken"
-
+ else:
+ computed_slack_channel = "dmst-build-test"
slack_msg_data, threaded_messages = construct_slack_msg(triggering_workflow, pipeline_url, pipeline_failed_jobs, pull_request,
shame_message)
diff --git a/Tests/scripts/infrastructure_tests/common_test.py b/Tests/scripts/infrastructure_tests/common_test.py
index de51808ddab9..47f71e6a2e3b 100644
--- a/Tests/scripts/infrastructure_tests/common_test.py
+++ b/Tests/scripts/infrastructure_tests/common_test.py
@@ -1,9 +1,11 @@
from pathlib import Path
-from Tests.scripts.common import get_reviewer, get_person_in_charge, are_pipelines_in_order, is_pivot, get_slack_user_name, \
- was_message_already_sent, get_nearest_newer_commit_with_pipeline, get_nearest_older_commit_with_pipeline
+from Tests.scripts.common import get_reviewer, get_person_in_charge, are_pipelines_in_order, is_pivot, get_slack_user_name
from requests_mock import MockerCore
+NAME_AND_PR_URL = ('John Doe', 'https://github.com/demisto/content/pull/123')
+
+
def test_get_person_in_charge(mocker):
"""
Given:
@@ -11,14 +13,14 @@ def test_get_person_in_charge(mocker):
When:
The function get_person_in_charge is called with that commit
Then:
- It should return a tuple with the author name and the pull request URL and the title beginning (up to 20 characters)
+ It should return a tuple with the author name and the pull request URL
"""
commit = mocker.Mock()
commit.author_name = 'John Doe'
commit.title = 'Fix a bug (#123)'
result = get_person_in_charge(commit)
- assert result == ('John Doe', 'https://github.com/demisto/content/pull/123', 'Fix a bug (#123)...')
+ assert result == NAME_AND_PR_URL
def test_get_person_in_charge__multiple_IDs(mocker):
@@ -28,15 +30,14 @@ def test_get_person_in_charge__multiple_IDs(mocker):
When:
The function get_person_in_charge is called with that commit
Then:
- It should return the a tuple with the author name and the pull request URL, with only the last ID in the URL,
- and the title beginning (up to 20 characters)
+ It should return the a tuple with the author name and the pull request URL, with only the last ID in the URL
"""
commit = mocker.Mock()
commit.author_name = 'John Doe'
commit.title = 'Fix a bug (#456) (#123)'
result = get_person_in_charge(commit)
- assert result == ('John Doe', 'https://github.com/demisto/content/pull/123', 'Fix a bug (#456) (#1...')
+ assert result == NAME_AND_PR_URL
def test_get_person_in_charge__no_parenthesis(mocker):
@@ -46,15 +47,14 @@ def test_get_person_in_charge__no_parenthesis(mocker):
When:
The function get_person_in_charge is called with the commit
Then:
- It should return the author name and the pull request URL (even if the ID was not in parenthesis)
- and the title beginning (up to 20 characters)
+ It should return the author name and the pull request URL even if the ID was not in parenthesis
"""
commit = mocker.Mock()
commit.author_name = 'John Doe'
commit.title = 'Fix a bug #123'
result = get_person_in_charge(commit)
- assert result == ('John Doe', 'https://github.com/demisto/content/pull/123', 'Fix a bug #123...')
+ assert result == NAME_AND_PR_URL
def test_get_person_in_charge__no_number_sign(mocker):
@@ -71,7 +71,7 @@ def test_get_person_in_charge__no_number_sign(mocker):
commit.title = 'Fix a bug (123)'
result = get_person_in_charge(commit)
- assert result == (None, None, None)
+ assert result == (None, None)
def test_pipelines_are_in_correct_order__false(mocker):
@@ -302,133 +302,3 @@ def test_get_slack_user_name__name_is_github_actions_bot():
name = "github-actions[bot]"
result = get_slack_user_name(name, str(Path(__file__).parent / 'tests_data/test_mapping.json'))
assert result == "docker images bot owner"
-
-
-COMMITS = ['commit1', 'commit2', 'commit3', 'commit4', 'commit5']
-PIPELINES = ['pipeline1', 'pipeline2', 'pipeline3', 'pipeline4', 'pipeline5']
-
-
-def test_was_message_already_sent__was_sent_for_true_pivot(mocker):
- """
- Given:
- An index of a commit and a list of commits and pipelines with a positive pivot in newer pipelines
- When:
- The function was_message_already_sent is called with the index, commits and pipelines
- Then:
- It should return True since the message was already sent for newer pipelines
- """
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', side_effect=lambda commit, pipelines: commit)
- mocker.patch('Tests.scripts.common.is_pivot', return_value=True)
-
- assert was_message_already_sent(2, COMMITS, PIPELINES) is True
-
-
-def test_was_message_already_sent__was_sent_for_false_pivot(mocker):
- """
- Given:
- An index of a commit and a list of commits and pipelines with a negative pivot in newer pipelines
- When:
- The function was_message_already_sent is called with the index, commits and pipelines
- Then:
- It should return True since the message was already sent for newer pipelines
- """
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', side_effect=lambda commit, pipelines: commit)
- mocker.patch('Tests.scripts.common.is_pivot', return_value=False)
- assert was_message_already_sent(2, COMMITS, PIPELINES) is True
-
-
-def test_was_message_already_sent__was_not_sent(mocker):
- """
- Given:
- An index of a commit and a list of commits and pipelines with a no pivots in newer pipelines
- When:
- The function was_message_already_sent is called with the index, commits and pipelines
- Then:
- It should return False since the message was not sent for newer pipelines
- """
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', side_effect=lambda commit, pipelines: commit)
- mocker.patch('Tests.scripts.common.is_pivot', return_value=None)
- assert was_message_already_sent(2, COMMITS, PIPELINES) is False
-
-
-def test_was_message_already_sent__was_not_sent_no_pipeline(mocker):
- """
- Given:
- An index of a commit that has no pipeline and a list of commits and pipelines with a positive pivot in newer pipelines
- When:
- The function was_message_already_sent is called with the index, commits and pipelines
- Then:
- It should return False since the message was not sent for newer pipelines since current commit has no pipeline
- """
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', side_effect=lambda commit, pipelines: commit)
- mocker.patch('Tests.scripts.common.is_pivot', return_value=True)
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', side_effect=lambda commit,
- pipelines: None if commit == 'commit2' else commit)
- assert was_message_already_sent(2, COMMITS, PIPELINES) is False
-
-
-def test_get_nearest_newer_commit__with_pipeline(mocker):
- """
- Given:
- A list of commits and pipelines, but only the first commit has a pipeline
- When:
- The function get_nearest_commit_with_pipeline is called with the list of commits,
- the index of current commit and "newer" as the direction
- Then:
- It should return the first commit since he is the closest with a pipeline,
- and a list of all commits between the first commit and the current one that are suspicious
- """
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', side_effect=lambda commit,
- pipelines: commit if commit == 'commit1' else None)
- pipeline, suspicious_commits = get_nearest_newer_commit_with_pipeline(PIPELINES, COMMITS, 3)
- assert pipeline == 'commit1'
- assert suspicious_commits == ['commit3', 'commit2']
-
-
-def test_get_nearest_older_commit__with_pipeline(mocker):
- """
- Given:
- A list of commits and pipelines, but only the last commit has a pipeline
- When:
- The function get_nearest_older_commit_with_pipeline is called with the list of commits,
- Then:
- It should return the last commit since he is the closest with a pipeline,
- and a list of all commits between the last commit and the current one that are suspicious
- """
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', side_effect=lambda commit,
- pipelines: commit if commit == 'commit5' else None)
- pipeline, suspicious_commits = get_nearest_older_commit_with_pipeline(PIPELINES, COMMITS, 1)
- assert pipeline == 'commit5'
- assert suspicious_commits == ['commit2', 'commit3', 'commit4']
-
-
-def test_get_nearest_newer_commit_with_pipeline__no_pipelines(mocker):
- """
- Given:
- A list of commits and pipelines, but no commit has a pipeline
- When:
- The function get_nearest_newer_commit_with_pipeline is called with the list of commits,
- Then:
- It should return None since no commit has a pipeline.
- """
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', return_value='pipeline_for_commit')
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', return_value=None)
- pipeline, suspicious_commits = get_nearest_newer_commit_with_pipeline(PIPELINES, COMMITS, 2)
- assert pipeline is None
- assert suspicious_commits is None
-
-
-def test_get_nearest_older_commit_with_pipeline__no_pipelines(mocker):
- """
- Given:
- A list of commits and pipelines, but no commit has a pipeline
- When:
- The function get_nearest_older_commit_with_pipeline is called with the list of commits,
- Then:
- It should return None since no commit has a pipeline.
- """
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', return_value='pipeline_for_commit')
- mocker.patch('Tests.scripts.common.get_pipeline_by_commit', return_value=None)
- pipeline, suspicious_commits = get_nearest_older_commit_with_pipeline(PIPELINES, COMMITS, 2)
- assert pipeline is None
- assert suspicious_commits is None
From ef002a1b327de0bbc538768ad369126c63fdfb80 Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Sun, 18 Feb 2024 15:01:50 +0200
Subject: [PATCH 003/272] MISP 2.1.41 - Add Custom Object command (#32955)
* MISP 2.1.41 - Add Custom Object command (#32881)
* MISP 2.1.41 - add-custom-object command
* Updated release notes
* Updated MISPV3_test.py
* Update Packs/MISP/ReleaseNotes/2_1_41.md
Co-authored-by: Yuval Hayun <70104171+YuvHayun@users.noreply.github.com>
* Updated MISPV3.py
* Revert Docker Version
---------
Co-authored-by: Yuval Hayun <70104171+YuvHayun@users.noreply.github.com>
* Update Packs/MISP/ReleaseNotes/2_1_41.md
Co-authored-by: Dan Tavori <38749041+dantavori@users.noreply.github.com>
---------
Co-authored-by: Martin Ohl
Co-authored-by: Yuval Hayun <70104171+YuvHayun@users.noreply.github.com>
Co-authored-by: Dan Tavori <38749041+dantavori@users.noreply.github.com>
---
Packs/MISP/Integrations/MISPV3/MISPV3.py | 45 +++++++++
Packs/MISP/Integrations/MISPV3/MISPV3.yml | 91 +++++++++++++++++++
Packs/MISP/Integrations/MISPV3/MISPV3_test.py | 35 +++++++
Packs/MISP/Integrations/MISPV3/README.md | 52 +++++++++++
.../MISPV3/test_data/response_add_object.json | 65 +++++++++++++
.../test_data/response_object_templates.json | 31 +++++++
.../response_raw_object_template.json | 52 +++++++++++
Packs/MISP/ReleaseNotes/2_1_41.md | 3 +
Packs/MISP/pack_metadata.json | 2 +-
9 files changed, 375 insertions(+), 1 deletion(-)
create mode 100644 Packs/MISP/Integrations/MISPV3/test_data/response_add_object.json
create mode 100644 Packs/MISP/Integrations/MISPV3/test_data/response_object_templates.json
create mode 100644 Packs/MISP/Integrations/MISPV3/test_data/response_raw_object_template.json
create mode 100644 Packs/MISP/ReleaseNotes/2_1_41.md
diff --git a/Packs/MISP/Integrations/MISPV3/MISPV3.py b/Packs/MISP/Integrations/MISPV3/MISPV3.py
index df7427799834..eaefc0263a8f 100644
--- a/Packs/MISP/Integrations/MISPV3/MISPV3.py
+++ b/Packs/MISP/Integrations/MISPV3/MISPV3.py
@@ -302,6 +302,28 @@ def build_generic_object(template_name: str, args: list[dict]) -> GenericObjectG
return misp_object
+def build_custom_object(template_name: str, args: list[dict]):
+ obj = PYMISP.object_templates()
+ for entry in obj:
+ if str(entry.get('ObjectTemplate').get('name')).lower() == template_name:
+
+ custom_obj = PYMISP.get_raw_object_template(template_name)
+
+ if not os.path.exists('/tmp/{}'.format(template_name)):
+ os.mkdir('/tmp/{}'.format(template_name))
+ open('/tmp/{}/definition.json'.format(template_name), 'w').write(json.dumps(custom_obj))
+
+ misp_object = MISPObject(name=template_name, misp_objects_path_custom='/tmp')
+
+ for arg in args:
+ for key, value in arg.items():
+ misp_object.add_attribute(key, value)
+
+ return misp_object
+
+ return False
+
+
def misp_convert_timestamp_to_date_string(timestamp: str | int) -> str:
"""
Gets a timestamp from MISP response (1546713469) and converts it to human readable format
@@ -1496,6 +1518,27 @@ def add_generic_object_command(demisto_args: dict):
f'`attribute` parameter could not be decoded, may not a valid JSON\nattribute: {attributes}', str(e))
+def add_custom_object_command(demisto_args: dict):
+ event_id = demisto_args.get('event_id', '')
+ template = demisto_args.get('template', '')
+ attributes = demisto_args.get('attributes', '').replace("'", '"')
+
+ try:
+ args = json.loads(attributes)
+ if not isinstance(args, list):
+ args = dict_to_generic_object_format(args)
+
+ obj = build_custom_object(template, args)
+ if obj is not False:
+ return add_object(event_id, obj)
+ else:
+ raise DemistoException('Unable to find custom template {}'. format(template))
+
+ except ValueError as e:
+ raise DemistoException(
+ f'`attribute` parameter could not be decoded, may not a valid JSON\nattribute: {attributes}', str(e))
+
+
def convert_arg_to_misp_args(demisto_args, args_names):
return [{arg.replace('_', '-'): demisto_args.get(arg)} for arg in args_names if demisto_args.get(arg)]
@@ -1768,6 +1811,8 @@ def main():
return_results(add_ip_object(args))
elif command == 'misp-add-object':
return_results(add_generic_object_command(args))
+ elif command == 'misp-add-custom-object':
+ return_results(add_custom_object_command(args))
elif command == 'misp-update-attribute':
return_results(update_attribute_command(args))
elif command == 'misp-delete-attribute':
diff --git a/Packs/MISP/Integrations/MISPV3/MISPV3.yml b/Packs/MISP/Integrations/MISPV3/MISPV3.yml
index 77b5193f05d7..86d9ec7eb0fd 100644
--- a/Packs/MISP/Integrations/MISPV3/MISPV3.yml
+++ b/Packs/MISP/Integrations/MISPV3/MISPV3.yml
@@ -2120,6 +2120,97 @@ script:
- contextPath: MISP.Event.Object.Description
description: Description of the object.
type: String
+ - arguments:
+ - description: ID of the event to add the object to.
+ name: event_id
+ required: true
+ - description: Custom Template name.
+ name: template
+ required: true
+ - description: 'Attributes. For example, {"description": "Manager Ferrari", "make": "Ferrari", "model": "308 GTS"}.'
+ name: attributes
+ required: true
+ description: Adds custom objects to MISP.
+ name: misp-add-custom-object
+ outputs:
+ - contextPath: MISP.Event.ID
+ description: MISP event ID.
+ type: number
+ - contextPath: MISP.Event.Object.MetaCategory
+ description: Object meta category.
+ type: String
+ - contextPath: MISP.Event.Object.Distribution
+ description: Distribution of the object.
+ type: Number
+ - contextPath: MISP.Event.Object.Name
+ description: Name of the object.
+ type: String
+ - contextPath: MISP.Event.Object.TemplateVersion
+ description: Template version of the object.
+ type: Number
+ - contextPath: MISP.Event.Object.EventID
+ description: ID of the event in which the object was first created.
+ type: Number
+ - contextPath: MISP.Event.Object.TemplateUUID
+ description: UUID of the template.
+ type: String
+ - contextPath: MISP.Event.Object.LastChanged
+ description: Timestamp when the object was last changed.
+ type: String
+ - contextPath: MISP.Event.Object.Deleted
+ description: Whether the object was deleted.
+ type: Boolean
+ - contextPath: MISP.Event.Object.ID
+ description: ID of the object.
+ type: Number
+ - contextPath: MISP.Event.Object.UUID
+ description: UUID of the object.
+ type: String
+ - contextPath: MISP.Event.Object.Attribute.Value
+ description: Value of the attribute.
+ type: String
+ - contextPath: MISP.Event.Object.Attribute.EventID
+ description: ID of the first event from which the object originated.
+ type: Number
+ - contextPath: MISP.Event.Object.Attribute.LastChanged
+ description: Attribute last changed timestamp.
+ type: Date
+ - contextPath: MISP.Event.Object.Attribute.Deleted
+ description: Whether the object was deleted?.
+ type: Boolean
+ - contextPath: MISP.Event.Object.Attribute.ObjectID
+ description: ID of the object.
+ type: Number
+ - contextPath: MISP.Event.Object.Attribute.DisableCorrelation
+ description: Whether correlation is disabled.
+ type: Boolean
+ - contextPath: MISP.Event.Object.Attribute.ID
+ description: ID of the attribute.
+ type: Unknown
+ - contextPath: MISP.Event.Object.Attribute.ObjectRelation
+ description: Relation of the object.
+ type: String
+ - contextPath: MISP.Event.Object.Attribute.Type
+ description: Object type.
+ type: String
+ - contextPath: MISP.Event.Object.Attribute.UUID
+ description: UUID of the attribute.
+ type: String
+ - contextPath: MISP.Event.Object.Attribute.ToIDs
+ description: Whether the to_ids flag is on.
+ type: Boolean
+ - contextPath: MISP.Event.Object.Attribute.Category
+ description: Category of the attribute.
+ type: String
+ - contextPath: MISP.Event.Object.Attribute.SharingGroupID
+ description: ID of the sharing group.
+ type: Number
+ - contextPath: MISP.Event.Object.Attribute.Comment
+ description: Comment of the attribute.
+ type: String
+ - contextPath: MISP.Event.Object.Description
+ description: Description of the object.
+ type: String
- arguments:
- description: ID of a MISP event.
name: event_id
diff --git a/Packs/MISP/Integrations/MISPV3/MISPV3_test.py b/Packs/MISP/Integrations/MISPV3/MISPV3_test.py
index 15e4b9353db4..46e7fe9a90d0 100644
--- a/Packs/MISP/Integrations/MISPV3/MISPV3_test.py
+++ b/Packs/MISP/Integrations/MISPV3/MISPV3_test.py
@@ -721,6 +721,41 @@ def test_add_msg_email_object(mocker):
assert 'misp-add-email-object command does not support *.msg files' in str(exception_info.value)
+def test_add_custom_object(mocker):
+ """
+ Given:
+ - A custom template name.
+ When:
+ - Running add_custom_object command.
+ Then:
+ - Ensure that the readable output is valid.
+ """
+ from MISPV3 import add_custom_object_command
+ event_id = 1572
+
+ result_object_templates = util_load_json('test_data/response_object_templates.json')
+ mocker.patch('MISPV3.PYMISP.object_templates', return_value=result_object_templates)
+
+ response_raw_obj_tempalte = util_load_json('test_data/response_raw_object_template.json')
+ mocker.patch('MISPV3.PYMISP.get_raw_object_template', return_value=response_raw_obj_tempalte)
+
+ response_add_obj = util_load_json('test_data/response_add_object.json')
+ mocker.patch('MISPV3.PYMISP.add_object', return_value=response_add_obj)
+
+ demisto_args = {
+ "event_id": event_id,
+ "template": "corporate-asset",
+ "attributes": "{'asset-type': 'Server','asset-id': '1','text': 'test text'}"
+ }
+
+ result = add_custom_object_command(demisto_args)
+ expected_output = {
+ 'readable_output': 'Object has been added to MISP event ID {}'.format(event_id),
+ 'outputs': response_add_obj
+ }
+ assert result.readable_output == expected_output['readable_output']
+
+
@pytest.mark.parametrize(
'demisto_args, is_attribute, expected_result',
[
diff --git a/Packs/MISP/Integrations/MISPV3/README.md b/Packs/MISP/Integrations/MISPV3/README.md
index e1fb66269bbf..162e22bbd48c 100644
--- a/Packs/MISP/Integrations/MISPV3/README.md
+++ b/Packs/MISP/Integrations/MISPV3/README.md
@@ -3650,6 +3650,58 @@ Adds any other object to MISP.
>Object has been added to MISP event ID 1655
+### misp-add-custom-object
+
+***
+Adds custom objects to MISP.
+
+#### Base Command
+
+`misp-add-custom-object`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| event_id | ID of the event to add the object to. | Required |
+| template | Custom Template name. | Required |
+| attributes | Attributes. For example, {"description": "Manager Ferrari", "make": "Ferrari", "model": "308 GTS"}. | Required |
+
+#### Context Output
+
+| **Path** | **Type** | **Description** |
+| --- | --- | --- |
+| MISP.Event.ID | number | MISP event ID. |
+| MISP.Event.Object.MetaCategory | String | Object meta category. |
+| MISP.Event.Object.Distribution | Number | Distribution of the object. |
+| MISP.Event.Object.Name | String | Name of the object. |
+| MISP.Event.Object.TemplateVersion | Number | Template version of the object. |
+| MISP.Event.Object.EventID | Number | ID of the event in which the object was first created. |
+| MISP.Event.Object.TemplateUUID | String | UUID of the template. |
+| MISP.Event.Object.LastChanged | String | Timestamp when the object was last changed. |
+| MISP.Event.Object.Deleted | Boolean | Whether the object was deleted. |
+| MISP.Event.Object.ID | Number | ID of the object. |
+| MISP.Event.Object.UUID | String | UUID of the object. |
+| MISP.Event.Object.Attribute.Value | String | Value of the attribute. |
+| MISP.Event.Object.Attribute.EventID | Number | ID of the first event from which the object originated. |
+| MISP.Event.Object.Attribute.LastChanged | Date | Attribute last changed timestamp. |
+| MISP.Event.Object.Attribute.Deleted | Boolean | Whether the object was deleted?. |
+| MISP.Event.Object.Attribute.ObjectID | Number | ID of the object. |
+| MISP.Event.Object.Attribute.DisableCorrelation | Boolean | Whether correlation is disabled. |
+| MISP.Event.Object.Attribute.ID | Unknown | ID of the attribute. |
+| MISP.Event.Object.Attribute.ObjectRelation | String | Relation of the object. |
+| MISP.Event.Object.Attribute.Type | String | Object type. |
+| MISP.Event.Object.Attribute.UUID | String | UUID of the attribute. |
+| MISP.Event.Object.Attribute.ToIDs | Boolean | Whether the to_ids flag is on. |
+| MISP.Event.Object.Attribute.Category | String | Category of the attribute. |
+| MISP.Event.Object.Attribute.SharingGroupID | Number | ID of the sharing group. |
+| MISP.Event.Object.Attribute.Comment | String | Comment of the attribute. |
+| MISP.Event.Object.Description | String | Description of the object. |
+
+#### Command Example
+
+```!misp-add-custom-object event_id="1572" template="corporate-asset" attributes="{\"asset-type\":\"Server\",\"asset-id\":\"12\",\"text\":\"Asset Details\"}"```
+
### misp-add-ip-object
***
diff --git a/Packs/MISP/Integrations/MISPV3/test_data/response_add_object.json b/Packs/MISP/Integrations/MISPV3/test_data/response_add_object.json
new file mode 100644
index 000000000000..519001959a0d
--- /dev/null
+++ b/Packs/MISP/Integrations/MISPV3/test_data/response_add_object.json
@@ -0,0 +1,65 @@
+{
+ "Object":
+ {
+ "id": "20524",
+ "name": "corporate-asset",
+ "meta-category": "misc",
+ "description": "Corporate asset",
+ "template_uuid": "1a99327a-bbe6-493d-97da-fce83965eccd",
+ "template_version": "20210317",
+ "event_id": "1572",
+ "uuid": "1642924e-c749-4758-b0e4-f1f9d8474393",
+ "timestamp": "1707861295",
+ "distribution": "5",
+ "sharing_group_id": "0",
+ "comment": "",
+ "deleted": false,
+ "first_seen": null,
+ "last_seen": null,
+ "Attribute":
+ [
+ {
+ "id": "285625",
+ "event_id": "1572",
+ "object_id": "20524",
+ "object_relation": "asset-type",
+ "category": "Other",
+ "type": "text",
+ "value1": "Server",
+ "value2": "",
+ "to_ids": false,
+ "uuid": "7399c837-8044-49be-b313-52192cf18af8",
+ "timestamp": "1707861295",
+ "distribution": "5",
+ "sharing_group_id": "0",
+ "comment": "",
+ "deleted": false,
+ "disable_correlation": true,
+ "first_seen": null,
+ "last_seen": null,
+ "value": "Server"
+ },
+ {
+ "id": "285626",
+ "event_id": "1572",
+ "object_id": "20524",
+ "object_relation": "asset-id",
+ "category": "Targeting data",
+ "type": "target-machine",
+ "value1": "1",
+ "value2": "",
+ "to_ids": false,
+ "uuid": "b7143b40-ae18-4b15-8e8e-af4bce5f906c",
+ "timestamp": "1707861295",
+ "distribution": "5",
+ "sharing_group_id": "0",
+ "comment": "",
+ "deleted": false,
+ "disable_correlation": true,
+ "first_seen": null,
+ "last_seen": null,
+ "value": "1"
+ }
+ ]
+ }
+}
\ No newline at end of file
diff --git a/Packs/MISP/Integrations/MISPV3/test_data/response_object_templates.json b/Packs/MISP/Integrations/MISPV3/test_data/response_object_templates.json
new file mode 100644
index 000000000000..a0ed35df491b
--- /dev/null
+++ b/Packs/MISP/Integrations/MISPV3/test_data/response_object_templates.json
@@ -0,0 +1,31 @@
+[
+ {
+ "ObjectTemplate":
+ {
+ "id": "300",
+ "user_id": "1",
+ "org_id": "1",
+ "uuid": "1a99327a-bbe6-493d-97da-fce83965eccd",
+ "name": "corporate-asset",
+ "meta-category": "misc",
+ "description": "Corporate asset",
+ "version": "20210317",
+ "requirements":
+ {
+ "required":
+ [
+ "asset-type",
+ "asset-id"
+ ]
+ },
+ "fixed": true,
+ "active": true
+ },
+ "Organisation":
+ {
+ "id": "1",
+ "name": "Palo",
+ "uuid": "8d1fff3b-a47a-4629-9b5e-1907e25cca99"
+ }
+ }
+]
\ No newline at end of file
diff --git a/Packs/MISP/Integrations/MISPV3/test_data/response_raw_object_template.json b/Packs/MISP/Integrations/MISPV3/test_data/response_raw_object_template.json
new file mode 100644
index 000000000000..a81ceb824f66
--- /dev/null
+++ b/Packs/MISP/Integrations/MISPV3/test_data/response_raw_object_template.json
@@ -0,0 +1,52 @@
+{
+ "description": "Corporate asset",
+ "meta-category": "misc",
+ "name": "corporate-asset",
+ "required":
+ [
+ "asset-type",
+ "asset-id"
+ ],
+ "uuid": "1a99327a-bbe6-493d-97da-fce83965eccd",
+ "version": 20210317,
+ "attributes":
+ {
+ "asset-type":
+ {
+ "description": "Type of asset",
+ "disable_correlation": true,
+ "misp-attribute": "text",
+ "ui-priority": 3,
+ "values_list":
+ [
+ "Server",
+ "Workstation",
+ "Printer",
+ "Network",
+ "Mobile",
+ "Monitor"
+ ]
+ },
+ "asset-id":
+ {
+ "description": "Asset identification",
+ "disable_correlation": true,
+ "misp-attribute": "target-machine",
+ "ui-priority": 0
+ },
+ "business-unit":
+ {
+ "description": "Organizational business unit associated with the asset",
+ "disable_correlation": true,
+ "misp-attribute": "target-org",
+ "ui-priority": 2
+ },
+ "text":
+ {
+ "description": "A description of the asset.",
+ "disable_correlation": true,
+ "misp-attribute": "text",
+ "ui-priority": 1
+ }
+ }
+}
\ No newline at end of file
diff --git a/Packs/MISP/ReleaseNotes/2_1_41.md b/Packs/MISP/ReleaseNotes/2_1_41.md
new file mode 100644
index 000000000000..09341431629d
--- /dev/null
+++ b/Packs/MISP/ReleaseNotes/2_1_41.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### MISP v3
+- Added the ***misp-add-custom-object*** command.
diff --git a/Packs/MISP/pack_metadata.json b/Packs/MISP/pack_metadata.json
index 49aa2988e19e..72fbbc8605da 100644
--- a/Packs/MISP/pack_metadata.json
+++ b/Packs/MISP/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "MISP",
"description": "Malware information and threat sharing platform.",
"support": "xsoar",
- "currentVersion": "2.1.40",
+ "currentVersion": "2.1.41",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 9765f29bfac204f81d6f2002498012109a4f7ad2 Mon Sep 17 00:00:00 2001
From: Darya Koval <72339940+daryakoval@users.noreply.github.com>
Date: Sun, 18 Feb 2024 15:09:01 +0200
Subject: [PATCH 004/272] Zimperium v2Integration (#32615)
* saving initial integration
* added fetch + fixes in the commands
* unitests and output descriptions
* pre-commit fix
* trying to fix fetch
* trying to fix fetch
* rn; mapper; last fixes;
* incident field
* remove conf.json
* added mapper
* fixes from cr
* fixes from cr
* adding readme, pre-commit fixes
* adding readme fixes
* fix for test module
* limit fix
* fix readme
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* docker, coverage
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* fix validation on readme
* limit and page_size
* save fixes from the demo
* filter report by improtance
* fixes in pre-commit after demo
* fixed a release notes
* change the search params descriptioin
* changes from thr cr
* pre-commit fix
* fromversion 6.9 to pass the build
* fromversion 6.9 to pass the build
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---
Packs/Zimperium/.secrets-ignore | 2 +
...sifier-Zimperium_v2_-_Incoming_Mapper.json | 31 +
.../incidentfield-Zimperium_Bundle_ID.json | 31 +
.../Integrations/ZimperiumV2/README.md | 1759 +++++++++++++
.../Integrations/ZimperiumV2/ZimperiumV2.py | 1105 ++++++++
.../Integrations/ZimperiumV2/ZimperiumV2.yml | 1353 ++++++++++
.../ZimperiumV2/ZimperiumV2_description.md | 14 +
.../ZimperiumV2/ZimperiumV2_image.png | Bin 0 -> 3297 bytes
.../ZimperiumV2/ZimperiumV2_test.py | 418 +++
.../ZimperiumV2/command_examples.txt | 16 +
.../test_data/app_version_list.json | 74 +
.../test_data/cve_devices_get.json | 62 +
.../ZimperiumV2/test_data/device_cve_get.json | 65 +
.../ZimperiumV2/test_data/device_search.json | 192 ++
.../test_data/devices_os_version.json | 46 +
.../test_data/policy_app_settings.json | 48 +
.../policy_device_inactivity_get.json | 36 +
.../policy_device_inactivity_list.json | 12 +
.../test_data/policy_group_list.json | 83 +
.../test_data/policy_phishing.json | 42 +
.../ZimperiumV2/test_data/policy_privacy.json | 61 +
.../ZimperiumV2/test_data/policy_threat.json | 69 +
.../ZimperiumV2/test_data/report_get.json | 61 +
.../ZimperiumV2/test_data/threat_search.json | 238 ++
.../ZimperiumV2/test_data/users_search.json | 25 +
.../test_data/vulnerability_get.json | 41 +
.../layoutscontainer-Zimperium_event.json | 9 +
Packs/Zimperium/ReleaseNotes/2_0_0.md | 23 +
.../Zimperiumv2-TestPlaybook.yml | 2293 +++++++++++++++++
Packs/Zimperium/pack_metadata.json | 2 +-
Tests/conf.json | 6 +-
31 files changed, 8215 insertions(+), 2 deletions(-)
create mode 100644 Packs/Zimperium/Classifiers/classifier-Zimperium_v2_-_Incoming_Mapper.json
create mode 100644 Packs/Zimperium/IncidentFields/incidentfield-Zimperium_Bundle_ID.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/README.md
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2.py
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2.yml
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2_description.md
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2_image.png
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2_test.py
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/command_examples.txt
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/app_version_list.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/cve_devices_get.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/device_cve_get.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/device_search.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/devices_os_version.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/policy_app_settings.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/policy_device_inactivity_get.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/policy_device_inactivity_list.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/policy_group_list.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/policy_phishing.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/policy_privacy.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/policy_threat.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/report_get.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/threat_search.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/users_search.json
create mode 100644 Packs/Zimperium/Integrations/ZimperiumV2/test_data/vulnerability_get.json
create mode 100644 Packs/Zimperium/ReleaseNotes/2_0_0.md
create mode 100644 Packs/Zimperium/TestPlaybooks/Zimperiumv2-TestPlaybook.yml
diff --git a/Packs/Zimperium/.secrets-ignore b/Packs/Zimperium/.secrets-ignore
index 640a9a093c20..97f9d0062c14 100644
--- a/Packs/Zimperium/.secrets-ignore
+++ b/Packs/Zimperium/.secrets-ignore
@@ -83,3 +83,5 @@ http://www.webrtc.org
64.233.178.82
216.58.194.110
172.217.14.170
+https://test_url.com
+https://mtduat.zimperium.com
diff --git a/Packs/Zimperium/Classifiers/classifier-Zimperium_v2_-_Incoming_Mapper.json b/Packs/Zimperium/Classifiers/classifier-Zimperium_v2_-_Incoming_Mapper.json
new file mode 100644
index 000000000000..bda405985aa1
--- /dev/null
+++ b/Packs/Zimperium/Classifiers/classifier-Zimperium_v2_-_Incoming_Mapper.json
@@ -0,0 +1,31 @@
+{
+ "description": "",
+ "feed": false,
+ "id": "Zimperium v2 - Incoming Mapper",
+ "mapping": {
+ "Zimperium Event": {
+ "dontMapEventToLabels": true,
+ "internalMapping": {
+ "App": {
+ "simple": "zappInstance.name"
+ },
+ "Zimperium Bundle ID": {
+ "simple": "zappInstance.bundleId"
+ },
+ "Mobile Device Model": {
+ "simple": "device.model"
+ },
+ "OS": {
+ "simple": "device.os.name"
+ },
+ "OS Version": {
+ "simple": "device.os.version"
+ }
+ }
+ }
+ },
+ "name": "Zimperium v2 - Incoming Mapper",
+ "type": "mapping-incoming",
+ "version": -1,
+ "fromVersion": "6.10.0"
+}
\ No newline at end of file
diff --git a/Packs/Zimperium/IncidentFields/incidentfield-Zimperium_Bundle_ID.json b/Packs/Zimperium/IncidentFields/incidentfield-Zimperium_Bundle_ID.json
new file mode 100644
index 000000000000..fcaa48d4aba6
--- /dev/null
+++ b/Packs/Zimperium/IncidentFields/incidentfield-Zimperium_Bundle_ID.json
@@ -0,0 +1,31 @@
+{
+ "id": "incident_zimperiumbundleid",
+ "version": -1,
+ "modified": "2024-02-01T09:42:52.067562173Z",
+ "name": "Zimperium Bundle ID",
+ "ownerOnly": false,
+ "cliName": "zimperiumbundleid",
+ "type": "shortText",
+ "closeForm": false,
+ "editForm": true,
+ "required": false,
+ "neverSetAsRequired": false,
+ "isReadOnly": false,
+ "useAsKpi": false,
+ "locked": false,
+ "system": false,
+ "content": true,
+ "group": 0,
+ "hidden": false,
+ "openEnded": false,
+ "associatedTypes": [
+ "Zimperium Event"
+ ],
+ "associatedToAll": false,
+ "unmapped": false,
+ "unsearchable": true,
+ "caseInsensitive": true,
+ "sla": 0,
+ "threshold": 72,
+ "fromVersion": "6.10.0"
+}
\ No newline at end of file
diff --git a/Packs/Zimperium/Integrations/ZimperiumV2/README.md b/Packs/Zimperium/Integrations/ZimperiumV2/README.md
new file mode 100644
index 000000000000..d475ea75be48
--- /dev/null
+++ b/Packs/Zimperium/Integrations/ZimperiumV2/README.md
@@ -0,0 +1,1759 @@
+Fetch and investigate mobile security alerts, generated based on anomalous or unauthorized activities detected on a user's mobile device.
+This integration was integrated and tested with version v.5.24.0 of Zimperium v2.
+
+Some changes have been made that might affect your existing content.
+If you are upgrading from a previous version of this integration, see [Breaking Changes](#breaking-changes-from-the-previous-version-of-this-integration).
+
+## Configure Zimperium v2 on Cortex XSOAR
+
+1. Navigate to **Settings** > **Integrations** > **Servers & Services**.
+2. Search for Zimperium v2.
+3. Click **Add instance** to create and configure a new integration instance.
+
+ | **Parameter** | **Description** | **Required** |
+ | --- | --- | --- |
+ | Server URL (e.g., https://mtduat.zimperium.com) | | True |
+ | Client ID | | True |
+ | Client Secret | | True |
+ | Fetch incidents | | False |
+ | Search Params (e.g, severityName=CRITICAL,teamId=myId) | Comma-separated list of search parameters and its values. Same as for the "zimperium-threat-search" command. | False |
+ | Max fetch | | False |
+ | First fetch timestamp (<number> <time unit>, e.g., 12 hours, 7 days) | | False |
+ | Advanced: Minutes to look back when fetching | Use this parameter to determine how far back to look in the search for incidents that were created before the last run time and did not match the query when they were created. | False |
+ | Trust any certificate (not secure) | | False |
+ | Use system proxy settings | | False |
+ | Incident type | | |
+
+4. Click **Test** to validate the URLs, token, and connection.
+
+## Commands
+
+You can execute these commands from the Cortex XSOAR CLI, as part of an automation, or in a playbook.
+After you successfully execute a command, a DBot message appears in the War Room with the command details.
+
+### zimperium-users-search
+
+***
+Search users. Only a user created as a "Team admin" is authorized to perform this request. Also, it will only get information about the teams that this user is associated with. Users that are not part of any team (such as account admin) won’t appear in the response.
+
+#### Base Command
+
+`zimperium-users-search`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| user_id | The ID of the user to search. | Optional |
+| page_size | Maximum number of results to retrieve in each page. If a limit is not provided, default is 50. | Optional |
+| page | Page number. Default is 0. | Optional |
+| limit | Number of total results to return. Default is 50. | Optional |
+| team_id | Used to filter the user data by the team the user belongs to. | Optional |
+
+#### Context Output
+
+| **Path** | **Type** | **Description** |
+| --- | --- | --- |
+| Zimperium.User.id | String | The ID of the Zimperium user. |
+| Zimperium.User.created | Date | The date and time that the user was created. |
+| Zimperium.User.email | String | The email address of the user. |
+| Zimperium.User.firstName | String | The first name of the user. |
+| Zimperium.User.languagePreference | Unknown | The language preference for the user. |
+| Zimperium.User.lastLogin | Unknown | The time of the last login of the user. |
+| Zimperium.User.lastName | String | The last name of the user. |
+| Zimperium.User.middleName | Unknown | The middle name of the user. |
+| Zimperium.User.modified | Date | The date and time that the user was modified. |
+| Zimperium.User.notificationEmail | String | The email address for the user's notifications. |
+| Zimperium.User.phone | Unknown | The phone number of the user. |
+| Zimperium.User.role.id | String | The role identifier of the user. |
+| Zimperium.User.role.name | String | The role name of the user. |
+| Zimperium.User.role.scopeBounds | String | The role scope for a user. |
+| Zimperium.User.teams.id | String | The ID of the team of the user. |
+| Zimperium.User.teams.name | String | The name of the team of the user. |
+| Zimperium.User.validated | Boolean | The user's validated status. |
+
+#### Command example
+```!zimperium-users-search user_id="1" team_id="1"```
+#### Context Example
+```json
+{
+ "Zimperium": {
+ "User": {
+ "created": "2024-01-21T11:02:08.789+00:00",
+ "email": "email1@email.com",
+ "firstName": "name",
+ "id": "1",
+ "languagePreference": null,
+ "lastLogin": null,
+ "lastName": "name",
+ "middleName": null,
+ "modified": "2024-01-21T11:02:08.789+00:00",
+ "notificationEmail": "email1@email.com",
+ "phone": null,
+ "role": {
+ "id": "1",
+ "name": "Team Admin",
+ "scopeBounds": "TEAM_BOUNDED"
+ },
+ "teams": [
+ {
+ "id": "1",
+ "name": "Default"
+ }
+ ],
+ "validated": false
+ }
+ }
+}
+```
+
+#### Human Readable Output
+
+>### Users Search Results
+>| Id | First Name | Last Name |Email|Created|Role|Teams|
+>|----|------------|-----------|---|---|---|---|
+>| 1 | name | name | email1@email.com | 2024-01-21T11:02:08.789+00:00 | scopeBounds: TEAM_BOUNDED// cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-2173 | false | exploitPocUrls: |
+>| CVE-2019-2176 | Remote code execution | Critical | https:// cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-2176 | false | exploitPocUrls: |
+
+
+### zimperium-vulnerability-get
+
+***
+Gets the vulnerabilities.
+
+#### Base Command
+
+`zimperium-vulnerability-get`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| page_size | Maximum number of results to retrieve in each page. If a limit is not provided, default is 50. | Optional |
+| page | Page number. Default is 0. | Optional |
+| limit | Number of total results to return. Default is 50. | Optional |
+
+#### Context Output
+
+| **Path** | **Type** | **Description** |
+| --- | --- | --- |
+| Zimperium.Vulnerability.id | String | The ID of the vulnerability. |
+| Zimperium.Vulnerability.blueBorneVulnerable | Boolean | Whether the operating system is blue born vulnerable. |
+| Zimperium.Vulnerability.cveCount | Number | Number of CVEs on the operating system. |
+| Zimperium.Vulnerability.lastCveSync | Date | The date of the last CVE sync. |
+| Zimperium.Vulnerability.os | Number | The vulnerability operating system. |
+| Zimperium.Vulnerability.osPatchDate | Unknown | The max patch date of operating system. |
+| Zimperium.Vulnerability.osRiskChecksum | String | The operating system risk checksum. |
+| Zimperium.Vulnerability.osVersion | String | The operating system version. |
+| Zimperium.Vulnerability.osVersionAndPatchDate | String | The operating system version and the patch date. |
+| Zimperium.Vulnerability.risk | String | The risk classification. |
+
+
+#### Command example
+```!zimperium-vulnerability-get limit=1```
+#### Context Example
+```json
+{
+ "Zimperium": {
+ "Vulnerability": {
+ "blueBorneVulnerable": false,
+ "cveCount": 432,
+ "id": 56745,
+ "lastCveSync": 1707218387516,
+ "os": 2,
+ "osPatchDate": null,
+ "osRiskChecksum": "6A",
+ "osVersion": "14.6",
+ "osVersionAndPatchDate": "14.6",
+ "risk": "Critical"
+ }
+ }
+}
+```
+
+#### Human Readable Output
+
+>### Vulnerabilities List
+>|Id|Os|Os Version And Patch Date|Os Version|Os Patch Date|Risk|Cve Count|Last Cve Sync|Os Risk Checksum|Blue Borne Vulnerable|
+>|---|---|---|---|---|---|---|---|---|---|
+>| 56745 | 2 | 14.6 | 14.6 | | Critical | 432 | 2024-02-06 11:19:47 | 6A | false |
+
+
+
+### zimperium-policy-group-list
+
+***
+Get policy groups.
+
+#### Base Command
+
+`zimperium-policy-group-list`
+
+#### Input
+
+| **Argument Name** | **Description** | **Required** |
+| --- | --- | --- |
+| module | The module parameter is required to get the groups related to EMM connection or ZIPS connection. Default is "ZIPS". Possible values are: EMM, ZIPS. | Optional |
+
+#### Context Output
+
+| **Path** | **Type** | **Description** |
+| --- | --- | --- |
+| Zimperium.PolicyGroup.id | String | The ID of the policy group. |
+| Zimperium.PolicyGroup.accountId | String | The account identifier for the policy group's content. |
+| Zimperium.PolicyGroup.appPolicyId | String | The app policy ID of the policy group. |
+| Zimperium.PolicyGroup.appSettingsId | String | The app settings ID of the policy group. |
+| Zimperium.PolicyGroup.brandingPolicyId | Unknown | The branding policy identifier of the policy group. |
+| Zimperium.PolicyGroup.created | Date | The date and time the policy group was created. |
+| Zimperium.PolicyGroup.description | String | The description of the policy group. |
+| Zimperium.PolicyGroup.dormancyPolicyId | String | The dormancy policy identifier of the policy group. |
+| Zimperium.PolicyGroup.emmConnectionId | Unknown | The enterprise mobile management (EMM) connection ID of the policy group. |
+| Zimperium.PolicyGroup.emmGroupId | Unknown | The enterprise mobile management (EMM) group ID of the policy group. |
+| Zimperium.PolicyGroup.emmPriority | Unknown | The enterprise mobile management (EMM) priority of the policy group. |
+| Zimperium.PolicyGroup.extensionPolicyId | String | The extension policy identifier of the policy group. |
+| Zimperium.PolicyGroup.content.global | Boolean | Whether the policy group is global. |
+| Zimperium.PolicyGroup.knoxPolicyId | Unknown | The Knox policy ID of the policy group. |
+| Zimperium.PolicyGroup.modified | Date | The date and time when the policy group was last modified. |
+| Zimperium.PolicyGroup.name | String | The name of the policy group. |
+| Zimperium.PolicyGroup.networkPolicyId | String | The network policy ID of the policy group. |
+| Zimperium.PolicyGroup.osRiskPolicyId | String | The operating system risk policy ID of the policy group. |
+| Zimperium.PolicyGroup.phishingPolicyId | String | The phishing policy identifier of the policy group. |
+| Zimperium.PolicyGroup.privacyId | String | The privacy identifier of the policy group. |
+| Zimperium.PolicyGroup.team.id | String | The ID of the team associated with the policy group. |
+| Zimperium.PolicyGroup.team.name | String | The team name of the policy group. |
+| Zimperium.PolicyGroup.trmId | String | The Threat Response Matrix (TRM) ID of the policy group. |
+| Zimperium.PolicyGroup.team | Unknown | The policy group's team information. |
+
+#### Command example
+```!zimperium-policy-group-list```
+#### Context Example
+```json
+{
+ "Zimperium": {
+ "PolicyGroup": [
+ {
+ "accountId": "2",
+ "appPolicyId": "2",
+ "appSettingsId": "a5",
+ "brandingPolicyId": null,
+ "created": "2024-01-22T11:37:36.749+00:00",
+ "description": "test",
+ "dormancyPolicyId": "2",
+ "emmConnectionId": null,
+ "emmGroupId": null,
+ "emmPriority": null,
+ "extensionPolicyId": "2",
+ "global": false,
+ "id": "65",
+ "knoxPolicyId": null,
+ "modified": "2024-01-22T11:37:36.749+00:00",
+ "name": "Test",
+ "networkPolicyId": "2",
+ "osRiskPolicyId": "2",
+ "phishingPolicyId": "2",
+ "privacyId": "a2",
+ "team": {
+ "id": "1",
+ "name": "Default"
+ },
+ "trmId": "er"
+ }
+ ]
+ }
+}
+```
+
+#### Human Readable Output
+
+>### Policy Group List
+>|Id|Name|Team|Privacy Id|Trm Id|Phishing Policy Id|App Settings Id|App Policy Id|Network Policy Id|Os Risk Policy Id|
+>|---|---|---|---|---|---|---|---|---|---|
+>| 65 | Test | id: 1 , e.g., 12 hours, 7 days)
+ name: first_fetch
+ required: false
+ type: 0
+ section: Collect
+- display: 'Advanced: Minutes to look back when fetching'
+ name: look_back
+ type: 0
+ required: false
+ defaultvalue: 1
+ additionalinfo: Use this parameter to determine how far back to look in the search for incidents that were created before the last run time and did not match the query when they were created.
+ section: Collect
+- display: Trust any certificate (not secure)
+ name: insecure
+ type: 8
+ required: false
+ section: Connect
+- display: Use system proxy settings
+ name: proxy
+ type: 8
+ required: false
+ section: Connect
+- display: Incident type
+ name: incidentType
+ type: 13
+description: Fetch and investigate mobile security alerts, generated based on anomalous or unauthorized activities detected on a user's mobile device. Compatible with Zimperium 5.X API version.
+name: Zimperium v2
+fromversion: 6.9.0
+display: Zimperium v2
+script:
+ commands:
+ - arguments:
+ - description: The ID of the user to search.
+ name: user_id
+ - description: Maximum number of results to retrieve in each page. If a limit is not provided, default is 50.
+ name: page_size
+ - defaultValue: '0'
+ description: Page number.
+ name: page
+ - defaultValue: '50'
+ description: Number of total results to return.
+ name: limit
+ - description: Used to filter the user data by the Team the user belongs to.
+ name: team_id
+ description: Search users. Only a user created as a "Team admin" is authorized to perform this request. Also, it will only get information about the teams that this user is associated with. Users that are not part of any team (such as account admin) won’t appear in the response.
+ name: zimperium-users-search
+ outputs:
+ - contextPath: Zimperium.User.id
+ description: The ID of the Zimperium user.
+ type: String
+ - contextPath: Zimperium.User.created
+ description: The date and time that the user was created.
+ type: Date
+ - contextPath: Zimperium.User.email
+ description: The email address of the user.
+ type: String
+ - contextPath: Zimperium.User.firstName
+ description: The first name of the user.
+ type: String
+ - contextPath: Zimperium.User.languagePreference
+ description: The language preference for the user.
+ type: Unknown
+ - contextPath: Zimperium.User.lastLogin
+ description: The time of the last login of the user.
+ type: Unknown
+ - contextPath: Zimperium.User.lastName
+ description: The last name of the user.
+ type: String
+ - contextPath: Zimperium.User.middleName
+ description: The middle name of the user.
+ type: Unknown
+ - contextPath: Zimperium.User.modified
+ description: The date and time that the user was modified.
+ type: Date
+ - contextPath: Zimperium.User.notificationEmail
+ description: The email address for the user's notifications.
+ type: String
+ - contextPath: Zimperium.User.phone
+ description: The phone number of the user.
+ type: Unknown
+ - contextPath: Zimperium.User.role.id
+ description: The role identifier of the user.
+ type: String
+ - contextPath: Zimperium.User.role.name
+ description: The role name of the user.
+ type: String
+ - contextPath: Zimperium.User.role.scopeBounds
+ description: The role scope for a user.
+ type: String
+ - contextPath: Zimperium.User.teams.id
+ description: The ID of the team of the user.
+ type: String
+ - contextPath: Zimperium.User.teams.name
+ description: The name of the team of the user.
+ type: String
+ - contextPath: Zimperium.User.validated
+ description: The user's validated status.
+ type: Boolean
+ - arguments:
+ - description: The ID of the device to search for.
+ name: device_id
+ - description: Maximum number of results to retrieve in each page. If a limit is not provided, default is 50.
+ name: page_size
+ - defaultValue: '0'
+ description: Page number.
+ name: page
+ - defaultValue: '50'
+ description: Number of total results to return.
+ name: limit
+ description: Search devices.
+ name: zimperium-devices-search
+ outputs:
+ - contextPath: Zimperium.Device.accountId
+ description: The account identifier of the device.
+ type: String
+ - contextPath: Zimperium.Device.activationName
+ description: The activation name of the device.
+ type: String
+ - contextPath: Zimperium.Device.additionalDeviceInfo
+ description: The additional device information.
+ type: Unknown
+ - contextPath: Zimperium.Device.agentType
+ description: The agent type of the device.
+ type: Number
+ - contextPath: Zimperium.Device.appStatus
+ description: The app status.
+ type: String
+ - contextPath: Zimperium.Device.appVersions
+ description: The app version of the device.
+ type: Unknown
+ - contextPath: Zimperium.Device.bundleId
+ description: The bundle identifier of the device.
+ type: Unknown
+ - contextPath: Zimperium.Device.created
+ description: The date and time that the device was created.
+ type: Date
+ - contextPath: Zimperium.Device.deleted
+ description: Whether the device was deleted.
+ type: Boolean
+ - contextPath: Zimperium.Device.developerOptionsOn
+ description: Whether the developer options are on.
+ type: Boolean
+ - contextPath: Zimperium.Device.deviceOwner.email
+ description: The email address of the device owner.
+ type: String
+ - contextPath: Zimperium.Device.fullType
+ description: The device's full type.
+ type: String
+ - contextPath: Zimperium.Device.groupId
+ description: The device group identifier.
+ type: String
+ - contextPath: Zimperium.Device.id
+ description: The unique identifier of the device.
+ type: String
+ - contextPath: Zimperium.Device.lastSeen
+ description: The time when the device was last seen.
+ type: Date
+ - contextPath: Zimperium.Device.lockScreenUnprotected
+ description: Whether the device's lockscreen is unprotected or not.
+ type: Boolean
+ - contextPath: Zimperium.Device.model
+ description: The model of the device.
+ type: String
+ - contextPath: Zimperium.Device.os.id
+ description: The operating system identifier of the device.
+ type: Number
+ - contextPath: Zimperium.Device.os.maxOsVersion
+ description: The maximum operating system version of the device.
+ type: String
+ - contextPath: Zimperium.Device.os.name
+ description: The operating system name.
+ type: String
+ - contextPath: Zimperium.Device.os.osVersionId
+ description: The operating system version identifier of the device.
+ type: Number
+ - contextPath: Zimperium.Device.os.policyCompliant
+ description: Whether the operating system policy is compliant in the device.
+ type: Boolean
+ - contextPath: Zimperium.Device.os.type
+ description: The operating system type of the device.
+ type: String
+ - contextPath: Zimperium.Device.os.version
+ description: The operating system version of the device.
+ type: String
+ - contextPath: Zimperium.Device.processed
+ description: Whether the device is processed.
+ type: Boolean
+ - contextPath: Zimperium.Device.processedAt
+ description: The date and time that the device was processed.
+ type: Date
+ - contextPath: Zimperium.Device.riskPosture
+ description: The risk posture of the device.
+ type: Number
+ - contextPath: Zimperium.Device.riskPostureName
+ description: The risk posture name of the device.
+ type: String
+ - contextPath: Zimperium.Device.teamId
+ description: The team ID of the device.
+ type: String
+ - contextPath: Zimperium.Device.teamName
+ description: The team name of the device.
+ type: String
+ - contextPath: Zimperium.Device.threatState
+ description: The threat state information.
+ type: Unknown
+ - contextPath: Zimperium.Device.zappInstance.agentType
+ description: The agent type of the device.
+ type: Number
+ - contextPath: Zimperium.Device.zappInstance.buildNumber
+ description: The build number of the zappInstance.
+ type: String
+ - contextPath: Zimperium.Device.zappInstance.bundleId
+ description: The bundle identifier of the zappInstance.
+ type: String
+ - contextPath: Zimperium.Device.zappInstance.groupId
+ description: The Zimperium device group identifier for the zappInstance.
+ type: String
+ - contextPath: Zimperium.Device.zappInstance.id
+ description: The ID of the zappInstance.
+ type: String
+ - contextPath: Zimperium.Device.zappInstance.lastSeen
+ description: The last seen timestamp for the zappInstance.
+ type: Date
+ - contextPath: Zimperium.Device.zappInstance.name
+ description: The name of the zappInstance.
+ type: String
+ - contextPath: Zimperium.Device.zappInstance.policiesInfo
+ description: The policies information.
+ type: String
+ - contextPath: Zimperium.Device.zappInstance.version
+ description: The version of the zappInstance.
+ type: String
+ - contextPath: Zimperium.Device.zappInstance.zappId
+ description: The ID of the zappInstance.
+ type: String
+ - contextPath: Zimperium.Device.zappInstance.zbuildNumber
+ description: The Zimperium device's zappinstance.
+ type: String
+ - contextPath: Zimperium.Device.zappInstance.zversion
+ description: The device's zappinstance version.
+ type: String
+ - contextPath: Zimperium.Device.zdeviceId
+ description: The zdevice ID.
+ type: String
+ - contextPath: Zimperium.Device.appVersions.appVersionId
+ description: The app version ID of the device.
+ type: String
+ - contextPath: Zimperium.Device.appVersions.bundleId
+ description: The bundle identifier of the app versions.
+ type: String
+ - contextPath: Zimperium.Device.os.maxOsPatchDate
+ description: The max patch date of operating system of the device.
+ type: String
+ - contextPath: Zimperium.Device.os.patchDate
+ description: The operating system patch date of the device.
+ type: Date
+ - contextPath: Zimperium.Device.threatState.numberOfCriticalThreats
+ description: The number of critical threats detected on the device.
+ type: Number
+ - contextPath: Zimperium.Device.zappInstance.permissionsState
+ description: The permissions state on the device.
+ type: Unknown
+ - contextPath: Zimperium.Device.dormancyProcessed
+ description: The device's dormancy processed status.
+ type: Boolean
+ - contextPath: Zimperium.Device.os.versionUpgradeable
+ description: The operating system version upgradeable for the device.
+ type: Boolean
+ - contextPath: Zimperium.Device.threatState
+ description: The threat state of the device.
+ type: Unknown
+ - contextPath: Zimperium.Device.zappInstance.policiesInfo
+ description: The device policies info.
+ type: Unknown
+ - contextPath: Zimperium.Device.isJailbroken
+ description: Whether the endpoint's device is jailbroken or not.
+ type: Boolean
+ - arguments:
+ - description: The ID of the app version for which to get a JSON report. Can be retrieved using the zimperium-app-version-list command, in the field "Zimperium.AppVersion.id".
+ name: app_version_id
+ required: true
+ - defaultValue: 'High'
+ auto: PREDEFINED
+ predefined:
+ - Low
+ - Medium
+ - High
+ - All
+ description: The importance of the threat.
+ name: importance
+ description: Gets a report.
+ name: zimperium-report-get
+ outputs:
+ - contextPath: Zimperium.Report.ContentInformation
+ description: The content of the report.
+ type: String
+ - contextPath: Zimperium.Report.glob
+ description: The glob pattern for the Zimperium report.
+ type: Number
+ - contextPath: Zimperium.Report.platform
+ description: The platform on which the report was created.
+ type: String
+ - contextPath: Zimperium.Report.report.androidAnalysis
+ description: The android analysis of the report.
+ type: String
+ - contextPath: Zimperium.Report.report.appProperties
+ description: The app properties.
+ type: String
+ - contextPath: Zimperium.Report.report.certificate
+ description: The certificate.
+ type: String
+ - contextPath: Zimperium.Report.report.communications
+ description: The communications.
+ type: String
+ - contextPath: Zimperium.Report.report.contentInformation
+ description: The content information of the report.
+ type: String
+ - contextPath: Zimperium.Report.report.distribution
+ description: The report distribution.
+ type: String
+ - contextPath: Zimperium.Report.report.jsonVersion
+ description: The JSON version of the report.
+ type: String
+ - contextPath: Zimperium.Report.report.riskProfile
+ description: The risk profile.
+ type: String
+ - contextPath: Zimperium.Report.report.scanDetails
+ description: The description of the scan details for the report.
+ type: Unknown
+ - contextPath: Zimperium.Report.report.scanVersion
+ description: The scan version of the Zimperium report.
+ type: Unknown
+ - contextPath: Zimperium.Report.report.vulnerabilities
+ description: The vulnerabilities found in the report.
+ type: Unknown
+ - contextPath: Zimperium.Report.result
+ description: The Zimperium report result.
+ type: Number
+ - arguments:
+ - description: The date in the criteria after which the threat occurred.
+ name: after
+ required: true
+ - description: The date in the criteria before which the threat occurred.
+ name: before
+ - description: "A comma-separated list of parameter and their values by which to filter your request. For example: 'device.os.version=7.1.1,vectorName=Device'. The parameters table is available under 'Threat API Details' section in the 'Threats' section, of the Zimperium API documentation, or on the website at https://mtduat.zimperium.com/ziap-docs/zips-docs/api/api_details_threat.html#optional-search-parameters-supported."
+ name: search_params
+ isArray: true
+ - description: Used to filter the user data by the team the user belongs to.
+ name: team_id
+ - auto: PREDEFINED
+ predefined:
+ - ios
+ - android
+ description: Used to filter by the operating system.
+ name: os
+ - auto: PREDEFINED
+ predefined:
+ - LOW
+ - NORMAL
+ - ELEVATED
+ - CRITICAL
+ description: The severity of the threat.
+ name: severity
+ - description: Maximum number of results to retrieve in each page. If a limit is not provided, default is 50.
+ name: page_size
+ - defaultValue: '0'
+ description: Page number.
+ name: page
+ - defaultValue: '50'
+ description: Number of total results to return.
+ name: limit
+ description: Search threats.
+ name: zimperium-threat-search
+ outputs:
+ - contextPath: Zimperium.Threat.id
+ description: The ID of the threat.
+ type: String
+ - contextPath: Zimperium.Threat.accountId
+ description: The account identifier of the threat.
+ type: String
+ - contextPath: Zimperium.Threat.activationName
+ description: The activation name of a threat.
+ type: String
+ - contextPath: Zimperium.Threat.agentType
+ description: The agent type for the threat.
+ type: Number
+ - contextPath: Zimperium.Threat.arpTablesInfo
+ description: The ARP tables information for the devices.
+ type: Unknown
+ - contextPath: Zimperium.Threat.categoryId
+ description: The category of a threat.
+ type: Number
+ - contextPath: Zimperium.Threat.classification
+ description: The classification of a threat.
+ type: Number
+ - contextPath: Zimperium.Threat.classificationName
+ description: The classification name for a threat.
+ type: String
+ - contextPath: Zimperium.Threat.detectionFiles
+ description: The threat detection files.
+ type: Unknown
+ - contextPath: Zimperium.Threat.device.id
+ description: The unique identifier of the device.
+ type: String
+ - contextPath: Zimperium.Threat.device.mamDeviceId
+ description: The mobile application management (MAM) ID of the device.
+ type: String
+ - contextPath: Zimperium.Threat.device.mdmDeviceId
+ description: The mobile device management (MAM) ID of the device.
+ type: String
+ - contextPath: Zimperium.Threat.device.model
+ description: The model of the device the threat was detected on.
+ type: String
+ - contextPath: Zimperium.Threat.device.os.id
+ description: The operating system identifier of the device the threat was detected on.
+ type: Number
+ - contextPath: Zimperium.Threat.device.os.name
+ description: The operating system name for the device.
+ type: String
+ - contextPath: Zimperium.Threat.device.os.version
+ description: The operating system version of the device.
+ type: String
+ - contextPath: Zimperium.Threat.device.zdeviceId
+ description: The zDevice ID of the device.
+ type: String
+ - contextPath: Zimperium.Threat.deviceId
+ description: The unique identifier of the device the threat was detected on.
+ type: String
+ - contextPath: Zimperium.Threat.deviceOwner
+ description: The owner of the device.
+ type: String
+ - contextPath: Zimperium.Threat.eventProcessedTimestamp
+ description: The timestamp when the threat event was processed.
+ type: Date
+ - contextPath: Zimperium.Threat.eventReceivedTimestamp
+ description: The timestamp when the threat event was received.
+ type: Date
+ - contextPath: Zimperium.Threat.generalInfo.actionTriggered
+ description: The threat action triggered on a threat.
+ type: String
+ - contextPath: Zimperium.Threat.generalInfo.bssid
+ description: The Basic Service Set Identifier (BSSID) of the threat.
+ type: String
+ - contextPath: Zimperium.Threat.generalInfo.deviceTimestamp
+ description: The timestamp of the endpoint's device.
+ type: Date
+ - contextPath: Zimperium.Threat.generalInfo.jailbreakReasons
+ description: The jailbreak reasons for the threat.
+ type: String
+ - contextPath: Zimperium.Threat.generalInfo.ssid
+ description: The service set identifier (SSID) for the threat.
+ type: String
+ - contextPath: Zimperium.Threat.generalInfo.timeInterval
+ description: The time interval for a threat.
+ type: Number
+ - contextPath: Zimperium.Threat.groupId
+ description: The ID of the threat group.
+ type: String
+ - contextPath: Zimperium.Threat.lastModified
+ description: The time the threat was last modified.
+ type: Date
+ - contextPath: Zimperium.Threat.mitigationEvents
+ description: The mitigation events for the threat.
+ type: Unknown
+ - contextPath: Zimperium.Threat.nearByNetworks
+ description: The near-by networks for the threat.
+ type: Unknown
+ - contextPath: Zimperium.Threat.networkStatistics
+ description: The Zimperium threat network statistics.
+ type: Unknown
+ - contextPath: Zimperium.Threat.os
+ description: The operating system.
+ type: String
+ - contextPath: Zimperium.Threat.policiesInfo.deployedAt
+ description: The date that the threat policy was deployed.
+ type: Date
+ - contextPath: Zimperium.Threat.policiesInfo.downloadedAt
+ description: The date when the threat policy was downloaded.
+ type: Date
+ - contextPath: Zimperium.Threat.policiesInfo.hash
+ description: The hash of the threat policy information.
+ type: String
+ - contextPath: Zimperium.Threat.policiesInfo.type
+ description: The threat policy type.
+ type: String
+ - contextPath: Zimperium.Threat.processList.parentProcessId
+ description: The parent process ID for a threat's process.
+ type: String
+ - contextPath: Zimperium.Threat.processList.processId
+ description: The Process ID for the threat process.
+ type: String
+ - contextPath: Zimperium.Threat.processList.processName
+ description: The Process Name for the threat.
+ type: String
+ - contextPath: Zimperium.Threat.processList.service
+ description: The services associated with the process list.
+ type: String
+ - contextPath: Zimperium.Threat.processList.user
+ description: The users and processes that are involved in the threat process.
+ type: String
+ - contextPath: Zimperium.Threat.responses.eventId
+ description: The unique identifier for an event in the threat response.
+ type: String
+ - contextPath: Zimperium.Threat.responses.responseId
+ description: The response identifier for a threat's response.
+ type: Number
+ - contextPath: Zimperium.Threat.responses.timestamp
+ description: The timestamp of the threat response.
+ type: Date
+ - contextPath: Zimperium.Threat.runningServices
+ description: The running services.
+ type: Unknown
+ - contextPath: Zimperium.Threat.severity
+ description: The severity of the threat.
+ type: Number
+ - contextPath: Zimperium.Threat.severityName
+ description: The severity name of the threat.
+ type: String
+ - contextPath: Zimperium.Threat.simulated
+ description: Is the threat simulated.
+ type: Boolean
+ - contextPath: Zimperium.Threat.state
+ description: The threat state.
+ type: Number
+ - contextPath: Zimperium.Threat.suspiciousUrlInfo
+ description: The suspicious URL information.
+ type: Unknown
+ - contextPath: Zimperium.Threat.teamId
+ description: The ID of the threat team for an incident.
+ type: String
+ - contextPath: Zimperium.Threat.teamName
+ description: The threat team name for the incident.
+ type: String
+ - contextPath: Zimperium.Threat.threatTypeId
+ description: The threat type identifier for the threat.
+ type: Number
+ - contextPath: Zimperium.Threat.threatTypeName
+ description: The threat type for the threat.
+ type: String
+ - contextPath: Zimperium.Threat.timestamp
+ description: The timestamp of the threat.
+ type: Date
+ - contextPath: Zimperium.Threat.timestampInfo
+ description: The timestamp information of the threat.
+ type: Unknown
+ - contextPath: Zimperium.Threat.vector
+ description: The threat vector for the incident.
+ type: Number
+ - contextPath: Zimperium.Threat.vectorName
+ description: The vector name for the threat.
+ type: String
+ - contextPath: Zimperium.Threat.zappId
+ description: The Zimperium threat app identifier.
+ type: String
+ - contextPath: Zimperium.Threat.zappInstance
+ description: The threat Zapp instance information.
+ type: Unknown
+ - contextPath: Zimperium.Threat.zappInstanceId
+ description: The Zapp threat instance ID.
+ type: String
+ - contextPath: Zimperium.Threat.zeventId
+ description: The Zimperium threat event identifier.
+ type: String
+ - contextPath: Zimperium.Threat.arpTablesInfo
+ description: The ARP tables info for the threat.
+ type: Unknown
+ - contextPath: Zimperium.Threat.locationInfo.geoPoint.lat
+ description: The latitude of the geoPoint.
+ type: Number
+ - contextPath: Zimperium.Threat.locationInfo.geoPoint.lon
+ description: The longitude of the geoPoint.
+ type: Number
+ - contextPath: Zimperium.Threat.locationInfo.source
+ description: The threat's source location information.
+ type: String
+ - contextPath: Zimperium.Threat.generalInfo.expectedOsVersion
+ description: The expected operating system version for the threat.
+ type: String
+ - contextPath: Zimperium.Threat.generalInfo.vulnerableOsVersion
+ description: The vulnerable operating system version for the threat.
+ type: String
+ - contextPath: Zimperium.Threat.generalInfo.vulnerableSecurityPatch
+ description: The vulnerable security patch for the endpoint.
+ type: String
+ - contextPath: Zimperium.Threat.mitigatedAt
+ description: The date when the Threat was mitigated.
+ type: Date
+ - arguments:
+ - description: The bundle ID of the app for which to get its app version.
+ name: bundle_id
+ - description: Maximum number of results to retrieve in each page. If a limit is not provided, default is 50.
+ name: page_size
+ - defaultValue: '0'
+ description: Page number.
+ name: page
+ - defaultValue: '50'
+ description: Number of total results to return.
+ name: limit
+ description: List the app versions.
+ name: zimperium-app-version-list
+ outputs:
+ - contextPath: Zimperium.AppVersion.id
+ description: The ID of the threat.
+ type: String
+ - contextPath: Zimperium.AppVersion.accountId
+ description: The account identifier for the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.bundleId
+ description: The bundle identifier for the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.classification
+ description: The classification of the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.created
+ description: When the app version was created.
+ type: Date
+ - contextPath: Zimperium.AppVersion.hash
+ description: The hash of the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.name
+ description: The name of the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.platform
+ description: The platform on which the Zimperium app version is running.
+ type: String
+ - contextPath: Zimperium.AppVersion.platformId
+ description: The platform identifier for the Zimperium app version.
+ type: Number
+ - contextPath: Zimperium.AppVersion.privacy
+ description: The privacy setting for the app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.privacyRisk
+ description: The privacy risk for the Zimperium app version.
+ type: Number
+ - contextPath: Zimperium.AppVersion.processState
+ description: The process state of the app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.reportRequestId
+ description: The Zimperium app version report request ID.
+ type: String
+ - contextPath: Zimperium.AppVersion.riskVersion
+ description: The risk version of the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.security
+ description: The security of the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.securityRisk
+ description: The security risk of the Zimperium app version.
+ type: Number
+ - contextPath: Zimperium.AppVersion.source
+ description: The Zimperium app version source.
+ type: String
+ - contextPath: Zimperium.AppVersion.updatedOn
+ description: The date and time when the app version was updated.
+ type: Date
+ - contextPath: Zimperium.AppVersion.version
+ description: The version of the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.developerName
+ description: The developer name for the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.developerSignature
+ description: The developer signature for the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.filename
+ description: The filename of the Zimperium app version.
+ type: String
+ - contextPath: Zimperium.AppVersion.managed
+ description: Whether the app version is managed.
+ type: Boolean
+ - arguments:
+ - description: The ID of the CVE which is input.
+ name: cve_id
+ required: true
+ - description: The date in the criteria after which the threat occurred.
+ name: after
+ - description: The date in the criteria before which the threat occurred.
+ name: before
+ - description: Used to filter the user data by the team the user belongs to.
+ name: team_id
+ - description: Maximum number of results to retrieve in each page. If a limit is not provided, default is 50.
+ name: page_size
+ - defaultValue: '0'
+ description: Page number.
+ name: page
+ - defaultValue: '50'
+ description: Number of total results to return.
+ name: limit
+ description: Gets a devices associated with a specific CVE.
+ name: zimperium-get-devices-by-cve
+ outputs:
+ - contextPath: Zimperium.DeviceByCVE.id
+ description: The ID of the device.
+ type: String
+ - contextPath: Zimperium.DeviceByCVE.cveId
+ description: The ID of the CVE.
+ type: String
+ - contextPath: Zimperium.DeviceByCVE.os.id
+ description: The operating system identifier of the device.
+ type: Number
+ - contextPath: Zimperium.DeviceByCVE.os.maxOsPatchDate
+ description: The device operating system max patch date.
+ type: String
+ - contextPath: Zimperium.DeviceByCVE.os.maxOsVersion
+ description: The device operating system max version.
+ type: String
+ - contextPath: Zimperium.DeviceByCVE.os.name
+ description: The operating system name of the device.
+ type: String
+ - contextPath: Zimperium.DeviceByCVE.os.osVersionId
+ description: The operating system version identifier of the device.
+ type: Number
+ - contextPath: Zimperium.DeviceByCVE.os.patchDate
+ description: The patch date for of the operating system.
+ type: Date
+ - contextPath: Zimperium.DeviceByCVE.os.policyCompliant
+ description: The operating system policy compliant with the device.
+ type: Boolean
+ - contextPath: Zimperium.DeviceByCVE.os.type
+ description: The operating system type of the device.
+ type: String
+ - contextPath: Zimperium.DeviceByCVE.os.version
+ description: The operating system version of the device.
+ type: String
+ - contextPath: Zimperium.DeviceByCVE.os.versionUpgradeable
+ description: Whether the operating system version upgradeable.
+ type: Boolean
+ - contextPath: Zimperium.DeviceByCVE.teamId
+ description: The team ID of the device.
+ type: String
+ - contextPath: Zimperium.DeviceByCVE.zdeviceId
+ description: The zdevice ID of the device.
+ type: String
+ - arguments:
+ - description: The name of the version which is input. Can be retrieved using zimperium-devices-search command under "Zimperium.Device.os.version".
+ name: os_version
+ required: true
+ - description: The date of the patch for a specific version. The date format is YYYY-MM-DD. This field is only applicable to Android. If you include this field, only CVEs for Android are returned since this value does not apply to iOS.
+ name: os_patch_date
+ - auto: PREDEFINED
+ predefined:
+ - 'true'
+ - 'false'
+ description: This is used to request the devices that have been deleted.
+ name: deleted
+ - description: The date in the criteria after which the threat occurred.
+ name: after
+ - description: The date in the criteria before which the threat occurred.
+ name: before
+ - description: This is used to filter the data to their respective teams.
+ name: team_id
+ - description: Maximum number of results to retrieve in each page. If a limit is not provided, default is 50.
+ name: page_size
+ - defaultValue: '0'
+ description: Page number.
+ name: page
+ - defaultValue: '50'
+ description: Number of total results to return.
+ name: limit
+ description: Gets devices associated with a specific operating system version.
+ name: zimperium-devices-os-version
+ outputs:
+ - contextPath: Zimperium.DeviceOsVersion.id
+ description: The ID of the device.
+ type: String
+ - contextPath: Zimperium.DeviceOsVersion.os.id
+ description: The operating system identifier of the device.
+ type: Number
+ - contextPath: Zimperium.DeviceOsVersion.os.maxOsPatchDate
+ description: The device operating system max patch date.
+ type: String
+ - contextPath: Zimperium.DeviceOsVersion.os.maxOsVersion
+ description: The device operating system max version.
+ type: String
+ - contextPath: Zimperium.DeviceOsVersion.os.name
+ description: The operating system name of the device.
+ type: String
+ - contextPath: Zimperium.DeviceOsVersion.os.osVersionId
+ description: The operating system version identifier of the device.
+ type: Number
+ - contextPath: Zimperium.DeviceOsVersion.os.patchDate
+ description: The patch date of the device's operating system.
+ type: Date
+ - contextPath: Zimperium.DeviceOsVersion.os.policyCompliant
+ description: Whether the endpoint's operating system is compliant with the policy.
+ type: Boolean
+ - contextPath: Zimperium.DeviceOsVersion.os.type
+ description: The operating system type.
+ type: String
+ - contextPath: Zimperium.DeviceOsVersion.os.version
+ description: The operating system version.
+ type: String
+ - contextPath: Zimperium.DeviceOsVersion.os.versionUpgradeable
+ description: Whether the device's operating system is upgradeable.
+ type: Boolean
+ - contextPath: Zimperium.DeviceOsVersion.teamId
+ description: The team ID of the device.
+ type: String
+ - contextPath: Zimperium.DeviceOsVersion.zdeviceId
+ description: The zdevice ID of the Device.
+ type: String
+ - arguments:
+ - description: The device ID to get CVEs for.
+ name: device_id
+ required: true
+ - description: Maximum number of results to retrieve in each page. If a limit is not provided, default is 50.
+ name: page_size
+ - defaultValue: '0'
+ description: Page number.
+ name: page
+ - defaultValue: '50'
+ description: Number of total results to return.
+ name: limit
+ description: Gets the CVEs associated with a specific device.
+ name: zimperium-get-cves-by-device
+ outputs:
+ - contextPath: Zimperium.CVEByDevice.id
+ description: The ID of the CVE.
+ type: String
+ - contextPath: Zimperium.CVEByDevice.deviceId
+ description: The ID of the device.
+ type: String
+ - contextPath: Zimperium.CVEByDevice.activeExploit
+ description: Whether the CVE is active or not.
+ type: Boolean
+ - contextPath: Zimperium.CVEByDevice.exploitPocUrl.exploitPocUrls
+ description: The exploit POC URLs for the CVE.
+ type: Unknown
+ - contextPath: Zimperium.CVEByDevice.severity
+ description: The severity of a CVE on the device.
+ type: String
+ - contextPath: Zimperium.CVEByDevice.type
+ description: The CVE type.
+ type: String
+ - contextPath: Zimperium.CVEByDevice.url
+ description: The URL of the CVE.
+ type: String
+ - arguments:
+ - description: Maximum number of results to retrieve in each page. If a limit is not provided, default is 50.
+ name: page_size
+ - defaultValue: '0'
+ description: Page number.
+ name: page
+ - defaultValue: '50'
+ description: Number of total results to return.
+ name: limit
+ description: Gets the vulnerabilities.
+ name: zimperium-vulnerability-get
+ outputs:
+ - contextPath: Zimperium.Vulnerability.id
+ description: The ID of the vulnerability.
+ type: String
+ - contextPath: Zimperium.Vulnerability.blueBorneVulnerable
+ description: Whether the operating system is blue born vulnerable.
+ type: Boolean
+ - contextPath: Zimperium.Vulnerability.cveCount
+ description: Number of CVEs on the operating system.
+ type: Number
+ - contextPath: Zimperium.Vulnerability.lastCveSync
+ description: The date of the last CVE sync.
+ type: Date
+ - contextPath: Zimperium.Vulnerability.os
+ description: The vulnerability operating system.
+ type: Number
+ - contextPath: Zimperium.Vulnerability.osPatchDate
+ description: The max patch date of operating system.
+ type: Unknown
+ - contextPath: Zimperium.Vulnerability.osRiskChecksum
+ description: The operating system risk checksum.
+ type: String
+ - contextPath: Zimperium.Vulnerability.osVersion
+ description: The operating system version.
+ type: String
+ - contextPath: Zimperium.Vulnerability.osVersionAndPatchDate
+ description: The operating system version and the patch date.
+ type: String
+ - contextPath: Zimperium.Vulnerability.risk
+ description: The risk classification.
+ type: String
+ - arguments:
+ - auto: PREDEFINED
+ predefined:
+ - EMM
+ - ZIPS
+ description: The module parameter is required to get the groups related to EMM connection or ZIPS connection. Default is "ZIPS".
+ name: module
+ description: Get policy groups.
+ name: zimperium-policy-group-list
+ outputs:
+ - contextPath: Zimperium.PolicyGroup.id
+ description: The ID of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.accountId
+ description: The account identifier for the policy group's content.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.appPolicyId
+ description: The app policy ID of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.appSettingsId
+ description: The app settings ID of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.brandingPolicyId
+ description: The branding policy identifier of the policy group.
+ type: Unknown
+ - contextPath: Zimperium.PolicyGroup.created
+ description: The date and time the policy group was created.
+ type: Date
+ - contextPath: Zimperium.PolicyGroup.description
+ description: The description of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.dormancyPolicyId
+ description: The dormancy policy identifier of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.emmConnectionId
+ description: The enterprise mobile management (EMM) connection ID of the policy group.
+ type: Unknown
+ - contextPath: Zimperium.PolicyGroup.emmGroupId
+ description: The enterprise mobile management (EMM) group ID of the policy group.
+ type: Unknown
+ - contextPath: Zimperium.PolicyGroup.emmPriority
+ description: The enterprise mobile management (EMM) priority of the policy group.
+ type: Unknown
+ - contextPath: Zimperium.PolicyGroup.extensionPolicyId
+ description: The extension policy identifier of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.content.global
+ description: Whether the policy group is global.
+ type: Boolean
+ - contextPath: Zimperium.PolicyGroup.knoxPolicyId
+ description: The Knox policy ID of the policy group.
+ type: Unknown
+ - contextPath: Zimperium.PolicyGroup.modified
+ description: The date and time when the policy group was last modified.
+ type: Date
+ - contextPath: Zimperium.PolicyGroup.name
+ description: The name of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.networkPolicyId
+ description: The network policy ID of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.osRiskPolicyId
+ description: The operating system risk policy ID of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.phishingPolicyId
+ description: The phishing policy identifier of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.privacyId
+ description: The privacy identifier of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.team.id
+ description: The ID of the team associated with the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.team.name
+ description: The team name of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.trmId
+ description: The Threat Response Matrix (TRM) ID of the policy group.
+ type: String
+ - contextPath: Zimperium.PolicyGroup.team
+ description: The policy group's team information.
+ type: Unknown
+ - arguments:
+ - description: The identifier of the policy. Can be retrieved using zimperium-policy-group-list in the Zimperium.PolicyGroup.privacyId field.
+ name: policy_id
+ required: true
+ description: Get a privacy policy by its identifier.
+ name: zimperium-policy-privacy-get
+ outputs:
+ - contextPath: Zimperium.PolicyPrivacy.id
+ description: The policy privacy identifier.
+ type: String
+ - contextPath: Zimperium.PolicyPrivacy.accountId
+ description: The account identifier of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyPrivacy.assigned
+ description: Whether the policy privacy is assigned.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPrivacy.created
+ description: The date and time the policy was created.
+ type: Date
+ - contextPath: Zimperium.PolicyPrivacy.global
+ description: Whether the policy settings are global.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPrivacy.groups
+ description: The groups the policy are associated with.
+ type: String
+ - contextPath: Zimperium.PolicyPrivacy.jsonHash
+ description: The JSON hash for the policy privacy policy.
+ type: String
+ - contextPath: Zimperium.PolicyPrivacy.locationAccuracy
+ description: The location accuracy for the policy.
+ type: Number
+ - contextPath: Zimperium.PolicyPrivacy.modified
+ description: The date and time when the policy was modified.
+ type: Date
+ - contextPath: Zimperium.PolicyPrivacy.name
+ description: The name of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyPrivacy.protoHash
+ description: The hash of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyPrivacy.rules
+ description: The policy rules list.
+ type: Unknown
+ - contextPath: Zimperium.PolicyPrivacy.rules.id
+ description: The ID of the rule.
+ type: String
+ - contextPath: Zimperium.PolicyPrivacy.team
+ description: The team for the policy.
+ type: Unknown
+ - contextPath: Zimperium.PolicyPrivacy.teamId
+ description: The team ID the policy associated with.
+ type: Unknown
+ - arguments:
+ - description: The identifier of the policy. Can be retrieved using zimperium-policy-group-list in the Zimperium.PolicyGroup.trmId field.
+ name: policy_id
+ required: true
+ description: Get a threat policy by its identifier.
+ name: zimperium-policy-threat-get
+ outputs:
+ - contextPath: Zimperium.PolicyThreat.id
+ description: The identifier of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyThreat.accountId
+ description: The account identifier of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyThreat.androidJsonHash
+ description: The Android JSON hash.
+ type: String
+ - contextPath: Zimperium.PolicyThreat.androidProtoHash
+ description: The Android Proto hash.
+ type: String
+ - contextPath: Zimperium.PolicyThreat.assigned
+ description: Whether the policy is assigned.
+ type: Boolean
+ - contextPath: Zimperium.PolicyThreat.created
+ description: The date and time the policy threat was created.
+ type: Date
+ - contextPath: Zimperium.PolicyThreat.deploymentDate
+ description: The date when the policy deployment occurred.
+ type: Date
+ - contextPath: Zimperium.PolicyThreat.global
+ description: Whether the policy settings are global.
+ type: Boolean
+ - contextPath: Zimperium.PolicyThreat.groups
+ description: The groups the policy associated with.
+ type: Unknown
+ - contextPath: Zimperium.PolicyThreat.iosJsonHash
+ description: IOS JSON hash.
+ type: String
+ - contextPath: Zimperium.PolicyThreat.iosProtoHash
+ description: IOS Proto hash.
+ type: String
+ - contextPath: Zimperium.PolicyThreat.isDeployed
+ description: Whether the policy threat is deployed or not.
+ type: Boolean
+ - contextPath: Zimperium.PolicyThreat.modified
+ description: The date and time when the policy was modified.
+ type: Date
+ - contextPath: Zimperium.PolicyThreat.name
+ description: The name of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyThreat.rules
+ description: The policy rules list.
+ type: Unknown
+ - contextPath: Zimperium.PolicyThreat.rules.id
+ description: The ID of the policy rule.
+ type: String
+ - arguments:
+ - description: The identifier of the policy. Can be retrieved using zimperium-policy-group-list in the Zimperium.PolicyGroup.phishingPolicyId field.
+ name: policy_id
+ required: true
+ description: Get a phishing policy by its identifier.
+ name: zimperium-policy-phishing-get
+ outputs:
+ - contextPath: Zimperium.PolicyPhishing.id
+ description: The identifier of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyPhishing.accessControlList
+ description: The access control list for the policy resource.
+ type: Unknown
+ - contextPath: Zimperium.PolicyPhishing.accountId
+ description: The account identifier of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyPhishing.allowEndUserControl
+ description: Whether the end user is allowed to control the policy.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPhishing.contentCategoryActionList
+ description: The content of the policy category action.
+ type: Unknown
+ - contextPath: Zimperium.PolicyPhishing.created
+ description: The date and time the policy threat was created.
+ type: Date
+ - contextPath: Zimperium.PolicyPhishing.enableDnsPhishingTutorial
+ description: Whether the DNS phishing tutorial is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPhishing.enableMessageFilterTutorial
+ description: Whether the message filter tutorial is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPhishing.enableSafariBrowserExtensionTutorial
+ description: Whether the Safari Browser Extension tutorial is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPhishing.global
+ description: Whether the policy settings are global.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPhishing.groups
+ description: The groups the policy are associated with.
+ type: Unknown
+ - contextPath: Zimperium.PolicyPhishing.isDnsEnabled
+ description: Whether DNS is enabled or not.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPhishing.modified
+ description: The date and time when the policy was modified.
+ type: Date
+ - contextPath: Zimperium.PolicyPhishing.name
+ description: The name of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyPhishing.phishingDetectionAction
+ description: The phishing detection action.
+ type: String
+ - contextPath: Zimperium.PolicyPhishing.phishingPolicyType
+ description: The phishing policy type.
+ type: String
+ - contextPath: Zimperium.PolicyPhishing.team
+ description: The team the policy is associated with.
+ type: Unknown
+ - contextPath: Zimperium.PolicyPhishing.teamId
+ description: The ID of the team.
+ type: Unknown
+ - contextPath: Zimperium.PolicyPhishing.useLocalVpn
+ description: Whether to use a local VPN or not.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPhishing.useRemoteContentInspection
+ description: Whether to use remote content inspection.
+ type: Boolean
+ - contextPath: Zimperium.PolicyPhishing.useUrlSharing
+ description: Whether the URL sharing is enabled or not.
+ type: Boolean
+ - arguments:
+ - description: The identifier of the policy. Can be retrieved using zimperium-policy-group-list in the Zimperium.PolicyGroup.appSettingsId field.
+ name: app_settings_policy_id
+ required: true
+ description: List the app versions.
+ name: zimperium-policy-app-settings-get
+ outputs:
+ - contextPath: Zimperium.PolicyAppSetting.id
+ description: The identifier of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyAppSetting.accountId
+ description: The account identifier of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyAppSetting.appRiskLookupEnabled
+ description: Whether the app risk lookup is enabled or not.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.assigned
+ description: Whether the policy is assigned.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.autoActivateKnox
+ description: Whether Knox should be automatically activated.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.autoBatteryOptimizationEnabled
+ description: Whether the battery optimization is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.cogitoEnabled
+ description: Whether the cogito is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.cogitoThreshold
+ description: The cogito threshold.
+ type: Number
+ - contextPath: Zimperium.PolicyAppSetting.created
+ description: The date and time the policy was created.
+ type: Date
+ - contextPath: Zimperium.PolicyAppSetting.dangerzoneEnabled
+ description: Whether the danger zone is enabled or not.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.detectionEnabled
+ description: Whether detection is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.forensicAnalysisEnabled
+ description: Whether forensic analysis is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.global
+ description: Whether the policy is global.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.groups
+ description: The groups information.
+ type: Unknown
+ - contextPath: Zimperium.PolicyAppSetting.jsonHash
+ description: The JSON hash of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyAppSetting.modified
+ description: The modified date of the policy.
+ type: Date
+ - contextPath: Zimperium.PolicyAppSetting.name
+ description: The name of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyAppSetting.phishingEnabled
+ description: Whether phishing is enabled or not.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.phishingLocalClassifierEnabled
+ description: Whether the phishing local classifier is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.phishingThreshold
+ description: The phishing threshold.
+ type: Number
+ - contextPath: Zimperium.PolicyAppSetting.privacySummaryEnabled
+ description: Whether the privacy summary is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.protoHash
+ description: The proto hash.
+ type: String
+ - contextPath: Zimperium.PolicyAppSetting.siteInsightEnabled
+ description: Whether the site insight is enabled or not.
+ type: Boolean
+ - contextPath: Zimperium.PolicyAppSetting.staticFilesWritten
+ description: The date when the static files were written.
+ type: Date
+ - contextPath: Zimperium.PolicyAppSetting.team
+ description: The team name the policy is associated with.
+ type: Unknown
+ - contextPath: Zimperium.PolicyAppSetting.teamId
+ description: The ID of the team to which the policy belongs.
+ type: Unknown
+ - arguments:
+ - description: Maximum number of results to retrieve in each page. If a limit is not provided, default is 50.
+ name: page_size
+ - defaultValue: '0'
+ description: Page number.
+ name: page
+ - defaultValue: '50'
+ description: Number of total results to return.
+ name: limit
+ - description: Used to filter the data by the team the user belongs to. If you provide this the query returns matching entries plus the policies without a team.
+ name: team_id
+ description: Get the policy device inactivity list.
+ name: zimperium-policy-device-inactivity-list
+ outputs:
+ - contextPath: Zimperium.PolicyDeviceInactivity.teamId
+ description: The team ID for the policy device inactivity.
+ type: String
+ - contextPath: Zimperium.PolicyDeviceInactivity.id
+ description: The policy device inactivity ID.
+ type: String
+ - contextPath: Zimperium.PolicyDeviceInactivity.name
+ description: The name of the policy device inactivity list.
+ type: String
+ - arguments:
+ - description: The identifier of the policy. Can be retrieved using zimperium-policy-device-inactivity-list.
+ name: policy_id
+ required: true
+ description: Get policy device inactivity.
+ name: zimperium-policy-device-inactivity-get
+ outputs:
+ - contextPath: Zimperium.PolicyDeviceInactivity.id
+ description: The policy device inactivity ID.
+ type: String
+ - contextPath: Zimperium.PolicyDeviceInactivity.accountId
+ description: The account identifier.
+ type: String
+ - contextPath: Zimperium.PolicyDeviceInactivity.created
+ description: The date and time the policy was created.
+ type: Date
+ - contextPath: Zimperium.PolicyDeviceInactivity.groups.id
+ description: The group ID.
+ type: String
+ - contextPath: Zimperium.PolicyDeviceInactivity.groups.name
+ description: The group name.
+ type: String
+ - contextPath: Zimperium.PolicyDeviceInactivity.inactiveAppSettings.enabled
+ description: Whether the app settings inactivity is enabled.
+ type: Boolean
+ - contextPath: Zimperium.PolicyDeviceInactivity.inactiveAppSettings.maxWarningsCount
+ description: The maximum number of warnings that can be issued for an app.
+ type: Number
+ - contextPath: Zimperium.PolicyDeviceInactivity.inactiveAppSettings
+ description: The inactive app settings.
+ type: Boolean
+ - contextPath: Zimperium.PolicyDeviceInactivity.modified
+ description: The policy modified date.
+ type: Date
+ - contextPath: Zimperium.PolicyDeviceInactivity.name
+ description: The name of the policy.
+ type: String
+ - contextPath: Zimperium.PolicyDeviceInactivity.pendingActivationSettings.enabled
+ description: Whether the device's policy setting is enabled or not.
+ type: Boolean
+ - contextPath: Zimperium.PolicyDeviceInactivity.pendingActivationSettings.maxWarningsCount
+ description: The maximum number of warnings that can be issued for the policy.
+ type: Number
+ - contextPath: Zimperium.PolicyDeviceInactivity.pendingActivationSettings.sendEmailAndroid
+ description: Whether to send an email.
+ type: Boolean
+ - contextPath: Zimperium.PolicyDeviceInactivity.pendingActivationSettings.sendEmailIos
+ description: Whether to send an email.
+ type: Boolean
+ - contextPath: Zimperium.PolicyDeviceInactivity.pendingActivationSettings.timeBeforeWarningDisplayUnits
+ description: The time before the warning display.
+ type: String
+ - contextPath: Zimperium.PolicyDeviceInactivity.pendingActivationSettings.timeBeforeWarningSeconds
+ description: The time before the warning seconds.
+ type: Number
+ - contextPath: Zimperium.PolicyDeviceInactivity.pendingActivationSettings.timeBetweenWarningsDisplayUnits
+ description: The time interval between warning displays.
+ type: String
+ - contextPath: Zimperium.PolicyDeviceInactivity.pendingActivationSettings.timeBetweenWarningsSeconds
+ description: The time in seconds between warnings.
+ type: Number
+ - contextPath: Zimperium.PolicyDeviceInactivity.teamId
+ description: The team ID for the policy device inactivity.
+ type: String
+ dockerimage: demisto/python3:3.10.13.87159
+ isfetch: true
+ runonce: false
+ script: '-'
+ subtype: python3
+ type: python
+tests:
+- Zimperiumv2-TestPlaybook
+defaultmapperin: Zimperium v2 - Incoming Mapper
diff --git a/Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2_description.md b/Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2_description.md
new file mode 100644
index 000000000000..4583e78e9b41
--- /dev/null
+++ b/Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2_description.md
@@ -0,0 +1,14 @@
+To obtain the Client ID and Client Secret, follow these steps:
+
+1. Log in to the [Zimperium application](https://mtduat.zimperium.com/)
+2. Click the settings gear located in the top right corner.
+3. Navigate to the **Authorizations** tab.
+4. Click **Generate API Key**.
+5. Associate the API key with the relevant teams.
+6. Specify the permissions for the API Key. This integration utilizes **view** permissions for the following resources: Teams, Users, App Inventory, App Settings, Devices, Phishing, Policies, and Threats.
+
+**Note**: Only an Account Admin user is authorized to generate an API Key.
+
+
+
+
diff --git a/Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2_image.png b/Packs/Zimperium/Integrations/ZimperiumV2/ZimperiumV2_image.png
new file mode 100644
index 0000000000000000000000000000000000000000..a74959d4c8063c1a06d038238bda6c349a98a82f
GIT binary patch
literal 3297
zcmbVP`8yMiA9t)+@|`)8V>TZm=Uh2In1vj3HOCy0Ia&!L$0VAOtD$mVk(?!B7$cOU
z=EG-lfpC
z|Iyqk$P@?1+3G7u)2mUOI~ZW5)MfGG`vP1fOl}#M`^9g#4ywF7|G6bjTI^d|A?4x5IO^?K%UkueliYVFn!c3w
z-x;fj&Uc9y?>*)UZVYUZZ5or!@#G8Fk4U
z0N8n3uv{|W_l^Tm2T
zg_PJL11_Js=)wK?nG#K{Yiry6_07fSrJ1uEByTdteO)yT#3i+3g#-yWl=beZ!Ssug
z7%@off8crNVT80~c`(BjMrgFT1`%Y~BDGN4+e)%x(+3*h9aALRCG$5B
zEcKjK{9^4Gfh=YGWg>RVKtU(zJ?7`+L9`UO(+uf!9lz&3c$A$yoc?BNtAx)OB6s6=
z{n5i4F469H9E;wof<0}KE?|bpL6kj6VAcOeK)Gi1B*B)20
zp1{sE8BHHhzCfC*9so`hE?!;M|FQU~F><#&gMz9^&XPH|vVQ>#C0v#ml{A!ODhUm#
zeu&FiKNO?x>V%ZdFOv_X#BfrnN~$zdI+`k9Rv^*DSFl|`@Or69ICIC=C{bV2UAHu?
zcPzX<6St!@w6RYp3;jHca2k<2A^K0B@1Nn4N30nW_0$q2$}H1Y
zI=z8y^QBGgy1O263EjY{Q*J2<1ev$HRop2*ZZo$4B2(!p8_%IY@;R?>uWLQYHCHH}
zZpFCY>Zsc_F#=x2xEcG$xY+BCwVmI;C{Fw>CnCm|qdmQEkPMR8{dmHPzO^l~LH)o4)J}+ky%GIra3HFw+WQqftL_E(f9#!@}?ud5UW_mbf)XisQt
z+sVC(i?5I&hC$i2WG9Cn3{!jVw7Fzs5Ia^O_G{95*K}
z;&u8i>6ZiIR2}<#*ZEaY>LoqgS(=Q2ZT;fAPnm!I8xRleiAzUTncP^lEAmEGc)<`z
zGo->oZPlGsGd#U$auT)kE@C=lMv)-PH6Hw&8(=1?@oHo3Obb`&iF@&5D;7V|Vb$b6
zHyvz90jyZ9yEzBWfmD3NkrfkLws?Q&GFYzqQYP2#AzTV&H_Da)&O8YmWb1&B^fahT
zj47Vvuj1X#8@&~0%w9V;ZZ@ldj~*r4TNj~_9YR^pS`FYoM_+b!#tuDcj(Sbj>v3G4
zO{(u*Js3vpq>~XrwMQ#kn^LV~t-}%lZhY*Xk}%&%qHkg1HNRAA{k+VYQOx5iIKUpe
zY$5*TmFy2$xrbNluFi`74&0$bh7t*a2JTZ0-TjIAom#qWDhvLI&VEnUX&rOr$+%L3
zV~ZSn_V|bda>{bLijz~eDe#r|CAx#egXvx@nReSM;x?7_waTaMq*TX>iVJ_NqSiz@
zXb^sH6UBtPumV<7@#r1VZg}WkjZHPr*+_vm^_g;qUaH?r8y`iWFSL%^=BzBt-d*aB
zdNygC%E#jNkD0`fFY#>SR1eemU8EDPc1wY74m@=uU!QegySBusj6_$%5^{#4$v5i8
zol!3vJ(yOS7cy4JhoW8uZqcX3a)(=r4$C$!>`&yRJ%3`b+!|yZ)w<+{Q8xK{fzFa>
z+qour_h#Kh^RwHn_+LEG$M0Y8PK-|dq%=#}M2+StvV+3M-w!!Nnht+h3($^WL&T@J
z-Giu8gSEi2o$j}TKOudd(YD!7p2fRhs--vJQg?uo@A2a%=xoV8N$MD$R;W_uoR@#^
z>aWrlB4-k%Y%Kg*4&c2G5;iX7>YqOQW5->T%jWws1UM4;SiVlxO6N7WS2*#FYI-6G
z-u3$8+%K&=Vk)JWdk50gH*(*U@&-$B`Wn9N^OaWMZgrP6EAd{baneyZO;alROzY8j
zTR*_3B`)Z@O*9~K)r#XoVtbQi+oi!<)IMh80R$o)nky1_I;in`K-fTs-t>hId+Gi}
zwgMjKq#jMvyHO^OUjilJACmP&D@bfwOizA}eQqM#Kf{m=WQu$}n9GqJY4ljDf{O=H
zrq!Ky-g&Ow53$~F71vzvpZr)>uvBV06TFD%6k7Ewo5!}$IGSR03ry7MHQGZC*3{ke
zFN@v?0=|Fg26`xbk#(B(yqlcu)G7>g9!bE;k71B0R)Da9nCbA5?Epnzeoi!O|;dPt3wFG0xxXwM;fXj7+KsY{JK1M}J(nV4rL~jkxlez{YnW?=J
zVtwV`Z*=~oNgf?tFC$)mgi#usHd%OOHiK*=_iwyvKQ(F3H5HVztds;bO&uVK_L#?r~=BQnB12#Xt9u2p!wYvl+^v
zQ+FpRKUYDh^)UopS~msg7drXIK!xU4S!ky@!(6U!H*Omt>;prctl5J#Lul8-$2Wdk
zghAgVY@ePf#OmP`zvU{@{G$33F@uEh&B0$b`>hB_PP|RE_CMcw`l~#tRco~!TgA~U
zqb>UX;A0PAlp1l@*tX*lWoT|yVqBdMojZ*>e~rh}QpCK~uwRgS>H(-=Q&l$$$g
z&!YOfOM{cb=?>i02AMPY+Y2QTv|#U|{Pfv}e9=N9zm&4l9A1$Qj_U#x*8<-*3|J{z
zEL|gnWaLYpLo0mgCK>WB@v`&gSi_6Dd{D;|QvOy^Cr?R0#VkKFL?*nIzCA!<{|k|-
zV6sfM3f)wiBGf+2_?pGmcia*qZP-_3bi+!8ZV7$R8x)hTR^5tjs_IGu4aX@}Nh)X{EaXCGL8oAdIy%K*V
l@ERT^VEI4b92{`W-?lwnA#>Sx
Date: Sun, 18 Feb 2024 15:11:51 +0200
Subject: [PATCH 005/272] Upgrade `python3` docker images 0-20 coverage rate
(#32446)
* update docker
* updateRN
* revert RN
* update RN
* Bump pack from version Base to 1.33.31.
* update RN after merge master
* Bump pack from version ArcherRSA to 1.2.16.
---------
Co-authored-by: Content Bot
---
Packs/ArcherRSA/ReleaseNotes/1_2_16.md | 6 ++
.../ArcherCreateIncidentExample.yml | 2 +-
Packs/ArcherRSA/pack_metadata.json | 2 +-
.../Attlasian_IAM/Attlasian_IAM.yml | 2 +-
Packs/Attlasian/ReleaseNotes/1_1_15.md | 6 ++
Packs/Attlasian/pack_metadata.json | 2 +-
Packs/Base/ReleaseNotes/1_33_31.md | 9 +++
.../DBotShowClusteringModelInfo.yml | 2 +-
.../DeleteIndicatorRelationships.yml | 2 +-
Packs/Base/pack_metadata.json | 2 +-
Packs/BigFix/Integrations/BigFix/BigFix.yml | 2 +-
Packs/BigFix/ReleaseNotes/1_0_15.md | 6 ++
Packs/BigFix/pack_metadata.json | 4 +-
.../BluecatAddressManager.yml | 2 +-
.../ReleaseNotes/1_1_13.md | 6 ++
.../BluecatAddressManager/pack_metadata.json | 2 +-
Packs/C2sec/Integrations/C2sec/C2sec.yml | 2 +-
Packs/C2sec/ReleaseNotes/1_0_11.md | 6 ++
Packs/C2sec/pack_metadata.json | 2 +-
Packs/CIRCL/Integrations/CIRCL/CIRCL.yml | 2 +-
Packs/CIRCL/ReleaseNotes/1_0_22.md | 6 ++
Packs/CIRCL/pack_metadata.json | 2 +-
Packs/Campaign/ReleaseNotes/3_4_4.md | 12 +++
.../ShowCampaignUniqueRecipients.yml | 2 +-
.../ShowCampaignUniqueSenders.yml | 2 +-
.../ShowNumberOfCampaignIncidents.yml | 2 +-
Packs/Campaign/pack_metadata.json | 2 +-
.../ReleaseNotes/2_1_45.md | 9 +++
.../Scripts/CBFindIP/CBFindIP.yml | 2 +-
.../CBLiveGetFile_V2/CBLiveGetFile_V2.yml | 2 +-
.../pack_metadata.json | 2 +-
Packs/Change_Management/ReleaseNotes/1_0_4.md | 6 ++
.../Scripts/IncidentState/IncidentState.yml | 2 +-
Packs/Change_Management/pack_metadata.json | 2 +-
Packs/Cherwell/ReleaseNotes/1_0_19.md | 21 +++++
.../CherwellCreateIncident.yml | 2 +-
.../CherwellGetIncident.yml | 2 +-
.../CherwellIncidentOwnTask.yml | 2 +-
.../CherwellIncidentUnlinkTask.yml | 2 +-
.../CherwellQueryIncidents.yml | 2 +-
.../CherwellUpdateIncident.yml | 2 +-
Packs/Cherwell/pack_metadata.json | 2 +-
.../ReleaseNotes/1_0_15.md | 9 +++
.../XCloudProviderWidget.yml | 2 +-
.../displayCloudIndicators.yml | 2 +-
.../CloudIncidentResponse/pack_metadata.json | 2 +-
Packs/CommonScripts/ReleaseNotes/1_13_40.md | 78 +++++++++++++++++++
.../AddDBotScoreToContext.yml | 2 +-
.../AssignToMeButton/AssignToMeButton.yml | 2 +-
.../Scripts/CVSSCalculator/CVSSCalculator.yml | 2 +-
.../CalculateTimeDifference.yml | 2 +-
.../CloseInvestigationAsDuplicate.yml | 2 +-
.../CompareIncidentsLabels.yml | 2 +-
.../ContextContains/ContextContains.yml | 2 +-
.../ConvertDateToUTC/ConvertDateToUTC.yml | 2 +-
.../CopyContextToField/CopyContextToField.yml | 2 +-
.../Scripts/DemistoVersion/DemistoVersion.yml | 2 +-
.../Scripts/EncodeToAscii/EncodeToAscii.yml | 2 +-
.../ExportContextToJSONFile.yml | 2 +-
.../GenerateRandomString.yml | 2 +-
.../GenerateSummaryReportButton.yml | 2 +-
.../Scripts/IPToHost/IPToHost.yml | 2 +-
.../IndicatorMaliciousRatioCalculation.yml | 2 +-
.../IsDomainInternal/IsDomainInternal.yml | 2 +-
.../Scripts/IsIPPrivate/IsIPPrivate.yml | 2 +-
.../LinkIncidentsButton.yml | 2 +-
.../LinkIncidentsWithRetry.yml | 2 +-
.../LoadJSONFileToContext.yml | 2 +-
.../MarkAsEvidenceByTag.yml | 2 +-
.../PopulateCriticalAssets.yml | 2 +-
.../Scripts/SetDateField/SetDateField.yml | 2 +-
.../displayUtilitiesResults.yml | 2 +-
Packs/CommonScripts/pack_metadata.json | 2 +-
.../ContentManagement/ReleaseNotes/1_2_18.md | 6 ++
.../Scripts/GetPrBranches/GetPrBranches.yml | 2 +-
Packs/ContentManagement/pack_metadata.json | 2 +-
.../Integrations/CounterTack/CounterTack.yml | 2 +-
Packs/CounterTack/ReleaseNotes/1_0_9.md | 6 ++
Packs/CounterTack/pack_metadata.json | 2 +-
.../CrowdStrikeOpenAPI/CrowdStrikeOpenAPI.yml | 2 +-
.../CrowdStrikeOpenAPI/ReleaseNotes/1_0_18.md | 6 ++
Packs/CrowdStrikeOpenAPI/pack_metadata.json | 2 +-
Packs/CuckooSandbox/ReleaseNotes/1_1_5.md | 6 ++
.../CuckooDisplayReport.yml | 2 +-
Packs/CuckooSandbox/pack_metadata.json | 2 +-
.../DBotTruthBombs/DBotTruthBombs.yml | 2 +-
Packs/DBotTruthBombs/ReleaseNotes/1_0_8.md | 12 +++
.../Scripts/FactsAboutYou/FactsAboutYou.yml | 2 +-
Packs/DBotTruthBombs/pack_metadata.json | 2 +-
.../Integrations/EasyVista/EasyVista.yml | 2 +-
Packs/EasyVista/ReleaseNotes/1_0_9.md | 6 ++
Packs/EasyVista/pack_metadata.json | 2 +-
.../FeedAlienVaultReputation.yml | 2 +-
Packs/FeedAlienVault/ReleaseNotes/1_1_30.md | 6 ++
Packs/FeedAlienVault/pack_metadata.json | 2 +-
.../MajesticMillion/MajesticMillion.yml | 2 +-
.../ReleaseNotes/1_1_14.md | 6 ++
Packs/FeedMajesticMillion/pack_metadata.json | 2 +-
.../FeedTorExitAddresses.yml | 2 +-
.../ReleaseNotes/1_0_9.md | 6 ++
Packs/FeedTorExitAddresses/pack_metadata.json | 2 +-
.../Feedsslabusech/Feedsslabusech.yml | 2 +-
Packs/Feedsslabusech/ReleaseNotes/1_1_26.md | 6 ++
Packs/Feedsslabusech/pack_metadata.json | 2 +-
.../FidelisEndpoint/FidelisEndpoint.yml | 2 +-
Packs/FidelisEndpoint/ReleaseNotes/1_0_6.md | 6 ++
Packs/FidelisEndpoint/pack_metadata.json | 2 +-
.../ReleaseNotes/1_2_61.md | 12 +++
.../FiltersAndTransformers/Scripts/DT/DT.yml | 2 +-
.../GetValuesOfMultipleFIelds.yml | 2 +-
.../Scripts/StripChar/StripChar.yml | 2 +-
.../FiltersAndTransformers/pack_metadata.json | 2 +-
.../Integrations/Forescout/Forescout.yml | 2 +-
Packs/Forescout/ReleaseNotes/1_0_9.md | 6 ++
Packs/Forescout/pack_metadata.json | 2 +-
.../Integrations/ImpervaWAF/ImpervaWAF.yml | 2 +-
Packs/Imperva_WAF/ReleaseNotes/1_0_18.md | 6 ++
Packs/Imperva_WAF/pack_metadata.json | 2 +-
.../Integrations/IvantiHeat/IvantiHeat.yml | 2 +-
Packs/IvantiHeat/ReleaseNotes/1_0_10.md | 18 +++++
.../IvantiHeatCloseIncidentExample.yml | 2 +-
.../IvantiHeatCreateIncidentExample.yml | 2 +-
.../IvantiHeatCreateProblemExample.yml | 2 +-
Packs/IvantiHeat/pack_metadata.json | 2 +-
.../LogRhythmRest/LogRhythmRest.yml | 2 +-
Packs/LogRhythmRest/ReleaseNotes/2_0_22.md | 6 ++
Packs/LogRhythmRest/pack_metadata.json | 2 +-
Packs/ML/ReleaseNotes/1_4_10.md | 6 ++
.../ExtendQueryBasedOnPhishingLabels.yml | 2 +-
Packs/ML/pack_metadata.json | 2 +-
.../ReleaseNotes/1_6_37.md | 27 +++++++
...reachResponseCompletedTasksCountWidget.yml | 2 +-
...achResponseEradicationTasksCountWidget.yml | 2 +-
...dBreachResponseHuntingTasksCountWidget.yml | 2 +-
...eachResponseMitigationTasksCountWidget.yml | 2 +-
...reachResponseRemainingTasksCountWidget.yml | 2 +-
...achResponseRemediationTasksCountWidget.yml | 2 +-
...reachResponseTotalIndicatorCountWidget.yml | 2 +-
...pidBreachResponseTotalTasksCountWidget.yml | 2 +-
.../pack_metadata.json | 2 +-
.../ReleaseNotes/4_5_17.md | 9 +++
.../MS365DefenderCountIncidentCategories.yml | 2 +-
.../MS365DefenderUserListToTable.yml | 2 +-
Packs/Microsoft365Defender/pack_metadata.json | 2 +-
.../PrismaAccessEgressIPFeed.yml | 2 +-
Packs/PrismaAccess/ReleaseNotes/2_1_4.md | 6 ++
Packs/PrismaAccess/pack_metadata.json | 2 +-
Packs/ProofpointTAP/ReleaseNotes/1_2_11.md | 9 +++
.../ProofpointTAPMostAttackedUsers.yml | 2 +-
.../ProofpointTapTopClickers.yml | 2 +-
Packs/ProofpointTAP/pack_metadata.json | 2 +-
Packs/Salesforce/ReleaseNotes/2_0_23.md | 9 +++
.../GenerateProfileId/GenerateProfileId.yml | 2 +-
.../GenerateTimeZone/GenerateTimeZone.yml | 2 +-
Packs/Salesforce/pack_metadata.json | 2 +-
Packs/ServiceNow/ReleaseNotes/2_5_53.md | 6 ++
.../ServiceNowIncidentStatus.yml | 2 +-
Packs/ServiceNow/pack_metadata.json | 2 +-
.../Integrations/Slack_IAM/Slack_IAM.yml | 2 +-
Packs/Slack/ReleaseNotes/3_4_5.md | 6 ++
Packs/Slack/pack_metadata.json | 2 +-
.../Integrations/Telegram/Telegram.yml | 2 +-
Packs/Telegram/ReleaseNotes/1_0_8.md | 6 ++
Packs/Telegram/pack_metadata.json | 2 +-
.../ThreatIntelReports/ReleaseNotes/1_0_13.md | 9 +++
.../PublishThreatIntelReport.yml | 2 +-
.../UnpublishThreatIntelReport.yml | 2 +-
Packs/ThreatIntelReports/pack_metadata.json | 2 +-
.../Integrations/ThreatMiner/ThreatMiner.yml | 2 +-
Packs/ThreatMiner/ReleaseNotes/1_0_13.md | 6 ++
Packs/ThreatMiner/pack_metadata.json | 2 +-
Packs/Troubleshoot/ReleaseNotes/2_0_18.md | 15 ++++
.../TroubleshootAggregateResults.yml | 2 +-
.../TroubleshootExecuteCommand.yml | 2 +-
.../TroubleshootGetCommandandArgs.yml | 2 +-
.../TroubleshootInstanceField.yml | 2 +-
Packs/Troubleshoot/pack_metadata.json | 2 +-
.../WhatIsMyBrowser/WhatIsMyBrowser.yml | 2 +-
Packs/WhatIsMyBrowser/ReleaseNotes/1_0_11.md | 6 ++
Packs/WhatIsMyBrowser/pack_metadata.json | 2 +-
180 files changed, 559 insertions(+), 139 deletions(-)
create mode 100644 Packs/ArcherRSA/ReleaseNotes/1_2_16.md
create mode 100644 Packs/Attlasian/ReleaseNotes/1_1_15.md
create mode 100644 Packs/Base/ReleaseNotes/1_33_31.md
create mode 100644 Packs/BigFix/ReleaseNotes/1_0_15.md
create mode 100644 Packs/BluecatAddressManager/ReleaseNotes/1_1_13.md
create mode 100644 Packs/C2sec/ReleaseNotes/1_0_11.md
create mode 100644 Packs/CIRCL/ReleaseNotes/1_0_22.md
create mode 100644 Packs/Campaign/ReleaseNotes/3_4_4.md
create mode 100644 Packs/Carbon_Black_Enterprise_Response/ReleaseNotes/2_1_45.md
create mode 100644 Packs/Change_Management/ReleaseNotes/1_0_4.md
create mode 100644 Packs/Cherwell/ReleaseNotes/1_0_19.md
create mode 100644 Packs/CloudIncidentResponse/ReleaseNotes/1_0_15.md
create mode 100644 Packs/CommonScripts/ReleaseNotes/1_13_40.md
create mode 100644 Packs/ContentManagement/ReleaseNotes/1_2_18.md
create mode 100644 Packs/CounterTack/ReleaseNotes/1_0_9.md
create mode 100644 Packs/CrowdStrikeOpenAPI/ReleaseNotes/1_0_18.md
create mode 100644 Packs/CuckooSandbox/ReleaseNotes/1_1_5.md
create mode 100644 Packs/DBotTruthBombs/ReleaseNotes/1_0_8.md
create mode 100644 Packs/EasyVista/ReleaseNotes/1_0_9.md
create mode 100644 Packs/FeedAlienVault/ReleaseNotes/1_1_30.md
create mode 100644 Packs/FeedMajesticMillion/ReleaseNotes/1_1_14.md
create mode 100644 Packs/FeedTorExitAddresses/ReleaseNotes/1_0_9.md
create mode 100644 Packs/Feedsslabusech/ReleaseNotes/1_1_26.md
create mode 100644 Packs/FidelisEndpoint/ReleaseNotes/1_0_6.md
create mode 100644 Packs/FiltersAndTransformers/ReleaseNotes/1_2_61.md
create mode 100644 Packs/Forescout/ReleaseNotes/1_0_9.md
create mode 100644 Packs/Imperva_WAF/ReleaseNotes/1_0_18.md
create mode 100644 Packs/IvantiHeat/ReleaseNotes/1_0_10.md
create mode 100644 Packs/LogRhythmRest/ReleaseNotes/2_0_22.md
create mode 100644 Packs/ML/ReleaseNotes/1_4_10.md
create mode 100644 Packs/MajorBreachesInvestigationandResponse/ReleaseNotes/1_6_37.md
create mode 100644 Packs/Microsoft365Defender/ReleaseNotes/4_5_17.md
create mode 100644 Packs/PrismaAccess/ReleaseNotes/2_1_4.md
create mode 100644 Packs/ProofpointTAP/ReleaseNotes/1_2_11.md
create mode 100644 Packs/Salesforce/ReleaseNotes/2_0_23.md
create mode 100644 Packs/ServiceNow/ReleaseNotes/2_5_53.md
create mode 100644 Packs/Slack/ReleaseNotes/3_4_5.md
create mode 100644 Packs/Telegram/ReleaseNotes/1_0_8.md
create mode 100644 Packs/ThreatIntelReports/ReleaseNotes/1_0_13.md
create mode 100644 Packs/ThreatMiner/ReleaseNotes/1_0_13.md
create mode 100644 Packs/Troubleshoot/ReleaseNotes/2_0_18.md
create mode 100644 Packs/WhatIsMyBrowser/ReleaseNotes/1_0_11.md
diff --git a/Packs/ArcherRSA/ReleaseNotes/1_2_16.md b/Packs/ArcherRSA/ReleaseNotes/1_2_16.md
new file mode 100644
index 000000000000..8a5060008b0d
--- /dev/null
+++ b/Packs/ArcherRSA/ReleaseNotes/1_2_16.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### ArcherCreateIncidentExample
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/ArcherRSA/Scripts/ArcherCreateIncidentExample/ArcherCreateIncidentExample.yml b/Packs/ArcherRSA/Scripts/ArcherCreateIncidentExample/ArcherCreateIncidentExample.yml
index d8908f23e4cd..116a97870887 100644
--- a/Packs/ArcherRSA/Scripts/ArcherCreateIncidentExample/ArcherCreateIncidentExample.yml
+++ b/Packs/ArcherRSA/Scripts/ArcherCreateIncidentExample/ArcherCreateIncidentExample.yml
@@ -33,7 +33,7 @@ script: '-'
subtype: python3
timeout: '0'
type: python
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
skipprepare:
diff --git a/Packs/ArcherRSA/pack_metadata.json b/Packs/ArcherRSA/pack_metadata.json
index d60048714851..d98608e5ff24 100644
--- a/Packs/ArcherRSA/pack_metadata.json
+++ b/Packs/ArcherRSA/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "RSA Archer",
"description": "The RSA Archer GRC Platform provides a common foundation for managing policies, controls, risks, assessments and deficiencies across lines of business.",
"support": "xsoar",
- "currentVersion": "1.2.15",
+ "currentVersion": "1.2.16",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Attlasian/Integrations/Attlasian_IAM/Attlasian_IAM.yml b/Packs/Attlasian/Integrations/Attlasian_IAM/Attlasian_IAM.yml
index 259c1984516a..f2ab47579153 100644
--- a/Packs/Attlasian/Integrations/Attlasian_IAM/Attlasian_IAM.yml
+++ b/Packs/Attlasian/Integrations/Attlasian_IAM/Attlasian_IAM.yml
@@ -238,7 +238,7 @@ script:
type: String
- description: Retrieves a User Profile schema, which holds all of the user fields within the application. Used for outgoing-mapping through the Get Schema option.
name: get-mapping-fields
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
ismappable: true
isremotesyncout: true
script: '-'
diff --git a/Packs/Attlasian/ReleaseNotes/1_1_15.md b/Packs/Attlasian/ReleaseNotes/1_1_15.md
new file mode 100644
index 000000000000..c83a3cb90369
--- /dev/null
+++ b/Packs/Attlasian/ReleaseNotes/1_1_15.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Atlassian IAM
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Attlasian/pack_metadata.json b/Packs/Attlasian/pack_metadata.json
index e1abca28981d..5a3a2d901a08 100644
--- a/Packs/Attlasian/pack_metadata.json
+++ b/Packs/Attlasian/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Atlassian IAM",
"description": "Atlassian IAM Integration allows the customers to do the generic ILM management operations such as create, update, delete, etc.",
"support": "xsoar",
- "currentVersion": "1.1.14",
+ "currentVersion": "1.1.15",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Base/ReleaseNotes/1_33_31.md b/Packs/Base/ReleaseNotes/1_33_31.md
new file mode 100644
index 000000000000..b7a6e3971e62
--- /dev/null
+++ b/Packs/Base/ReleaseNotes/1_33_31.md
@@ -0,0 +1,9 @@
+
+#### Scripts
+
+##### DeleteIndicatorRelationships
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### DBotShowClusteringModelInfo
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Base/Scripts/DBotShowClusteringModelInfo/DBotShowClusteringModelInfo.yml b/Packs/Base/Scripts/DBotShowClusteringModelInfo/DBotShowClusteringModelInfo.yml
index 190b39bd285b..89e4ee18a040 100644
--- a/Packs/Base/Scripts/DBotShowClusteringModelInfo/DBotShowClusteringModelInfo.yml
+++ b/Packs/Base/Scripts/DBotShowClusteringModelInfo/DBotShowClusteringModelInfo.yml
@@ -29,6 +29,6 @@ type: python
fromversion: 6.2.0
tests:
- No tests (auto formatted)
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
marketplaces:
- xsoar
diff --git a/Packs/Base/Scripts/DeleteIndicatorRelationships/DeleteIndicatorRelationships.yml b/Packs/Base/Scripts/DeleteIndicatorRelationships/DeleteIndicatorRelationships.yml
index e7b94c5032cd..390d70004561 100644
--- a/Packs/Base/Scripts/DeleteIndicatorRelationships/DeleteIndicatorRelationships.yml
+++ b/Packs/Base/Scripts/DeleteIndicatorRelationships/DeleteIndicatorRelationships.yml
@@ -15,7 +15,7 @@ tags:
timeout: '0'
type: python
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
fromversion: 6.2.0
tests:
- Relationships scripts - Test
diff --git a/Packs/Base/pack_metadata.json b/Packs/Base/pack_metadata.json
index 875097b5a2e5..c303b18714ef 100644
--- a/Packs/Base/pack_metadata.json
+++ b/Packs/Base/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Base",
"description": "The base pack for Cortex XSOAR.",
"support": "xsoar",
- "currentVersion": "1.33.30",
+ "currentVersion": "1.33.31",
"author": "Cortex XSOAR",
"serverMinVersion": "6.0.0",
"url": "https://www.paloaltonetworks.com/cortex",
diff --git a/Packs/BigFix/Integrations/BigFix/BigFix.yml b/Packs/BigFix/Integrations/BigFix/BigFix.yml
index db8f0e25d94f..85c30cbe6c98 100644
--- a/Packs/BigFix/Integrations/BigFix/BigFix.yml
+++ b/Packs/BigFix/Integrations/BigFix/BigFix.yml
@@ -478,5 +478,5 @@ script:
script: '-'
subtype: python3
type: python
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
fromversion: 5.0.0
diff --git a/Packs/BigFix/ReleaseNotes/1_0_15.md b/Packs/BigFix/ReleaseNotes/1_0_15.md
new file mode 100644
index 000000000000..2e4f58b4f67e
--- /dev/null
+++ b/Packs/BigFix/ReleaseNotes/1_0_15.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### BigFix
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/BigFix/pack_metadata.json b/Packs/BigFix/pack_metadata.json
index 82adee64fa3b..894d103827f6 100644
--- a/Packs/BigFix/pack_metadata.json
+++ b/Packs/BigFix/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "HCL BigFix",
"description": "HCL BigFix Patch provides an automated, simplified patching process that is administered from a single console.",
"support": "xsoar",
- "currentVersion": "1.0.14",
+ "currentVersion": "1.0.15",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
@@ -17,4 +17,4 @@
"xsoar",
"marketplacev2"
]
-}
+}
\ No newline at end of file
diff --git a/Packs/BluecatAddressManager/Integrations/BluecatAddressManager/BluecatAddressManager.yml b/Packs/BluecatAddressManager/Integrations/BluecatAddressManager/BluecatAddressManager.yml
index 4b8aa6b092e7..60ca23d554eb 100644
--- a/Packs/BluecatAddressManager/Integrations/BluecatAddressManager/BluecatAddressManager.yml
+++ b/Packs/BluecatAddressManager/Integrations/BluecatAddressManager/BluecatAddressManager.yml
@@ -162,7 +162,7 @@ script:
- contextPath: BlueCat.AddressManager.Range.Parents.CIDR
description: Classless Inter-Domain Routing.
type: String
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/BluecatAddressManager/ReleaseNotes/1_1_13.md b/Packs/BluecatAddressManager/ReleaseNotes/1_1_13.md
new file mode 100644
index 000000000000..ff9e050e0f23
--- /dev/null
+++ b/Packs/BluecatAddressManager/ReleaseNotes/1_1_13.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Bluecat Address Manager
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/BluecatAddressManager/pack_metadata.json b/Packs/BluecatAddressManager/pack_metadata.json
index fc2e8db67b8d..41fbbce4aab6 100644
--- a/Packs/BluecatAddressManager/pack_metadata.json
+++ b/Packs/BluecatAddressManager/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Bluecat Address Manager",
"description": "Use the BlueCat Address Manager integration to enrich IP addresses and manage response policies.",
"support": "xsoar",
- "currentVersion": "1.1.12",
+ "currentVersion": "1.1.13",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/C2sec/Integrations/C2sec/C2sec.yml b/Packs/C2sec/Integrations/C2sec/C2sec.yml
index 3f71242db8b9..fa6c5eee2f75 100644
--- a/Packs/C2sec/Integrations/C2sec/C2sec.yml
+++ b/Packs/C2sec/Integrations/C2sec/C2sec.yml
@@ -199,6 +199,6 @@ script:
type: string
description: Query Data for specific component for companies in the portfolio
runonce: false
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
tests:
- No tests (auto formatted)
diff --git a/Packs/C2sec/ReleaseNotes/1_0_11.md b/Packs/C2sec/ReleaseNotes/1_0_11.md
new file mode 100644
index 000000000000..95d42ee2d45f
--- /dev/null
+++ b/Packs/C2sec/ReleaseNotes/1_0_11.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### C2sec irisk
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/C2sec/pack_metadata.json b/Packs/C2sec/pack_metadata.json
index d760b1599f8a..4696f06328fa 100644
--- a/Packs/C2sec/pack_metadata.json
+++ b/Packs/C2sec/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "C2sec irisk",
"description": "Understand Your Cyber Exposure as Easy as a Google Search",
"support": "xsoar",
- "currentVersion": "1.0.10",
+ "currentVersion": "1.0.11",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/CIRCL/Integrations/CIRCL/CIRCL.yml b/Packs/CIRCL/Integrations/CIRCL/CIRCL.yml
index 649fdbd4b2eb..ebd81ed8fcbe 100644
--- a/Packs/CIRCL/Integrations/CIRCL/CIRCL.yml
+++ b/Packs/CIRCL/Integrations/CIRCL/CIRCL.yml
@@ -116,7 +116,7 @@ script:
script: '-'
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
tests:
- CirclIntegrationTest
fromversion: 5.0.0
diff --git a/Packs/CIRCL/ReleaseNotes/1_0_22.md b/Packs/CIRCL/ReleaseNotes/1_0_22.md
new file mode 100644
index 000000000000..932797c6547d
--- /dev/null
+++ b/Packs/CIRCL/ReleaseNotes/1_0_22.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### CIRCL
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/CIRCL/pack_metadata.json b/Packs/CIRCL/pack_metadata.json
index 412ffa58cf16..836c143c69f5 100644
--- a/Packs/CIRCL/pack_metadata.json
+++ b/Packs/CIRCL/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "CIRCL",
"description": "The Computer Incident Response Center Luxembourg (CIRCL) is a government-driven initiative designed to provide a systematic response facility to computer security threats and incidents.\nThis pack includes:\n# CIRCL Passive DNS which is a database storing historical DNS records from various resources.\n# CIRCL Passive SSL is a database storing historical X.509 certificates seen per IP address. The Passive SSL historical data is indexed per IP address.\n# CIRCL CVE Search, interface to search publicly known information from security vulnerabilities in software and hardware along with their corresponding exposures.",
"support": "xsoar",
- "currentVersion": "1.0.21",
+ "currentVersion": "1.0.22",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Campaign/ReleaseNotes/3_4_4.md b/Packs/Campaign/ReleaseNotes/3_4_4.md
new file mode 100644
index 000000000000..f659d3befc99
--- /dev/null
+++ b/Packs/Campaign/ReleaseNotes/3_4_4.md
@@ -0,0 +1,12 @@
+
+#### Scripts
+
+##### ShowCampaignUniqueSenders
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### ShowNumberOfCampaignIncidents
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### ShowCampaignUniqueRecipients
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Campaign/Scripts/ShowCampaignUniqueRecipients/ShowCampaignUniqueRecipients.yml b/Packs/Campaign/Scripts/ShowCampaignUniqueRecipients/ShowCampaignUniqueRecipients.yml
index 6dd22be988fc..652e08b0c8ed 100644
--- a/Packs/Campaign/Scripts/ShowCampaignUniqueRecipients/ShowCampaignUniqueRecipients.yml
+++ b/Packs/Campaign/Scripts/ShowCampaignUniqueRecipients/ShowCampaignUniqueRecipients.yml
@@ -10,7 +10,7 @@ comment: Displays the number of unique recipients of an email campaign.
enabled: true
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.0.0
tests:
diff --git a/Packs/Campaign/Scripts/ShowCampaignUniqueSenders/ShowCampaignUniqueSenders.yml b/Packs/Campaign/Scripts/ShowCampaignUniqueSenders/ShowCampaignUniqueSenders.yml
index f6f9864df48d..a447c60d67a7 100644
--- a/Packs/Campaign/Scripts/ShowCampaignUniqueSenders/ShowCampaignUniqueSenders.yml
+++ b/Packs/Campaign/Scripts/ShowCampaignUniqueSenders/ShowCampaignUniqueSenders.yml
@@ -11,7 +11,7 @@ enabled: true
scripttarget: 0
subtype: python3
fromversion: 6.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
tests:
- No tests (auto formatted)
diff --git a/Packs/Campaign/Scripts/ShowNumberOfCampaignIncidents/ShowNumberOfCampaignIncidents.yml b/Packs/Campaign/Scripts/ShowNumberOfCampaignIncidents/ShowNumberOfCampaignIncidents.yml
index 8dcd99f4ebf6..312af40b7e04 100644
--- a/Packs/Campaign/Scripts/ShowNumberOfCampaignIncidents/ShowNumberOfCampaignIncidents.yml
+++ b/Packs/Campaign/Scripts/ShowNumberOfCampaignIncidents/ShowNumberOfCampaignIncidents.yml
@@ -11,7 +11,7 @@ enabled: true
scripttarget: 0
subtype: python3
fromversion: 6.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
tests:
- No tests (auto formatted)
diff --git a/Packs/Campaign/pack_metadata.json b/Packs/Campaign/pack_metadata.json
index d04df1d315de..f77a831765ac 100644
--- a/Packs/Campaign/pack_metadata.json
+++ b/Packs/Campaign/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Phishing Campaign",
"description": "This pack can help you find related phishing, spam or other types of email incidents and characterize campaigns.",
"support": "xsoar",
- "currentVersion": "3.4.3",
+ "currentVersion": "3.4.4",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Carbon_Black_Enterprise_Response/ReleaseNotes/2_1_45.md b/Packs/Carbon_Black_Enterprise_Response/ReleaseNotes/2_1_45.md
new file mode 100644
index 000000000000..a55197e6ddbe
--- /dev/null
+++ b/Packs/Carbon_Black_Enterprise_Response/ReleaseNotes/2_1_45.md
@@ -0,0 +1,9 @@
+
+#### Scripts
+
+##### CBFindIP
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CBLiveGetFile_V2
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Carbon_Black_Enterprise_Response/Scripts/CBFindIP/CBFindIP.yml b/Packs/Carbon_Black_Enterprise_Response/Scripts/CBFindIP/CBFindIP.yml
index b138cca3409c..23af799d071a 100644
--- a/Packs/Carbon_Black_Enterprise_Response/Scripts/CBFindIP/CBFindIP.yml
+++ b/Packs/Carbon_Black_Enterprise_Response/Scripts/CBFindIP/CBFindIP.yml
@@ -48,4 +48,4 @@ tests:
dependson:
must: []
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
diff --git a/Packs/Carbon_Black_Enterprise_Response/Scripts/CBLiveGetFile_V2/CBLiveGetFile_V2.yml b/Packs/Carbon_Black_Enterprise_Response/Scripts/CBLiveGetFile_V2/CBLiveGetFile_V2.yml
index b2c78806a1f5..ee4e8b7308bb 100644
--- a/Packs/Carbon_Black_Enterprise_Response/Scripts/CBLiveGetFile_V2/CBLiveGetFile_V2.yml
+++ b/Packs/Carbon_Black_Enterprise_Response/Scripts/CBLiveGetFile_V2/CBLiveGetFile_V2.yml
@@ -105,7 +105,7 @@ tags:
- endpoint
timeout: '0'
type: python
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- No Test
dependson:
diff --git a/Packs/Carbon_Black_Enterprise_Response/pack_metadata.json b/Packs/Carbon_Black_Enterprise_Response/pack_metadata.json
index b19a774dec75..cb1d28a6e48a 100644
--- a/Packs/Carbon_Black_Enterprise_Response/pack_metadata.json
+++ b/Packs/Carbon_Black_Enterprise_Response/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Carbon Black Enterprise Response",
"description": "Query and respond with Carbon Black endpoint detection and response.",
"support": "xsoar",
- "currentVersion": "2.1.44",
+ "currentVersion": "2.1.45",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Change_Management/ReleaseNotes/1_0_4.md b/Packs/Change_Management/ReleaseNotes/1_0_4.md
new file mode 100644
index 000000000000..635d62ec67dd
--- /dev/null
+++ b/Packs/Change_Management/ReleaseNotes/1_0_4.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### IncidentState
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Change_Management/Scripts/IncidentState/IncidentState.yml b/Packs/Change_Management/Scripts/IncidentState/IncidentState.yml
index eec247ad1f25..2df66816c8e6 100644
--- a/Packs/Change_Management/Scripts/IncidentState/IncidentState.yml
+++ b/Packs/Change_Management/Scripts/IncidentState/IncidentState.yml
@@ -6,7 +6,7 @@ commonfields:
contentitemexportablefields:
contentitemfields:
fromServerVersion: ""
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: IncidentState
runas: DBotWeakRole
diff --git a/Packs/Change_Management/pack_metadata.json b/Packs/Change_Management/pack_metadata.json
index 8f4faa5fa1c0..5c6c4d3a6bae 100644
--- a/Packs/Change_Management/pack_metadata.json
+++ b/Packs/Change_Management/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Change Management",
"description": "If you use Pan-Os or Panorama as your enterprise firewall and Jira or ServiceNow as your enterprise ticketing system, this pack will assist you to perform a well coordinated and documented process.",
"support": "xsoar",
- "currentVersion": "1.0.3",
+ "currentVersion": "1.0.4",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Cherwell/ReleaseNotes/1_0_19.md b/Packs/Cherwell/ReleaseNotes/1_0_19.md
new file mode 100644
index 000000000000..1c90d783db39
--- /dev/null
+++ b/Packs/Cherwell/ReleaseNotes/1_0_19.md
@@ -0,0 +1,21 @@
+
+#### Scripts
+
+##### CherwellIncidentUnlinkTask
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CherwellIncidentOwnTask
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CherwellGetIncident
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CherwellCreateIncident
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CherwellQueryIncidents
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CherwellUpdateIncident
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Cherwell/Scripts/CherwellCreateIncident/CherwellCreateIncident.yml b/Packs/Cherwell/Scripts/CherwellCreateIncident/CherwellCreateIncident.yml
index ece46308df41..916fd07fdf9b 100644
--- a/Packs/Cherwell/Scripts/CherwellCreateIncident/CherwellCreateIncident.yml
+++ b/Packs/Cherwell/Scripts/CherwellCreateIncident/CherwellCreateIncident.yml
@@ -39,7 +39,7 @@ type: python
dependson:
must:
- Cherwell|||cherwell-create-business-object
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
subtype: python3
tests:
- Cherwell Example Scripts - test
diff --git a/Packs/Cherwell/Scripts/CherwellGetIncident/CherwellGetIncident.yml b/Packs/Cherwell/Scripts/CherwellGetIncident/CherwellGetIncident.yml
index dec5b58eae46..b0620a66019c 100644
--- a/Packs/Cherwell/Scripts/CherwellGetIncident/CherwellGetIncident.yml
+++ b/Packs/Cherwell/Scripts/CherwellGetIncident/CherwellGetIncident.yml
@@ -49,7 +49,7 @@ tags: [Cherwell]
dependson:
must:
- Cherwell|||cherwell-get-business-object
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
subtype: python3
tests:
- Cherwell Example Scripts - test
diff --git a/Packs/Cherwell/Scripts/CherwellIncidentOwnTask/CherwellIncidentOwnTask.yml b/Packs/Cherwell/Scripts/CherwellIncidentOwnTask/CherwellIncidentOwnTask.yml
index 5e66777d23f9..1a3823fb7c3b 100644
--- a/Packs/Cherwell/Scripts/CherwellIncidentOwnTask/CherwellIncidentOwnTask.yml
+++ b/Packs/Cherwell/Scripts/CherwellIncidentOwnTask/CherwellIncidentOwnTask.yml
@@ -10,7 +10,7 @@ commonfields:
id: CherwellIncidentOwnTask
version: -1
name: CherwellIncidentOwnTask
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
subtype: python3
script: '-'
timeout: '0'
diff --git a/Packs/Cherwell/Scripts/CherwellIncidentUnlinkTask/CherwellIncidentUnlinkTask.yml b/Packs/Cherwell/Scripts/CherwellIncidentUnlinkTask/CherwellIncidentUnlinkTask.yml
index 661191dc7dde..38d01554af2e 100644
--- a/Packs/Cherwell/Scripts/CherwellIncidentUnlinkTask/CherwellIncidentUnlinkTask.yml
+++ b/Packs/Cherwell/Scripts/CherwellIncidentUnlinkTask/CherwellIncidentUnlinkTask.yml
@@ -13,7 +13,7 @@ name: CherwellIncidentUnlinkTask
script: '-'
timeout: '0'
type: python
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
subtype: python3
tags: [Cherwell]
dependson:
diff --git a/Packs/Cherwell/Scripts/CherwellQueryIncidents/CherwellQueryIncidents.yml b/Packs/Cherwell/Scripts/CherwellQueryIncidents/CherwellQueryIncidents.yml
index 8809f0fa2605..da8b76a71abd 100644
--- a/Packs/Cherwell/Scripts/CherwellQueryIncidents/CherwellQueryIncidents.yml
+++ b/Packs/Cherwell/Scripts/CherwellQueryIncidents/CherwellQueryIncidents.yml
@@ -42,7 +42,7 @@ outputs:
script: '-'
timeout: '0'
type: python
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
subtype: python3
tests:
- Cherwell Example Scripts - test
diff --git a/Packs/Cherwell/Scripts/CherwellUpdateIncident/CherwellUpdateIncident.yml b/Packs/Cherwell/Scripts/CherwellUpdateIncident/CherwellUpdateIncident.yml
index 3ac9cadf5021..aca4fa261e2d 100644
--- a/Packs/Cherwell/Scripts/CherwellUpdateIncident/CherwellUpdateIncident.yml
+++ b/Packs/Cherwell/Scripts/CherwellUpdateIncident/CherwellUpdateIncident.yml
@@ -44,7 +44,7 @@ outputs:
script: '-'
timeout: '0'
type: python
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
subtype: python3
tests:
- Cherwell Example Scripts - test
diff --git a/Packs/Cherwell/pack_metadata.json b/Packs/Cherwell/pack_metadata.json
index f6828b4688a6..e8f3c92977b8 100644
--- a/Packs/Cherwell/pack_metadata.json
+++ b/Packs/Cherwell/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Cherwell",
"description": "Cloud-based IT service management solution",
"support": "xsoar",
- "currentVersion": "1.0.18",
+ "currentVersion": "1.0.19",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/CloudIncidentResponse/ReleaseNotes/1_0_15.md b/Packs/CloudIncidentResponse/ReleaseNotes/1_0_15.md
new file mode 100644
index 000000000000..08c50952ab59
--- /dev/null
+++ b/Packs/CloudIncidentResponse/ReleaseNotes/1_0_15.md
@@ -0,0 +1,9 @@
+
+#### Scripts
+
+##### XCloudProviderWidget
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### displayCloudIndicators
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/CloudIncidentResponse/Scripts/XCloudProviderWidget/XCloudProviderWidget.yml b/Packs/CloudIncidentResponse/Scripts/XCloudProviderWidget/XCloudProviderWidget.yml
index a107ede8c6ce..7c690d8a7bdd 100644
--- a/Packs/CloudIncidentResponse/Scripts/XCloudProviderWidget/XCloudProviderWidget.yml
+++ b/Packs/CloudIncidentResponse/Scripts/XCloudProviderWidget/XCloudProviderWidget.yml
@@ -10,7 +10,7 @@ comment: 'This script returns an HTML result of the cloud providers in the incid
enabled: true
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.8.0
tests:
diff --git a/Packs/CloudIncidentResponse/Scripts/displayCloudIndicators/displayCloudIndicators.yml b/Packs/CloudIncidentResponse/Scripts/displayCloudIndicators/displayCloudIndicators.yml
index 4f8cd5ac2e01..2e513f4e2344 100644
--- a/Packs/CloudIncidentResponse/Scripts/displayCloudIndicators/displayCloudIndicators.yml
+++ b/Packs/CloudIncidentResponse/Scripts/displayCloudIndicators/displayCloudIndicators.yml
@@ -10,7 +10,7 @@ comment: Display the Cloud indicators found in a dynamic-section
enabled: true
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.8.0
tests:
diff --git a/Packs/CloudIncidentResponse/pack_metadata.json b/Packs/CloudIncidentResponse/pack_metadata.json
index 84dba991c9ee..98460efae1a2 100644
--- a/Packs/CloudIncidentResponse/pack_metadata.json
+++ b/Packs/CloudIncidentResponse/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Cloud Incident Response",
"description": "This content Pack helps you automate collection, investigation, and remediation of incidents related to cloud infrastructure activities in AWS, Azure, and GCP.",
"support": "xsoar",
- "currentVersion": "1.0.14",
+ "currentVersion": "1.0.15",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/CommonScripts/ReleaseNotes/1_13_40.md b/Packs/CommonScripts/ReleaseNotes/1_13_40.md
new file mode 100644
index 000000000000..e7e8b03cfe32
--- /dev/null
+++ b/Packs/CommonScripts/ReleaseNotes/1_13_40.md
@@ -0,0 +1,78 @@
+
+#### Scripts
+
+##### LinkIncidentsWithRetry
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CVSSCalculator
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### ExportContextToJSONFile
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### displayUtilitiesResults
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### PopulateCriticalAssets
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### LinkIncidentsButton
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### ConvertDatetoUTC
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### AssignToMeButton
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### IsDomainInternal
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### IndicatorMaliciousRatioCalculation
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### IPToHost
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### MarkAsEvidenceByTag
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CopyContextToField
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### AddDBotScoreToContext
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CloseInvestigationAsDuplicate
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### SetDateField
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CompareIncidentsLabels
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### ContextContains
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### GenerateSummaryReportButton
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### DemistoVersion
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### IsIPPrivate
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### GenerateRandomString
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### EncodeToAscii
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### LoadJSONFileToContext
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### CalculateTimeDifference
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/CommonScripts/Scripts/AddDBotScoreToContext/AddDBotScoreToContext.yml b/Packs/CommonScripts/Scripts/AddDBotScoreToContext/AddDBotScoreToContext.yml
index 4c20b2817b37..302f52cc9583 100644
--- a/Packs/CommonScripts/Scripts/AddDBotScoreToContext/AddDBotScoreToContext.yml
+++ b/Packs/CommonScripts/Scripts/AddDBotScoreToContext/AddDBotScoreToContext.yml
@@ -26,7 +26,7 @@ comment: Add DBot score to context for indicators with custom vendor, score, rel
commonfields:
id: AddDBotScoreToContext
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: AddDBotScoreToContext
runas: DBotWeakRole
diff --git a/Packs/CommonScripts/Scripts/AssignToMeButton/AssignToMeButton.yml b/Packs/CommonScripts/Scripts/AssignToMeButton/AssignToMeButton.yml
index c22cb91edddd..1dcc7026d632 100644
--- a/Packs/CommonScripts/Scripts/AssignToMeButton/AssignToMeButton.yml
+++ b/Packs/CommonScripts/Scripts/AssignToMeButton/AssignToMeButton.yml
@@ -2,7 +2,7 @@ comment: 'Assigns the current Incident to the Cortex XSOAR user who clicked the
commonfields:
id: AssignToMeButton
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: AssignToMeButton
runas: DBotWeakRole
diff --git a/Packs/CommonScripts/Scripts/CVSSCalculator/CVSSCalculator.yml b/Packs/CommonScripts/Scripts/CVSSCalculator/CVSSCalculator.yml
index 404f7b353059..eaa0f8fcda78 100644
--- a/Packs/CommonScripts/Scripts/CVSSCalculator/CVSSCalculator.yml
+++ b/Packs/CommonScripts/Scripts/CVSSCalculator/CVSSCalculator.yml
@@ -240,5 +240,5 @@ outputs:
description: Version of CVSS used in the calculation.
type: number
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
fromversion: 5.0.0
diff --git a/Packs/CommonScripts/Scripts/CalculateTimeDifference/CalculateTimeDifference.yml b/Packs/CommonScripts/Scripts/CalculateTimeDifference/CalculateTimeDifference.yml
index 5ebc69947fda..60ba2e3c4487 100644
--- a/Packs/CommonScripts/Scripts/CalculateTimeDifference/CalculateTimeDifference.yml
+++ b/Packs/CommonScripts/Scripts/CalculateTimeDifference/CalculateTimeDifference.yml
@@ -28,4 +28,4 @@ runas: DBotWeakRole
tests:
- Impossible Traveler - Test
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
diff --git a/Packs/CommonScripts/Scripts/CloseInvestigationAsDuplicate/CloseInvestigationAsDuplicate.yml b/Packs/CommonScripts/Scripts/CloseInvestigationAsDuplicate/CloseInvestigationAsDuplicate.yml
index 56955bd0c093..d7f69cc2abc4 100644
--- a/Packs/CommonScripts/Scripts/CloseInvestigationAsDuplicate/CloseInvestigationAsDuplicate.yml
+++ b/Packs/CommonScripts/Scripts/CloseInvestigationAsDuplicate/CloseInvestigationAsDuplicate.yml
@@ -15,6 +15,6 @@ args:
description: Duplicate incident id
scripttarget: 0
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- No tests (auto formatted)
diff --git a/Packs/CommonScripts/Scripts/CompareIncidentsLabels/CompareIncidentsLabels.yml b/Packs/CommonScripts/Scripts/CompareIncidentsLabels/CompareIncidentsLabels.yml
index 618df6055f96..f4115a842ef6 100644
--- a/Packs/CommonScripts/Scripts/CompareIncidentsLabels/CompareIncidentsLabels.yml
+++ b/Packs/CommonScripts/Scripts/CompareIncidentsLabels/CompareIncidentsLabels.yml
@@ -23,6 +23,6 @@ timeout: '0'
type: python
subtype: python3
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- CompareIncidentsLabels-test-playbook
diff --git a/Packs/CommonScripts/Scripts/ContextContains/ContextContains.yml b/Packs/CommonScripts/Scripts/ContextContains/ContextContains.yml
index 452fa71184d2..03d722c57b30 100644
--- a/Packs/CommonScripts/Scripts/ContextContains/ContextContains.yml
+++ b/Packs/CommonScripts/Scripts/ContextContains/ContextContains.yml
@@ -17,6 +17,6 @@ args:
description: Value to search
scripttarget: 0
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- No tests (auto formatted)
diff --git a/Packs/CommonScripts/Scripts/ConvertDateToUTC/ConvertDateToUTC.yml b/Packs/CommonScripts/Scripts/ConvertDateToUTC/ConvertDateToUTC.yml
index 3daa070b3f41..d2b792355662 100644
--- a/Packs/CommonScripts/Scripts/ConvertDateToUTC/ConvertDateToUTC.yml
+++ b/Packs/CommonScripts/Scripts/ConvertDateToUTC/ConvertDateToUTC.yml
@@ -28,7 +28,7 @@ outputs:
type: Unknown
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
tests:
diff --git a/Packs/CommonScripts/Scripts/CopyContextToField/CopyContextToField.yml b/Packs/CommonScripts/Scripts/CopyContextToField/CopyContextToField.yml
index ec9d6f17b085..1777780cda3f 100644
--- a/Packs/CommonScripts/Scripts/CopyContextToField/CopyContextToField.yml
+++ b/Packs/CommonScripts/Scripts/CopyContextToField/CopyContextToField.yml
@@ -32,6 +32,6 @@ timeout: '0'
type: python
subtype: python3
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- CopyContextToFieldTest
diff --git a/Packs/CommonScripts/Scripts/DemistoVersion/DemistoVersion.yml b/Packs/CommonScripts/Scripts/DemistoVersion/DemistoVersion.yml
index 3eaa43086f7a..d4ef4905475f 100644
--- a/Packs/CommonScripts/Scripts/DemistoVersion/DemistoVersion.yml
+++ b/Packs/CommonScripts/Scripts/DemistoVersion/DemistoVersion.yml
@@ -16,7 +16,7 @@ outputs:
type: string
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
marketplaces:
diff --git a/Packs/CommonScripts/Scripts/EncodeToAscii/EncodeToAscii.yml b/Packs/CommonScripts/Scripts/EncodeToAscii/EncodeToAscii.yml
index 21c387674fd1..a199048a3558 100644
--- a/Packs/CommonScripts/Scripts/EncodeToAscii/EncodeToAscii.yml
+++ b/Packs/CommonScripts/Scripts/EncodeToAscii/EncodeToAscii.yml
@@ -18,6 +18,6 @@ outputs:
type: string
scripttarget: 0
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- No tests (auto formatted)
diff --git a/Packs/CommonScripts/Scripts/ExportContextToJSONFile/ExportContextToJSONFile.yml b/Packs/CommonScripts/Scripts/ExportContextToJSONFile/ExportContextToJSONFile.yml
index 21d5cbb1257d..b0ad63b4922e 100644
--- a/Packs/CommonScripts/Scripts/ExportContextToJSONFile/ExportContextToJSONFile.yml
+++ b/Packs/CommonScripts/Scripts/ExportContextToJSONFile/ExportContextToJSONFile.yml
@@ -9,7 +9,7 @@ commonfields:
contentitemexportablefields:
contentitemfields:
fromServerVersion: ""
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: ExportContextToJSONFile
runas: DBotWeakRole
diff --git a/Packs/CommonScripts/Scripts/GenerateRandomString/GenerateRandomString.yml b/Packs/CommonScripts/Scripts/GenerateRandomString/GenerateRandomString.yml
index 080930a8f49e..d69a332f03a5 100644
--- a/Packs/CommonScripts/Scripts/GenerateRandomString/GenerateRandomString.yml
+++ b/Packs/CommonScripts/Scripts/GenerateRandomString/GenerateRandomString.yml
@@ -49,4 +49,4 @@ scripttarget: 0
tests:
- RandomStringGenerateTest
fromversion: 6.2.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
diff --git a/Packs/CommonScripts/Scripts/GenerateSummaryReportButton/GenerateSummaryReportButton.yml b/Packs/CommonScripts/Scripts/GenerateSummaryReportButton/GenerateSummaryReportButton.yml
index 770c564852f5..f1dd182289a5 100644
--- a/Packs/CommonScripts/Scripts/GenerateSummaryReportButton/GenerateSummaryReportButton.yml
+++ b/Packs/CommonScripts/Scripts/GenerateSummaryReportButton/GenerateSummaryReportButton.yml
@@ -2,7 +2,7 @@ comment: This button will generate summary 'Case Report' template for a given In
commonfields:
id: GenerateSummaryReportButton
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: GenerateSummaryReportButton
runas: DBotWeakRole
diff --git a/Packs/CommonScripts/Scripts/IPToHost/IPToHost.yml b/Packs/CommonScripts/Scripts/IPToHost/IPToHost.yml
index efeb51647d73..ea005c717028 100644
--- a/Packs/CommonScripts/Scripts/IPToHost/IPToHost.yml
+++ b/Packs/CommonScripts/Scripts/IPToHost/IPToHost.yml
@@ -24,6 +24,6 @@ outputs:
type: string
scripttarget: 0
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- IPToHost - Test
diff --git a/Packs/CommonScripts/Scripts/IndicatorMaliciousRatioCalculation/IndicatorMaliciousRatioCalculation.yml b/Packs/CommonScripts/Scripts/IndicatorMaliciousRatioCalculation/IndicatorMaliciousRatioCalculation.yml
index 3ac1449baed7..d9d8fba6562b 100644
--- a/Packs/CommonScripts/Scripts/IndicatorMaliciousRatioCalculation/IndicatorMaliciousRatioCalculation.yml
+++ b/Packs/CommonScripts/Scripts/IndicatorMaliciousRatioCalculation/IndicatorMaliciousRatioCalculation.yml
@@ -44,4 +44,4 @@ timeout: 300ns
fromversion: 5.0.0
tests:
- IndicatorMaliciousRatioCalculation_test
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
diff --git a/Packs/CommonScripts/Scripts/IsDomainInternal/IsDomainInternal.yml b/Packs/CommonScripts/Scripts/IsDomainInternal/IsDomainInternal.yml
index ceba2474b991..8554b2b00b2b 100644
--- a/Packs/CommonScripts/Scripts/IsDomainInternal/IsDomainInternal.yml
+++ b/Packs/CommonScripts/Scripts/IsDomainInternal/IsDomainInternal.yml
@@ -28,7 +28,7 @@ outputs:
type: boolean
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.5.0
marketplaces:
diff --git a/Packs/CommonScripts/Scripts/IsIPPrivate/IsIPPrivate.yml b/Packs/CommonScripts/Scripts/IsIPPrivate/IsIPPrivate.yml
index a701eab16e9c..290998bb8e47 100644
--- a/Packs/CommonScripts/Scripts/IsIPPrivate/IsIPPrivate.yml
+++ b/Packs/CommonScripts/Scripts/IsIPPrivate/IsIPPrivate.yml
@@ -32,7 +32,7 @@ outputs:
description: Any tags that were added to the indicator. The tags are added by this script if they were specified for the IP or IP range in the Cortex XSOAR list.
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.5.0
marketplaces:
diff --git a/Packs/CommonScripts/Scripts/LinkIncidentsButton/LinkIncidentsButton.yml b/Packs/CommonScripts/Scripts/LinkIncidentsButton/LinkIncidentsButton.yml
index 958ac323d95a..1b2d980c89c9 100644
--- a/Packs/CommonScripts/Scripts/LinkIncidentsButton/LinkIncidentsButton.yml
+++ b/Packs/CommonScripts/Scripts/LinkIncidentsButton/LinkIncidentsButton.yml
@@ -14,7 +14,7 @@ comment: |
commonfields:
id: LinkIncidentsButton
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: LinkIncidentsButton
runas: DBotWeakRole
diff --git a/Packs/CommonScripts/Scripts/LinkIncidentsWithRetry/LinkIncidentsWithRetry.yml b/Packs/CommonScripts/Scripts/LinkIncidentsWithRetry/LinkIncidentsWithRetry.yml
index 39678c11236f..a843ae9e8b7a 100644
--- a/Packs/CommonScripts/Scripts/LinkIncidentsWithRetry/LinkIncidentsWithRetry.yml
+++ b/Packs/CommonScripts/Scripts/LinkIncidentsWithRetry/LinkIncidentsWithRetry.yml
@@ -18,7 +18,7 @@ scripttarget: 0
comment: |-
Use this script to avoid DB version errors when simultaneously running multiple linked incidents.
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- No tests (auto formatted)
marketplaces:
diff --git a/Packs/CommonScripts/Scripts/LoadJSONFileToContext/LoadJSONFileToContext.yml b/Packs/CommonScripts/Scripts/LoadJSONFileToContext/LoadJSONFileToContext.yml
index 1027daa2de0c..1a678553ea86 100644
--- a/Packs/CommonScripts/Scripts/LoadJSONFileToContext/LoadJSONFileToContext.yml
+++ b/Packs/CommonScripts/Scripts/LoadJSONFileToContext/LoadJSONFileToContext.yml
@@ -12,7 +12,7 @@ commonfields:
contentitemexportablefields:
contentitemfields:
fromServerVersion: ""
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: LoadJSONFileToContext
runas: DBotWeakRole
diff --git a/Packs/CommonScripts/Scripts/MarkAsEvidenceByTag/MarkAsEvidenceByTag.yml b/Packs/CommonScripts/Scripts/MarkAsEvidenceByTag/MarkAsEvidenceByTag.yml
index d236cf303063..1903af81892e 100644
--- a/Packs/CommonScripts/Scripts/MarkAsEvidenceByTag/MarkAsEvidenceByTag.yml
+++ b/Packs/CommonScripts/Scripts/MarkAsEvidenceByTag/MarkAsEvidenceByTag.yml
@@ -23,6 +23,6 @@ tags:
- Utility
type: python
fromversion: 6.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- No tests (auto formatted)
diff --git a/Packs/CommonScripts/Scripts/PopulateCriticalAssets/PopulateCriticalAssets.yml b/Packs/CommonScripts/Scripts/PopulateCriticalAssets/PopulateCriticalAssets.yml
index 346a356798cb..04a38e185ba2 100644
--- a/Packs/CommonScripts/Scripts/PopulateCriticalAssets/PopulateCriticalAssets.yml
+++ b/Packs/CommonScripts/Scripts/PopulateCriticalAssets/PopulateCriticalAssets.yml
@@ -18,4 +18,4 @@ runas: DBotWeakRole
tests:
- Calculate Severity - Generic v2 - Test
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
diff --git a/Packs/CommonScripts/Scripts/SetDateField/SetDateField.yml b/Packs/CommonScripts/Scripts/SetDateField/SetDateField.yml
index 9b7f34ace338..a14cdff04683 100644
--- a/Packs/CommonScripts/Scripts/SetDateField/SetDateField.yml
+++ b/Packs/CommonScripts/Scripts/SetDateField/SetDateField.yml
@@ -15,6 +15,6 @@ args:
description: "The name of the incident custom field of type date"
scripttarget: 0
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- No tests (auto formatted)
diff --git a/Packs/CommonScripts/Scripts/displayUtilitiesResults/displayUtilitiesResults.yml b/Packs/CommonScripts/Scripts/displayUtilitiesResults/displayUtilitiesResults.yml
index 6c164a280547..e43c7863e7df 100644
--- a/Packs/CommonScripts/Scripts/displayUtilitiesResults/displayUtilitiesResults.yml
+++ b/Packs/CommonScripts/Scripts/displayUtilitiesResults/displayUtilitiesResults.yml
@@ -10,7 +10,7 @@ tags:
enabled: true
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.10.0
tests:
diff --git a/Packs/CommonScripts/pack_metadata.json b/Packs/CommonScripts/pack_metadata.json
index c5f5b73d6cc4..ef668157d2b1 100644
--- a/Packs/CommonScripts/pack_metadata.json
+++ b/Packs/CommonScripts/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Common Scripts",
"description": "Frequently used scripts pack.",
"support": "xsoar",
- "currentVersion": "1.13.39",
+ "currentVersion": "1.13.40",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/ContentManagement/ReleaseNotes/1_2_18.md b/Packs/ContentManagement/ReleaseNotes/1_2_18.md
new file mode 100644
index 000000000000..0406cdc76929
--- /dev/null
+++ b/Packs/ContentManagement/ReleaseNotes/1_2_18.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### GetPrBranches
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/ContentManagement/Scripts/GetPrBranches/GetPrBranches.yml b/Packs/ContentManagement/Scripts/GetPrBranches/GetPrBranches.yml
index 52e9bc47b058..41eee1484574 100644
--- a/Packs/ContentManagement/Scripts/GetPrBranches/GetPrBranches.yml
+++ b/Packs/ContentManagement/Scripts/GetPrBranches/GetPrBranches.yml
@@ -5,7 +5,7 @@ commonfields:
contentitemexportablefields:
contentitemfields:
fromServerVersion: ''
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: GetPrBranches
runas: DBotWeakRole
diff --git a/Packs/ContentManagement/pack_metadata.json b/Packs/ContentManagement/pack_metadata.json
index 9a7199f3ca40..0f41abe9da0a 100644
--- a/Packs/ContentManagement/pack_metadata.json
+++ b/Packs/ContentManagement/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "XSOAR CI/CD",
"description": "This pack enables you to orchestrate your XSOAR system configuration.",
"support": "xsoar",
- "currentVersion": "1.2.17",
+ "currentVersion": "1.2.18",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/CounterTack/Integrations/CounterTack/CounterTack.yml b/Packs/CounterTack/Integrations/CounterTack/CounterTack.yml
index 41c497d843a2..4d93f3613e6d 100644
--- a/Packs/CounterTack/Integrations/CounterTack/CounterTack.yml
+++ b/Packs/CounterTack/Integrations/CounterTack/CounterTack.yml
@@ -1145,7 +1145,7 @@ script:
script: '-'
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
tests:
- no tests
fromversion: 5.0.0
diff --git a/Packs/CounterTack/ReleaseNotes/1_0_9.md b/Packs/CounterTack/ReleaseNotes/1_0_9.md
new file mode 100644
index 000000000000..18619bce4e1c
--- /dev/null
+++ b/Packs/CounterTack/ReleaseNotes/1_0_9.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### CounterTack
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/CounterTack/pack_metadata.json b/Packs/CounterTack/pack_metadata.json
index 902b7561c756..d5e62aa6af2a 100644
--- a/Packs/CounterTack/pack_metadata.json
+++ b/Packs/CounterTack/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "CounterTack",
"description": "CounterTack empowers endpoint security teams to assure endpoint protection for Identifying Cyber Threats. Integrating a predictive endpoint protection platform",
"support": "xsoar",
- "currentVersion": "1.0.8",
+ "currentVersion": "1.0.9",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/CrowdStrikeOpenAPI/Integrations/CrowdStrikeOpenAPI/CrowdStrikeOpenAPI.yml b/Packs/CrowdStrikeOpenAPI/Integrations/CrowdStrikeOpenAPI/CrowdStrikeOpenAPI.yml
index c46c7d06e578..e341e0de6910 100644
--- a/Packs/CrowdStrikeOpenAPI/Integrations/CrowdStrikeOpenAPI/CrowdStrikeOpenAPI.yml
+++ b/Packs/CrowdStrikeOpenAPI/Integrations/CrowdStrikeOpenAPI/CrowdStrikeOpenAPI.yml
@@ -25717,7 +25717,7 @@ script:
- contextPath: CrowdStrike.deviceNetworkHistory.resources.history.timestamp
description: ''
type: String
- dockerimage: demisto/python3:3.10.13.85667
+ dockerimage: demisto/python3:3.10.13.86272
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/CrowdStrikeOpenAPI/ReleaseNotes/1_0_18.md b/Packs/CrowdStrikeOpenAPI/ReleaseNotes/1_0_18.md
new file mode 100644
index 000000000000..e5a9937d5915
--- /dev/null
+++ b/Packs/CrowdStrikeOpenAPI/ReleaseNotes/1_0_18.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### CrowdStrike OpenAPI (Beta)
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/CrowdStrikeOpenAPI/pack_metadata.json b/Packs/CrowdStrikeOpenAPI/pack_metadata.json
index 571ae0d4efd0..8532b718ccb2 100644
--- a/Packs/CrowdStrikeOpenAPI/pack_metadata.json
+++ b/Packs/CrowdStrikeOpenAPI/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "CrowdStrike OpenAPI",
"description": "Use the CrowdStrike OpenAPI integration to interact with CrowdStrike APIs that do not have dedicated integrations in Cortex XSOAR, for example, CrowdStrike FalconX, etc.",
"support": "xsoar",
- "currentVersion": "1.0.17",
+ "currentVersion": "1.0.18",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/CuckooSandbox/ReleaseNotes/1_1_5.md b/Packs/CuckooSandbox/ReleaseNotes/1_1_5.md
new file mode 100644
index 000000000000..2acdb56852db
--- /dev/null
+++ b/Packs/CuckooSandbox/ReleaseNotes/1_1_5.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### CuckooDisplayReport
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/CuckooSandbox/Scripts/CuckooDisplayReport/CuckooDisplayReport.yml b/Packs/CuckooSandbox/Scripts/CuckooDisplayReport/CuckooDisplayReport.yml
index cd30cff49f3e..67c3760b8b8b 100644
--- a/Packs/CuckooSandbox/Scripts/CuckooDisplayReport/CuckooDisplayReport.yml
+++ b/Packs/CuckooSandbox/Scripts/CuckooDisplayReport/CuckooDisplayReport.yml
@@ -22,6 +22,6 @@ args:
scripttarget: 0
timeout: 0s
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
tests:
- No tests (auto formatted)
diff --git a/Packs/CuckooSandbox/pack_metadata.json b/Packs/CuckooSandbox/pack_metadata.json
index ffe88b8bdaf7..bf60908e2232 100644
--- a/Packs/CuckooSandbox/pack_metadata.json
+++ b/Packs/CuckooSandbox/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Cuckoo Sandbox",
"description": "Malware dynamic analysis sandboxing",
"support": "xsoar",
- "currentVersion": "1.1.4",
+ "currentVersion": "1.1.5",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/DBotTruthBombs/Integrations/DBotTruthBombs/DBotTruthBombs.yml b/Packs/DBotTruthBombs/Integrations/DBotTruthBombs/DBotTruthBombs.yml
index fe77d06d7421..8207258cef63 100644
--- a/Packs/DBotTruthBombs/Integrations/DBotTruthBombs/DBotTruthBombs.yml
+++ b/Packs/DBotTruthBombs/Integrations/DBotTruthBombs/DBotTruthBombs.yml
@@ -33,7 +33,7 @@ script:
- Travel
description: Returns a previously undisclosed fact about DBot.
name: dbot-truth-bomb
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
runonce: false
script: ''
subtype: python3
diff --git a/Packs/DBotTruthBombs/ReleaseNotes/1_0_8.md b/Packs/DBotTruthBombs/ReleaseNotes/1_0_8.md
new file mode 100644
index 000000000000..f678aff3042c
--- /dev/null
+++ b/Packs/DBotTruthBombs/ReleaseNotes/1_0_8.md
@@ -0,0 +1,12 @@
+
+#### Integrations
+
+##### DBot Truth Bombs
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+
+#### Scripts
+
+##### FactAboutYou
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/DBotTruthBombs/Scripts/FactsAboutYou/FactsAboutYou.yml b/Packs/DBotTruthBombs/Scripts/FactsAboutYou/FactsAboutYou.yml
index 808477108386..a1134f372441 100644
--- a/Packs/DBotTruthBombs/Scripts/FactsAboutYou/FactsAboutYou.yml
+++ b/Packs/DBotTruthBombs/Scripts/FactsAboutYou/FactsAboutYou.yml
@@ -16,7 +16,7 @@ comment: Reveal some facts about yourself.
commonfields:
id: FactAboutYou
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: FactAboutYou
runas: DBotWeakRole
diff --git a/Packs/DBotTruthBombs/pack_metadata.json b/Packs/DBotTruthBombs/pack_metadata.json
index 37d586f3790a..0d81f17a4795 100644
--- a/Packs/DBotTruthBombs/pack_metadata.json
+++ b/Packs/DBotTruthBombs/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "DBot Truth Bombs",
"description": "Nefarious attackers coming in at you from all fronts. Don't you wish you could just go Texas Ranger on them?",
"support": "xsoar",
- "currentVersion": "1.0.7",
+ "currentVersion": "1.0.8",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/EasyVista/Integrations/EasyVista/EasyVista.yml b/Packs/EasyVista/Integrations/EasyVista/EasyVista.yml
index e03205403268..dba4b5529a04 100644
--- a/Packs/EasyVista/Integrations/EasyVista/EasyVista.yml
+++ b/Packs/EasyVista/Integrations/EasyVista/EasyVista.yml
@@ -134,7 +134,7 @@ script:
description: Request ID
type: string
description: This method allows a list of incidents / requests (service, change, investment) to be obtained.
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
tests:
- No tests
fromversion: 5.0.0
diff --git a/Packs/EasyVista/ReleaseNotes/1_0_9.md b/Packs/EasyVista/ReleaseNotes/1_0_9.md
new file mode 100644
index 000000000000..65e1794b396e
--- /dev/null
+++ b/Packs/EasyVista/ReleaseNotes/1_0_9.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### EasyVista
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/EasyVista/pack_metadata.json b/Packs/EasyVista/pack_metadata.json
index b5f844592d64..043a20ed9467 100644
--- a/Packs/EasyVista/pack_metadata.json
+++ b/Packs/EasyVista/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "EasyVista",
"description": "EasyVista Service Manager manages the entire process of designing, managing and delivering IT services.",
"support": "xsoar",
- "currentVersion": "1.0.8",
+ "currentVersion": "1.0.9",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/FeedAlienVault/Integrations/FeedAlienVaultReputation/FeedAlienVaultReputation.yml b/Packs/FeedAlienVault/Integrations/FeedAlienVaultReputation/FeedAlienVaultReputation.yml
index 98c3834f56cb..2982e6157434 100644
--- a/Packs/FeedAlienVault/Integrations/FeedAlienVaultReputation/FeedAlienVaultReputation.yml
+++ b/Packs/FeedAlienVault/Integrations/FeedAlienVaultReputation/FeedAlienVaultReputation.yml
@@ -93,7 +93,7 @@ script:
name: indicator_type
description: Gets the feed indicators.
name: alienvault-get-indicators
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
feed: true
runonce: false
script: '-'
diff --git a/Packs/FeedAlienVault/ReleaseNotes/1_1_30.md b/Packs/FeedAlienVault/ReleaseNotes/1_1_30.md
new file mode 100644
index 000000000000..1bc009815f81
--- /dev/null
+++ b/Packs/FeedAlienVault/ReleaseNotes/1_1_30.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### AlienVault Reputation Feed
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/FeedAlienVault/pack_metadata.json b/Packs/FeedAlienVault/pack_metadata.json
index 6387ef2415a4..ef1e1c59ed35 100644
--- a/Packs/FeedAlienVault/pack_metadata.json
+++ b/Packs/FeedAlienVault/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "AlienVault Feed",
"description": "Indicators feed from AlienVault",
"support": "xsoar",
- "currentVersion": "1.1.29",
+ "currentVersion": "1.1.30",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/FeedMajesticMillion/Integrations/MajesticMillion/MajesticMillion.yml b/Packs/FeedMajesticMillion/Integrations/MajesticMillion/MajesticMillion.yml
index 12add95ae031..d1dcfee8fcd4 100644
--- a/Packs/FeedMajesticMillion/Integrations/MajesticMillion/MajesticMillion.yml
+++ b/Packs/FeedMajesticMillion/Integrations/MajesticMillion/MajesticMillion.yml
@@ -101,7 +101,7 @@ script:
name: limit
description: Gets the feed indicators.
name: majesticmillion-get-indicators
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
feed: true
runonce: false
script: '-'
diff --git a/Packs/FeedMajesticMillion/ReleaseNotes/1_1_14.md b/Packs/FeedMajesticMillion/ReleaseNotes/1_1_14.md
new file mode 100644
index 000000000000..46c589f32578
--- /dev/null
+++ b/Packs/FeedMajesticMillion/ReleaseNotes/1_1_14.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Majestic Million Feed
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/FeedMajesticMillion/pack_metadata.json b/Packs/FeedMajesticMillion/pack_metadata.json
index ca2e57702138..d9ba5fa9ad0e 100644
--- a/Packs/FeedMajesticMillion/pack_metadata.json
+++ b/Packs/FeedMajesticMillion/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Majestic Million Feed",
"description": "Use the Majestic Million pack to ingest the top known websites as 'good' indicators.",
"support": "xsoar",
- "currentVersion": "1.1.13",
+ "currentVersion": "1.1.14",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/FeedTorExitAddresses/Integrations/FeedTorExitAddresses/FeedTorExitAddresses.yml b/Packs/FeedTorExitAddresses/Integrations/FeedTorExitAddresses/FeedTorExitAddresses.yml
index 340823c9a693..4b563191e270 100644
--- a/Packs/FeedTorExitAddresses/Integrations/FeedTorExitAddresses/FeedTorExitAddresses.yml
+++ b/Packs/FeedTorExitAddresses/Integrations/FeedTorExitAddresses/FeedTorExitAddresses.yml
@@ -91,7 +91,7 @@ script:
name: limit
description: Gets the feed indicators.
name: tor-get-indicators
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
feed: true
runonce: false
script: '-'
diff --git a/Packs/FeedTorExitAddresses/ReleaseNotes/1_0_9.md b/Packs/FeedTorExitAddresses/ReleaseNotes/1_0_9.md
new file mode 100644
index 000000000000..d34543ab6691
--- /dev/null
+++ b/Packs/FeedTorExitAddresses/ReleaseNotes/1_0_9.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Tor Exit Addresses Feed
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/FeedTorExitAddresses/pack_metadata.json b/Packs/FeedTorExitAddresses/pack_metadata.json
index 49203a751b95..bf95329d17d4 100644
--- a/Packs/FeedTorExitAddresses/pack_metadata.json
+++ b/Packs/FeedTorExitAddresses/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Tor Exit Addresses Feed",
"description": "Tor is free software and an open network that helps you defend against\n traffic analysis, a form of network surveillance that threatens personal freedom\n and privacy, confidential business activities and relationships, and state security.",
"support": "xsoar",
- "currentVersion": "1.0.8",
+ "currentVersion": "1.0.9",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Feedsslabusech/Integrations/Feedsslabusech/Feedsslabusech.yml b/Packs/Feedsslabusech/Integrations/Feedsslabusech/Feedsslabusech.yml
index 75b3ccf02e53..abc476c5cd4e 100644
--- a/Packs/Feedsslabusech/Integrations/Feedsslabusech/Feedsslabusech.yml
+++ b/Packs/Feedsslabusech/Integrations/Feedsslabusech/Feedsslabusech.yml
@@ -107,7 +107,7 @@ script:
name: indicator_type
description: Gets the feed indicators.
name: sslbl-get-indicators
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
feed: true
runonce: false
script: '-'
diff --git a/Packs/Feedsslabusech/ReleaseNotes/1_1_26.md b/Packs/Feedsslabusech/ReleaseNotes/1_1_26.md
new file mode 100644
index 000000000000..057bf26b8a78
--- /dev/null
+++ b/Packs/Feedsslabusech/ReleaseNotes/1_1_26.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### abuse.ch SSL Blacklist Feed
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Feedsslabusech/pack_metadata.json b/Packs/Feedsslabusech/pack_metadata.json
index bf594313ec31..5a2911df2b55 100644
--- a/Packs/Feedsslabusech/pack_metadata.json
+++ b/Packs/Feedsslabusech/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Abuse.ch SSL Blacklist Feed",
"description": "The SSL IP Blacklist contains all hosts (IP addresses) that SSLBL has seen in the past 30 days and\n identified as being associated with a malicious SSL certificate.",
"support": "xsoar",
- "currentVersion": "1.1.25",
+ "currentVersion": "1.1.26",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/FidelisEndpoint/Integrations/FidelisEndpoint/FidelisEndpoint.yml b/Packs/FidelisEndpoint/Integrations/FidelisEndpoint/FidelisEndpoint.yml
index 4f22a30be38e..459499870939 100644
--- a/Packs/FidelisEndpoint/Integrations/FidelisEndpoint/FidelisEndpoint.yml
+++ b/Packs/FidelisEndpoint/Integrations/FidelisEndpoint/FidelisEndpoint.yml
@@ -1243,7 +1243,7 @@ script:
- contextPath: FidelisEndpoint.Query.EntityType
description: Entity type.
type: Number
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/FidelisEndpoint/ReleaseNotes/1_0_6.md b/Packs/FidelisEndpoint/ReleaseNotes/1_0_6.md
new file mode 100644
index 000000000000..438a10e86416
--- /dev/null
+++ b/Packs/FidelisEndpoint/ReleaseNotes/1_0_6.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Fidelis EDR
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/FidelisEndpoint/pack_metadata.json b/Packs/FidelisEndpoint/pack_metadata.json
index 113d1de0925c..6c0b74b0046a 100644
--- a/Packs/FidelisEndpoint/pack_metadata.json
+++ b/Packs/FidelisEndpoint/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Fidelis Endpoint",
"description": "Fidelis Endpoint",
"support": "xsoar",
- "currentVersion": "1.0.5",
+ "currentVersion": "1.0.6",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/FiltersAndTransformers/ReleaseNotes/1_2_61.md b/Packs/FiltersAndTransformers/ReleaseNotes/1_2_61.md
new file mode 100644
index 000000000000..d7050d95512c
--- /dev/null
+++ b/Packs/FiltersAndTransformers/ReleaseNotes/1_2_61.md
@@ -0,0 +1,12 @@
+
+#### Scripts
+
+##### DT
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### StripChars
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### GetValuesOfMultipleFields
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/FiltersAndTransformers/Scripts/DT/DT.yml b/Packs/FiltersAndTransformers/Scripts/DT/DT.yml
index e08cdcf94382..26185d1ec414 100644
--- a/Packs/FiltersAndTransformers/Scripts/DT/DT.yml
+++ b/Packs/FiltersAndTransformers/Scripts/DT/DT.yml
@@ -21,4 +21,4 @@ scripttarget: 0
tests:
- No tests - script used for testing
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
diff --git a/Packs/FiltersAndTransformers/Scripts/GetValuesOfMultipleFIelds/GetValuesOfMultipleFIelds.yml b/Packs/FiltersAndTransformers/Scripts/GetValuesOfMultipleFIelds/GetValuesOfMultipleFIelds.yml
index 086899ca1335..ad217a264452 100644
--- a/Packs/FiltersAndTransformers/Scripts/GetValuesOfMultipleFIelds/GetValuesOfMultipleFIelds.yml
+++ b/Packs/FiltersAndTransformers/Scripts/GetValuesOfMultipleFIelds/GetValuesOfMultipleFIelds.yml
@@ -14,7 +14,7 @@ commonfields:
name: GetValuesOfMultipleFields
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
script: '-'
tags:
diff --git a/Packs/FiltersAndTransformers/Scripts/StripChar/StripChar.yml b/Packs/FiltersAndTransformers/Scripts/StripChar/StripChar.yml
index 0b7ad59df4d1..35256123626b 100644
--- a/Packs/FiltersAndTransformers/Scripts/StripChar/StripChar.yml
+++ b/Packs/FiltersAndTransformers/Scripts/StripChar/StripChar.yml
@@ -23,4 +23,4 @@ subtype: python3
tests:
- stripChars - Test
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
diff --git a/Packs/FiltersAndTransformers/pack_metadata.json b/Packs/FiltersAndTransformers/pack_metadata.json
index 5758b55b6a3e..32a16f933fab 100644
--- a/Packs/FiltersAndTransformers/pack_metadata.json
+++ b/Packs/FiltersAndTransformers/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Filters And Transformers",
"description": "Frequently used filters and transformers pack.",
"support": "xsoar",
- "currentVersion": "1.2.60",
+ "currentVersion": "1.2.61",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Forescout/Integrations/Forescout/Forescout.yml b/Packs/Forescout/Integrations/Forescout/Forescout.yml
index 55f2156e0e11..5dd4129121ad 100644
--- a/Packs/Forescout/Integrations/Forescout/Forescout.yml
+++ b/Packs/Forescout/Integrations/Forescout/Forescout.yml
@@ -331,7 +331,7 @@ script:
name: values
description: Update Forescout lists.
name: forescout-update-lists
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
runonce: false
script: '-'
type: python
diff --git a/Packs/Forescout/ReleaseNotes/1_0_9.md b/Packs/Forescout/ReleaseNotes/1_0_9.md
new file mode 100644
index 000000000000..ea7ba4e85f51
--- /dev/null
+++ b/Packs/Forescout/ReleaseNotes/1_0_9.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Forescout CounterACT
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Forescout/pack_metadata.json b/Packs/Forescout/pack_metadata.json
index a30e8b993065..02982640d35a 100644
--- a/Packs/Forescout/pack_metadata.json
+++ b/Packs/Forescout/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Forescout CounterACT",
"description": "Unified device visibility and control platform for IT and OT Security.",
"support": "xsoar",
- "currentVersion": "1.0.8",
+ "currentVersion": "1.0.9",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Imperva_WAF/Integrations/ImpervaWAF/ImpervaWAF.yml b/Packs/Imperva_WAF/Integrations/ImpervaWAF/ImpervaWAF.yml
index 60431acc3e32..d62d7a4b2fa2 100644
--- a/Packs/Imperva_WAF/Integrations/ImpervaWAF/ImpervaWAF.yml
+++ b/Packs/Imperva_WAF/Integrations/ImpervaWAF/ImpervaWAF.yml
@@ -507,7 +507,7 @@ script:
required: true
description: Deletes a web service custom policy indicated by the policy name.
name: imperva-waf-web-service-custom-policy-delete
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/Imperva_WAF/ReleaseNotes/1_0_18.md b/Packs/Imperva_WAF/ReleaseNotes/1_0_18.md
new file mode 100644
index 000000000000..8a8c5f011ff7
--- /dev/null
+++ b/Packs/Imperva_WAF/ReleaseNotes/1_0_18.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Imperva WAF
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Imperva_WAF/pack_metadata.json b/Packs/Imperva_WAF/pack_metadata.json
index 0c91ef785d2d..27381bf0e217 100644
--- a/Packs/Imperva_WAF/pack_metadata.json
+++ b/Packs/Imperva_WAF/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Imperva WAF",
"description": "Use the Imperva WAF integration to manage IP groups and Web security policies in Imperva WAF.",
"support": "xsoar",
- "currentVersion": "1.0.17",
+ "currentVersion": "1.0.18",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/IvantiHeat/Integrations/IvantiHeat/IvantiHeat.yml b/Packs/IvantiHeat/Integrations/IvantiHeat/IvantiHeat.yml
index bda42fa5d538..f6bc9949764f 100644
--- a/Packs/IvantiHeat/Integrations/IvantiHeat/IvantiHeat.yml
+++ b/Packs/IvantiHeat/Integrations/IvantiHeat/IvantiHeat.yml
@@ -280,7 +280,7 @@ script:
- contextPath: IvantiHeat.incidents.Email
description: Incident owner email address.
type: String
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/IvantiHeat/ReleaseNotes/1_0_10.md b/Packs/IvantiHeat/ReleaseNotes/1_0_10.md
new file mode 100644
index 000000000000..ba8b0d3e6dfd
--- /dev/null
+++ b/Packs/IvantiHeat/ReleaseNotes/1_0_10.md
@@ -0,0 +1,18 @@
+
+#### Integrations
+
+##### Ivanti Heat
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+
+#### Scripts
+
+##### IvantiHeatCreateIncidentExample
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### IvantiHeatCloseIncidentExample
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### IvantiHeatCreateProblemExample
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/IvantiHeat/Scripts/IvantiHeatCloseIncidentExample/IvantiHeatCloseIncidentExample.yml b/Packs/IvantiHeat/Scripts/IvantiHeatCloseIncidentExample/IvantiHeatCloseIncidentExample.yml
index 1761b20d78a0..e1fa28fa9ff8 100644
--- a/Packs/IvantiHeat/Scripts/IvantiHeatCloseIncidentExample/IvantiHeatCloseIncidentExample.yml
+++ b/Packs/IvantiHeat/Scripts/IvantiHeatCloseIncidentExample/IvantiHeatCloseIncidentExample.yml
@@ -13,7 +13,7 @@ args:
description: Incident object ID.
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
tests:
diff --git a/Packs/IvantiHeat/Scripts/IvantiHeatCreateIncidentExample/IvantiHeatCreateIncidentExample.yml b/Packs/IvantiHeat/Scripts/IvantiHeatCreateIncidentExample/IvantiHeatCreateIncidentExample.yml
index deb2c9ade622..7b0295092725 100644
--- a/Packs/IvantiHeat/Scripts/IvantiHeatCreateIncidentExample/IvantiHeatCreateIncidentExample.yml
+++ b/Packs/IvantiHeat/Scripts/IvantiHeatCreateIncidentExample/IvantiHeatCreateIncidentExample.yml
@@ -31,7 +31,7 @@ args:
description: Incident customer.
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
tests:
diff --git a/Packs/IvantiHeat/Scripts/IvantiHeatCreateProblemExample/IvantiHeatCreateProblemExample.yml b/Packs/IvantiHeat/Scripts/IvantiHeatCreateProblemExample/IvantiHeatCreateProblemExample.yml
index e8c7937dc0f7..4dcebe199ebc 100644
--- a/Packs/IvantiHeat/Scripts/IvantiHeatCreateProblemExample/IvantiHeatCreateProblemExample.yml
+++ b/Packs/IvantiHeat/Scripts/IvantiHeatCreateProblemExample/IvantiHeatCreateProblemExample.yml
@@ -28,7 +28,7 @@ args:
description: Problem description.
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
tests:
diff --git a/Packs/IvantiHeat/pack_metadata.json b/Packs/IvantiHeat/pack_metadata.json
index 628989fcfaf3..7d3b01b26a93 100644
--- a/Packs/IvantiHeat/pack_metadata.json
+++ b/Packs/IvantiHeat/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Ivanti Heat",
"description": "Use Ivanti Heat integration to manage issues and create Demisto incidents from ivanti.",
"support": "xsoar",
- "currentVersion": "1.0.9",
+ "currentVersion": "1.0.10",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/LogRhythmRest/Integrations/LogRhythmRest/LogRhythmRest.yml b/Packs/LogRhythmRest/Integrations/LogRhythmRest/LogRhythmRest.yml
index a8a4cc88f803..73b07189378c 100644
--- a/Packs/LogRhythmRest/Integrations/LogRhythmRest/LogRhythmRest.yml
+++ b/Packs/LogRhythmRest/Integrations/LogRhythmRest/LogRhythmRest.yml
@@ -1880,7 +1880,7 @@ script:
script: '-'
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
tests:
- LogRhythm REST test
fromversion: 5.0.0
diff --git a/Packs/LogRhythmRest/ReleaseNotes/2_0_22.md b/Packs/LogRhythmRest/ReleaseNotes/2_0_22.md
new file mode 100644
index 000000000000..b043319e0e9d
--- /dev/null
+++ b/Packs/LogRhythmRest/ReleaseNotes/2_0_22.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### LogRhythmRest
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/LogRhythmRest/pack_metadata.json b/Packs/LogRhythmRest/pack_metadata.json
index 221ce977df7e..268982492041 100644
--- a/Packs/LogRhythmRest/pack_metadata.json
+++ b/Packs/LogRhythmRest/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "LogRhythm",
"description": "LogRhythm security intelligence.",
"support": "xsoar",
- "currentVersion": "2.0.21",
+ "currentVersion": "2.0.22",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/ML/ReleaseNotes/1_4_10.md b/Packs/ML/ReleaseNotes/1_4_10.md
new file mode 100644
index 000000000000..f545b94b1225
--- /dev/null
+++ b/Packs/ML/ReleaseNotes/1_4_10.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### ExtendQueryBasedOnPhishingLabels
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/ML/Scripts/ExtendQueryBasedOnPhishingLabels/ExtendQueryBasedOnPhishingLabels.yml b/Packs/ML/Scripts/ExtendQueryBasedOnPhishingLabels/ExtendQueryBasedOnPhishingLabels.yml
index d07179b8bf6a..3362a20b5e2d 100644
--- a/Packs/ML/Scripts/ExtendQueryBasedOnPhishingLabels/ExtendQueryBasedOnPhishingLabels.yml
+++ b/Packs/ML/Scripts/ExtendQueryBasedOnPhishingLabels/ExtendQueryBasedOnPhishingLabels.yml
@@ -23,7 +23,7 @@ tags:
- ml
timeout: '0'
type: python
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
tests:
diff --git a/Packs/ML/pack_metadata.json b/Packs/ML/pack_metadata.json
index d7f87bfafbb7..4ac67ca6f356 100644
--- a/Packs/ML/pack_metadata.json
+++ b/Packs/ML/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Machine Learning",
"description": "Help to manage machine learning models in Cortex XSOAR",
"support": "xsoar",
- "currentVersion": "1.4.9",
+ "currentVersion": "1.4.10",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/MajorBreachesInvestigationandResponse/ReleaseNotes/1_6_37.md b/Packs/MajorBreachesInvestigationandResponse/ReleaseNotes/1_6_37.md
new file mode 100644
index 000000000000..ec9b60f12d75
--- /dev/null
+++ b/Packs/MajorBreachesInvestigationandResponse/ReleaseNotes/1_6_37.md
@@ -0,0 +1,27 @@
+
+#### Scripts
+
+##### RapidBreachResponse-MitigationTasksCount-Widget
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### RapidBreachResponse-CompletedTasksCount-Widget
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### RapidBreachResponse-RemediationTasksCount-Widget
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### RapidBreachResponse-HuntingTasksCount-Widget
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### RapidBreachResponse-TotalIndicatorCount-Widget
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### RapidBreachResponse-EradicationTasksCount-Widget
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### RapidBreachResponse-RemainingTasksCount-Widget
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### RapidBreachResponse-TotalTasksCount-Widget
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseCompletedTasksCountWidget/RapidBreachResponseCompletedTasksCountWidget.yml b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseCompletedTasksCountWidget/RapidBreachResponseCompletedTasksCountWidget.yml
index 42365f6ea0f9..1285d16a05f4 100644
--- a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseCompletedTasksCountWidget/RapidBreachResponseCompletedTasksCountWidget.yml
+++ b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseCompletedTasksCountWidget/RapidBreachResponseCompletedTasksCountWidget.yml
@@ -1,7 +1,7 @@
commonfields:
id: RapidBreachResponse-CompletedTasksCount-Widget
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: RapidBreachResponse-CompletedTasksCount-Widget
runas: DBotWeakRole
diff --git a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseEradicationTasksCountWidget/RapidBreachResponseEradicationTasksCountWidget.yml b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseEradicationTasksCountWidget/RapidBreachResponseEradicationTasksCountWidget.yml
index d70c66e99c89..e76db2ada9fa 100644
--- a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseEradicationTasksCountWidget/RapidBreachResponseEradicationTasksCountWidget.yml
+++ b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseEradicationTasksCountWidget/RapidBreachResponseEradicationTasksCountWidget.yml
@@ -1,7 +1,7 @@
commonfields:
id: RapidBreachResponse-EradicationTasksCount-Widget
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: RapidBreachResponse-EradicationTasksCount-Widget
runas: DBotWeakRole
diff --git a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseHuntingTasksCountWidget/RapidBreachResponseHuntingTasksCountWidget.yml b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseHuntingTasksCountWidget/RapidBreachResponseHuntingTasksCountWidget.yml
index 5811ad89874c..a566e8fd2f15 100644
--- a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseHuntingTasksCountWidget/RapidBreachResponseHuntingTasksCountWidget.yml
+++ b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseHuntingTasksCountWidget/RapidBreachResponseHuntingTasksCountWidget.yml
@@ -1,7 +1,7 @@
commonfields:
id: RapidBreachResponse-HuntingTasksCount-Widget
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: RapidBreachResponse-HuntingTasksCount-Widget
runas: DBotWeakRole
diff --git a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseMitigationTasksCountWidget/RapidBreachResponseMitigationTasksCountWidget.yml b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseMitigationTasksCountWidget/RapidBreachResponseMitigationTasksCountWidget.yml
index 64260b58cb7b..43b7d0591b2a 100644
--- a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseMitigationTasksCountWidget/RapidBreachResponseMitigationTasksCountWidget.yml
+++ b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseMitigationTasksCountWidget/RapidBreachResponseMitigationTasksCountWidget.yml
@@ -1,7 +1,7 @@
commonfields:
id: RapidBreachResponse-MitigationTasksCount-Widget
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: RapidBreachResponse-MitigationTasksCount-Widget
runas: DBotWeakRole
diff --git a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseRemainingTasksCountWidget/RapidBreachResponseRemainingTasksCountWidget.yml b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseRemainingTasksCountWidget/RapidBreachResponseRemainingTasksCountWidget.yml
index 34946ac03cf2..f367ca8026e8 100644
--- a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseRemainingTasksCountWidget/RapidBreachResponseRemainingTasksCountWidget.yml
+++ b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseRemainingTasksCountWidget/RapidBreachResponseRemainingTasksCountWidget.yml
@@ -1,7 +1,7 @@
commonfields:
id: RapidBreachResponse-RemainingTasksCount-Widget
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: RapidBreachResponse-RemainingTasksCount-Widget
runas: DBotWeakRole
diff --git a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseRemediationTasksCountWidget/RapidBreachResponseRemediationTasksCountWidget.yml b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseRemediationTasksCountWidget/RapidBreachResponseRemediationTasksCountWidget.yml
index 524eb20c355a..3c1d3506f17c 100644
--- a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseRemediationTasksCountWidget/RapidBreachResponseRemediationTasksCountWidget.yml
+++ b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseRemediationTasksCountWidget/RapidBreachResponseRemediationTasksCountWidget.yml
@@ -1,7 +1,7 @@
commonfields:
id: RapidBreachResponse-RemediationTasksCount-Widget
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: RapidBreachResponse-RemediationTasksCount-Widget
runas: DBotWeakRole
diff --git a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseTotalIndicatorCountWidget/RapidBreachResponseTotalIndicatorCountWidget.yml b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseTotalIndicatorCountWidget/RapidBreachResponseTotalIndicatorCountWidget.yml
index dc392ae26351..ac4104e3a859 100644
--- a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseTotalIndicatorCountWidget/RapidBreachResponseTotalIndicatorCountWidget.yml
+++ b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseTotalIndicatorCountWidget/RapidBreachResponseTotalIndicatorCountWidget.yml
@@ -1,7 +1,7 @@
commonfields:
id: RapidBreachResponse-TotalIndicatorCount-Widget
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: RapidBreachResponse-TotalIndicatorCount-Widget
runas: DBotWeakRole
diff --git a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseTotalTasksCountWidget/RapidBreachResponseTotalTasksCountWidget.yml b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseTotalTasksCountWidget/RapidBreachResponseTotalTasksCountWidget.yml
index 01958b60ec21..4c74f82d6fd0 100644
--- a/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseTotalTasksCountWidget/RapidBreachResponseTotalTasksCountWidget.yml
+++ b/Packs/MajorBreachesInvestigationandResponse/Scripts/RapidBreachResponseTotalTasksCountWidget/RapidBreachResponseTotalTasksCountWidget.yml
@@ -1,7 +1,7 @@
commonfields:
id: RapidBreachResponse-TotalTasksCount-Widget
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: RapidBreachResponse-TotalTasksCount-Widget
runas: DBotWeakRole
diff --git a/Packs/MajorBreachesInvestigationandResponse/pack_metadata.json b/Packs/MajorBreachesInvestigationandResponse/pack_metadata.json
index e3c526552258..d86e39ab9552 100644
--- a/Packs/MajorBreachesInvestigationandResponse/pack_metadata.json
+++ b/Packs/MajorBreachesInvestigationandResponse/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Rapid Breach Response",
"description": "This content Pack helps you collect, investigate, and remediate incidents related to major breaches.",
"support": "xsoar",
- "currentVersion": "1.6.36",
+ "currentVersion": "1.6.37",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Microsoft365Defender/ReleaseNotes/4_5_17.md b/Packs/Microsoft365Defender/ReleaseNotes/4_5_17.md
new file mode 100644
index 000000000000..f7e4d0409fe1
--- /dev/null
+++ b/Packs/Microsoft365Defender/ReleaseNotes/4_5_17.md
@@ -0,0 +1,9 @@
+
+#### Scripts
+
+##### MS365DefenderUserListToTable
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### MS365DefenderCountIncidentCategories
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Microsoft365Defender/Scripts/MS365DefenderCountIncidentCategories/MS365DefenderCountIncidentCategories.yml b/Packs/Microsoft365Defender/Scripts/MS365DefenderCountIncidentCategories/MS365DefenderCountIncidentCategories.yml
index a90fff2b3970..e0c6b9286a01 100644
--- a/Packs/Microsoft365Defender/Scripts/MS365DefenderCountIncidentCategories/MS365DefenderCountIncidentCategories.yml
+++ b/Packs/Microsoft365Defender/Scripts/MS365DefenderCountIncidentCategories/MS365DefenderCountIncidentCategories.yml
@@ -5,7 +5,7 @@ comment: count the categories of alerts in given incident
commonfields:
id: MS365DefenderCountIncidentCategories
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: MS365DefenderCountIncidentCategories
runas: DBotWeakRole
diff --git a/Packs/Microsoft365Defender/Scripts/MS365DefenderUserListToTable/MS365DefenderUserListToTable.yml b/Packs/Microsoft365Defender/Scripts/MS365DefenderUserListToTable/MS365DefenderUserListToTable.yml
index 9e419a2d3fa8..a9ae8ed2199f 100644
--- a/Packs/Microsoft365Defender/Scripts/MS365DefenderUserListToTable/MS365DefenderUserListToTable.yml
+++ b/Packs/Microsoft365Defender/Scripts/MS365DefenderUserListToTable/MS365DefenderUserListToTable.yml
@@ -4,7 +4,7 @@ args:
commonfields:
id: MS365DefenderUserListToTable
version: -1
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
enabled: true
name: MS365DefenderUserListToTable
runas: DBotWeakRole
diff --git a/Packs/Microsoft365Defender/pack_metadata.json b/Packs/Microsoft365Defender/pack_metadata.json
index 606f0a02a00f..6c12fe360418 100644
--- a/Packs/Microsoft365Defender/pack_metadata.json
+++ b/Packs/Microsoft365Defender/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Microsoft 365 Defender",
"description": "Microsoft 365 Defender is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.",
"support": "xsoar",
- "currentVersion": "4.5.16",
+ "currentVersion": "4.5.17",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/PrismaAccess/Integrations/PrismaAccessEgressIPFeed/PrismaAccessEgressIPFeed.yml b/Packs/PrismaAccess/Integrations/PrismaAccessEgressIPFeed/PrismaAccessEgressIPFeed.yml
index 5f4bbfb66a4f..a82c6007b400 100644
--- a/Packs/PrismaAccess/Integrations/PrismaAccessEgressIPFeed/PrismaAccessEgressIPFeed.yml
+++ b/Packs/PrismaAccess/Integrations/PrismaAccessEgressIPFeed/PrismaAccessEgressIPFeed.yml
@@ -147,7 +147,7 @@ script:
description: Prisma Access Egress IP zone
type: string
description: Gets indicators from the feed.
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
feed: true
subtype: python3
fromversion: 5.5.0
diff --git a/Packs/PrismaAccess/ReleaseNotes/2_1_4.md b/Packs/PrismaAccess/ReleaseNotes/2_1_4.md
new file mode 100644
index 000000000000..11d311f40deb
--- /dev/null
+++ b/Packs/PrismaAccess/ReleaseNotes/2_1_4.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Prisma Access Egress IP feed
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/PrismaAccess/pack_metadata.json b/Packs/PrismaAccess/pack_metadata.json
index 9e70b313d833..7d178b703be5 100644
--- a/Packs/PrismaAccess/pack_metadata.json
+++ b/Packs/PrismaAccess/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Prisma SASE by Palo Alto Networks",
"description": "Integrate with Palo Alto Networks Prisma SASE to query activity and take actions.",
"support": "xsoar",
- "currentVersion": "2.1.3",
+ "currentVersion": "2.1.4",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/ProofpointTAP/ReleaseNotes/1_2_11.md b/Packs/ProofpointTAP/ReleaseNotes/1_2_11.md
new file mode 100644
index 000000000000..7a9f53f5dd65
--- /dev/null
+++ b/Packs/ProofpointTAP/ReleaseNotes/1_2_11.md
@@ -0,0 +1,9 @@
+
+#### Scripts
+
+##### ProofpointTapTopClickers
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### ProofpointTAPMostAttackedUsers
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/ProofpointTAP/Scripts/ProofpointTAPMostAttackedUsers/ProofpointTAPMostAttackedUsers.yml b/Packs/ProofpointTAP/Scripts/ProofpointTAPMostAttackedUsers/ProofpointTAPMostAttackedUsers.yml
index 49aca6cee352..270e33d24b10 100644
--- a/Packs/ProofpointTAP/Scripts/ProofpointTAPMostAttackedUsers/ProofpointTAPMostAttackedUsers.yml
+++ b/Packs/ProofpointTAP/Scripts/ProofpointTAPMostAttackedUsers/ProofpointTAPMostAttackedUsers.yml
@@ -10,7 +10,7 @@ enabled: true
comment: Exports a list of Proofpoint TAP most attacked users to the Cortex XSOAR widget.
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
tests:
diff --git a/Packs/ProofpointTAP/Scripts/ProofpointTapTopClickers/ProofpointTapTopClickers.yml b/Packs/ProofpointTAP/Scripts/ProofpointTapTopClickers/ProofpointTapTopClickers.yml
index 4841b0ec3b4d..f2842f8073af 100644
--- a/Packs/ProofpointTAP/Scripts/ProofpointTapTopClickers/ProofpointTapTopClickers.yml
+++ b/Packs/ProofpointTAP/Scripts/ProofpointTapTopClickers/ProofpointTapTopClickers.yml
@@ -10,7 +10,7 @@ enabled: true
comment: Exports a list of Proofpoint TAP top clickers to the Cortex XSOAR widget.
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
tests:
diff --git a/Packs/ProofpointTAP/pack_metadata.json b/Packs/ProofpointTAP/pack_metadata.json
index 110e0d9a499c..08ee2657e954 100644
--- a/Packs/ProofpointTAP/pack_metadata.json
+++ b/Packs/ProofpointTAP/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Proofpoint TAP",
"description": "Use the Proofpoint Targeted Attack Protection (TAP) integration to protect against and provide additional visibility into phishing and other malicious email attacks.",
"support": "xsoar",
- "currentVersion": "1.2.10",
+ "currentVersion": "1.2.11",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Salesforce/ReleaseNotes/2_0_23.md b/Packs/Salesforce/ReleaseNotes/2_0_23.md
new file mode 100644
index 000000000000..476f6fee1931
--- /dev/null
+++ b/Packs/Salesforce/ReleaseNotes/2_0_23.md
@@ -0,0 +1,9 @@
+
+#### Scripts
+
+##### generate_profile_id
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### generate_timezonesidkey
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Salesforce/Scripts/GenerateProfileId/GenerateProfileId.yml b/Packs/Salesforce/Scripts/GenerateProfileId/GenerateProfileId.yml
index 231c42eca423..0ea76e9b48c8 100644
--- a/Packs/Salesforce/Scripts/GenerateProfileId/GenerateProfileId.yml
+++ b/Packs/Salesforce/Scripts/GenerateProfileId/GenerateProfileId.yml
@@ -10,7 +10,7 @@ comment: Generate profileId by user data.
enabled: true
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.0.0
tests:
diff --git a/Packs/Salesforce/Scripts/GenerateTimeZone/GenerateTimeZone.yml b/Packs/Salesforce/Scripts/GenerateTimeZone/GenerateTimeZone.yml
index be508870d0f0..2bedf7aaca29 100644
--- a/Packs/Salesforce/Scripts/GenerateTimeZone/GenerateTimeZone.yml
+++ b/Packs/Salesforce/Scripts/GenerateTimeZone/GenerateTimeZone.yml
@@ -10,7 +10,7 @@ comment: Generate timezonesidkey by user data.
enabled: true
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.0.0
tests:
diff --git a/Packs/Salesforce/pack_metadata.json b/Packs/Salesforce/pack_metadata.json
index e4f039d5904a..a1aea515e7aa 100644
--- a/Packs/Salesforce/pack_metadata.json
+++ b/Packs/Salesforce/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Salesforce",
"description": "CRM Services",
"support": "xsoar",
- "currentVersion": "2.0.22",
+ "currentVersion": "2.0.23",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/ServiceNow/ReleaseNotes/2_5_53.md b/Packs/ServiceNow/ReleaseNotes/2_5_53.md
new file mode 100644
index 000000000000..8a27eb04f9a0
--- /dev/null
+++ b/Packs/ServiceNow/ReleaseNotes/2_5_53.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### ServiceNowIncidentStatus
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/ServiceNow/Scripts/ServiceNowIncidentStatus/ServiceNowIncidentStatus.yml b/Packs/ServiceNow/Scripts/ServiceNowIncidentStatus/ServiceNowIncidentStatus.yml
index f288e4da7712..4c4e284e7459 100644
--- a/Packs/ServiceNow/Scripts/ServiceNowIncidentStatus/ServiceNowIncidentStatus.yml
+++ b/Packs/ServiceNow/Scripts/ServiceNowIncidentStatus/ServiceNowIncidentStatus.yml
@@ -13,7 +13,7 @@ comment: |
enabled: true
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
tests:
- No tests (auto formatted)
diff --git a/Packs/ServiceNow/pack_metadata.json b/Packs/ServiceNow/pack_metadata.json
index b519b2b3771b..24af09c0df5f 100644
--- a/Packs/ServiceNow/pack_metadata.json
+++ b/Packs/ServiceNow/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "ServiceNow",
"description": "Use The ServiceNow IT Service Management (ITSM) solution to modernize the way you manage and deliver services to your users.",
"support": "xsoar",
- "currentVersion": "2.5.52",
+ "currentVersion": "2.5.53",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Slack/Integrations/Slack_IAM/Slack_IAM.yml b/Packs/Slack/Integrations/Slack_IAM/Slack_IAM.yml
index c33e25bdb486..a8cb48fc834f 100644
--- a/Packs/Slack/Integrations/Slack_IAM/Slack_IAM.yml
+++ b/Packs/Slack/Integrations/Slack_IAM/Slack_IAM.yml
@@ -356,7 +356,7 @@ script:
- contextPath: UpdateGroup.errorMessage
description: Reason why the API failed.
type: String
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/Slack/ReleaseNotes/3_4_5.md b/Packs/Slack/ReleaseNotes/3_4_5.md
new file mode 100644
index 000000000000..9dded9568291
--- /dev/null
+++ b/Packs/Slack/ReleaseNotes/3_4_5.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Slack IAM
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Slack/pack_metadata.json b/Packs/Slack/pack_metadata.json
index c2729f5e97b6..ec314bf3d144 100644
--- a/Packs/Slack/pack_metadata.json
+++ b/Packs/Slack/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Slack",
"description": "Interact with Slack API - collect logs, send messages and notifications to your Slack team.",
"support": "xsoar",
- "currentVersion": "3.4.4",
+ "currentVersion": "3.4.5",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Telegram/Integrations/Telegram/Telegram.yml b/Packs/Telegram/Integrations/Telegram/Telegram.yml
index b7076b8c78e6..847fa3faab7c 100644
--- a/Packs/Telegram/Integrations/Telegram/Telegram.yml
+++ b/Packs/Telegram/Integrations/Telegram/Telegram.yml
@@ -36,7 +36,7 @@ script:
name: telegram-send-message
- description: List users
name: telegram-list-users
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
runonce: false
script: '-'
type: python
diff --git a/Packs/Telegram/ReleaseNotes/1_0_8.md b/Packs/Telegram/ReleaseNotes/1_0_8.md
new file mode 100644
index 000000000000..be2c7f867505
--- /dev/null
+++ b/Packs/Telegram/ReleaseNotes/1_0_8.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Telegram (Beta)
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Telegram/pack_metadata.json b/Packs/Telegram/pack_metadata.json
index 3822832b4587..ecb7f29d64b6 100644
--- a/Packs/Telegram/pack_metadata.json
+++ b/Packs/Telegram/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Telegram (Beta)",
"description": "Telegram integration",
"support": "xsoar",
- "currentVersion": "1.0.7",
+ "currentVersion": "1.0.8",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/ThreatIntelReports/ReleaseNotes/1_0_13.md b/Packs/ThreatIntelReports/ReleaseNotes/1_0_13.md
new file mode 100644
index 000000000000..1f75c856a909
--- /dev/null
+++ b/Packs/ThreatIntelReports/ReleaseNotes/1_0_13.md
@@ -0,0 +1,9 @@
+
+#### Scripts
+
+##### UnpublishThreatIntelReport
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### PublishThreatIntelReport
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/ThreatIntelReports/Scripts/PublishThreatIntelReport/PublishThreatIntelReport.yml b/Packs/ThreatIntelReports/Scripts/PublishThreatIntelReport/PublishThreatIntelReport.yml
index 76008f94b6b3..735299aa0296 100644
--- a/Packs/ThreatIntelReports/Scripts/PublishThreatIntelReport/PublishThreatIntelReport.yml
+++ b/Packs/ThreatIntelReports/Scripts/PublishThreatIntelReport/PublishThreatIntelReport.yml
@@ -14,7 +14,7 @@ args:
description: The Threat Intel Report object to publish.
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.5.0
tests:
diff --git a/Packs/ThreatIntelReports/Scripts/UnpublishThreatIntelReport/UnpublishThreatIntelReport.yml b/Packs/ThreatIntelReports/Scripts/UnpublishThreatIntelReport/UnpublishThreatIntelReport.yml
index 0bb31b37fbd5..97e4ba363408 100644
--- a/Packs/ThreatIntelReports/Scripts/UnpublishThreatIntelReport/UnpublishThreatIntelReport.yml
+++ b/Packs/ThreatIntelReports/Scripts/UnpublishThreatIntelReport/UnpublishThreatIntelReport.yml
@@ -14,7 +14,7 @@ args:
description: The Threat Intel Report object to unpublish.
scripttarget: 0
subtype: python3
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 6.5.0
tests:
diff --git a/Packs/ThreatIntelReports/pack_metadata.json b/Packs/ThreatIntelReports/pack_metadata.json
index cd58b7020853..09f0369edf8b 100644
--- a/Packs/ThreatIntelReports/pack_metadata.json
+++ b/Packs/ThreatIntelReports/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Threat Intel Reports (BETA)",
"description": "Threat Intel Reports gives the user the ability to create, review, publish, and export threat intelligence reports.",
"support": "xsoar",
- "currentVersion": "1.0.12",
+ "currentVersion": "1.0.13",
"serverMinVersion": "6.5.0",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
diff --git a/Packs/ThreatMiner/Integrations/ThreatMiner/ThreatMiner.yml b/Packs/ThreatMiner/Integrations/ThreatMiner/ThreatMiner.yml
index 2aef786b6c3c..7e10a8d0d525 100644
--- a/Packs/ThreatMiner/Integrations/ThreatMiner/ThreatMiner.yml
+++ b/Packs/ThreatMiner/Integrations/ThreatMiner/ThreatMiner.yml
@@ -292,7 +292,7 @@ script:
type: string
description: Retrieves data from ThreatMiner about a specified file.
runonce: false
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
tests:
- ThreatMiner-Test
fromversion: 5.0.0
diff --git a/Packs/ThreatMiner/ReleaseNotes/1_0_13.md b/Packs/ThreatMiner/ReleaseNotes/1_0_13.md
new file mode 100644
index 000000000000..4ba89044cc9f
--- /dev/null
+++ b/Packs/ThreatMiner/ReleaseNotes/1_0_13.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### ThreatMiner
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/ThreatMiner/pack_metadata.json b/Packs/ThreatMiner/pack_metadata.json
index 75fc7b6b59da..84eec9850ca1 100644
--- a/Packs/ThreatMiner/pack_metadata.json
+++ b/Packs/ThreatMiner/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "ThreatMiner",
"description": "Data Mining for Threat Intelligence",
"support": "xsoar",
- "currentVersion": "1.0.12",
+ "currentVersion": "1.0.13",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Troubleshoot/ReleaseNotes/2_0_18.md b/Packs/Troubleshoot/ReleaseNotes/2_0_18.md
new file mode 100644
index 000000000000..c8222b42ee06
--- /dev/null
+++ b/Packs/Troubleshoot/ReleaseNotes/2_0_18.md
@@ -0,0 +1,15 @@
+
+#### Scripts
+
+##### TroubleshootGetCommandandArgs
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### TroubleshootAggregateResults
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### TroubleshootExecuteCommand
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
+##### TroubleshootInstanceField
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/Troubleshoot/Scripts/TroubleshootAggregateResults/TroubleshootAggregateResults.yml b/Packs/Troubleshoot/Scripts/TroubleshootAggregateResults/TroubleshootAggregateResults.yml
index 6c75b9f5e9da..b94e1f78d4fd 100644
--- a/Packs/Troubleshoot/Scripts/TroubleshootAggregateResults/TroubleshootAggregateResults.yml
+++ b/Packs/Troubleshoot/Scripts/TroubleshootAggregateResults/TroubleshootAggregateResults.yml
@@ -32,7 +32,7 @@ tags:
- troubleshoot
timeout: '0'
type: python
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
fromversion: 5.0.0
tests:
- No tests (auto formatted)
diff --git a/Packs/Troubleshoot/Scripts/TroubleshootExecuteCommand/TroubleshootExecuteCommand.yml b/Packs/Troubleshoot/Scripts/TroubleshootExecuteCommand/TroubleshootExecuteCommand.yml
index 63e4316eb988..065fa959a2f1 100644
--- a/Packs/Troubleshoot/Scripts/TroubleshootExecuteCommand/TroubleshootExecuteCommand.yml
+++ b/Packs/Troubleshoot/Scripts/TroubleshootExecuteCommand/TroubleshootExecuteCommand.yml
@@ -58,7 +58,7 @@ tags:
- troubleshoot
timeout: '0'
type: python
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
fromversion: 5.0.0
tests:
- No tests (auto formatted)
diff --git a/Packs/Troubleshoot/Scripts/TroubleshootGetCommandandArgs/TroubleshootGetCommandandArgs.yml b/Packs/Troubleshoot/Scripts/TroubleshootGetCommandandArgs/TroubleshootGetCommandandArgs.yml
index 28d4f48c167b..962621009b60 100644
--- a/Packs/Troubleshoot/Scripts/TroubleshootGetCommandandArgs/TroubleshootGetCommandandArgs.yml
+++ b/Packs/Troubleshoot/Scripts/TroubleshootGetCommandandArgs/TroubleshootGetCommandandArgs.yml
@@ -27,7 +27,7 @@ tags:
- troubleshoot
timeout: '0'
type: python
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
fromversion: 5.0.0
tests:
- No tests (auto formatted)
diff --git a/Packs/Troubleshoot/Scripts/TroubleshootInstanceField/TroubleshootInstanceField.yml b/Packs/Troubleshoot/Scripts/TroubleshootInstanceField/TroubleshootInstanceField.yml
index efd01e44b744..91a6c5b38c60 100644
--- a/Packs/Troubleshoot/Scripts/TroubleshootInstanceField/TroubleshootInstanceField.yml
+++ b/Packs/Troubleshoot/Scripts/TroubleshootInstanceField/TroubleshootInstanceField.yml
@@ -10,7 +10,7 @@ enabled: true
scripttarget: 0
subtype: python3
comment: Populates the InstanceName field with active instances.
-dockerimage: demisto/python3:3.10.12.63474
+dockerimage: demisto/python3:3.10.13.86272
runas: DBotWeakRole
fromversion: 5.0.0
tests:
diff --git a/Packs/Troubleshoot/pack_metadata.json b/Packs/Troubleshoot/pack_metadata.json
index 2a85ac627b3d..d32f6c66be5b 100644
--- a/Packs/Troubleshoot/pack_metadata.json
+++ b/Packs/Troubleshoot/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Troubleshoot",
"description": "Use this pack to troubleshoot your environment.",
"support": "xsoar",
- "currentVersion": "2.0.17",
+ "currentVersion": "2.0.18",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/WhatIsMyBrowser/Integrations/WhatIsMyBrowser/WhatIsMyBrowser.yml b/Packs/WhatIsMyBrowser/Integrations/WhatIsMyBrowser/WhatIsMyBrowser.yml
index c0df5bc1f3a5..debe50d1ac45 100644
--- a/Packs/WhatIsMyBrowser/Integrations/WhatIsMyBrowser/WhatIsMyBrowser.yml
+++ b/Packs/WhatIsMyBrowser/Integrations/WhatIsMyBrowser/WhatIsMyBrowser.yml
@@ -66,7 +66,7 @@ script:
type: string
description: Parses a User Agent string
subtype: python3
- dockerimage: demisto/python3:3.10.12.63474
+ dockerimage: demisto/python3:3.10.13.86272
tests:
- WhatsMyBrowser-Test
fromversion: 5.0.0
diff --git a/Packs/WhatIsMyBrowser/ReleaseNotes/1_0_11.md b/Packs/WhatIsMyBrowser/ReleaseNotes/1_0_11.md
new file mode 100644
index 000000000000..0bfe176473d8
--- /dev/null
+++ b/Packs/WhatIsMyBrowser/ReleaseNotes/1_0_11.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### WhatIsMyBrowser
+
+- Updated the Docker image to: *demisto/python3:3.10.13.86272*.
diff --git a/Packs/WhatIsMyBrowser/pack_metadata.json b/Packs/WhatIsMyBrowser/pack_metadata.json
index 5058d77e08ab..618a6ee15ba0 100644
--- a/Packs/WhatIsMyBrowser/pack_metadata.json
+++ b/Packs/WhatIsMyBrowser/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "WhatIsMyBrowser",
"description": "Parse user agents and determine if they are malicious as well as enrich information about the agent",
"support": "xsoar",
- "currentVersion": "1.0.10",
+ "currentVersion": "1.0.11",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From c757613e8297abe2a669a49a419db983c758beb8 Mon Sep 17 00:00:00 2001
From: Michael Yochpaz <8832013+MichaelYochpaz@users.noreply.github.com>
Date: Sun, 18 Feb 2024 15:27:17 +0200
Subject: [PATCH 006/272] [Okta v2] Make API Token Non-required When Using
OAuth (#32877)
* Make API token optional and non-required when using OAuth
* Update documentation
* Bump version
* pre-commit
* Bump pack from version Okta to 3.2.11.
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Bump Docker version
* Fix mypy issues
* Fix release-notes
* Minor documentation improvement
* Minor fix
---------
Co-authored-by: Content Bot
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---
.../Scripts/OktaApiModule/OktaApiModule.py | 74 ++++++-------------
.../OktaApiModule/OktaApiModule_test.py | 11 +--
Packs/Okta/Integrations/Okta_v2/Okta_v2.py | 21 ++----
Packs/Okta/Integrations/Okta_v2/Okta_v2.yml | 20 ++---
.../Okta_v2/Okta_v2_description.md | 41 +++++-----
Packs/Okta/Integrations/Okta_v2/README.md | 54 +++++++-------
Packs/Okta/ReleaseNotes/3_2_11.md | 8 ++
Packs/Okta/pack_metadata.json | 2 +-
8 files changed, 98 insertions(+), 133 deletions(-)
create mode 100644 Packs/Okta/ReleaseNotes/3_2_11.md
diff --git a/Packs/ApiModules/Scripts/OktaApiModule/OktaApiModule.py b/Packs/ApiModules/Scripts/OktaApiModule/OktaApiModule.py
index a6ee4040d4a1..d6e0eb735409 100644
--- a/Packs/ApiModules/Scripts/OktaApiModule/OktaApiModule.py
+++ b/Packs/ApiModules/Scripts/OktaApiModule/OktaApiModule.py
@@ -1,10 +1,11 @@
from CommonServerPython import *
-import jwt
import uuid
from datetime import datetime, timedelta
from enum import Enum
+import jwt
+
TOKEN_EXPIRATION_TIME = 60 # In minutes. This value must be a maximum of only an hour (according to Okta's documentation).
TOKEN_RENEWAL_TIME_LIMIT = 60 # In seconds. The minimum time before the token expires to renew it.
@@ -26,13 +27,13 @@ class AuthType(Enum):
class OktaClient(BaseClient):
- def __init__(self, api_token: str, auth_type: AuthType = AuthType.API_TOKEN,
+ def __init__(self, auth_type: AuthType = AuthType.API_TOKEN, api_token: str | None = None,
client_id: str | None = None, scopes: list[str] | None = None, private_key: str | None = None,
jwt_algorithm: JWTAlgorithm | None = None, *args, **kwargs):
"""
Args:
- api_token (str): API token for authentication.
auth_type (AuthType, optional): The type of authentication to use.
+ api_token (str | None, optional): API token for authentication (required if 'auth_type' is AuthType.API_TOKEN).
client_id (str | None, optional): Client ID for OAuth authentication (required if 'auth_type' is AuthType.OAUTH).
scopes (list[str] | None, optional): A list of scopes to request for the token
(required if 'auth_type' is AuthType.OAUTH).
@@ -41,36 +42,37 @@ def __init__(self, api_token: str, auth_type: AuthType = AuthType.API_TOKEN,
(required if 'auth_type' is AuthType.OAUTH).
"""
super().__init__(*args, **kwargs)
- self.api_token = api_token
self.auth_type = auth_type
+ self.api_token = api_token
+
+ self.client_id = client_id
+ self.scopes = scopes
+ self.jwt_algorithm = jwt_algorithm
+ self.private_key = private_key
+
missing_required_params = []
+ if self.auth_type == AuthType.API_TOKEN and not api_token:
+ raise ValueError('API token is missing')
+
if self.auth_type == AuthType.OAUTH:
- if not client_id:
+ if not self.client_id:
missing_required_params.append('Client ID')
- if not scopes:
+ if not self.scopes:
missing_required_params.append('Scopes')
- if not jwt_algorithm:
+ if not self.jwt_algorithm:
missing_required_params.append('JWT algorithm')
- if not private_key:
+ if not self.private_key:
missing_required_params.append('Private key')
if missing_required_params:
raise ValueError(f'Required OAuth parameters are missing: {", ".join(missing_required_params)}')
- # Set type of variables non-optional after we assured they're assigned for mypy
- self.client_id: str = client_id # type: ignore
- self.scopes: list[str] = scopes # type: ignore
- self.private_key: str = private_key # type: ignore
- self.jwt_algorithm: JWTAlgorithm = jwt_algorithm # type: ignore
-
- self.initial_setup()
-
- def assign_app_role(self, client_id: str, role: str, auth_type: AuthType = AuthType.API_TOKEN) -> dict:
+ def assign_app_role(self, client_id: str, role: str, auth_type: AuthType) -> dict:
"""
Assign a role to a client application.
@@ -113,8 +115,8 @@ def generate_jwt_token(self, url: str) -> str:
'sub': self.client_id,
'jti': str(uuid.uuid4()),
},
- key=self.private_key,
- algorithm=self.jwt_algorithm.value,
+ key=self.private_key, # type: ignore[arg-type]
+ algorithm=self.jwt_algorithm.value, # type: ignore[union-attr]
)
def generate_oauth_token(self, scopes: list[str]) -> dict:
@@ -148,7 +150,7 @@ def generate_oauth_token(self, scopes: list[str]) -> dict:
def get_token(self):
"""
- Get an API token for authentication.
+ Get an OAuth token for authentication.
If there isn't an existing one, or the existing one is expired, a new one will be generated.
"""
expiration_time_format = '%Y-%m-%dT%H:%M:%S'
@@ -170,7 +172,7 @@ def get_token(self):
else:
demisto.debug('No existing token was found. A new token will be generated.')
- token_generation_response = self.generate_oauth_token(scopes=self.scopes)
+ token_generation_response = self.generate_oauth_token(scopes=self.scopes) # type: ignore[arg-type]
token: str = token_generation_response['access_token']
expires_in: int = token_generation_response['expires_in']
token_expiration = datetime.utcnow() + timedelta(seconds=expires_in)
@@ -182,36 +184,6 @@ def get_token(self):
return token
- def initial_setup(self):
- """
- Initial setup for the first time the integration is used.
- """
- integration_context = get_integration_context()
-
- if integration_context.get('initialized', False): # If the initial setup was already done, do nothing
- return
-
- if self.auth_type == AuthType.OAUTH:
- # Add "SUPER_ADMIN" role to client application, which is required for OAuth authentication
- try:
- self.assign_app_role(client_id=self.client_id, role="SUPER_ADMIN", auth_type=AuthType.API_TOKEN)
- demisto.debug("'SUPER_ADMIN' role has been assigned to the client application.")
-
- except DemistoException as e:
- # If the client application already has the "SUPER_ADMIN" role, ignore the error.
- # E0000090 Error code official docs description: Duplicate role assignment exception.
- if e.res.headers.get('content-type') == 'application/json' and e.res.json().get('errorCode') == 'E0000090':
- demisto.debug('The client application already has the "SUPER_ADMIN" role assigned.')
-
- else:
- raise e
-
- self.get_token()
-
- integration_context = get_integration_context()
- integration_context['initialized'] = True
- set_integration_context(integration_context)
-
def http_request(self, auth_type: AuthType | None = None, **kwargs):
"""
Override BaseClient._http_request() to automatically add authentication headers.
diff --git a/Packs/ApiModules/Scripts/OktaApiModule/OktaApiModule_test.py b/Packs/ApiModules/Scripts/OktaApiModule/OktaApiModule_test.py
index 3b61a355fc19..9f93279f92df 100644
--- a/Packs/ApiModules/Scripts/OktaApiModule/OktaApiModule_test.py
+++ b/Packs/ApiModules/Scripts/OktaApiModule/OktaApiModule_test.py
@@ -46,7 +46,7 @@ def test_okta_client_no_required_params():
OktaClient(
base_url='https://test.url',
api_token='X',
- auth_type=AuthType.NO_AUTH
+ auth_type=AuthType.API_TOKEN,
)
@@ -56,7 +56,6 @@ def test_assign_app_role(mocker):
When: Assigning a role to a client application
Then: Assure the call is made properly, and that the 'auth_type' parameter overrides the client's auth type.
"""
- mocker.patch.object(OktaClient, 'initial_setup')
client = OktaClient(
base_url='https://test.url',
api_token='X',
@@ -116,7 +115,6 @@ def test_generate_jwt_token(mocker):
When: Generating a JWT token
Then: Assure the token is generated correctly.
"""
- mocker.patch.object(OktaClient, 'initial_setup')
client = OktaClient(
base_url='https://test.url',
api_token='X',
@@ -169,7 +167,6 @@ def test_generate_oauth_token(mocker):
When: Generating an OAuth token
Then: Assure the token generation API call is called correctly.
"""
- mocker.patch.object(OktaClient, 'initial_setup')
client = OktaClient(
base_url='https://test.url',
api_token='X',
@@ -209,7 +206,6 @@ def test_get_token_create_new_token(mocker):
Then: Assure a new token is generated, and that the integration context is updated with the new token.
"""
import OktaApiModule
- mocker.patch.object(OktaClient, 'initial_setup')
client = OktaClient( # 'initial_setup' is called within the constructor
base_url='https://test.url',
api_token='X',
@@ -240,7 +236,6 @@ def test_get_token_use_existing(mocker):
Then: Assure the existing token is returned.
"""
import OktaApiModule
- mocker.patch.object(OktaClient, 'initial_setup')
client = OktaClient( # 'initial_setup' is called within the constructor
base_url='https://test.url',
api_token='X',
@@ -264,7 +259,6 @@ def test_get_token_regenerate_existing(mocker):
Then: Assure a new token is generated
"""
import OktaApiModule
- mocker.patch.object(OktaClient, 'initial_setup')
client = OktaClient( # 'initial_setup' is called within the constructor
base_url='https://test.url',
api_token='X',
@@ -291,7 +285,6 @@ def test_http_request_no_auth(mocker):
When: Making an API call with no authentication
Then: Assure the call is made without any authentication headers.
"""
- mocker.patch.object(OktaClient, 'initial_setup')
client = OktaClient(
base_url='https://test.url',
api_token='X',
@@ -322,7 +315,6 @@ def test_http_request_api_token_auth(mocker):
When: Making an API call with API token authentication
Then: Assure the call is made with the API token properly used in the 'Authorization' header.
"""
- mocker.patch.object(OktaClient, 'initial_setup')
client = OktaClient(
base_url='https://test.url',
api_token='X',
@@ -354,7 +346,6 @@ def test_http_request_oauth_auth(mocker):
When: Making an API call with OAuth authentication
Then: Assure the call is made with the JWT token properly used in the 'Authorization' header.
"""
- mocker.patch.object(OktaClient, 'initial_setup')
client = OktaClient(
base_url='https://test.url',
api_token='X',
diff --git a/Packs/Okta/Integrations/Okta_v2/Okta_v2.py b/Packs/Okta/Integrations/Okta_v2/Okta_v2.py
index a92b84a41afe..d41c71c98dd3 100644
--- a/Packs/Okta/Integrations/Okta_v2/Okta_v2.py
+++ b/Packs/Okta/Integrations/Okta_v2/Okta_v2.py
@@ -1371,18 +1371,8 @@ def delete_limit_param(url):
def main():
try:
params = demisto.params()
- base_url = params['url'].rstrip('/')
-
- api_token = params.get("credentials", {}).get("password") or params.get('apitoken')
-
- if not api_token:
- raise ValueError('Missing API token.')
-
- verify_certificate = not params.get('insecure', False)
- proxy = params.get('proxy', False)
demisto.debug(f'Command being called is {demisto.command()}')
-
commands = {
'test-module': module_test,
'okta-unlock-user': unlock_user_command,
@@ -1422,19 +1412,18 @@ def main():
}
command = demisto.command()
- auth_type = AuthType.OAUTH if argToBoolean(params.get('use_oauth', False)) else AuthType.API_TOKEN
client = Client(
- base_url=base_url,
- verify=verify_certificate,
+ base_url=params['url'].rstrip('/'),
+ verify=(not params.get('insecure', False)),
headers={
'Accept': 'application/json',
'Content-Type': 'application/json',
},
- proxy=proxy,
+ proxy=params.get('proxy', False),
ok_codes=(200, 201, 204),
- api_token=api_token,
- auth_type=auth_type,
+ api_token=params.get("credentials", {}).get("password") or params.get('apitoken'),
+ auth_type=AuthType.OAUTH if argToBoolean(params.get('use_oauth', False)) else AuthType.API_TOKEN,
client_id=params.get('client_id'),
scopes=OAUTH_TOKEN_SCOPES,
private_key=params.get('private_key'),
diff --git a/Packs/Okta/Integrations/Okta_v2/Okta_v2.yml b/Packs/Okta/Integrations/Okta_v2/Okta_v2.yml
index 25404e4572a5..5f8981cb3fa9 100644
--- a/Packs/Okta/Integrations/Okta_v2/Okta_v2.yml
+++ b/Packs/Okta/Integrations/Okta_v2/Okta_v2.yml
@@ -37,13 +37,13 @@ configuration:
required: false
additionalinfo: Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab.
- display: Private Key
- additionalinfo: Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab.
+ additionalinfo: In PEM format. Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab.
name: private_key
type: 14
section: Connect
required: false
-- display: JWT Encoding Algorithm
- additionalinfo: Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab.
+- display: JWT Signing Algorithm
+ additionalinfo: Algorithm to sign generated JWT tokens with. Doesn't affect integration's functionality. Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab.
name: jwt_algorithm
type: 15
section: Connect
@@ -340,13 +340,13 @@ script:
- arguments:
- description: "The cursor in which to retrive the results from and on. if the query didn't reach the end of results, the tag can be obtained from the bottom of the grid in the readable output, or in the context path Okta.User.tag."
name: after
- - description: The maximum number of results to return, the default is 200.
+ - description: The maximum number of results to return.
name: limit
default: true
defaultValue: '200'
- auto: PREDEFINED
defaultValue: 'false'
- description: Whether to return extended user information. Can be "true" or "false". The default is "false".
+ description: Whether to return extended user information.
name: verbose
predefined:
- 'true'
@@ -1417,16 +1417,16 @@ script:
name: okta-create-group
outputs:
- contextPath: OktaGroup.ID
- description: Group ID in Okta,.
+ description: Group ID in Okta.
type: Unknown
- contextPath: OktaGroup.Name
- description: Group name in Okta,.
+ description: Group name in Okta.
type: Unknown
- contextPath: OktaGroup.Description
- description: Group description in Okta,.
+ description: Group description in Okta.
type: Unknown
- contextPath: OktaGroup.Type
- description: Group type in Okta,.
+ description: Group type in Okta.
type: Unknown
- arguments:
- description: Name of the group to assign to the app.
@@ -1485,7 +1485,7 @@ script:
type: String
- description: Reset OAuth authentication data (authentication process will start from the beginning, and a new token will be generated).
name: okta-auth-reset
- dockerimage: demisto/crypto:1.0.0.83343
+ dockerimage: demisto/crypto:1.0.0.87358
runonce: false
script: ""
subtype: python3
diff --git a/Packs/Okta/Integrations/Okta_v2/Okta_v2_description.md b/Packs/Okta/Integrations/Okta_v2/Okta_v2_description.md
index c9422dd33268..01472d28134e 100644
--- a/Packs/Okta/Integrations/Okta_v2/Okta_v2_description.md
+++ b/Packs/Okta/Integrations/Okta_v2/Okta_v2_description.md
@@ -2,16 +2,15 @@
Okta API tokens are used to authenticate requests to Okta APIs.
### Prerequisites
-1. Sign in to your Okta organization as a user with administrator privileges.
-2. In the Admin Console, select **Security** > **API** from the menu and then select the **Tokens** tab.
+1. Sign in to your Okta organization as a user **with administrator privileges**.
+2. In the Admin Console, select **Security** > **API** from the menu, and then select the **Tokens** tab.
3. Click **Create Token**.
4. Name your token and click **Create Token**.
#### Notes
-- API tokens have the same permissions as the user who creates them, and if the user permissions change, the API token permissions also change.
+- API tokens have the same permissions as the user who creates them, and if the permissions of a user change, so do the permissions of the API token.
-For more information, see the '[Create an API token
-](https://developer.okta.com/docs/guides/create-an-api-token/main/)' official documentation article.
+For more information, see the '[Create an API token](https://developer.okta.com/docs/guides/create-an-api-token/main/)' official documentation article.
## Authentication using OAuth 2.0 Authentication
As an alternative to Okta API tokens, you can interact with Okta APIs using scoped OAuth 2.0 access tokens for a number of Okta endpoints.
@@ -33,16 +32,22 @@ The following scopes are required for the Okta v2 integration to work properly:
### Prerequisites
-1. Generate an API token as described previously. This is required for some backend API calls that are needed to set up OAuth authentication.
-2. Sign in to your Okta organization as a user with administrative privileges.
-3. In the Admin Console, go to **Applications** > **Applications**.
-4. Click **Create App Integration**.
-5. Select **API Services** as the sign-in method, and click **Next**.
-6. Enter a name for your app integration.
-7. On the app configuration page, under the **General** tab and the **Client Credentials** section, select **Public key / Private key** for the **Client authentication** option.
-8. Under the newly added **PUBLIC KEYS** section, click the **Add Key** button.
-9. In the **Add Public Key** dialog box, click **Generate new key**, and make sure to keep the private key (in PEM format) in somewhere safe.
-10. On the app configuration page, under the **Okta API Scopes** tab, make sure that the required scopes mentioned above are granted.
-
-For more information, see the '[Implement OAuth for Okta
-](https://developer.okta.com/docs/guides/implement-oauth-for-okta/main/)' official documentation article.
+1. Sign in to Okta Admin Console.
+2. In the Admin Console, go to **Applications** > **Applications**.
+3. Click **Create App Integration**.
+4. Select **API Services** as the sign-in method, and click **Next**.
+5. Enter the desired name for the created app (e.g., "Cortex XSOAR"), and click **Save**.
+6. In the app configuration page, under the **General** tab and the **Client Credentials** section, select **Public key / Private key** for the **Client authentication** option.
+7. Under the newly added **PUBLIC KEYS** section, click **Add Key**.
+8. In the **Add Public Key** dialog box, click **Generate new key**. Make sure to copy the generated private key (in PEM format) to somewhere safe, and click **Save**.
+9. Under the **General Settings** section:
+ 1. Next to the **Proof of possession** label, uncheck the **Require Demonstrating Proof of Possession (DPoP) header in token requests** option if it's selected.
+ 2. Next to the **Grant type** label, make sure the **Client Credentials** option is selected, and that the **Token Exchange** option is not selected.
+ 3. Click **Save**.
+10. Under the **Okta API Scopes** tab, grant the required scopes mentioned above for the app.
+11. Under the **Admin roles** tab:
+ 1. Click **Edit assignments**.
+ 2. In the dropdown list under "Role", select **Super Administrator**.
+ 3. Click **Save changes** at the top.
+
+For more information, see the '[Implement OAuth for Okta](https://developer.okta.com/docs/guides/implement-oauth-for-okta/main/)' official documentation article.
diff --git a/Packs/Okta/Integrations/Okta_v2/README.md b/Packs/Okta/Integrations/Okta_v2/README.md
index 5f7c4fae6b77..697f528a2893 100644
--- a/Packs/Okta/Integrations/Okta_v2/README.md
+++ b/Packs/Okta/Integrations/Okta_v2/README.md
@@ -1,23 +1,18 @@
-## Configure Okta v2 on Cortex XSOAR
-
-### Authentication using API Token
-Okta API tokens are used to authenticate requests to Okta APIs.
+Integration with Okta's cloud-based identity management service.
-#### Prerequisites
+## Configure Okta v2 on Cortex XSOAR
+### API Token Authentication Prerequisites
1. Sign in to your Okta organization as a user with administrator privileges.
-2. In the Admin Console, select **Security > API** from the menu and then select the **Tokens** tab.
+2. On the **Admin Console**, select **Security** > **API** from the menu, and then select the **Tokens** tab.
3. Click **Create Token**.
4. Name your token and click **Create Token**.
-##### Notes
-- API tokens have the same permissions as the user who creates them, and if the user permissions change, the API token permissions also change.
+#### Notes
+- API tokens have the same permissions as the user who creates them, and if the permissions of a user change, so do the permissions of the API token.
For more information, see the '[Create an API token](https://developer.okta.com/docs/guides/create-an-api-token/main/)' official documentation article.
-### Authentication using OAuth 2.0 Authentication
-As an alternative to Okta API tokens, you can interact with Okta APIs using scoped OAuth 2.0 access tokens for a number of Okta endpoints.
-Each access token enables the bearer to perform specific actions on specific Okta endpoints, with that ability controlled by which scopes the access token contains.
-
+### OAuth 2.0 Authentication Prerequisites
#### Required Scopes
The following scopes are required for the Okta v2 integration to work properly:
- okta.apps.manage
@@ -32,21 +27,27 @@ The following scopes are required for the Okta v2 integration to work properly:
- okta.users.manage
- okta.users.read
-
-##### Prerequisites
-1. Generate an API token as described previously. This is required for some backend API calls that are needed to setup OAuth authentication.
-2. Sign in to your Okta organization as a user with administrative privileges.
-3. In the Admin Console, go to **Applications** > **Applications**.
-4. Click **Create App Integration**.
-5. Select **API Services** as the sign-in method, and click **Next**.
-6. Enter a name for your app integration.
-7. On the app configuration page, under the **General** tab and the **Client Credentials** section, select **Public key / Private key** for the **Client authentication** option.
-8. Under the newly added **PUBLIC KEYS** section, click the **Add Key** button.
-9. In the **Add Public Key** dialog box, click **Generate new key**, and make sure to keep the private key (in PEM format) in somewhere safe.
-10. On the app configuration page, under the **Okta API Scopes** tab, make sure that the required scopes mentioned above are granted.
+1. Sign in to Okta Admin Console.
+2. In the Admin Console, go to **Applications** > **Applications**.
+3. Click **Create App Integration**.
+4. Select **API Services** as the sign-in method, and click **Next**.
+5. Enter the desired name for the created app (e.g., "Cortex XSOAR"), and click **Save**.
+6. In the app configuration page, under the **General** tab and the **Client Credentials** section, select **Public key / Private key** for the **Client authentication** option.
+7. Under the newly added **PUBLIC KEYS** section, click **Add Key**.
+8. In the **Add Public Key** dialog box, click **Generate new key**. Make sure to copy the generated private key (in PEM format) to somewhere safe, and click **Save**.
+9. Under the **General Settings** section:
+ 1. Next to the **Proof of possession** label, uncheck the **Require Demonstrating Proof of Possession (DPoP) header in token requests** option if it's selected.
+ 2. Next to the **Grant type** label, make sure the **Client Credentials** option is selected, and that the **Token Exchange** option is not selected.
+ 3. Click **Save**.
+10. Under the **Okta API Scopes** tab, grant the required scopes mentioned above for the app.
+11. Under the **Admin roles** tab:
+ 1. Click **Edit assignments**.
+ 2. In the dropdown list under "Role", select **Super Administrator**.
+ 3. Click **Save changes** at the top.
For more information, see the '[Implement OAuth for Okta](https://developer.okta.com/docs/guides/implement-oauth-for-okta/main/)' official documentation article.
+
### Instance Configuration
1. Navigate to **Settings** > **Integrations** > **Servers & Services**.
2. Search for Okta v2.
@@ -58,8 +59,8 @@ For more information, see the '[Implement OAuth for Okta](https://developer.okta
| API Token | | False |
| Use OAuth 2.0 Authentication | See detailed instructions on the 'Help' tab. | False |
| Client ID | Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab. | False |
- | Private Key | Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab. | False |
- | JWT Encoding Algorithm | Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab. | False |
+ | Private Key | In PEM format. Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab. | False |
+ | JWT Signing Algorithm | Algorithm to sign generated JWT tokens with. Doesn't affect integration's functionality. Required and used if OAuth 2.0 is used for authentication. See detailed instructions on the 'Help' tab. | False |
| Trust any certificate (not secure) | | False |
| Use system proxy settings | | False |
@@ -749,7 +750,6 @@ Lists users in your organization.
| Account.PasswordChanged | Date | Timestamp for when the user's password was last changed. |
| Okta.User.tag | String | The location of the next item, used with after param. |
-
### okta-create-user
***
diff --git a/Packs/Okta/ReleaseNotes/3_2_11.md b/Packs/Okta/ReleaseNotes/3_2_11.md
new file mode 100644
index 000000000000..4aace813ebbf
--- /dev/null
+++ b/Packs/Okta/ReleaseNotes/3_2_11.md
@@ -0,0 +1,8 @@
+
+#### Integrations
+
+##### Okta v2
+
+- *API Token* field is no longer required when configuring an instance using OAuth authentication.
+ Since the API token was previously used to set the app with a "Super Administrator" role, this role will be needed to be set manually for newly created apps (see [the documentation](https://xsoar.pan.dev/docs/reference/integrations/okta-v2#oauth-20-authentication-prerequisites) for more information).
+- Updated the Docker image to: *demisto/crypto:1.0.0.87358*.
diff --git a/Packs/Okta/pack_metadata.json b/Packs/Okta/pack_metadata.json
index 41436e4430cd..74bd96b59ff7 100644
--- a/Packs/Okta/pack_metadata.json
+++ b/Packs/Okta/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Okta",
"description": "Integration with Okta's cloud-based identity management service.",
"support": "xsoar",
- "currentVersion": "3.2.10",
+ "currentVersion": "3.2.11",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 9c886082d4ce7c05a0bdc2715cc381bee696f9ae Mon Sep 17 00:00:00 2001
From: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
Date: Sun, 18 Feb 2024 17:25:05 +0200
Subject: [PATCH 007/272] [Xsup 33523] fix for
microsoft-365-defender-advanced-hunting (#32976)
* reproduce the error
* replace split by "|" with regex
* update rn
* pre commit
* update docker
---
.../Microsoft365Defender/Microsoft365Defender.py | 2 +-
.../Microsoft365Defender/Microsoft365Defender.yml | 8 ++++----
.../Microsoft365Defender/Microsoft365Defender_test.py | 5 +++--
Packs/Microsoft365Defender/ReleaseNotes/4_5_18.md | 6 ++++++
Packs/Microsoft365Defender/pack_metadata.json | 2 +-
5 files changed, 15 insertions(+), 8 deletions(-)
create mode 100644 Packs/Microsoft365Defender/ReleaseNotes/4_5_18.md
diff --git a/Packs/Microsoft365Defender/Integrations/Microsoft365Defender/Microsoft365Defender.py b/Packs/Microsoft365Defender/Integrations/Microsoft365Defender/Microsoft365Defender.py
index 656ddb4b08e1..b52f24a7b7a7 100644
--- a/Packs/Microsoft365Defender/Integrations/Microsoft365Defender/Microsoft365Defender.py
+++ b/Packs/Microsoft365Defender/Integrations/Microsoft365Defender/Microsoft365Defender.py
@@ -532,7 +532,7 @@ def _query_set_limit(query: str, limit: int) -> str:
return query
# the query has the structure of "section | section | section ..."
- query_list = query.split('|')
+ query_list = re.split(r'(?
Date: Sun, 18 Feb 2024 17:53:10 +0200
Subject: [PATCH 008/272] [AlienVault] Add error handling for
convert_timestamp_to_iso86 (#32958)
---
.../AlienVault_USM_Anywhere.py | 27 ++++++++++---------
.../AlienVault_USM_Anywhere.yml | 2 +-
.../AlienVault_USM_Anywhere_test.py | 16 ++++++-----
.../ReleaseNotes/1_0_22.md | 6 +++++
.../pack_metadata.json | 2 +-
5 files changed, 32 insertions(+), 21 deletions(-)
create mode 100644 Packs/AlienVault_USM_Anywhere/ReleaseNotes/1_0_22.md
diff --git a/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere.py b/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere.py
index 0e810e939d44..38ac3d9a549a 100644
--- a/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere.py
+++ b/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere.py
@@ -8,7 +8,6 @@
import dateparser
import urllib3
from datetime import datetime
-from typing import Dict
# Disable insecure warnings
urllib3.disable_warnings()
@@ -77,7 +76,7 @@ def http_request(method, url_suffix, params=None, headers=None, data=None, **kwa
if res.status_code == 401:
raise Exception('UnauthorizedError: please validate your credentials.')
if res.status_code not in {200}:
- raise Exception('Error in API call to Example Integration [{}] - {}'.format(res.status_code, res.reason))
+ raise Exception(f'Error in API call to Example Integration [{res.status_code}] - {res.reason}')
return res.json()
@@ -133,7 +132,7 @@ def get_time_range(time_frame=None, start_time=None, end_time=None):
elif time_frame == 'Last 30 Days':
start_time = end_time - timedelta(days=30)
else:
- raise ValueError('Could not parse time frame: {}'.format(time_frame))
+ raise ValueError(f'Could not parse time frame: {time_frame}')
return date_to_timestamp(start_time), date_to_timestamp(end_time)
@@ -150,8 +149,12 @@ def convert_timestamp_to_iso86(timestamp: str, timezone_letter: str = 'Z') -> st
"""
if not timestamp:
return ''
- datetime_from_timestamp = dateparser.parse(timestamp, settings={"TO_TIMEZONE": timezone_letter,
- "RETURN_AS_TIMEZONE_AWARE": True})
+ try:
+ datetime_from_timestamp = dateparser.parse(str(timestamp), settings={"TO_TIMEZONE": timezone_letter,
+ "RETURN_AS_TIMEZONE_AWARE": True})
+ except Exception as e:
+ demisto.error(f"Encountered issue parsing {timestamp}. err: {str(e)}")
+ return ''
assert datetime_from_timestamp is not None, f'{timestamp} could not be parsed'
time_in_iso86 = datetime_from_timestamp.strftime("%Y-%m-%dT%H:%M:%S.%f")
return time_in_iso86[:-3] + timezone_letter
@@ -261,7 +264,7 @@ def parse_events(events_data):
return events
-def dict_value_to_int(target_dict: Dict, key: str):
+def dict_value_to_int(target_dict: dict, key: str):
"""
:param target_dict: A dictionary which has the key param
:param key: The key that we need to convert it's value to integer
@@ -321,7 +324,7 @@ def get_alarm_command():
# Parse response into context & content entries
alarm_details = parse_alarms(response)
- return_outputs(tableToMarkdown('Alarm {}'.format(alarm_id), alarm_details),
+ return_outputs(tableToMarkdown(f'Alarm {alarm_id}', alarm_details),
{'AlienVault.Alarm(val.ID && val.ID == obj.ID)': alarm_details},
response)
@@ -363,7 +366,7 @@ def search_alarms(start_time=None, end_time=None, status=None, priority=None, sh
params = {
'page': 0,
'size': limit,
- 'sort': 'timestamp_occured,{}'.format(direction),
+ 'sort': f'timestamp_occured,{direction}',
'suppressed': show_suppressed
}
@@ -417,7 +420,7 @@ def search_events(start_time=None, end_time=None, account_name=None, event_name=
params = {
'page': 1,
'size': limit,
- 'sort': 'timestamp_occured,{}'.format(direction),
+ 'sort': f'timestamp_occured,{direction}',
}
if account_name:
@@ -447,7 +450,7 @@ def get_events_by_alarm_command():
events = parse_events(alarm['events'])
- return_outputs(tableToMarkdown('Events of Alarm {}:'.format(alarm_id), events),
+ return_outputs(tableToMarkdown(f'Events of Alarm {alarm_id}:', events),
{'AlienVault.Event(val.ID && val.ID == obj.ID)': events},
alarm)
@@ -503,7 +506,7 @@ def fetch_incidents():
def main():
global AUTH_TOKEN
cmd = demisto.command()
- LOG('Command being called is {}'.format(cmd))
+ LOG(f'Command being called is {cmd}')
try:
handle_proxy()
@@ -522,7 +525,7 @@ def main():
LOG.print_log()
raise
else:
- return_error('An error occurred: {}'.format(str(e)))
+ return_error(f'An error occurred: {str(e)}')
# python2 uses __builtin__ python3 uses builtins
diff --git a/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere.yml b/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere.yml
index e1a0c913b37b..03e75e57ead5 100644
--- a/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere.yml
+++ b/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere.yml
@@ -340,7 +340,7 @@ script:
- contextPath: AlienVault.Event.Subcategory
description: The event subcategory.
type: String
- dockerimage: demisto/python3:3.10.13.72123
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere_test.py b/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere_test.py
index 1d995e66df72..b7db2dd511de 100644
--- a/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere_test.py
+++ b/Packs/AlienVault_USM_Anywhere/Integrations/AlienVault_USM_Anywhere/AlienVault_USM_Anywhere_test.py
@@ -1,4 +1,3 @@
-import io
import json
import pytest
import demistomock as demisto
@@ -10,7 +9,7 @@
def util_load_json(path):
- with io.open(path, mode='r', encoding='utf-8') as f:
+ with open(path, encoding='utf-8') as f:
return json.loads(f.read())
@@ -93,24 +92,27 @@ def test_get_time_range():
dt = datetime.now()
start, end = get_time_range('Today', None, None)
- assert datetime.fromtimestamp(start / 1000).date() == dt.date() and approximate_compare(dt, end)
+ assert datetime.fromtimestamp(start / 1000).date() == dt.date()
+ assert approximate_compare(dt, end)
dt = datetime.now()
# should ignore the start/end time values
start, end = get_time_range('Today', 'asfd', 'asdf')
- assert datetime.fromtimestamp(start / 1000).date() == dt.date() and approximate_compare(dt, end)
+ assert datetime.fromtimestamp(start / 1000).date() == dt.date()
+ assert approximate_compare(dt, end)
dt = datetime.now()
start, end = get_time_range('Yesterday', None, None)
- assert datetime.fromtimestamp(start / 1000).date() == (dt.date() - timedelta(days=1)) and approximate_compare(dt, end)
+ assert datetime.fromtimestamp(start / 1000).date() == (dt.date() - timedelta(days=1))
+ assert approximate_compare(dt, end)
start, end = get_time_range('Custom', '2019-12-30T01:02:03Z', '2019-12-30T04:05:06Z')
assert ((start, end) == (date_to_timestamp(dateparser.parse('2019-12-30T01:02:03Z')),
date_to_timestamp(dateparser.parse('2019-12-30T04:05:06Z'))))
start, end = get_time_range('Custom', '2019-12-30T01:02:03Z', None)
- assert (start == date_to_timestamp(dateparser.parse('2019-12-30T01:02:03Z'))
- and approximate_compare(end, datetime.now()))
+ assert start == date_to_timestamp(dateparser.parse('2019-12-30T01:02:03Z'))
+ assert approximate_compare(end, datetime.now())
parsed_regular_alarm = {'ID': 'some_uuid',
diff --git a/Packs/AlienVault_USM_Anywhere/ReleaseNotes/1_0_22.md b/Packs/AlienVault_USM_Anywhere/ReleaseNotes/1_0_22.md
new file mode 100644
index 000000000000..3a48ebd82fc0
--- /dev/null
+++ b/Packs/AlienVault_USM_Anywhere/ReleaseNotes/1_0_22.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### AlienVault USM Anywhere
+- Fixed an issue where *alienvault-get-alarm* command failed to convert timestamps to iso86 format.
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/AlienVault_USM_Anywhere/pack_metadata.json b/Packs/AlienVault_USM_Anywhere/pack_metadata.json
index 84414f7fa0ad..ea1f86012048 100644
--- a/Packs/AlienVault_USM_Anywhere/pack_metadata.json
+++ b/Packs/AlienVault_USM_Anywhere/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "AlienVault USM Anywhere",
"description": "Searches for and monitors alarms and events from AlienVault USM Anywhere.",
"support": "xsoar",
- "currentVersion": "1.0.21",
+ "currentVersion": "1.0.22",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 2a982b9cc77d858946e67dbff9d38809bb71c9a5 Mon Sep 17 00:00:00 2001
From: Anar Azadaliyev
Date: Sun, 18 Feb 2024 17:55:24 +0200
Subject: [PATCH 009/272] fix IdentifyAttachedEmail handle None (#32966)
* fix IdentifyAttachedEmail handle None
* fix docker
* add coverage
* Bump pack from version CommonScripts to 1.14.0.
---------
Co-authored-by: Content Bot
---
Packs/CommonScripts/ReleaseNotes/1_14_0.md | 7 ++
.../IdentifyAttachedEmail.py | 3 +
.../IdentifyAttachedEmail.yml | 2 +-
.../IdentifyAttachedEmail_test.py | 82 +++++++++++++++++++
Packs/CommonScripts/pack_metadata.json | 2 +-
5 files changed, 94 insertions(+), 2 deletions(-)
create mode 100644 Packs/CommonScripts/ReleaseNotes/1_14_0.md
diff --git a/Packs/CommonScripts/ReleaseNotes/1_14_0.md b/Packs/CommonScripts/ReleaseNotes/1_14_0.md
new file mode 100644
index 000000000000..ccc3ebcf8813
--- /dev/null
+++ b/Packs/CommonScripts/ReleaseNotes/1_14_0.md
@@ -0,0 +1,7 @@
+
+#### Scripts
+
+##### IdentifyAttachedEmail
+
+- Fixed an issue where the script was erroring when there were no File entries in the warroom.
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail.py b/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail.py
index a47585fae16e..307c6de93ab0 100644
--- a/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail.py
+++ b/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail.py
@@ -66,6 +66,9 @@ def identify_attached_mail(args):
else:
entries = demisto.executeCommand('getEntries', {"filter": {"categories": ["attachments"]}})
+ if not entries:
+ return 'no', None
+
for e in entries:
id = is_entry_email(e)
if id:
diff --git a/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail.yml b/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail.yml
index dbb7afd937ce..8f1db8a80336 100644
--- a/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail.yml
+++ b/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail.yml
@@ -28,4 +28,4 @@ tests:
- Process Email - Generic - Test - Incident Starter
- Phishing v2 - Test - Incident Starter
fromversion: 5.0.0
-dockerimage: demisto/python3:3.10.13.86272
+dockerimage: demisto/python3:3.10.13.87159
diff --git a/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail_test.py b/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail_test.py
index df84b466f8db..ece17fa892c4 100644
--- a/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail_test.py
+++ b/Packs/CommonScripts/Scripts/IdentifyAttachedEmail/IdentifyAttachedEmail_test.py
@@ -166,3 +166,85 @@ def execute_command(command, args):
results = identify_attached_mail({})
assert results == ('yes', {'reportedemailentryid': '23@2'})
+
+
+def test_identify_attached_mail_no_email_found(mocker):
+ """
+ Given
+ - no email entries in the warroom
+ - the platform is xsoar saas
+
+ When
+ - running the script to get the entries
+
+ Then
+ - no entries to be found
+
+ """
+ import CommonServerPython
+ mocker.patch.object(CommonServerPython, 'get_demisto_version', return_value={
+ 'version': '8.2.0',
+ 'buildNumber': '12345'
+ })
+
+ def execute_command(command, args):
+ if command == 'getEntries' and args == {"filter": {"categories": ["attachments"]}}:
+ return
+ else:
+ pytest.fail()
+
+ mocker.patch.object(demisto, 'executeCommand', side_effect=execute_command)
+
+ results = identify_attached_mail({})
+ assert results == ('no', None)
+
+
+def test_list_of_entries_passed_in_xsoar_saas_but_no_file_entries(mocker):
+ """
+ Given
+ - two entries with ids 23@2 24@2 which are not file entries
+ - the platform is xsoar saas
+
+ When
+ - running the script to get the entries
+
+ Then
+ - expect the getEntriesByIDs to be called
+ - expect no email entries to be found
+
+ """
+ entry_ids = """[\"23@2\",\"24@2\"]"""
+ import CommonServerPython
+ mocker.patch.object(CommonServerPython, 'get_demisto_version', return_value={
+ 'version': '8.2.0',
+ 'buildNumber': '12345'
+ })
+
+ def execute_command(command, args):
+ if command == 'getEntriesByIDs' and args.get('entryIDs') == '23@2,24@2':
+ return [
+ {
+ 'File': 'msg.txt',
+ 'FileMetadata': {
+ 'info': 'ASCII text, with CRLF line terminators'
+ },
+ 'ID': '23@2'
+ },
+ {
+ 'File': 'foo.txt',
+ 'FileMetadata': {
+ 'info': 'ASCII text, with CRLF line terminators'
+ },
+ 'ID': '24@2'
+ }
+ ]
+ else:
+ pytest.fail()
+
+ mocker.patch.object(demisto, 'executeCommand', side_effect=execute_command)
+
+ args = {
+ 'entryid': entry_ids
+ }
+ results = identify_attached_mail(args)
+ assert results == ('no', None)
diff --git a/Packs/CommonScripts/pack_metadata.json b/Packs/CommonScripts/pack_metadata.json
index ef668157d2b1..293d37cc7cee 100644
--- a/Packs/CommonScripts/pack_metadata.json
+++ b/Packs/CommonScripts/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Common Scripts",
"description": "Frequently used scripts pack.",
"support": "xsoar",
- "currentVersion": "1.13.40",
+ "currentVersion": "1.14.0",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From e14e854e6a53eeb88a19d7ead3a053f84a4cdc37 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:22:57 +0200
Subject: [PATCH 010/272] Update `demisto/dxl` 25-40 coverage rate (#32648)
* upgrade images
* update RN
---
Packs/McAfee-MAR/Integrations/McAfee-MAR/McAfee-MAR.yml | 2 +-
Packs/McAfee-MAR/ReleaseNotes/1_0_8.md | 6 ++++++
Packs/McAfee-MAR/pack_metadata.json | 2 +-
Packs/McAfee_DXL/Integrations/McAfee_DXL/McAfee_DXL.yml | 2 +-
Packs/McAfee_DXL/ReleaseNotes/1_0_5.md | 6 ++++++
Packs/McAfee_DXL/pack_metadata.json | 2 +-
6 files changed, 16 insertions(+), 4 deletions(-)
create mode 100644 Packs/McAfee-MAR/ReleaseNotes/1_0_8.md
create mode 100644 Packs/McAfee_DXL/ReleaseNotes/1_0_5.md
diff --git a/Packs/McAfee-MAR/Integrations/McAfee-MAR/McAfee-MAR.yml b/Packs/McAfee-MAR/Integrations/McAfee-MAR/McAfee-MAR.yml
index aec95a02a0db..0a3cc52b00a6 100644
--- a/Packs/McAfee-MAR/Integrations/McAfee-MAR/McAfee-MAR.yml
+++ b/Packs/McAfee-MAR/Integrations/McAfee-MAR/McAfee-MAR.yml
@@ -496,7 +496,7 @@ script:
- contextPath: MAR.HostInfo.Os
description: Host operation system
description: Gets host information from McAfee Active Response
- dockerimage: demisto/dxl:1.0.0.63890
+ dockerimage: demisto/dxl:1.0.0.86273
fromversion: 5.0.0
tests:
- No tests (auto formatted)
diff --git a/Packs/McAfee-MAR/ReleaseNotes/1_0_8.md b/Packs/McAfee-MAR/ReleaseNotes/1_0_8.md
new file mode 100644
index 000000000000..2d076089a968
--- /dev/null
+++ b/Packs/McAfee-MAR/ReleaseNotes/1_0_8.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### McAfee Active Response
+
+- Updated the Docker image to: *demisto/dxl:1.0.0.86273*.
diff --git a/Packs/McAfee-MAR/pack_metadata.json b/Packs/McAfee-MAR/pack_metadata.json
index ff17f7b5b06a..f4de82ba9cc9 100644
--- a/Packs/McAfee-MAR/pack_metadata.json
+++ b/Packs/McAfee-MAR/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "McAfee Active Response",
"description": "Connect to MAR using its DXL client",
"support": "xsoar",
- "currentVersion": "1.0.7",
+ "currentVersion": "1.0.8",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/McAfee_DXL/Integrations/McAfee_DXL/McAfee_DXL.yml b/Packs/McAfee_DXL/Integrations/McAfee_DXL/McAfee_DXL.yml
index e5825f01def4..6634e8b75ae1 100644
--- a/Packs/McAfee_DXL/Integrations/McAfee_DXL/McAfee_DXL.yml
+++ b/Packs/McAfee_DXL/Integrations/McAfee_DXL/McAfee_DXL.yml
@@ -141,7 +141,7 @@ script:
name: topic
description: The push hash to the DXL fabric.
name: dxl-push-hash
- dockerimage: demisto/dxl:1.0.0.35274
+ dockerimage: demisto/dxl:1.0.0.86273
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/McAfee_DXL/ReleaseNotes/1_0_5.md b/Packs/McAfee_DXL/ReleaseNotes/1_0_5.md
new file mode 100644
index 000000000000..7932a80fb22a
--- /dev/null
+++ b/Packs/McAfee_DXL/ReleaseNotes/1_0_5.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### McAfee DXL
+
+- Updated the Docker image to: *demisto/dxl:1.0.0.86273*.
diff --git a/Packs/McAfee_DXL/pack_metadata.json b/Packs/McAfee_DXL/pack_metadata.json
index 96608cc156ff..9b111b8faa31 100644
--- a/Packs/McAfee_DXL/pack_metadata.json
+++ b/Packs/McAfee_DXL/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "McAfee DXL",
"description": "McAfee DXL client",
"support": "xsoar",
- "currentVersion": "1.0.4",
+ "currentVersion": "1.0.5",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From d40f35cc5f9215c26ae647e2b871f6f9c0cfe299 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:23:11 +0200
Subject: [PATCH 011/272] Update `demisto/googleapi-python3` 0-10 coverage rate
(#32646)
* upgrade images
* update RN
---
.../Integrations/GoogleCloudCompute/GoogleCloudCompute.yml | 2 +-
Packs/GoogleCloudCompute/ReleaseNotes/1_1_8.md | 6 ++++++
Packs/GoogleCloudCompute/pack_metadata.json | 2 +-
.../GoogleResourceManager/GoogleResourceManager.yml | 2 +-
Packs/GoogleResourceManager/ReleaseNotes/1_0_5.md | 6 ++++++
Packs/GoogleResourceManager/pack_metadata.json | 2 +-
Packs/GoogleVault/Integrations/GoogleVault/GoogleVault.yml | 2 +-
Packs/GoogleVault/ReleaseNotes/1_0_12.md | 6 ++++++
Packs/GoogleVault/pack_metadata.json | 2 +-
9 files changed, 24 insertions(+), 6 deletions(-)
create mode 100644 Packs/GoogleCloudCompute/ReleaseNotes/1_1_8.md
create mode 100644 Packs/GoogleResourceManager/ReleaseNotes/1_0_5.md
create mode 100644 Packs/GoogleVault/ReleaseNotes/1_0_12.md
diff --git a/Packs/GoogleCloudCompute/Integrations/GoogleCloudCompute/GoogleCloudCompute.yml b/Packs/GoogleCloudCompute/Integrations/GoogleCloudCompute/GoogleCloudCompute.yml
index 788b82f6b864..242bfe9f2c9b 100644
--- a/Packs/GoogleCloudCompute/Integrations/GoogleCloudCompute/GoogleCloudCompute.yml
+++ b/Packs/GoogleCloudCompute/Integrations/GoogleCloudCompute/GoogleCloudCompute.yml
@@ -8418,7 +8418,7 @@ script:
- contextPath: GoogleCloudCompute.Instances.kind
description: '] Type of the resource. Always compute#instance for instances.'
type: string
- dockerimage: demisto/googleapi-python3:1.0.0.65068
+ dockerimage: demisto/googleapi-python3:1.0.0.86653
script: ''
subtype: python3
type: python
diff --git a/Packs/GoogleCloudCompute/ReleaseNotes/1_1_8.md b/Packs/GoogleCloudCompute/ReleaseNotes/1_1_8.md
new file mode 100644
index 000000000000..032ca560c148
--- /dev/null
+++ b/Packs/GoogleCloudCompute/ReleaseNotes/1_1_8.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Google Cloud Compute
+
+- Updated the Docker image to: *demisto/googleapi-python3:1.0.0.86653*.
diff --git a/Packs/GoogleCloudCompute/pack_metadata.json b/Packs/GoogleCloudCompute/pack_metadata.json
index c04c4a974d4f..e3b440eb9a2b 100644
--- a/Packs/GoogleCloudCompute/pack_metadata.json
+++ b/Packs/GoogleCloudCompute/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Cloud Compute",
"description": "Google Compute Engine delivers virtual machines running in Google's innovative data centers and worldwide fiber network. Compute Engine's tooling and workflow support enable scaling from single instances to global, load-balanced cloud computing.",
"support": "xsoar",
- "currentVersion": "1.1.7",
+ "currentVersion": "1.1.8",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/GoogleResourceManager/Integrations/GoogleResourceManager/GoogleResourceManager.yml b/Packs/GoogleResourceManager/Integrations/GoogleResourceManager/GoogleResourceManager.yml
index dbbe230b69d6..8c19462fa8d9 100644
--- a/Packs/GoogleResourceManager/Integrations/GoogleResourceManager/GoogleResourceManager.yml
+++ b/Packs/GoogleResourceManager/Integrations/GoogleResourceManager/GoogleResourceManager.yml
@@ -397,7 +397,7 @@ script:
- contextPath: GRM.Project.Parent.Type
description: Type of the parent resource.
type: String
- dockerimage: demisto/googleapi-python3:1.0.0.63869
+ dockerimage: demisto/googleapi-python3:1.0.0.86653
runonce: false
script: ''
type: python
diff --git a/Packs/GoogleResourceManager/ReleaseNotes/1_0_5.md b/Packs/GoogleResourceManager/ReleaseNotes/1_0_5.md
new file mode 100644
index 000000000000..2909de985d9f
--- /dev/null
+++ b/Packs/GoogleResourceManager/ReleaseNotes/1_0_5.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Google Resource Manager
+
+- Updated the Docker image to: *demisto/googleapi-python3:1.0.0.86653*.
diff --git a/Packs/GoogleResourceManager/pack_metadata.json b/Packs/GoogleResourceManager/pack_metadata.json
index bfd837000213..04c18d3cc213 100644
--- a/Packs/GoogleResourceManager/pack_metadata.json
+++ b/Packs/GoogleResourceManager/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Resource Manager",
"description": "Google Cloud Platform Resource Manager",
"support": "xsoar",
- "currentVersion": "1.0.4",
+ "currentVersion": "1.0.5",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/GoogleVault/Integrations/GoogleVault/GoogleVault.yml b/Packs/GoogleVault/Integrations/GoogleVault/GoogleVault.yml
index f845b7271fe6..e805adba7525 100644
--- a/Packs/GoogleVault/Integrations/GoogleVault/GoogleVault.yml
+++ b/Packs/GoogleVault/Integrations/GoogleVault/GoogleVault.yml
@@ -540,7 +540,7 @@ script:
- contextPath: GoogleVault.Matter.Export.Results.To
description: The address the message was sent to
type: string
- dockerimage: demisto/googleapi-python3:1.0.0.64742
+ dockerimage: demisto/googleapi-python3:1.0.0.86653
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/GoogleVault/ReleaseNotes/1_0_12.md b/Packs/GoogleVault/ReleaseNotes/1_0_12.md
new file mode 100644
index 000000000000..24cd57b50f74
--- /dev/null
+++ b/Packs/GoogleVault/ReleaseNotes/1_0_12.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Google Vault
+
+- Updated the Docker image to: *demisto/googleapi-python3:1.0.0.86653*.
diff --git a/Packs/GoogleVault/pack_metadata.json b/Packs/GoogleVault/pack_metadata.json
index d8817f94a023..3d12651f95fa 100644
--- a/Packs/GoogleVault/pack_metadata.json
+++ b/Packs/GoogleVault/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Vault",
"description": "Archiving and eDiscovery for G Suite.",
"support": "xsoar",
- "currentVersion": "1.0.11",
+ "currentVersion": "1.0.12",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 9be11ce0befff7868308a98e98e1b81e47682368 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:23:21 +0200
Subject: [PATCH 012/272] Update `demisto/google-api-py3` 25-40 coverage rate
(#32645)
* upgrade images
* update RN
---
.../GoogleCloudFunctions/GoogleCloudFunctions.yml | 2 +-
Packs/GoogleCloudFunctions/ReleaseNotes/1_0_27.md | 6 ++++++
Packs/GoogleCloudFunctions/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/GoogleCloudFunctions/ReleaseNotes/1_0_27.md
diff --git a/Packs/GoogleCloudFunctions/Integrations/GoogleCloudFunctions/GoogleCloudFunctions.yml b/Packs/GoogleCloudFunctions/Integrations/GoogleCloudFunctions/GoogleCloudFunctions.yml
index ece6b7d2d9a8..c9dbde8d83a0 100644
--- a/Packs/GoogleCloudFunctions/Integrations/GoogleCloudFunctions/GoogleCloudFunctions.yml
+++ b/Packs/GoogleCloudFunctions/Integrations/GoogleCloudFunctions/GoogleCloudFunctions.yml
@@ -114,7 +114,7 @@ script:
- contextPath: GoogleCloudFunctions.Execution.error
description: Either a system or user-function generated error. Set if the execution was not successful.
type: String
- dockerimage: demisto/google-api-py3:1.0.0.64100
+ dockerimage: demisto/google-api-py3:1.0.0.86674
runonce: false
script: '-'
type: python
diff --git a/Packs/GoogleCloudFunctions/ReleaseNotes/1_0_27.md b/Packs/GoogleCloudFunctions/ReleaseNotes/1_0_27.md
new file mode 100644
index 000000000000..75537ce70df0
--- /dev/null
+++ b/Packs/GoogleCloudFunctions/ReleaseNotes/1_0_27.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Google Cloud Functions
+
+- Updated the Docker image to: *demisto/google-api-py3:1.0.0.86674*.
diff --git a/Packs/GoogleCloudFunctions/pack_metadata.json b/Packs/GoogleCloudFunctions/pack_metadata.json
index 998007334dcc..8f9d5db56712 100644
--- a/Packs/GoogleCloudFunctions/pack_metadata.json
+++ b/Packs/GoogleCloudFunctions/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Cloud Functions",
"description": "Google Cloud Functions",
"support": "xsoar",
- "currentVersion": "1.0.26",
+ "currentVersion": "1.0.27",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 11da3140a014406486bce7fc64bfabb57ce35e94 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:23:40 +0200
Subject: [PATCH 013/272] Update `demisto/bs4-py3` 0-10 coverage rate (#32637)
* upgrade images
* update RN
---
.../SymantecMessagingGateway/SymantecMessagingGateway.yml | 2 +-
Packs/Symantec_Messaging_Gateway/ReleaseNotes/1_0_15.md | 6 ++++++
Packs/Symantec_Messaging_Gateway/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/Symantec_Messaging_Gateway/ReleaseNotes/1_0_15.md
diff --git a/Packs/Symantec_Messaging_Gateway/Integrations/SymantecMessagingGateway/SymantecMessagingGateway.yml b/Packs/Symantec_Messaging_Gateway/Integrations/SymantecMessagingGateway/SymantecMessagingGateway.yml
index ece80fd84de9..eef326247945 100644
--- a/Packs/Symantec_Messaging_Gateway/Integrations/SymantecMessagingGateway/SymantecMessagingGateway.yml
+++ b/Packs/Symantec_Messaging_Gateway/Integrations/SymantecMessagingGateway/SymantecMessagingGateway.yml
@@ -118,7 +118,7 @@ script:
- name: smg-get-blocked-ips
arguments: []
description: Returns a list of all blocked IP addresses.
- dockerimage: demisto/bs4-py3:1.0.0.48637
+ dockerimage: demisto/bs4-py3:1.0.0.86348
fromversion: 5.0.0
tests:
- No tests (auto formatted)
diff --git a/Packs/Symantec_Messaging_Gateway/ReleaseNotes/1_0_15.md b/Packs/Symantec_Messaging_Gateway/ReleaseNotes/1_0_15.md
new file mode 100644
index 000000000000..486607f6f508
--- /dev/null
+++ b/Packs/Symantec_Messaging_Gateway/ReleaseNotes/1_0_15.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Symantec Messaging Gateway
+
+- Updated the Docker image to: *demisto/bs4-py3:1.0.0.86348*.
diff --git a/Packs/Symantec_Messaging_Gateway/pack_metadata.json b/Packs/Symantec_Messaging_Gateway/pack_metadata.json
index 9b17e9ce741d..448c8a068c45 100644
--- a/Packs/Symantec_Messaging_Gateway/pack_metadata.json
+++ b/Packs/Symantec_Messaging_Gateway/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Symantec Messaging Gateway",
"description": "Symantec Messaging Gateway protects against spam, malware, and targeted attacks and provides advanced content filtering, data loss prevention, and email encryption.",
"support": "xsoar",
- "currentVersion": "1.0.14",
+ "currentVersion": "1.0.15",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 9eddbe465e99abd5e1394f45b34bb9d00e9eb4e4 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:24:00 +0200
Subject: [PATCH 014/272] Update `demisto/netutils` 0-10 coverage rate (#32631)
* upgrade images
* update RN
---
.../Integrations/FeedPublicDNS/FeedPublicDNS.yml | 2 +-
Packs/FeedPublicDNS/ReleaseNotes/1_0_15.md | 6 ++++++
Packs/FeedPublicDNS/pack_metadata.json | 2 +-
Packs/Nmap/Integrations/Nmap/Nmap.yml | 2 +-
Packs/Nmap/ReleaseNotes/1_2_3.md | 6 ++++++
Packs/Nmap/pack_metadata.json | 2 +-
6 files changed, 16 insertions(+), 4 deletions(-)
create mode 100644 Packs/FeedPublicDNS/ReleaseNotes/1_0_15.md
create mode 100644 Packs/Nmap/ReleaseNotes/1_2_3.md
diff --git a/Packs/FeedPublicDNS/Integrations/FeedPublicDNS/FeedPublicDNS.yml b/Packs/FeedPublicDNS/Integrations/FeedPublicDNS/FeedPublicDNS.yml
index f00e17e83d9a..5bc4ef84706f 100644
--- a/Packs/FeedPublicDNS/Integrations/FeedPublicDNS/FeedPublicDNS.yml
+++ b/Packs/FeedPublicDNS/Integrations/FeedPublicDNS/FeedPublicDNS.yml
@@ -96,7 +96,7 @@ script:
name: limit
description: Gets indicators from the feed.
name: public-dns-get-indicators
- dockerimage: demisto/netutils:1.0.0.74582
+ dockerimage: demisto/netutils:1.0.0.86390
feed: true
runonce: false
script: '-'
diff --git a/Packs/FeedPublicDNS/ReleaseNotes/1_0_15.md b/Packs/FeedPublicDNS/ReleaseNotes/1_0_15.md
new file mode 100644
index 000000000000..f825984a3803
--- /dev/null
+++ b/Packs/FeedPublicDNS/ReleaseNotes/1_0_15.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Public DNS Feed
+
+- Updated the Docker image to: *demisto/netutils:1.0.0.86390*.
diff --git a/Packs/FeedPublicDNS/pack_metadata.json b/Packs/FeedPublicDNS/pack_metadata.json
index 61ca4714b880..aedb00b8f166 100644
--- a/Packs/FeedPublicDNS/pack_metadata.json
+++ b/Packs/FeedPublicDNS/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Public DNS Feed",
"description": "The Public DNS Feed fetches known IPs associated with public DNS servers from https://public-dns.info/",
"support": "xsoar",
- "currentVersion": "1.0.14",
+ "currentVersion": "1.0.15",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Nmap/Integrations/Nmap/Nmap.yml b/Packs/Nmap/Integrations/Nmap/Nmap.yml
index bdefe233642a..eec937eda2df 100644
--- a/Packs/Nmap/Integrations/Nmap/Nmap.yml
+++ b/Packs/Nmap/Integrations/Nmap/Nmap.yml
@@ -57,4 +57,4 @@ script:
description: Additional parseable fields from the script output.
description: Scan targets with the given parameters
execution: true
- dockerimage: demisto/netutils:1.0.0.74582
+ dockerimage: demisto/netutils:1.0.0.86390
diff --git a/Packs/Nmap/ReleaseNotes/1_2_3.md b/Packs/Nmap/ReleaseNotes/1_2_3.md
new file mode 100644
index 000000000000..cc92e2c8685e
--- /dev/null
+++ b/Packs/Nmap/ReleaseNotes/1_2_3.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### nmap
+
+- Updated the Docker image to: *demisto/netutils:1.0.0.86390*.
diff --git a/Packs/Nmap/pack_metadata.json b/Packs/Nmap/pack_metadata.json
index 061fd90c75d8..bd662c815619 100644
--- a/Packs/Nmap/pack_metadata.json
+++ b/Packs/Nmap/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Nmap",
"description": "Run nmap scans with the given parameters",
"support": "xsoar",
- "currentVersion": "1.2.2",
+ "currentVersion": "1.2.3",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 99df807a363c8dc4c758a2a2444ce190e17374bc Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:24:26 +0200
Subject: [PATCH 015/272] Update `demisto/graphql` 0-10 coverage rate (#32625)
* upgrade images
* update RN
---
Packs/GraphQL/Integrations/GraphQL/GraphQL.yml | 2 +-
Packs/GraphQL/ReleaseNotes/1_0_18.md | 6 ++++++
Packs/GraphQL/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/GraphQL/ReleaseNotes/1_0_18.md
diff --git a/Packs/GraphQL/Integrations/GraphQL/GraphQL.yml b/Packs/GraphQL/Integrations/GraphQL/GraphQL.yml
index 498c65246423..4bb0ef70b218 100644
--- a/Packs/GraphQL/Integrations/GraphQL/GraphQL.yml
+++ b/Packs/GraphQL/Integrations/GraphQL/GraphQL.yml
@@ -84,7 +84,7 @@ script:
- 'false'
description: Executes a mutation request to the GraphQL server.
name: graphql-mutation
- dockerimage: demisto/graphql:1.0.0.45620
+ dockerimage: demisto/graphql:1.0.0.86378
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/GraphQL/ReleaseNotes/1_0_18.md b/Packs/GraphQL/ReleaseNotes/1_0_18.md
new file mode 100644
index 000000000000..aa5dfdf45449
--- /dev/null
+++ b/Packs/GraphQL/ReleaseNotes/1_0_18.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### GraphQL
+
+- Updated the Docker image to: *demisto/graphql:1.0.0.86378*.
diff --git a/Packs/GraphQL/pack_metadata.json b/Packs/GraphQL/pack_metadata.json
index 55572e6473ce..4170043f86a2 100644
--- a/Packs/GraphQL/pack_metadata.json
+++ b/Packs/GraphQL/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "GraphQL",
"description": "Generic GraphQL client to interact with any GraphQL server API.",
"support": "xsoar",
- "currentVersion": "1.0.17",
+ "currentVersion": "1.0.18",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 8953ba46ceebbad6e4e3c7a9bffc930598c8d8a7 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:24:51 +0200
Subject: [PATCH 016/272] Update `demisto/blueliv` 0-10 coverage rate (#32624)
* upgrade images
* update RN
---
Packs/Blueliv/Integrations/Blueliv/Blueliv.yml | 2 +-
Packs/Blueliv/ReleaseNotes/1_0_3.md | 6 ++++++
Packs/Blueliv/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/Blueliv/ReleaseNotes/1_0_3.md
diff --git a/Packs/Blueliv/Integrations/Blueliv/Blueliv.yml b/Packs/Blueliv/Integrations/Blueliv/Blueliv.yml
index b01d908285a7..c75086c7fd36 100644
--- a/Packs/Blueliv/Integrations/Blueliv/Blueliv.yml
+++ b/Packs/Blueliv/Integrations/Blueliv/Blueliv.yml
@@ -37,7 +37,7 @@ script:
name: blueliv-get-attackingips-feed
- description: 'Data related to the number of hacktivism tweets recently created. Blueliv provides two types of feeds: the first one contains the most popular hacktivism hashtags and the second one contains the countries where more number of hacktivism tweets are coming from.'
name: blueliv-get-hacktivism-feed
- dockerimage: demisto/blueliv:1.0.0.52588
+ dockerimage: demisto/blueliv:1.0.0.76921
runonce: false
script: ''
type: python
diff --git a/Packs/Blueliv/ReleaseNotes/1_0_3.md b/Packs/Blueliv/ReleaseNotes/1_0_3.md
new file mode 100644
index 000000000000..b79460975a3f
--- /dev/null
+++ b/Packs/Blueliv/ReleaseNotes/1_0_3.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Blueliv (Beta)
+
+- Updated the Docker image to: *demisto/blueliv:1.0.0.76921*.
diff --git a/Packs/Blueliv/pack_metadata.json b/Packs/Blueliv/pack_metadata.json
index eeda387fb835..69cf2e10ef17 100644
--- a/Packs/Blueliv/pack_metadata.json
+++ b/Packs/Blueliv/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Blueliv (Beta)",
"description": "Blueliv reduces risk through actionable, dynamic and targeted threat intelligence, trusted by your organization.",
"support": "xsoar",
- "currentVersion": "1.0.2",
+ "currentVersion": "1.0.3",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 7815b6f6a0678e590ea68fe01e1228bb1f4a6f86 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:27:37 +0200
Subject: [PATCH 017/272] Update `demisto/taxii` 10-25 coverage rate (#32604)
* upgrade images
* update RN
* Bump pack from version FeedAlienVault to 1.1.31.
---------
Co-authored-by: Content Bot
---
.../FeedAlienVaultOTXTaxii/FeedAlienVaultOTXTaxii.yml | 2 +-
Packs/FeedAlienVault/ReleaseNotes/1_1_31.md | 6 ++++++
Packs/FeedAlienVault/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/FeedAlienVault/ReleaseNotes/1_1_31.md
diff --git a/Packs/FeedAlienVault/Integrations/FeedAlienVaultOTXTaxii/FeedAlienVaultOTXTaxii.yml b/Packs/FeedAlienVault/Integrations/FeedAlienVaultOTXTaxii/FeedAlienVaultOTXTaxii.yml
index 6baeefd08e73..d9c3da1bb49d 100644
--- a/Packs/FeedAlienVault/Integrations/FeedAlienVaultOTXTaxii/FeedAlienVaultOTXTaxii.yml
+++ b/Packs/FeedAlienVault/Integrations/FeedAlienVaultOTXTaxii/FeedAlienVaultOTXTaxii.yml
@@ -120,7 +120,7 @@ script:
name: begin_date
description: Gets the indicators from AlienVault OTX.
name: alienvaultotx-get-indicators
- dockerimage: demisto/taxii:1.0.0.43208
+ dockerimage: demisto/taxii:1.0.0.86676
feed: true
runonce: false
script: '-'
diff --git a/Packs/FeedAlienVault/ReleaseNotes/1_1_31.md b/Packs/FeedAlienVault/ReleaseNotes/1_1_31.md
new file mode 100644
index 000000000000..9154e3946b6f
--- /dev/null
+++ b/Packs/FeedAlienVault/ReleaseNotes/1_1_31.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### AlienVault OTX TAXII Feed
+
+- Updated the Docker image to: *demisto/taxii:1.0.0.86676*.
diff --git a/Packs/FeedAlienVault/pack_metadata.json b/Packs/FeedAlienVault/pack_metadata.json
index ef1e1c59ed35..4ec738bc5864 100644
--- a/Packs/FeedAlienVault/pack_metadata.json
+++ b/Packs/FeedAlienVault/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "AlienVault Feed",
"description": "Indicators feed from AlienVault",
"support": "xsoar",
- "currentVersion": "1.1.30",
+ "currentVersion": "1.1.31",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 123f8db89c6e9b6b34361aafdf09748cd7df142c Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:28:04 +0200
Subject: [PATCH 018/272] Update `demisto/dnstwist` '0-10' coverage rate
(#32582)
* upgrade images
* updateRN
---
Packs/dnstwist/Integrations/dnstwist/dnstwist.yml | 2 +-
Packs/dnstwist/ReleaseNotes/1_1_13.md | 6 ++++++
Packs/dnstwist/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/dnstwist/ReleaseNotes/1_1_13.md
diff --git a/Packs/dnstwist/Integrations/dnstwist/dnstwist.yml b/Packs/dnstwist/Integrations/dnstwist/dnstwist.yml
index e966a3133124..aea1ed94185f 100644
--- a/Packs/dnstwist/Integrations/dnstwist/dnstwist.yml
+++ b/Packs/dnstwist/Integrations/dnstwist/dnstwist.yml
@@ -44,7 +44,7 @@ script:
- contextPath: dnstwist.Domain.Domains.WhoisCreated
description: Whois created for domain name variations.
type: string
- dockerimage: demisto/dnstwist:1.0.0.46433
+ dockerimage: demisto/dnstwist:1.0.0.86365
runonce: false
script: '-'
type: python
diff --git a/Packs/dnstwist/ReleaseNotes/1_1_13.md b/Packs/dnstwist/ReleaseNotes/1_1_13.md
new file mode 100644
index 000000000000..cdda90ae3f00
--- /dev/null
+++ b/Packs/dnstwist/ReleaseNotes/1_1_13.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### dnstwist
+
+- Updated the Docker image to: *demisto/dnstwist:1.0.0.86365*.
diff --git a/Packs/dnstwist/pack_metadata.json b/Packs/dnstwist/pack_metadata.json
index a12d4d24839d..86b159e85e62 100644
--- a/Packs/dnstwist/pack_metadata.json
+++ b/Packs/dnstwist/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Dnstwist",
"description": "Use the DNSTwist integration to detect typosquatting, phishing, and corporate espionage.",
"support": "xsoar",
- "currentVersion": "1.1.12",
+ "currentVersion": "1.1.13",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From f30ac1443a0269a50ff2eb69179694b067dede96 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:29:05 +0200
Subject: [PATCH 019/272] Update `demisto/fastapi` 0-10 coverage rate (#32571)
* upgrade images
* update RN
* Bump pack from version AlibabaActionTrail to 1.0.24.
---------
Co-authored-by: Content Bot
---
.../AlibabaActionTrailEventCollector.yml | 2 +-
Packs/AlibabaActionTrail/ReleaseNotes/1_0_24.md | 6 ++++++
Packs/AlibabaActionTrail/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/AlibabaActionTrail/ReleaseNotes/1_0_24.md
diff --git a/Packs/AlibabaActionTrail/Integrations/AlibabaActionTrailEventCollector/AlibabaActionTrailEventCollector.yml b/Packs/AlibabaActionTrail/Integrations/AlibabaActionTrailEventCollector/AlibabaActionTrailEventCollector.yml
index 913bce155274..f257ec20355c 100644
--- a/Packs/AlibabaActionTrail/Integrations/AlibabaActionTrailEventCollector/AlibabaActionTrailEventCollector.yml
+++ b/Packs/AlibabaActionTrail/Integrations/AlibabaActionTrailEventCollector/AlibabaActionTrailEventCollector.yml
@@ -81,7 +81,7 @@ script:
- "True"
- "False"
required: true
- dockerimage: demisto/fastapi:1.0.0.36992
+ dockerimage: demisto/fastapi:1.0.0.86524
isfetchevents: true
subtype: python3
marketplaces:
diff --git a/Packs/AlibabaActionTrail/ReleaseNotes/1_0_24.md b/Packs/AlibabaActionTrail/ReleaseNotes/1_0_24.md
new file mode 100644
index 000000000000..39a21e38487f
--- /dev/null
+++ b/Packs/AlibabaActionTrail/ReleaseNotes/1_0_24.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Alibaba Action Trail Event Collector
+
+- Updated the Docker image to: *demisto/fastapi:1.0.0.86524*.
diff --git a/Packs/AlibabaActionTrail/pack_metadata.json b/Packs/AlibabaActionTrail/pack_metadata.json
index 24f2b0f0e8c9..a2903ddc57b3 100644
--- a/Packs/AlibabaActionTrail/pack_metadata.json
+++ b/Packs/AlibabaActionTrail/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Alibaba Action Trail",
"description": "An Integration Pack to fetch Alibaba action trail events.",
"support": "xsoar",
- "currentVersion": "1.0.23",
+ "currentVersion": "1.0.24",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From a46e2317a90de3d194e3051619f830811d6462a2 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Sun, 18 Feb 2024 18:29:42 +0200
Subject: [PATCH 020/272] Upgrade `demisto/boto3py3` items 0-10 coverage rate
(#32565)
* upgrade images
* update RN
* update docker
* upgrade docker
* update AWSWAF
---
.../Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml | 2 +-
Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md | 6 ++++++
Packs/AWS-CloudWatchLogs/pack_metadata.json | 2 +-
.../AWS-NetworkFirewall/AWS-NetworkFirewall.yml | 2 +-
Packs/AWS-NetworkFirewall/ReleaseNotes/1_0_5.md | 6 ++++++
Packs/AWS-NetworkFirewall/pack_metadata.json | 2 +-
.../AWS_DynamoDB/Integrations/AWS_DynamoDB/AWS_DynamoDB.yml | 2 +-
Packs/AWS_DynamoDB/ReleaseNotes/1_0_32.md | 6 ++++++
Packs/AWS_DynamoDB/pack_metadata.json | 2 +-
Packs/AWS_WAF/Integrations/AWSWAF/AWSWAF.yml | 2 +-
Packs/AWS_WAF/ReleaseNotes/1_0_5.md | 6 ++++++
Packs/AWS_WAF/pack_metadata.json | 2 +-
12 files changed, 32 insertions(+), 8 deletions(-)
create mode 100644 Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md
create mode 100644 Packs/AWS-NetworkFirewall/ReleaseNotes/1_0_5.md
create mode 100644 Packs/AWS_DynamoDB/ReleaseNotes/1_0_32.md
create mode 100644 Packs/AWS_WAF/ReleaseNotes/1_0_5.md
diff --git a/Packs/AWS-CloudWatchLogs/Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml b/Packs/AWS-CloudWatchLogs/Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml
index ec96f2a7f08a..688073e08848 100644
--- a/Packs/AWS-CloudWatchLogs/Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml
+++ b/Packs/AWS-CloudWatchLogs/Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml
@@ -447,7 +447,7 @@ script:
description: The name of the log group.
type: string
description: Lists the specified metric filters. You can list all the metric filters or filter the results by log name, prefix, metric name, or metric namespace.
- dockerimage: demisto/boto3py3:1.0.0.52713
+ dockerimage: demisto/boto3py3:1.0.0.87655
tests:
- No Tests
fromversion: 5.0.0
diff --git a/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md b/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md
new file mode 100644
index 000000000000..9078c2c905c1
--- /dev/null
+++ b/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### AWS - CloudWatchLogs
+
+- Updated the Docker image to: *demisto/boto3py3:1.0.0.87655*.
diff --git a/Packs/AWS-CloudWatchLogs/pack_metadata.json b/Packs/AWS-CloudWatchLogs/pack_metadata.json
index 5a44101bb0a2..ac7edd3c9b04 100644
--- a/Packs/AWS-CloudWatchLogs/pack_metadata.json
+++ b/Packs/AWS-CloudWatchLogs/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "AWS - CloudWatchLogs",
"description": "Amazon Web Services CloudWatch Logs (logs).",
"support": "xsoar",
- "currentVersion": "1.2.18",
+ "currentVersion": "1.2.19",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/AWS-NetworkFirewall/Integrations/AWS-NetworkFirewall/AWS-NetworkFirewall.yml b/Packs/AWS-NetworkFirewall/Integrations/AWS-NetworkFirewall/AWS-NetworkFirewall.yml
index 9dd72d74fab6..4c365ed165ef 100755
--- a/Packs/AWS-NetworkFirewall/Integrations/AWS-NetworkFirewall/AWS-NetworkFirewall.yml
+++ b/Packs/AWS-NetworkFirewall/Integrations/AWS-NetworkFirewall/AWS-NetworkFirewall.yml
@@ -1512,7 +1512,7 @@ script:
- contextPath: AWS-NetworkFirewall.SubnetChangeProtection
description: A setting indicating whether the firewall is protected against changes to the subnet associations. Use this setting to protect against accidentally modifying the subnet associations for a firewall that is in use. When you create a firewall, the operation initializes this setting to TRUE.
type: Unknown
- dockerimage: demisto/boto3py3:1.0.0.41082
+ dockerimage: demisto/boto3py3:1.0.0.87655
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/AWS-NetworkFirewall/ReleaseNotes/1_0_5.md b/Packs/AWS-NetworkFirewall/ReleaseNotes/1_0_5.md
new file mode 100644
index 000000000000..0b9f87dc8ebb
--- /dev/null
+++ b/Packs/AWS-NetworkFirewall/ReleaseNotes/1_0_5.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### AWS Network Firewall
+
+- Updated the Docker image to: *demisto/boto3py3:1.0.0.87655*.
diff --git a/Packs/AWS-NetworkFirewall/pack_metadata.json b/Packs/AWS-NetworkFirewall/pack_metadata.json
index fbf61ab80e13..68716b84325e 100644
--- a/Packs/AWS-NetworkFirewall/pack_metadata.json
+++ b/Packs/AWS-NetworkFirewall/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "AWS - Network Firewall",
"description": "Amazon Web Services Network Firewall",
"support": "xsoar",
- "currentVersion": "1.0.4",
+ "currentVersion": "1.0.5",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/AWS_DynamoDB/Integrations/AWS_DynamoDB/AWS_DynamoDB.yml b/Packs/AWS_DynamoDB/Integrations/AWS_DynamoDB/AWS_DynamoDB.yml
index 171cc8150f60..a788462d90be 100644
--- a/Packs/AWS_DynamoDB/Integrations/AWS_DynamoDB/AWS_DynamoDB.yml
+++ b/Packs/AWS_DynamoDB/Integrations/AWS_DynamoDB/AWS_DynamoDB.yml
@@ -2989,7 +2989,7 @@ script:
description: The name of the TTL attribute used to store the expiration time for items in the table.
- contextPath: AWS-DynamoDB.TimeToLiveSpecification
description: Represents the output of an UpdateTimeToLive operation.
- dockerimage: demisto/boto3py3:1.0.0.41926
+ dockerimage: demisto/boto3py3:1.0.0.87655
script: ''
subtype: python3
type: python
diff --git a/Packs/AWS_DynamoDB/ReleaseNotes/1_0_32.md b/Packs/AWS_DynamoDB/ReleaseNotes/1_0_32.md
new file mode 100644
index 000000000000..4f053df45092
--- /dev/null
+++ b/Packs/AWS_DynamoDB/ReleaseNotes/1_0_32.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Amazon DynamoDB
+
+- Updated the Docker image to: *demisto/boto3py3:1.0.0.87655*.
diff --git a/Packs/AWS_DynamoDB/pack_metadata.json b/Packs/AWS_DynamoDB/pack_metadata.json
index 3eeacd1d9d23..31e515f5d478 100644
--- a/Packs/AWS_DynamoDB/pack_metadata.json
+++ b/Packs/AWS_DynamoDB/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Amazon DynamoDB",
"description": "Amazon DynamoDB Amazon DynamoDB is a fully managed NoSQL database service that provides fast and predictable performance with seamless scalability. DynamoDB lets you offload the administrative burdens of operating and scaling a distributed database, so that you don't have to worry about hardware provisioning, setup and configuration, replication, software patching, or cluster scaling. With DynamoDB, you can create database tables that can store and retrieve any amount of data, and serve any level of request traffic. You can scale up or scale down your tables' throughput capacity without downtime or performance degradation, and use the AWS Management Console to monitor resource utilization and performance metrics. DynamoDB automatically spreads the data and traffic for your tables over a sufficient number of servers to handle your throughput and storage requirements, while maintaining consistent and fast performance. All of your data is stored on solid state disks (SSDs) and automatically replicated across multiple Availability Zones in an AWS region, providing built-in high availability and data durability. ",
"support": "xsoar",
- "currentVersion": "1.0.31",
+ "currentVersion": "1.0.32",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/AWS_WAF/Integrations/AWSWAF/AWSWAF.yml b/Packs/AWS_WAF/Integrations/AWSWAF/AWSWAF.yml
index 09312563e557..35b967335714 100644
--- a/Packs/AWS_WAF/Integrations/AWSWAF/AWSWAF.yml
+++ b/Packs/AWS_WAF/Integrations/AWSWAF/AWSWAF.yml
@@ -1412,7 +1412,7 @@ script:
script: '-'
type: python
subtype: python3
- dockerimage: demisto/boto3py3:1.0.0.83962
+ dockerimage: demisto/boto3py3:1.0.0.87902
fromversion: 6.5.0
tests:
- No tests (auto formatted)
diff --git a/Packs/AWS_WAF/ReleaseNotes/1_0_5.md b/Packs/AWS_WAF/ReleaseNotes/1_0_5.md
new file mode 100644
index 000000000000..ffb77bbe894e
--- /dev/null
+++ b/Packs/AWS_WAF/ReleaseNotes/1_0_5.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### AWS-WAF
+
+- Updated the Docker image to: *demisto/boto3py3:1.0.0.87902*.
diff --git a/Packs/AWS_WAF/pack_metadata.json b/Packs/AWS_WAF/pack_metadata.json
index b1622a240d31..85f5f0eb4b83 100644
--- a/Packs/AWS_WAF/pack_metadata.json
+++ b/Packs/AWS_WAF/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "AWS WAF",
"description": "Amazon Web Services Web Application Firewall (WAF)",
"support": "xsoar",
- "currentVersion": "1.0.4",
+ "currentVersion": "1.0.5",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 3588960c74e7fcf866be95202bbade7d1fead1c6 Mon Sep 17 00:00:00 2001
From: Danny Fried
Date: Mon, 19 Feb 2024 08:08:28 +0200
Subject: [PATCH 021/272] Awssns listener (#31633)
* init commit
* Adding missing files,
* Remove unnecessary imports
* Adding test playbook.
Removing redundant fields from yml conf
* Adding the TPB to the yml test
* Ignoring secret
Deleting redundant file
* Fix validations issues
* Edit readme files.
* flake8 error
* Adding image
* Remove redundant import
* Remove redundant file.
Fix image name.
* Apply suggestions from code review
tech doc review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Fix wrong descriptions.
* Fix description in yml and README.
Fix TestPlaybook
* Add instance_names to TPB
* Adding store sample logic
* update docker version.
* Add a unique endpoint instead of the server builtin endpoint
* Adding validation to messages
* testing long running port
* with comments
* adding comments
* working
* Trying to validate the request
* Added proxy and verify to call
* Removed redundant log writes.
Added validation for version2
* Added integration username and password specific verification
* bump docker version
* Added additional info to username command
* updated the README
* Logs refactoring
* Specified a version in README
* remove TODO
* README description and yml changes.
* Code review changes
* Added support for baseclient
Added CSP implementation of handle proxy for long runnning integrations
* Code review changes
* Split long functions
* Extracting server config
* RN for CSP
* Fix READMS. bump docker version.
* ignoring false positive secrets
* changes ep on tbp
* ignore AWS-SNS_Listener TPB
* after merge from master
* Add unit tests
* ignore false positive secret
* fix pragma no cover annotation.
Bump Base version
* ignore demitso.error print from test.
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---
Packs/AWS-SNS-Listener/.pack-ignore | 2 +
Packs/AWS-SNS-Listener/.secrets-ignore | 3 +
.../AWSSNSListener/AWSSNSListener.py | 317 ++++++++++++++
.../AWSSNSListener/AWSSNSListener.yml | 73 ++++
.../AWSSNSListener_description.md | 32 ++
.../AWSSNSListener/AWSSNSListener_image.png | Bin 0 -> 4986 bytes
.../AWSSNSListener/AWSSNSListener_test.py | 113 +++++
.../Integrations/AWSSNSListener/README.md | 27 ++
Packs/AWS-SNS-Listener/README.md | 6 +
.../TestPlaybooks/AWS_SNS_Listener_-_Test.yml | 385 ++++++++++++++++++
Packs/AWS-SNS-Listener/pack_metadata.json | 22 +
Packs/Base/ReleaseNotes/1_33_32.md | 6 +
.../CommonServerPython/CommonServerPython.py | 36 ++
Packs/Base/pack_metadata.json | 2 +-
Tests/conf.json | 8 +-
15 files changed, 1030 insertions(+), 2 deletions(-)
create mode 100644 Packs/AWS-SNS-Listener/.pack-ignore
create mode 100644 Packs/AWS-SNS-Listener/.secrets-ignore
create mode 100644 Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener.py
create mode 100644 Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener.yml
create mode 100644 Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_description.md
create mode 100644 Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_image.png
create mode 100644 Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_test.py
create mode 100644 Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/README.md
create mode 100644 Packs/AWS-SNS-Listener/README.md
create mode 100644 Packs/AWS-SNS-Listener/TestPlaybooks/AWS_SNS_Listener_-_Test.yml
create mode 100644 Packs/AWS-SNS-Listener/pack_metadata.json
create mode 100644 Packs/Base/ReleaseNotes/1_33_32.md
diff --git a/Packs/AWS-SNS-Listener/.pack-ignore b/Packs/AWS-SNS-Listener/.pack-ignore
new file mode 100644
index 000000000000..b0151bdf4b20
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/.pack-ignore
@@ -0,0 +1,2 @@
+[file:AWSSNSListener.yml]
+ignore=BA124
\ No newline at end of file
diff --git a/Packs/AWS-SNS-Listener/.secrets-ignore b/Packs/AWS-SNS-Listener/.secrets-ignore
new file mode 100644
index 000000000000..1a0f000daf66
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/.secrets-ignore
@@ -0,0 +1,3 @@
+https://sns.eu-central-1.amazonaws.com
+https://user:pass@ext-myxsoar-address/xsoar/instance/execute/My-AWS-SNS-Listener/sns_ep
+https://link.pem
\ No newline at end of file
diff --git a/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener.py b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener.py
new file mode 100644
index 000000000000..5471d3105487
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener.py
@@ -0,0 +1,317 @@
+from CommonServerPython import * # noqa: F401
+from CommonServerUserPython import *
+from tempfile import NamedTemporaryFile
+from traceback import format_exc
+from collections import deque
+import uvicorn
+from secrets import compare_digest
+from fastapi import Depends, FastAPI, Request, Response, status
+from fastapi.security import HTTPBasic, HTTPBasicCredentials
+from fastapi.security.api_key import APIKeyHeader
+from fastapi.openapi.models import APIKey
+import base64
+from M2Crypto import X509
+
+
+PARAMS: dict = demisto.params()
+sample_events_to_store = deque(maxlen=20) # type: ignore[var-annotated]
+
+app = FastAPI(docs_url=None, redoc_url=None, openapi_url=None)
+basic_auth = HTTPBasic(auto_error=False)
+token_auth = APIKeyHeader(auto_error=False, name='Authorization')
+
+
+PROXIES, USE_SSL = handle_proxy_for_long_running()
+
+
+class AWS_SNS_CLIENT(BaseClient): # pragma: no cover
+ def __init__(self, base_url=None):
+ if PROXIES:
+ self.proxies = PROXIES
+ elif PARAMS.get('proxy'):
+ self.proxies = handle_proxy()
+ headers = {'Accept': 'application/json'}
+ super().__init__(base_url=base_url, proxy=bool(PROXIES), verify=USE_SSL, headers=headers)
+
+ def get(self, full_url, resp_type='json'):
+ return self._http_request(method='GET', full_url=full_url, proxies=PROXIES, resp_type=resp_type)
+
+
+client = AWS_SNS_CLIENT()
+
+
+class ServerConfig(): # pragma: no cover
+ def __init__(self, certificate_path, private_key_path, log_config, ssl_args):
+ self.certificate_path = certificate_path
+ self.private_key_path = private_key_path
+ self.log_config = log_config
+ self.ssl_args = ssl_args
+
+
+def is_valid_sns_message(sns_payload):
+ """
+ Validates an incoming Amazon Simple Notification Service (SNS) message.
+
+ Args:
+ sns_payload (dict): The SNS payload containing relevant fields.
+
+ Returns:
+ bool: True if the message is valid, False otherwise.
+ """
+ # taken from https://github.com/boto/boto3/issues/2508
+ demisto.debug('In is_valid_sns_message')
+ # Can only be one of these types.
+ if sns_payload["Type"] not in ["SubscriptionConfirmation", "Notification", "UnsubscribeConfirmation"]:
+ demisto.error('Not a valid SNS message')
+ return False
+
+ # Amazon SNS currently supports signature version 1 or 2.
+ if sns_payload.get("SignatureVersion") not in ["1", "2"]:
+ demisto.error('Not using the supported AWS-SNS SignatureVersion 1 or 2')
+ return False
+ demisto.debug(f'Handling Signature Version: {sns_payload.get("SignatureVersion")}')
+ # Fields for a standard notification.
+ fields = ["Message", "MessageId", "Subject", "Timestamp", "TopicArn", "Type"]
+
+ # Determine the required fields based on message type
+ if sns_payload["Type"] in ["SubscriptionConfirmation", "UnsubscribeConfirmation"]:
+ fields = ["Message", "MessageId", "SubscribeURL", "Timestamp", "Token", "TopicArn", "Type"]
+
+ # Build the string to be signed.
+ string_to_sign = ""
+ for field in fields:
+ string_to_sign += field + "\n" + sns_payload[field] + "\n"
+
+ # Verify the signature
+ decoded_signature = base64.b64decode(sns_payload["Signature"])
+ try:
+ response = client.get(full_url=sns_payload["SigningCertURL"], resp_type='response')
+ response.raise_for_status()
+ certificate = X509.load_cert_string(response.text)
+ except Exception as e:
+ demisto.error(f'Exception validating sign cert url: {e}')
+ return False
+
+ public_key = certificate.get_pubkey()
+ # Verify the signature based on SignatureVersion
+ if sns_payload["SignatureVersion"] == "1":
+ public_key.reset_context(md="sha1")
+ else: # version2
+ public_key.reset_context(md="sha256")
+
+ public_key.verify_init()
+ public_key.verify_update(string_to_sign.encode())
+ verification_result = public_key.verify_final(decoded_signature)
+
+ if verification_result != 1:
+ demisto.error('Signature verification failed.')
+ return False
+
+ demisto.debug('Signature verification succeeded.')
+ return True
+
+
+def is_valid_integration_credentials(credentials, request_headers, token):
+ credentials_param = PARAMS.get('credentials')
+ auth_failed = False
+ header_name = None
+ if credentials_param and (username := credentials_param.get('identifier')):
+ password = credentials_param.get('password', '')
+ if username.startswith('_header'):
+ header_name = username.split(':')[1]
+ token_auth.model.name = header_name
+ if not token or not compare_digest(token, password):
+ auth_failed = True
+ elif (not credentials) or (not (compare_digest(credentials.username, username)
+ and compare_digest(credentials.password, password))):
+ auth_failed = True
+ if auth_failed:
+ secret_header = (header_name or 'Authorization').lower()
+ if secret_header in request_headers:
+ request_headers[secret_header] = '***'
+ demisto.debug(f'Authorization failed - request headers {request_headers}')
+ if auth_failed: # auth failed not valid credentials
+ return False, header_name
+ else:
+ return True, header_name
+
+
+def handle_subscription_confirmation(subscribe_url) -> Response: # pragma: no cover
+ demisto.debug('SubscriptionConfirmation request')
+ try:
+ return client.get(full_url=subscribe_url)
+ except Exception as e:
+ demisto.error(f'Failed handling SubscriptionConfirmation: {e}')
+ return Response(status_code=status.HTTP_500_INTERNAL_SERVER_ERROR,
+ content='Failed handling SubscriptionConfirmation')
+
+
+def handle_notification(payload, raw_json):
+ message = payload['Message']
+ demisto.debug(f'Notification request msg: {message}')
+ return {
+ 'name': payload['Subject'],
+ 'labels': [],
+ 'rawJSON': raw_json,
+ 'occurred': payload['Timestamp'],
+ 'details': f'ExternalID:{payload["MessageId"]} TopicArn:{payload["TopicArn"]} Message:{message}',
+ 'type': 'AWS-SNS Notification'
+ }
+
+
+def store_samples(incident): # pragma: no cover
+ try:
+ sample_events_to_store.append(incident)
+ integration_context = get_integration_context()
+ sample_events = deque(json.loads(integration_context.get('sample_events', '[]')), maxlen=20)
+ sample_events += sample_events_to_store
+ integration_context['sample_events'] = list(sample_events)
+ set_to_integration_context_with_retries(integration_context)
+ except Exception as e:
+ demisto.error(f'Failed storing sample events - {e}')
+
+
+@app.post(f'/{PARAMS.get("endpoint","")}')
+async def handle_post(request: Request,
+ credentials: HTTPBasicCredentials = Depends(basic_auth),
+ token: APIKey = Depends(token_auth)): # pragma: no cover
+ """
+ Handles incoming AWS-SNS POST requests.
+ Supports SubscriptionConfirmation, Notification and UnsubscribeConfirmation.
+
+ Args:
+ request (Request): The incoming HTTP request.
+ credentials (HTTPBasicCredentials): Basic authentication credentials.
+ token (APIKey): API key for authentication.
+
+ Returns:
+ Union[Response, str]: Response data or error message.
+ """
+ data = ''
+ request_headers = dict(request.headers)
+ is_valid_credentials = False
+ try:
+ is_valid_credentials, header_name = is_valid_integration_credentials(credentials, request_headers, token)
+ except Exception as e:
+ demisto.error(f'Error handling auth failure: {e}')
+ if not is_valid_credentials:
+ return Response(status_code=status.HTTP_401_UNAUTHORIZED, content='Authorization failed.')
+
+ secret_header = (header_name or 'Authorization').lower()
+ request_headers.pop(secret_header, None)
+
+ try:
+ type = request_headers['x-amz-sns-message-type']
+ payload = await request.json()
+ raw_json = json.dumps(payload)
+ except Exception as e:
+ demisto.error(f'Error in request parsing: {e}')
+ return Response(status_code=status.HTTP_400_BAD_REQUEST, content='Failed parsing request.')
+ if not is_valid_sns_message(payload):
+ return 'Validation of SNS message failed.'
+
+ if type == 'SubscriptionConfirmation':
+ demisto.debug('SubscriptionConfirmation request')
+ subscribe_url = payload['SubscribeURL']
+ try:
+ response = handle_subscription_confirmation(subscribe_url=subscribe_url)
+ response.raise_for_status()
+ except Exception as e:
+ demisto.error(f'Failed handling SubscriptionConfirmation: {e}')
+ return 'Failed handling SubscriptionConfirmation'
+ demisto.debug(f'Response from subscribe url: {response}')
+ return response
+ elif type == 'Notification':
+ incident = handle_notification(payload, raw_json)
+ data = demisto.createIncidents(incidents=[incident])
+ demisto.debug(f'Created incident: {incident}')
+ if PARAMS.get('store_samples'):
+ store_samples(incident)
+ if not data:
+ demisto.error('Failed creating incident')
+ data = 'Failed creating incident'
+ return data
+ elif type == 'UnsubscribeConfirmation':
+ message = payload['Message']
+ demisto.debug(f'UnsubscribeConfirmation request msg: {message}')
+ return f'UnsubscribeConfirmation request msg: {message}'
+ else:
+ demisto.error(f'Failed handling AWS SNS request, unknown type: {payload["Type"]}')
+ return f'Failed handling AWS SNS request, unknown type: {payload["Type"]}'
+
+
+def unlink_certificate(certificate_path, private_key_path): # pragma: no cover
+ if certificate_path:
+ os.unlink(certificate_path)
+ if private_key_path:
+ os.unlink(private_key_path)
+ time.sleep(5)
+
+
+def setup_server(): # pragma: no cover
+ certificate = PARAMS.get('certificate', '')
+ private_key = PARAMS.get('key', '')
+
+ certificate_path = ''
+ private_key_path = ''
+ ssl_args = {}
+ if certificate and private_key:
+ certificate_file = NamedTemporaryFile(delete=False)
+ certificate_path = certificate_file.name
+ certificate_file.write(bytes(certificate, 'utf-8'))
+ certificate_file.close()
+ ssl_args['ssl_certfile'] = certificate_path
+
+ private_key_file = NamedTemporaryFile(delete=False)
+ private_key_path = private_key_file.name
+ private_key_file.write(bytes(private_key, 'utf-8'))
+ private_key_file.close()
+ ssl_args['ssl_keyfile'] = private_key_path
+
+ demisto.debug('Starting HTTPS Server')
+ else:
+ demisto.debug('Starting HTTP Server')
+
+ integration_logger = IntegrationLogger()
+ integration_logger.buffering = False
+ log_config = dict(uvicorn.config.LOGGING_CONFIG)
+ log_config['handlers']['default']['stream'] = integration_logger
+ log_config['handlers']['access']['stream'] = integration_logger
+ return ServerConfig(log_config=log_config, ssl_args=ssl_args,
+ certificate_path=certificate_path, private_key_path=private_key_path)
+
+
+''' MAIN FUNCTION '''
+
+
+def main(): # pragma: no cover
+ demisto.debug(f'Command being called is {demisto.command()}')
+ try:
+ try:
+ port = PARAMS.get('longRunningPort')
+ except ValueError as e:
+ raise ValueError(f'Invalid listen port - {e}')
+ if demisto.command() == 'test-module':
+ return_results("ok")
+ elif demisto.command() == 'long-running-execution':
+ demisto.debug('Started long-running-execution.')
+ while True:
+ server_config = setup_server()
+ if not server_config:
+ raise DemistoException('Failed to configure server.')
+ try:
+ uvicorn.run(app, host='0.0.0.0', port=port, log_config=server_config.log_config, **server_config.ssl_args)
+ except Exception as e:
+ demisto.error(f'An error occurred in the long running loop: {str(e)} - {format_exc()}')
+ demisto.updateModuleHealth(f'An error occurred: {str(e)}')
+ finally:
+ unlink_certificate(server_config.certificate_path, server_config.private_key_path)
+ else:
+ raise NotImplementedError(f'Command {demisto.command()} is not implemented.')
+ except Exception as e:
+ demisto.error(format_exc())
+ return_error(f'Failed to execute {demisto.command()} command. Error: {e}')
+
+
+if __name__ in ('__main__', '__builtin__', 'builtins'):
+ main()
diff --git a/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener.yml b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener.yml
new file mode 100644
index 000000000000..f554c661c8f7
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener.yml
@@ -0,0 +1,73 @@
+category: Messaging and Conferencing
+sectionOrder:
+- Connect
+- Collect
+commonfields:
+ id: AWS-SNS-Listener
+ version: -1
+configuration:
+- display: Long running instance
+ defaultvalue: 'true'
+ name: longRunning
+ type: 8
+ hidden: true
+ section: Connect
+ advanced: true
+ required: false
+- additionalinfo: "Runs the service on this port from within Cortex XSOAR. Requires a unique port for each long-running integration instance. Do not use the same port for multiple instances. Note: If you click the test button more than once, a failure may occur mistakenly indicating that the port is already in use. (For Cortex XSOAR 8 and Cortex XSIAM) If you do not enter a Listen Port, an unused port for AWS SNS Listener will automatically be generated when the instance is saved. However, if using an engine, you must enter a Listen Port."
+ display: Listen Port
+ name: longRunningPort
+ type: 0
+ required: false
+ section: Connect
+- additionalinfo: Uses basic authentication for accessing the list. If empty, no authentication is enforced. (For Cortex XSOAR 8 and Cortex XSIAM) Optional for engines, otherwise mandatory.
+ display: Username
+ name: credentials
+ type: 9
+ section: Connect
+ required: false
+- additionalinfo: "Set the endpoint of your listener. example: /snsv2"
+ display: Endpoint
+ name: endpoint
+ type: 0
+ section: Connect
+ required: false
+- display: Certificate (Required for HTTPS)
+ additionalinfo: "(For Cortex XSOAR 6.x) For use with HTTPS - the certificate that the service should use. (For Cortex XSOAR 8 and Cortex XSIAM) Custom certificates are not supported."
+ name: certificate
+ type: 12
+ section: Connect
+ required: false
+- display: Private Key (Required for HTTPS)
+ additionalinfo: "(For Cortex XSOAR 6.x) For use with HTTPS - the private key that the service should use. (For Cortex XSOAR 8 and Cortex XSIAM) When using an engine, configure a private API key. Not supported on the Cortex XSOAR or Cortex XSIAM server."
+ name: key
+ type: 14
+ section: Connect
+ required: false
+- additionalinfo: "Because this is a push-based integration, it cannot fetch sample events in the mapping wizard. After you finish mapping, it is recommended to turn off the sample events storage to reduce performance overhead."
+ display: Store sample events for mapping
+ name: store_samples
+ type: 8
+ section: Connect
+ required: false
+- display: Use system proxy settings
+ name: proxy
+ type: 8
+ section: Connect
+ advanced: true
+ required: false
+description: 'Amazon Simple Notification Service (SNS) is a managed service that provides message delivery from publishers to subscribers.'
+display: AWS-SNS-Listener
+name: AWS-SNS-Listener
+script:
+ commands: []
+ dockerimage: demisto/fastapi:1.0.0.87576
+ longRunning: true
+ longRunningPort: true
+ script: '-'
+ subtype: python3
+ type: python
+ isFetchSamples: true
+fromversion: 6.10.0
+tests:
+- AWS SNS Listener - Test
diff --git a/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_description.md b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_description.md
new file mode 100644
index 000000000000..8d4d6f80c3b9
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_description.md
@@ -0,0 +1,32 @@
+## AWS-SNS-Listener Help
+
+In order to configure the AWS-SNS-Listener
+
+XSOAR6
+
+* http: configure an endpoint and a free port for the internal long running server.
+* https: In addition to http configuration please add a CA certificate and private
+* key AWS-SNS works only with CA certificates.
+* Another option is via engine.
+
+Configuring the subscriber on AWS-SNS UI is straightforward:
+http/https://:/
+For more general information on long running integrations on XSOAR6:
+https://xsoar.pan.dev/docs/reference/articles/long-running-invoke
+
+XSOAR8 or XSIAM:
+
+* The instance should be configured to run only on HTTP.
+* The instance is using the HTTPS certificate of the server.
+* Please set a user and password (can be global via long running integrations configurations)
+* or local for this integration only.
+
+Configuring the subscriber on AWS-SNS UI:
+https://@ext-/xsoar/instance/execute/
+
+example:
+https://user:pass@ext-myxsoar-address/xsoar/instance/execute/My-AWS-SNS-Listener/sns_ep
+
+For more info on long running integrations on XSOAR8 or XSIAM:
+https://docs-cortex.paloaltonetworks.com/r/Cortex-XSOAR/8/Cortex-XSOAR-Administrator-Guide/Forward-Requests-to-Long-Running-Integrations
+
diff --git a/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_image.png b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_image.png
new file mode 100644
index 0000000000000000000000000000000000000000..e2af23f59a4ed639a62d0dde10db58e702e34c1c
GIT binary patch
literal 4986
zcmV-=6NT)FP)bB&^AM_ntHVbKkp1!JceV2awm8
zhMY0@+L{_l!3lw5CU87q?PoTD<0eTF`UJr-5%?EVDjs2sP4E1?GlAnKOA-3-3_2Yf
zlys-Fgp_lgRc?Ic{2n26pFVxEvobQqapK=6CUb#*CrP=iJ`i|4zF)c9eYt5;zF@4`
z-{4>3b-Bhc#?KQ{w6^Tt{akBn>#knCdgW$kXHNvfx|tB`e8J%S&hwR*m*o!(C}`2zfzB9EY{MC%mj;;vZcN;@J9S2uh)A83Hm;fkdm<#e!u_C
zPVHXI^8+TiQ5W>RQC3#gUxvez1?QO@^VbCeAJSo<%M$$Zw4p@SyBcGK)agC2O`q-D-FjIIK(&>*Jwcp{u(=Jmtzw)#
zWcLLj{Na!o=Wwv!<6Ta%pPN#y-g{vG54UgMzE|CQUEUuPm-9HW0ctibJIwcH%icYc
zckbM|+gh93y@@kko^W%e+_yR4w>GDwu+YPt&bNrM;p#q$Q-Uux8N$3I7!1~`2OhWk
zX}srDsYaXfPK~pBvDP9RCHhVSL(Wb#9j7CJvaz#&Hn@7fkgM@>^^m^mjjvYTzW$X;
zFC8O9CAwPS?2gwBhE8Xi`3_!sfRuP?Ar?tf{Kk@C0B7vHUfH=*;>Tb^)R7P3JZQ}w
zB@l?<0dW^9;!0~t5de;1S?TE)sB2em*8tAx1s%jy8wP254U_&Jmu=C$<8m`Hu8EB$
z76hgy89h3@vy}F|gFBpmK;Pj^km8aL!6@%2^cvAXC$YDB_wJn&hZ79In8x`ubQvJy
z7))dQ{xi-v!;xsO4ol$KQ!2cQuyCNNDb9gXM1dZeqljJHH)9O-0Cbno;c&PDFIixX
zWwNR^7`URgA#gKEG0pA+6s%yudTvwUJbBPCHR
zf+K^x1m;+JJv#ZNN7`9VCofK~!P4878|*oy%OV
zv6%PV$Of42)dl<);Q-FeCX88)
zt&O`%a$SoxuKlZeE`(fD7Yr;_*JUox`#Aj|I>Z_eRk;kO%z}b~Tusx2l4ys627s)k
zG2}v|bzY~kol?kWAmLoiEtq`Jzs0{g@~-^C*jkA%KDbD>6tn&`GC3QK(>z_VhZb!X
z;uT*ou)$iZ+r1ur&QjN!&~hjN#0acZacTd|+s_!7=Vv5qK3&`5`KGmmX|Vf{3cFpPMYDG^4&d1IVPW$Y5Na%>
zzYN1Nk2DuI<#U|FW=Gy?`I&zIaDqGfXsKz+SFl&ZG2bnTaF%#H_rQ#evTlUj
zE_6Ntu6@j}2JtfE7&3M#xeTj!vP=ZD)FFrk3F-#uQS=`A7K4y%X#713i>tV9+gPy(
zVS?ogl(`UY90kZDv^y9Z&!fbJIjw>^zg}IJxIF2J`nz1NGc{sQMEb+RO7l8jz26_-
z2NL`>{#)+=XEE1)4#v%35h=r1R!_$WNA#kF5svkDGA&z%~zdLo1wf@rRJOt_NjUfarMC?ZiPA>
zf}3qz3WIt8OwL~hJKY+IQsh8QlbZlsZP!cfYsX!`&v
z+EUFJTZ(}BQe5Vl4pVOoHg5407vHFB`kTtnL-ZTXoN+~56XWjzbJnRRaZYpxkaXls
zRZ5Qh;Z4K1H0nCSFURuz*_lKA(+-d0=vRs#dpg{|7L&E|$-oxo|-j8LJ
z!?}WIF8_+-zmabJ)Ez_4A{nUc+E}LR&mGmx{s9D9?CKrK3du1_zN@(Cz>F$?7
zXAZLBdGc>PKr1)4#ya-SbJ7oo^y)Bp<=3s`-*(^-q+Lx_b`|jQH5KEl&!-*&MFeb0
z1_;+gCjiv^yLRnjDhE!-8Isb;I#$q3dACEdE#Cb69!=DA6_}8J?wwokKlFEiBF9NwP;g?8AW4jEBW9kPnwUVXdjhAt?!Lr6{wqo+m?axn#N=u~8!%8H7LPQpt)hNH~kWPgG~)EjZ^Mewd)
zMAhXts0II6jZrB|I88TU^X4NvITT*(a=Us{Qsll8-t8M8tWx34D9_!aWio4X&GyhA
zQPz7D8LxF1o5vk|iMz;s0pxWYoZ;tnozKNuPEFI0zL4x^aJa^+aada~&iQ|Uhz7!|
zYtZMal9G~s4kv#PcvSp;fHUn0W{SD0f2qs!1d=6lRe2G(Td>+HFvzV|WlIz9;QoAM
zP&UHt8i~r<7lvUVdXQnHSu?n4UIhYAP=Cz8bL@Ob|TL>hyb_vetN`vt-tbla|LcKpp?Ud5fLCY`$3=Ytn4eOQadP&((=
z;##z|7_kHg8OBXmx65d6yRgphABV8(F;#jjEh-ua{<{H2q^hnVa9v%{|5H@4mVp6o
z(KGaNj70T|evP&}WH>YeYyB@(1Th%<3z?x6NTR%9n&zX{yp*gU5c_hvIXfdm5lqFQ
zJ0J;{I*8SR>(^*Z%dv!%({FRq(k*+34O0aPRVeqPzclvK|EcGuPG4%ms_C7o?xFfW
zgZjHibEYjT^?24|;0nR{Tx{Z%mT{G0A}Tqf!9*%+oEIJUF{YDy+uCgtfG9@(5e#uV
zQkP}W9!g3-Y1-4&TviatgJ6xPsRCDE>sBkAL-ag1YzpAfQOuw`5biw8qbgY{{w`Ht
ziR=v>*pTf^4?qjdDtCD=g9LvKNnV5k$_{kf5uH00G9|4S9U`-aRB@bX4_LRPzP6z6
zL5NUO6Mcap0A?jdgye6B3~?cbe*pp(
zL+bD2ChEjo>l0}g)o6QH9k`w;3^7AJ2Lakqm)&RMms0x^_$Cb=`;}mt5$HFs<6B5I
zf17>xbuiczX8d!E$+EuQU~=ujdE_&OA@1I}W9Rk|iIHHQ=OZOic>`?z;_|5J=?qCr
zU?e*lu?fqSih~@z4aaAmDjBMT1{Bl#pu*ayopnQXZx%vqal%GQJ#B)G14V?B;mA-r
z=|e1|%;bh>(+!%=&P6SEG*So^kdWITiN$cei&Z1k=nBTP*-#I^#C00%uu3!?;x%XF
zWGF@pFpb{_DbFOQ_HleWvQRi;Hcf^fJP0?El=04LNbQ#fzN@g%ZO4?|VE6RmIEx^*E)+G~ug!pDmG`uYwPC6h7L
z)}}MA9IKn4E$+uWOW<{{0=Ilj8ovd)S!t+y8JF-CjzDJ0UIv=T&~3FqgVa7bPbtzf0);M6<>Z+9-F_G);>FJR+UI`p2}VDNvL6r-go
zb`U*>an~Vh{7_vm_&99gZV;fc^BTFymcUf6L5TLO{S4#(3V&cNGHI(!MpGfJ>Jy}A
zFwaIZjj5^&B=Z_L1s{Q!)1f)QM6{^Q4Bvta_mbwov+%)Z)^jhOL)L49zAoWOc1T(Rm%6>m
zOHop77t7Vx56ez2^44!^^r?Gvu-a>)Z8oUn#ZPcp<+(DKSE&fq?{tdT%FcL_8Z5qr
z3VaHu1r8|t_I8ycIG$=RlAib3k
z$9XvaN=axOsBfd=!<8$dc!tE`S%s@%^bY`*1W)_*`h_?xT=LlI^S3m%PRh+or@U;Z
zWp|rf!zgJ<#q~Y*OT>hrh{@)q+)5Dhc)Gd#imdzC)*F^q+XKJMBELg~#okFLe49MKnNCLkAT->Y=sQzc=gj
zA-h}Kh87k&8Jw#6LF21S)kp9rrOQ>@w(cnig$#s$jEahTw9@7qG@)jAcLsncUMQSa
z5LJDGC^_sZ60wtEU*kW}Yk?|w0eVVFtdhuGa^5UK~|>3=WC%o`^}HCGPIHm2eTMKfl~P=os@Mrv_6bIKmJE;
zT?I(pB(NyrQX0x4PL&@LI2O*)YO9UWBT&61u)&pJhHA784?AcV2w0EjtOFiKBftnl
zSj2|=LHN7OJ+vT^T2ChER-$9ngI`r4_*PPFN$d9Qd!>?2{8cFeje6iqUrwerQj?S+ln^J?xmoqPASSA+9s#M(h*
zw2g%%boky#{R-0vC;Es%R8jX~5{^16REh$MDza#E(C61k)
z@gTc&mxU)k`3Zd7Jmb#lTtRxeg9-=4KH|3|zhZpN_0&zUzFZVk2gaI-7kJA4d=%$@
z!+9d4u{2&q+v99it*(`dj>Gd5#?4HGhmstQTP`|Io!fCOwY7z*wKY~9qj<^h4)~O@
zM~H;W+bB{4RRx3{@Tx~3?>siHYX|SnQq_zW*v}On^dCtP=PHH=$Cyrdk`|6{YzugQ
z)+umW^bx3MjzO8GQiWJ>&X^-jJ1Xhz3`#21+0ZTR>Z7BCp2G8OgX2!%cvvufXnvYz
zR%T^8$Mo%=GvjDH=M;pDLB6H|9_RUL9Fv$RR91007*qoM6N<$
Ef)SOZ%>V!Z
literal 0
HcmV?d00001
diff --git a/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_test.py b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_test.py
new file mode 100644
index 000000000000..9a6f91da2418
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/AWSSNSListener_test.py
@@ -0,0 +1,113 @@
+import pytest
+from AWSSNSListener import handle_notification, is_valid_sns_message, is_valid_integration_credentials
+from unittest.mock import patch
+import requests
+
+VALID_PAYLOAD = {
+ "Type": "Notification",
+ "MessageId": "uuid",
+ "TopicArn": "topicarn",
+ "Subject": "NotificationSubject",
+ "Message": "NotificationMessage",
+ "Timestamp": "2024-02-13T18:03:27.239Z",
+ "SignatureVersion": "1",
+ "Signature": b"sign",
+ "SigningCertURL": "https://link.pem",
+}
+
+
+@pytest.fixture
+def mock_params(mocker):
+ return mocker.patch('AWSSNSListener.PARAMS', new={'credentials': {'identifier': 'foo', 'password': 'bar'}},
+ autospec=False)
+
+
+def test_handle_notification_valid():
+ '''
+ Given a valid SNS notification message
+ When handle_notification is called with the message and raw json
+ Then should parse to a valid incident
+ '''
+ raw_json = {}
+ expected_notification = {
+ 'name': 'NotificationSubject',
+ 'labels': [],
+ 'rawJSON': raw_json,
+ 'occurred': '2024-02-13T18:03:27.239Z',
+ 'details': 'ExternalID:uuid TopicArn:topicarn Message:NotificationMessage',
+ 'type': 'AWS-SNS Notification'
+ }
+
+ actual_incident = handle_notification(VALID_PAYLOAD, raw_json)
+
+ assert actual_incident == expected_notification
+
+
+@patch("AWSSNSListener.client")
+@patch("AWSSNSListener.X509")
+@patch("M2Crypto.EVP.PKey")
+def test_is_valid_sns_message(mock_client, mock_x509, mock_PKey):
+ mock_resp = requests.models.Response()
+ mock_resp.status_code = 200
+ response_content = '''-----BEGIN VALID CERTIFICATE-----
+ -----END CERTIFICATE-----'''
+ mock_resp._content = str.encode(response_content)
+ mock_client.get.return_value = mock_resp
+ mock_PKey.verify_final.return_value = 1
+ mock_x509.get_pubkey.return_value = mock_PKey
+ mock_x509.load_cert_string.return_value = mock_x509
+ is_valid = is_valid_sns_message(VALID_PAYLOAD)
+ assert is_valid
+
+
+@patch("AWSSNSListener.client")
+@patch("AWSSNSListener.X509")
+@patch("M2Crypto.EVP.PKey")
+def test_not_valid_sns_message(mock_client, mock_x509, mock_PKey, capfd):
+ mock_resp = requests.models.Response()
+ mock_resp.status_code = 200
+ response_content = '''-----BEGIN INVALID CERTIFICATE-----
+ -----END CERTIFICATE-----'''
+ mock_resp._content = str.encode(response_content)
+ mock_client.get.return_value = mock_resp
+ mock_PKey.verify_final.return_value = 2
+ mock_x509.get_pubkey.return_value = mock_PKey
+ mock_x509.load_cert_string.return_value = mock_x509
+ with capfd.disabled():
+ is_valid = is_valid_sns_message(VALID_PAYLOAD)
+ assert is_valid is False
+
+
+@patch('fastapi.security.http.HTTPBasicCredentials')
+def test_valid_credentials(mock_httpBasicCredentials, mock_params):
+ """
+ Given valid credentials, request headers and token
+ When is_valid_integration_credentials is called
+ Then it should return True, header_name
+ """
+ mock_httpBasicCredentials.username = 'foo'
+ mock_httpBasicCredentials.password = 'bar'
+ request_headers = {}
+ token = "sometoken"
+ result, header_name = is_valid_integration_credentials(
+ mock_httpBasicCredentials, request_headers, token
+ )
+ assert result is True
+ assert header_name is None
+
+
+@patch('fastapi.security.http.HTTPBasicCredentials')
+def test_invalid_credentials(mock_httpBasicCredentials, mock_params):
+ """
+ Given invalid credentials, request headers and token
+ When is_valid_integration_credentials is called
+ Then it should return True, header_name
+ """
+ mock_httpBasicCredentials.username = 'foot'
+ mock_httpBasicCredentials.password = 'bark'
+ request_headers = {}
+ token = "sometoken"
+ result, header_name = is_valid_integration_credentials(
+ mock_httpBasicCredentials, request_headers, token
+ )
+ assert result is False
diff --git a/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/README.md b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/README.md
new file mode 100644
index 000000000000..2afae159959c
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/Integrations/AWSSNSListener/README.md
@@ -0,0 +1,27 @@
+Amazon Simple Notification Service (SNS) is a managed service that provides message delivery from publishers to subscribers.
+This integration was integrated and tested with version January 2024 of AWS-SNS-Listener.
+
+## Configure AWS-SNS-Listener on Cortex XSOAR
+
+1. Navigate to **Settings** > **Integrations** > **Servers & Services**.
+2. Search for AWS-SNS-Listener.
+3. Click **Add instance** to create and configure a new integration instance.
+
+ | **Parameter** | **Description** | **Required** |
+ | --- | --- | --- |
+ | Long running instance | | False |
+ | Listen Port | Runs the service on this port from within Cortex XSOAR. Requires a unique port for each long-running integration instance. Do not use the same port for multiple instances. Note: If you click the test button more than once, a failure may occur mistakenly indicating that the port is already in use. \(For Cortex XSOAR 8 and Cortex XSIAM\) If you do not enter a Listen Port, an unused port for AWS SNS Listener will automatically be generated when the instance is saved. However, if using an engine, you must enter a Listen Port. | False |
+ | Username | Uses basic authentication for accessing the list. If empty, no authentication is enforced. \(For Cortex XSOAR 8 and Cortex XSIAM\) Optional for engines, otherwise mandatory. | False |
+ | Password | | False |
+ | Endpoint | Set the endpoint of your listener. example: /snsv2 | False |
+ | Certificate (Required for HTTPS) | \(For Cortex XSOAR 6.x\) For use with HTTPS - the certificate that the service should use. \(For Cortex XSOAR 8 and Cortex XSIAM\) Custom certificates are not supported. | False |
+ | Private Key (Required for HTTPS) | \(For Cortex XSOAR 6.x\) For use with HTTPS - the private key that the service should use. \(For Cortex XSOAR 8 and Cortex XSIAM\) When using an engine, configure a private API key. Not supported on the Cortex XSOAR or Cortex XSIAM server. | False |
+ | Store sample events for mapping | Because this is a push-based integration, it cannot fetch sample events in the mapping wizard. After you finish mapping, it is recommended to turn off the sample events storage to reduce performance overhead. | False |
+ | Use system proxy settings | | False |
+
+4. Click **Test** to validate the URLs, token, and connection.
+
+## Commands
+
+You can execute these commands from the Cortex XSOAR CLI, as part of an automation, or in a playbook.
+After you successfully execute a command, a DBot message appears in the War Room with the command details.
diff --git a/Packs/AWS-SNS-Listener/README.md b/Packs/AWS-SNS-Listener/README.md
new file mode 100644
index 000000000000..246c33a23f0f
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/README.md
@@ -0,0 +1,6 @@
+Amazon Simple Notification Service (SNS) is a managed service that provides message delivery from publishers to subscribers. Publishers communicate asynchronously with subscribers by sending messages to a topic, which is a logical access point and communication channel. Clients can subscribe to the SNS topic and receive published messages using a supported endpoint type, such as Amazon Kinesis Data Firehose, Amazon SQS, AWS Lambda, HTTP, email, mobile push notifications, and mobile text messages (SMS).
+
+## What does this pack do
+The AWS SNS Listener supports two types of POST requests:
+* SubscriptionConfirmation: Extract the subscription URL send subscription confirmation.
+* Notification: Extract the subject and message body and creates a Cortex XSOAR / Cortex XSIAM incident.
\ No newline at end of file
diff --git a/Packs/AWS-SNS-Listener/TestPlaybooks/AWS_SNS_Listener_-_Test.yml b/Packs/AWS-SNS-Listener/TestPlaybooks/AWS_SNS_Listener_-_Test.yml
new file mode 100644
index 000000000000..11365dfe5b51
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/TestPlaybooks/AWS_SNS_Listener_-_Test.yml
@@ -0,0 +1,385 @@
+id: AWS SNS Listener - Test
+version: -1
+name: AWS SNS Listener - Test
+starttaskid: "0"
+tasks:
+ "0":
+ id: "0"
+ taskid: 976ffcfd-467b-4c2a-82ee-9285ddb6d84a
+ type: start
+ task:
+ id: 976ffcfd-467b-4c2a-82ee-9285ddb6d84a
+ version: -1
+ name: ""
+ iscommand: false
+ brand: ""
+ description: ''
+ nexttasks:
+ '#none#':
+ - "6"
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 50
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "1":
+ id: "1"
+ taskid: 89106f4b-7057-44e3-81d0-5715f937de6d
+ type: regular
+ task:
+ id: 89106f4b-7057-44e3-81d0-5715f937de6d
+ version: -1
+ name: Post a msg to SNS-Listener
+ description: Sends http request. Returns the response as json.
+ scriptName: http
+ type: regular
+ iscommand: false
+ brand: ""
+ nexttasks:
+ '#none#':
+ - "7"
+ scriptarguments:
+ body:
+ simple: |-
+ {"Type": "Notification",
+ "MessageId": "afe031bb-5ef5-53b1-b1ad-6c4a4288defb",
+ "TopicArn": "arn:aws:sns:eu-central-1:test:test",
+ "Subject": "SNS-test-subject",
+ "Message": "SNS-test-message body",
+ "Timestamp": "2023-12-11T14:18:37.923Z",
+ "SignatureVersion": "1",
+ "Signature": "Signature_test",
+ "SigningCertURL": "https://sns.eu-central-1.amazonaws.com/SimpleNotificationService-01d088a6f77103d0fe307c0069e40ed6.pem",
+ "UnsubscribeURL": "https://sns.eu-central-1.amazonaws.com/?Action=Unsubscribe"
+ }
+ headers:
+ simple: Authorization:token
+ method:
+ simple: POST
+ url:
+ simple: http://localhost:9000/incident/aws/
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 545
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "2":
+ id: "2"
+ taskid: 38bf8674-3546-47e1-8d8f-8c921e45733a
+ type: regular
+ task:
+ id: 38bf8674-3546-47e1-8d8f-8c921e45733a
+ version: -1
+ name: Search the incident
+ description: Searches Demisto incidents
+ scriptName: SearchIncidentsV2
+ type: regular
+ iscommand: false
+ brand: ""
+ nexttasks:
+ '#none#':
+ - "3"
+ scriptarguments:
+ name:
+ simple: SNS-test-subject
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 1070
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "3":
+ id: "3"
+ taskid: 0ee4c9b7-8a4b-4c59-8064-d01b5214d888
+ type: condition
+ task:
+ id: 0ee4c9b7-8a4b-4c59-8064-d01b5214d888
+ version: -1
+ name: Verify incident was created successfully
+ type: condition
+ iscommand: false
+ brand: ""
+ nexttasks:
+ "yes":
+ - "4"
+ separatecontext: false
+ conditions:
+ - label: "yes"
+ condition:
+ - - operator: isExists
+ left:
+ value:
+ simple: foundIncidents.id
+ iscontext: true
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 1245
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "4":
+ id: "4"
+ taskid: 3daf5a1f-bf67-474d-8a4e-c63f02eb544c
+ type: regular
+ task:
+ id: 3daf5a1f-bf67-474d-8a4e-c63f02eb544c
+ version: -1
+ name: Close webhook triggered incident
+ description: commands.local.cmd.close.inv
+ script: Builtin|||closeInvestigation
+ type: regular
+ iscommand: true
+ brand: Builtin
+ nexttasks:
+ '#none#':
+ - "10"
+ scriptarguments:
+ id:
+ simple: ${foundIncidents.id}
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 1420
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "6":
+ id: "6"
+ taskid: 5bf72787-3920-4dd6-87c2-11e307629d7c
+ type: regular
+ task:
+ id: 5bf72787-3920-4dd6-87c2-11e307629d7c
+ version: -1
+ name: DeleteContext
+ description: Delete field from context
+ scriptName: DeleteContext
+ type: regular
+ iscommand: false
+ brand: ""
+ nexttasks:
+ '#none#':
+ - "8"
+ scriptarguments:
+ all:
+ simple: "yes"
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 195
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "7":
+ id: "7"
+ taskid: 813fcb90-ff23-4e50-80df-48cc4890cf29
+ type: condition
+ task:
+ id: 813fcb90-ff23-4e50-80df-48cc4890cf29
+ version: -1
+ name: Verify Success HTTP Response
+ type: condition
+ iscommand: false
+ brand: ""
+ nexttasks:
+ "yes":
+ - "9"
+ separatecontext: false
+ conditions:
+ - label: "yes"
+ condition:
+ - - operator: isEqualNumber
+ left:
+ value:
+ simple: HttpRequest.Response.StatusCode
+ iscontext: true
+ right:
+ value:
+ simple: "200"
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 720
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "8":
+ id: "8"
+ taskid: 813e76da-af96-4d95-8d93-fe10e0a71e56
+ type: regular
+ task:
+ id: 813e76da-af96-4d95-8d93-fe10e0a71e56
+ version: -1
+ name: Sleep 10 seconds to let the webserver spin up
+ description: Sleep for X seconds
+ scriptName: Sleep
+ type: regular
+ iscommand: false
+ brand: ""
+ nexttasks:
+ '#none#':
+ - "1"
+ scriptarguments:
+ seconds:
+ simple: "10"
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 370
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "9":
+ id: "9"
+ taskid: 2bb0bae1-4241-4c88-8d85-ebe7c1586580
+ type: regular
+ task:
+ id: 2bb0bae1-4241-4c88-8d85-ebe7c1586580
+ version: -1
+ name: Sleep 10 seconds before searching the incident
+ description: Sleep for X seconds
+ scriptName: Sleep
+ type: regular
+ iscommand: false
+ brand: ""
+ nexttasks:
+ '#none#':
+ - "2"
+ scriptarguments:
+ seconds:
+ simple: "10"
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 895
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "10":
+ id: "10"
+ taskid: d5fbc51b-96bc-4723-8c71-ff960b4eab70
+ type: title
+ task:
+ id: d5fbc51b-96bc-4723-8c71-ff960b4eab70
+ version: -1
+ name: Done
+ type: title
+ iscommand: false
+ brand: ""
+ description: ''
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 50,
+ "y": 1580
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+view: |-
+ {
+ "linkLabelsPosition": {},
+ "paper": {
+ "dimensions": {
+ "height": 1595,
+ "width": 380,
+ "x": 50,
+ "y": 50
+ }
+ }
+ }
+inputs: []
+outputs: []
+fromversion: 6.10.0
+description: ''
diff --git a/Packs/AWS-SNS-Listener/pack_metadata.json b/Packs/AWS-SNS-Listener/pack_metadata.json
new file mode 100644
index 000000000000..b506aa119a11
--- /dev/null
+++ b/Packs/AWS-SNS-Listener/pack_metadata.json
@@ -0,0 +1,22 @@
+{
+ "name": "AWS-SNS-Listener",
+ "description": "A long running AWS SNS Listener service that can subscribe to an SNS topic and create incidents from the messages received.",
+ "support": "xsoar",
+ "currentVersion": "1.0.0",
+ "author": "Cortex XSOAR",
+ "url": "https://www.paloaltonetworks.com/cortex",
+ "email": "",
+ "created": "2023-01-12T00:00:00Z",
+ "categories": [
+ "Cloud Services"
+ ],
+ "tags": [],
+ "useCases": [],
+ "keywords": [
+ "Amazon"
+ ],
+ "marketplaces": [
+ "xsoar",
+ "marketplacev2"
+ ]
+}
\ No newline at end of file
diff --git a/Packs/Base/ReleaseNotes/1_33_32.md b/Packs/Base/ReleaseNotes/1_33_32.md
new file mode 100644
index 000000000000..30a4e223365c
--- /dev/null
+++ b/Packs/Base/ReleaseNotes/1_33_32.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### CommonServerPython
+
+- Added support for long running integrations handle proxies.
diff --git a/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py b/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py
index e3642a550c23..e44e32aff057 100644
--- a/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py
+++ b/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py
@@ -826,6 +826,42 @@ def add_http_prefix_if_missing(address=''):
return 'http://' + address
+def handle_proxy_for_long_running(proxy_param_name='proxy', checkbox_default_value=False, handle_insecure=True,
+ insecure_param_name=None):
+ """
+ Handle logic for long running integration routing traffic through the system proxy.
+ Should usually be called at the beginning of the integration, depending on proxy checkbox state.
+ Long running integrations on hosted tenants XSOAR8 and XSIAM has a dedicated env. var.: CRTX_HTTP_PROXY.
+ Fallback call to handle_proxy in cases long running integration on engine or XSOAR6
+
+ :type proxy_param_name: ``string``
+ :param proxy_param_name: name of the "use system proxy" integration parameter
+
+ :type checkbox_default_value: ``bool``
+ :param checkbox_default_value: Default value of the proxy param checkbox
+
+ :type handle_insecure: ``bool``
+ :param handle_insecure: Whether to check the insecure param and unset env variables
+
+ :type insecure_param_name: ``string``
+ :param insecure_param_name: Name of insecure param. If None will search insecure and unsecure
+
+ :return: proxies dict for the 'proxies' parameter of 'requests' functions and use_ssl boolean
+ :rtype: ``Tuple[dict, boolean]``
+ """
+ proxies = {}
+ crtx_http_proxy = os.environ.get('CRTX_HTTP_PROXY', None)
+ if crtx_http_proxy:
+ demisto.error('Setting proxies according to CRTX_HTTP_PROXY: {}'.format(crtx_http_proxy))
+ proxies = {
+ 'http': crtx_http_proxy,
+ 'https': crtx_http_proxy
+ }
+ handle_insecure = True
+ return proxies, handle_insecure
+ return handle_proxy(proxy_param_name, checkbox_default_value, handle_insecure, insecure_param_name), handle_insecure
+
+
def handle_proxy(proxy_param_name='proxy', checkbox_default_value=False, handle_insecure=True,
insecure_param_name=None):
"""
diff --git a/Packs/Base/pack_metadata.json b/Packs/Base/pack_metadata.json
index c303b18714ef..21eda318c044 100644
--- a/Packs/Base/pack_metadata.json
+++ b/Packs/Base/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Base",
"description": "The base pack for Cortex XSOAR.",
"support": "xsoar",
- "currentVersion": "1.33.31",
+ "currentVersion": "1.33.32",
"author": "Cortex XSOAR",
"serverMinVersion": "6.0.0",
"url": "https://www.paloaltonetworks.com/cortex",
diff --git a/Tests/conf.json b/Tests/conf.json
index b6e5283ce38e..fdc83215ea3d 100644
--- a/Tests/conf.json
+++ b/Tests/conf.json
@@ -5675,6 +5675,11 @@
{
"integrations": "Zimperium v2",
"playbookID": "Zimperiumv2-TestPlaybook"
+ },
+ {
+ "integrations": "AWS-SNS-Listener",
+ "playbookID": "AWS SNS Listener - Test",
+ "instance_names": "AWS-SNS-Listener"
}
],
"skipped_tests": {
@@ -5859,7 +5864,8 @@
"OpsGenieV3TestPlaybook": "Issue CIAC-7649",
"ThreatStream-Test": "Issue CRTX-96526",
"MSG-Threat-Assessment-test": "API limitation",
- "BambenekConsultingFeed_Test": "Issue CRTX-99480"
+ "BambenekConsultingFeed_Test": "Issue CRTX-99480",
+ "AWS SNS Listener - Test": "Cant validate mock msg against AWS-SNS in TBP"
},
"skipped_integrations": {
"EWS Mail Sender": "The integration is deprecated",
From ec9e097c6f4cd12b34467334683b992d8168b804 Mon Sep 17 00:00:00 2001
From: Guy Afik <53861351+GuyAfik@users.noreply.github.com>
Date: Mon, 19 Feb 2024 09:49:53 +0200
Subject: [PATCH 022/272] [Slack v3] - add support for file-mirroring from
xsoar to slack (#32611)
* logs
* mirror files from xsoar to slack
* start implementing mirror from slack to xsoar
* mirror from slack to xsoar - in progress
* use http-request for mirroring slack files to xsoar
* revert enable_dm param
* revert csp changes
* handle ssl errors
* add context
* revert mirror from slack to xsoar
* add test
* bump rn
* type ignore
* add comment handling and fix test
* update param location
* bump docker
* rn
* update docs
* fix test
* update rn
* update disclaimer
* Bump pack from version Slack to 3.4.6.
---------
Co-authored-by: Content Bot
---
Packs/Slack/Integrations/SlackV3/README.md | 47 ++++++++---------
Packs/Slack/Integrations/SlackV3/SlackV3.py | 51 ++++++++++++++++---
Packs/Slack/Integrations/SlackV3/SlackV3.yml | 10 +++-
.../Integrations/SlackV3/SlackV3_test.py | 38 ++++++++++++++
Packs/Slack/ReleaseNotes/3_4_6.md | 8 +++
Packs/Slack/pack_metadata.json | 2 +-
6 files changed, 123 insertions(+), 33 deletions(-)
create mode 100644 Packs/Slack/ReleaseNotes/3_4_6.md
diff --git a/Packs/Slack/Integrations/SlackV3/README.md b/Packs/Slack/Integrations/SlackV3/README.md
index c35bf51b0820..4157ea5de9f0 100644
--- a/Packs/Slack/Integrations/SlackV3/README.md
+++ b/Packs/Slack/Integrations/SlackV3/README.md
@@ -15,30 +15,31 @@ to learn about configuring SlackV3 using the app manifest.
2. Search for SlackV3.
3. Click **Add instance** to create and configure a new integration instance.
- | **Parameter** | **Description** | **Required** |
- |---|---|---|
- | `bot_token` | Slack API bot token. | False |
- | `user_token` | Slack API user token. | False |
- | `app_token` | Slack API app token. | False |
- | `incidentNotificationChannel` | Dedicated Slack channel to receive notifications. | False |
- | `min_severity` | Minimum incident severity by which to send messages to Slack. | False |
- | `incidentType` | Type of incidents created in Slack. | False |
- | `allow_incidents` | Allow external users to create incidents via direct messages. | False |
- | `proxy` | Use system proxy settings. | False |
- | `unsecure` | Trust any certificate (not secure). Make sure to mark this parameter if you want the SlackBlockBuilder script to send a response back to the incident context. | False |
- | `longRunning` | Long running instance. Required for investigation mirroring and direct messages. | False |
- | `bot_name` | Bot display name in Slack (Cortex XSOAR by default). | False |
- | `bot_icon` | Bot icon in Slack - Image URL (Cortex XSOAR icon by default). | False |
- | `max_limit_time` | Maximum time to wait for a rate limiting call in seconds. | False |
- | `paginated_count` | Number of objects to return in each paginated call. | False |
- | `proxy_url` | Proxy URL to use in Slack API calls. | False |
- | `filtered_tags` | Comma-separated list of tags by which to filter the messages sent from Cortex XSOAR. Only supported in Cortex XSOAR V6.1 and above. | False |
- | `permitted_notifications` | Types of notifications to send (to individual users and to the dedicated Slack channel, if specified). | False |
- | `common_channels` | For workspaces where a handful of channels are consistently being used, you may add them as a CSV in the format ChannelName:ChannelID. | False |
+ | **Parameter** | **Description** | **Required** |
+ |---|---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|---|
+ | `bot_token` | Slack API bot token. | False |
+ | `user_token` | Slack API user token. | False |
+ | `app_token` | Slack API app token. | False |
+ | `incidentNotificationChannel` | Dedicated Slack channel to receive notifications. | False |
+ | `min_severity` | Minimum incident severity by which to send messages to Slack. | False |
+ | `incidentType` | Type of incidents created in Slack. | False |
+ | `allow_incidents` | Allow external users to create incidents via direct messages. | False |
+ | `proxy` | Use system proxy settings. | False |
+ | `unsecure` | Trust any certificate (not secure). Make sure to mark this parameter if you want the SlackBlockBuilder script to send a response back to the incident context. | False |
+ | `longRunning` | Long running instance. Required for investigation mirroring and direct messages. | False |
+ | `bot_name` | Bot display name in Slack (Cortex XSOAR by default). | False |
+ | `bot_icon` | Bot icon in Slack - Image URL (Cortex XSOAR icon by default). | False |
+ | `max_limit_time` | Maximum time to wait for a rate limiting call in seconds. | False |
+ | `paginated_count` | Number of objects to return in each paginated call. | False |
+ | `proxy_url` | Proxy URL to use in Slack API calls. | False |
+ | `filtered_tags` | Comma-separated list of tags by which to filter the messages sent from Cortex XSOAR. Only supported in Cortex XSOAR V6.1 and above. | False |
+ | `permitted_notifications` | Types of notifications to send (to individual users and to the dedicated Slack channel, if specified). | False |
+ | `common_channels` | For workspaces where a handful of channels are consistently being used, you may add them as a CSV in the format ChannelName:ChannelID. | False |
| `disable_caching` | When configured, Disable Caching will prevent the integration from paginating to search for Users or Conversations. Additionally, it will prevent excess data from being stored to the integration context. If this parameter is disabled, the instance may create high memory usage. | False |
- | `mirroring` | Enable Incident Mirroring. | False |
- | `ignore_event_retries` | In some cases, events may not be processed fast enough. If you wish to attempt to retry the event, select `false`. Note that this can result in some responses being double-posted. Default is `True`. | False |
- | `extensive_logging` | Extensive Logging. This parameter will write additional data to the logs and should only be used when you are directed to by XSOAR support. | False |
+ | `mirroring` | Enable Incident Mirroring. | False |
+ | `enable_outbound_file_mirroring` | Enable Outbound File Mirroring. Whether to enable mirroring from xsoar to slack, mark it file mirroring is required in investigations. | False |
+ | `ignore_event_retries` | In some cases, events may not be processed fast enough. If you wish to attempt to retry the event, select `false`. Note that this can result in some responses being double-posted. Default is `True`. | False |
+ | `extensive_logging` | Extensive Logging. This parameter will write additional data to the logs and should only be used when you are directed to by XSOAR support. | False |
5. Click **Test** to validate the URLs, token, and connection.
diff --git a/Packs/Slack/Integrations/SlackV3/SlackV3.py b/Packs/Slack/Integrations/SlackV3/SlackV3.py
index fdfda5228f74..bd0a3318dd78 100644
--- a/Packs/Slack/Integrations/SlackV3/SlackV3.py
+++ b/Packs/Slack/Integrations/SlackV3/SlackV3.py
@@ -85,6 +85,7 @@
CACHED_INTEGRATION_CONTEXT: dict
CACHE_EXPIRY: float
MIRRORING_ENABLED: bool
+FILE_MIRRORING_ENABLED: bool
LONG_RUNNING_ENABLED: bool
DEMISTO_API_KEY: str
DEMISTO_URL: str
@@ -1767,6 +1768,31 @@ def get_conversation_by_name(conversation_name: str) -> dict:
return conversation
+def send_mirrored_file_to_slack(entry: str, message: str, original_channel: str, channel_id: str, comment: Optional[str] = None):
+ """
+ Sends a file from xsoar investigation to a mirrored slack channel
+
+ Args:
+ entry: the entry ID of the file
+ message: the message from the war-room when uploading file
+ original_channel: the channel name to upload the file
+ channel_id: the channel ID to upload the file
+ comment: a comment that was added when uploading the file
+ """
+ file_name = demisto.getFilePath(entry)["name"]
+ if FILE_MIRRORING_ENABLED:
+ demisto.debug(
+ f'file {file_name} has been uploaded to a mirrored incident, '
+ f'uploading the file to slack channel {original_channel}'
+ )
+ if comment:
+ # if a comment was added when uploading the file, add it to the message
+ message = f'{message}\nComment: {comment}'
+ slack_send_file(original_channel, channel_id, entry, message)
+ else:
+ demisto.debug(f'file {file_name} will not be mirrored because file mirroring is not enabled')
+
+
def slack_send():
"""
Sends a message to slack
@@ -1807,6 +1833,16 @@ def slack_send():
if tags and not any(elem in entry_tags for elem in tags):
return
+ if entry:
+ send_mirrored_file_to_slack(
+ entry,
+ message=message,
+ original_channel=original_channel,
+ channel_id=channel_id,
+ comment=entry_object.get("contents")
+ )
+ return
+
if (to and group) or (to and original_channel) or (to and original_channel and group):
return_error('Only one destination can be provided.')
@@ -1910,17 +1946,17 @@ def save_entitlement(entitlement, thread, reply, expiry, default_response):
set_to_integration_context_with_retries({'questions': questions}, OBJECTS_TO_KEYS, SYNC_CONTEXT)
-def slack_send_file():
+def slack_send_file(_channel: str | None = None, _channel_id: str = '', _entry_id: str | None = None, _comment: str = ""):
"""
Sends a file to slack
"""
to = demisto.args().get('to')
- channel = demisto.args().get('channel')
- channel_id = demisto.args().get('channel_id', '')
+ channel = _channel or demisto.args().get('channel')
+ channel_id = _channel_id or demisto.args().get('channel_id', '')
group = demisto.args().get('group')
- entry_id = demisto.args().get('file')
+ entry_id = _entry_id or demisto.args().get('file')
thread_id = demisto.args().get('threadID')
- comment = demisto.args().get('comment', '')
+ comment = _comment or demisto.args().get('comment', '')
if not (to or channel or group):
mirror = find_mirror_by_investigation()
@@ -2747,7 +2783,7 @@ def init_globals(command_name: str = ''):
"""
global BOT_TOKEN, PROXY_URL, PROXIES, DEDICATED_CHANNEL, CLIENT, USER_CLIENT, \
- CACHED_INTEGRATION_CONTEXT, MIRRORING_ENABLED, USER_TOKEN
+ CACHED_INTEGRATION_CONTEXT, MIRRORING_ENABLED, FILE_MIRRORING_ENABLED, USER_TOKEN
global SEVERITY_THRESHOLD, ALLOW_INCIDENTS, INCIDENT_TYPE, VERIFY_CERT, ENABLE_DM, BOT_ID, CACHE_EXPIRY
global BOT_NAME, BOT_ICON_URL, MAX_LIMIT_TIME, PAGINATED_COUNT, SSL_CONTEXT, APP_TOKEN, ASYNC_CLIENT
global DEFAULT_PERMITTED_NOTIFICATION_TYPES, CUSTOM_PERMITTED_NOTIFICATION_TYPES, PERMITTED_NOTIFICATION_TYPES
@@ -2784,6 +2820,7 @@ def init_globals(command_name: str = ''):
CUSTOM_PERMITTED_NOTIFICATION_TYPES = demisto.params().get('permitted_notifications', [])
PERMITTED_NOTIFICATION_TYPES = DEFAULT_PERMITTED_NOTIFICATION_TYPES + CUSTOM_PERMITTED_NOTIFICATION_TYPES
MIRRORING_ENABLED = demisto.params().get('mirroring', True)
+ FILE_MIRRORING_ENABLED = demisto.params().get('enable_outbound_file_mirroring', False)
LONG_RUNNING_ENABLED = demisto.params().get('longRunning', True)
DEMISTO_API_KEY = demisto.params().get('demisto_api_key', {}).get('password', '')
demisto_urls = demisto.demistoUrls()
@@ -2949,7 +2986,7 @@ def main() -> None:
if EXTENSIVE_LOGGING:
os.environ['PYTHONASYNCIODEBUG'] = "1"
support_multithreading()
- command_func()
+ command_func() # type: ignore
except Exception as e:
demisto.debug(e)
return_error(str(e))
diff --git a/Packs/Slack/Integrations/SlackV3/SlackV3.yml b/Packs/Slack/Integrations/SlackV3/SlackV3.yml
index c548bcba78c6..409d2532aaca 100644
--- a/Packs/Slack/Integrations/SlackV3/SlackV3.yml
+++ b/Packs/Slack/Integrations/SlackV3/SlackV3.yml
@@ -103,8 +103,14 @@ configuration:
display: Enable Incident Mirroring
name: mirroring
type: 8
- section: Collect
+ section: Connect
+ required: false
+- display: Enable Outbound File Mirroring
+ name: enable_outbound_file_mirroring
+ type: 8
+ section: Connect
required: false
+ additionalinfo: Whether to enable mirroring only from xsoar to slack, mark it if file mirroring is required in investigations.
- defaultvalue: 'true'
display: Long running instance. Required for investigation mirroring and direct messages.
name: longRunning
@@ -492,7 +498,7 @@ script:
description: Set this argument to specify how many results to return.
description: Retrieves replies to specific messages, regardless of whether it's from a public or private channel, direct message, or otherwise.
name: slack-get-conversation-replies
- dockerimage: demisto/slackv3:1.0.0.86601
+ dockerimage: demisto/slackv3:1.0.0.87650
longRunning: true
runonce: false
script: '-'
diff --git a/Packs/Slack/Integrations/SlackV3/SlackV3_test.py b/Packs/Slack/Integrations/SlackV3/SlackV3_test.py
index bc8cbce14047..5554b9457304 100644
--- a/Packs/Slack/Integrations/SlackV3/SlackV3_test.py
+++ b/Packs/Slack/Integrations/SlackV3/SlackV3_test.py
@@ -2835,6 +2835,44 @@ def api_call(method: str, http_verb: str = 'POST', file: str = None, params=None
assert demisto.getIntegrationContext()['questions'] == js.dumps(questions)
+def test_slack_send_with_mirrored_file(mocker):
+ """
+ Given:
+ - mirror entry which is basically a file
+
+ When:
+ - running send-notification triggered from mirroring
+
+ Then:
+ - Validate that the file is sent successfully
+ """
+ import SlackV3
+
+ mocker.patch.object(demisto, 'params', return_value={'enable_outbound_file_mirroring': True})
+
+ SlackV3.init_globals()
+
+ mocker.patch.object(
+ demisto,
+ 'args',
+ return_value={
+ "message": "test",
+ "channel_id": "1234",
+ "channel": "channel",
+ "entry": "1234",
+ "messageType": SlackV3.MIRROR_TYPE,
+ "entryObject": {}
+ }
+ )
+ slack_send_request = mocker.patch.object(SlackV3, 'slack_send_request', return_value='file-sent')
+ demisto_results = mocker.patch.object(demisto, 'results')
+
+ SlackV3.slack_send()
+ assert slack_send_request.call_args_list[0].kwargs["file_dict"]
+ assert slack_send_request.call_args_list[0].kwargs["channel_id"] == "1234"
+ assert demisto_results.call_args_list[0][0][0] == 'File sent to Slack successfully.'
+
+
def test_send_request_with_entitlement_blocks(mocker):
import SlackV3
diff --git a/Packs/Slack/ReleaseNotes/3_4_6.md b/Packs/Slack/ReleaseNotes/3_4_6.md
new file mode 100644
index 000000000000..747b2021976d
--- /dev/null
+++ b/Packs/Slack/ReleaseNotes/3_4_6.md
@@ -0,0 +1,8 @@
+
+#### Integrations
+
+##### Slack v3
+
+- Added support for mirroring files from xsoar to slack.
+- Added the **Enable Outbound File Mirroring** integration parameter to allow file mirroring from xsoar to slack. The parameter is unchecked by default, disabling file mirroring.
+- Updated the Docker image to: *demisto/slackv3:1.0.0.87650*.
diff --git a/Packs/Slack/pack_metadata.json b/Packs/Slack/pack_metadata.json
index ec314bf3d144..29638ec27709 100644
--- a/Packs/Slack/pack_metadata.json
+++ b/Packs/Slack/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Slack",
"description": "Interact with Slack API - collect logs, send messages and notifications to your Slack team.",
"support": "xsoar",
- "currentVersion": "3.4.5",
+ "currentVersion": "3.4.6",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From c7e7a80ad9b5fb489bcc01fc95deca98778c12b5 Mon Sep 17 00:00:00 2001
From: JudithB <132264628+jbabazadeh@users.noreply.github.com>
Date: Mon, 19 Feb 2024 13:23:01 +0200
Subject: [PATCH 023/272] Qradar reference sets list issue (#32779)
* fix qradar-reference-sets-list to able use ref_name with filter and range
* Bump pack from version QRadar to 2.4.49.
* filter description
* Update QRadar_v3.py
* RN
* RN
---------
Co-authored-by: Content Bot
---
Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.py | 4 ++--
Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.yml | 4 +++-
Packs/QRadar/ReleaseNotes/2_4_50.md | 7 +++++++
Packs/QRadar/pack_metadata.json | 2 +-
4 files changed, 13 insertions(+), 4 deletions(-)
create mode 100644 Packs/QRadar/ReleaseNotes/2_4_50.md
diff --git a/Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.py b/Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.py
index d63a4c96ac07..df63a9618081 100644
--- a/Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.py
+++ b/Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.py
@@ -587,8 +587,8 @@ def search_results_get(self, search_id: str, range_: Optional[str] = None):
def reference_sets_list(self, range_: Optional[str] = None, ref_name: Optional[str] = None,
filter_: Optional[str] = None, fields: Optional[str] = None):
name_suffix = f'/{parse.quote(ref_name, safe="")}' if ref_name else ''
- params = assign_params(fields=fields) if ref_name else assign_params(filter=filter_, fields=fields)
- additional_headers = {'Range': range_} if not ref_name else None
+ params = assign_params(filter=filter_, fields=fields)
+ additional_headers = {'Range': range_}
return self.http_request(
method='GET',
url_suffix=f'/reference_data/sets{name_suffix}',
diff --git a/Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.yml b/Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.yml
index ea8e6120b9f8..5e7727e755ae 100644
--- a/Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.yml
+++ b/Packs/QRadar/Integrations/QRadar_v3/QRadar_v3.yml
@@ -927,7 +927,9 @@ script:
description: 'Range of results to return (e.g.: 0-20, 3-5, 3-3).'
defaultValue: 0-49
- name: filter
- description: 'Query by which to filter reference sets, e.g., "timeout_type=FIRST_SEEN". For reference, see: https://www.ibm.com/support/knowledgecenter/SS42VS_SHR/com.ibm.qradarapi.doc/c_rest_api_filtering.html'
+ description: |-
+ Query by which to filter reference sets, e.g., "timeout_type=FIRST_SEEN". For reference, see: https://www.ibm.com/support/knowledgecenter/SS42VS_SHR/com.ibm.qradarapi.doc/c_rest_api_filtering.html.
+ when using both ref_name and filter arguments, the filter should be from the data values of the specified reference set, e.g. "value='1.1.1.1'".
- name: fields
description: 'Comma-separated list of fields to retrieve in the response. Fields that are not explicitly named are excluded. E.g., "name,timeout_type". Specify subfields in brackets and multiple fields in the same object separated by commas. For a full list of available fields, see: https://ibmsecuritydocs.github.io/qradar_api_14.0/14.0--reference_data-sets-GET.html.'
isArray: true
diff --git a/Packs/QRadar/ReleaseNotes/2_4_50.md b/Packs/QRadar/ReleaseNotes/2_4_50.md
new file mode 100644
index 000000000000..eb447eecfb3b
--- /dev/null
+++ b/Packs/QRadar/ReleaseNotes/2_4_50.md
@@ -0,0 +1,7 @@
+
+#### Integrations
+
+##### IBM QRadar v3
+
+- Fixed an issue in **qradar-reference-sets-list** when using the ref_name argument with filter or range arguments didn't effect on the results as expected.
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
\ No newline at end of file
diff --git a/Packs/QRadar/pack_metadata.json b/Packs/QRadar/pack_metadata.json
index 34f8c663bd2c..e5c36b3a42ca 100644
--- a/Packs/QRadar/pack_metadata.json
+++ b/Packs/QRadar/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "IBM QRadar",
"description": "Fetch offenses as incidents and search QRadar",
"support": "xsoar",
- "currentVersion": "2.4.49",
+ "currentVersion": "2.4.50",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From e1bdd8de4adf35b9948038cabd3d7c45db9f7608 Mon Sep 17 00:00:00 2001
From: Yaakov Praisler <59408745+yaakovpraisler@users.noreply.github.com>
Date: Mon, 19 Feb 2024 16:04:29 +0200
Subject: [PATCH 024/272] [XSUP-33662] Fix Okta Auth0 test-module (#32992)
* fixed XSUP-33662
* docker
---
.../OktaAuth0EventCollector/OktaAuth0EventCollector.py | 1 -
.../OktaAuth0EventCollector/OktaAuth0EventCollector.yml | 2 +-
Packs/OktaAuth0/ReleaseNotes/1_0_2.md | 7 +++++++
Packs/OktaAuth0/pack_metadata.json | 2 +-
4 files changed, 9 insertions(+), 3 deletions(-)
create mode 100644 Packs/OktaAuth0/ReleaseNotes/1_0_2.md
diff --git a/Packs/OktaAuth0/Integrations/OktaAuth0EventCollector/OktaAuth0EventCollector.py b/Packs/OktaAuth0/Integrations/OktaAuth0EventCollector/OktaAuth0EventCollector.py
index 4be960410c6a..1f8730233122 100644
--- a/Packs/OktaAuth0/Integrations/OktaAuth0EventCollector/OktaAuth0EventCollector.py
+++ b/Packs/OktaAuth0/Integrations/OktaAuth0EventCollector/OktaAuth0EventCollector.py
@@ -174,7 +174,6 @@ def test_module_command(client: Client, params: dict, last_run: dict) -> str:
Returns:
(str) 'ok' if success.
"""
- params = prepare_query_params(params)
fetch_events_command(client, params, last_run)
return 'ok'
diff --git a/Packs/OktaAuth0/Integrations/OktaAuth0EventCollector/OktaAuth0EventCollector.yml b/Packs/OktaAuth0/Integrations/OktaAuth0EventCollector/OktaAuth0EventCollector.yml
index 34cd8fd3152f..9fbfaf93892f 100644
--- a/Packs/OktaAuth0/Integrations/OktaAuth0EventCollector/OktaAuth0EventCollector.yml
+++ b/Packs/OktaAuth0/Integrations/OktaAuth0EventCollector/OktaAuth0EventCollector.yml
@@ -61,7 +61,7 @@ script:
script: '-'
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
marketplaces:
- marketplacev2
fromversion: 8.2.0
diff --git a/Packs/OktaAuth0/ReleaseNotes/1_0_2.md b/Packs/OktaAuth0/ReleaseNotes/1_0_2.md
new file mode 100644
index 000000000000..9ab4f27c8b27
--- /dev/null
+++ b/Packs/OktaAuth0/ReleaseNotes/1_0_2.md
@@ -0,0 +1,7 @@
+
+#### Integrations
+
+##### Okta Auth0 Event Collector
+
+- Fixed an issue where the *Test button* failed to generate correct query params for the test.
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/OktaAuth0/pack_metadata.json b/Packs/OktaAuth0/pack_metadata.json
index d677c9ef1b2d..a8ea82975386 100644
--- a/Packs/OktaAuth0/pack_metadata.json
+++ b/Packs/OktaAuth0/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Okta Auth0",
"description": "Identity platform to manage access to your applications.",
"support": "xsoar",
- "currentVersion": "1.0.1",
+ "currentVersion": "1.0.2",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 4385426ac38c4d4f83b52379b0ef6553c7e4ebab Mon Sep 17 00:00:00 2001
From: Arad Carmi <62752352+AradCarmi@users.noreply.github.com>
Date: Mon, 19 Feb 2024 16:53:23 +0200
Subject: [PATCH 025/272] XSIAM Compliance Dashboard&Report Update (#31947)
* test commit
* Update RN
* Ignoring failing RN validation
* Updated to verison 2.0.0
* Changed ReadME
* Updated RN
* Updated RN
* Updated Hipaa RN testing
* Updated RN
* Updated README
* Updated pack ignore
---------
Co-authored-by: cweltPA <129675344+cweltPA@users.noreply.github.com>
---
Packs/XSIAMCompliance_HIPAA/.pack-ignore | 11 ++++++++++-
Packs/XSIAMCompliance_HIPAA/README.md | 6 ++----
Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_1.md | 7 +++++--
Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_2.md | 8 +++++---
Packs/XSIAMCompliance_HIPAA/ReleaseNotes/2_0_0.md | 12 ++++++++++++
Packs/XSIAMCompliance_HIPAA/pack_metadata.json | 10 ++++------
Packs/XSIAMCompliance_NIST_800_171/.pack-ignore | 11 ++++++++++-
Packs/XSIAMCompliance_NIST_800_171/README.md | 4 +---
.../ReleaseNotes/1_0_1.md | 5 +++--
.../ReleaseNotes/1_0_2.md | 7 ++++---
.../ReleaseNotes/2_0_0.md | 12 ++++++++++++
.../XSIAMCompliance_NIST_800_171/pack_metadata.json | 10 ++++------
Packs/XSIAMCompliance_NIST_800_53/.pack-ignore | 11 ++++++++++-
Packs/XSIAMCompliance_NIST_800_53/README.md | 4 +---
.../ReleaseNotes/1_0_1.md | 5 +++--
.../ReleaseNotes/1_0_2.md | 5 +++--
.../ReleaseNotes/2_0_0.md | 12 ++++++++++++
Packs/XSIAMCompliance_NIST_800_53/pack_metadata.json | 10 ++++------
Packs/XSIAMCompliance_NIST_CSF/.pack-ignore | 11 ++++++++++-
Packs/XSIAMCompliance_NIST_CSF/README.md | 3 +--
Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_1.md | 5 +++--
Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_2.md | 7 ++++---
Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/2_0_0.md | 12 ++++++++++++
Packs/XSIAMCompliance_NIST_CSF/pack_metadata.json | 10 ++++------
Packs/XSIAMCompliance_PCI_DSS/.pack-ignore | 11 ++++++++++-
Packs/XSIAMCompliance_PCI_DSS/README.md | 3 +--
Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_1.md | 5 +++--
Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_2.md | 7 ++++---
Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/2_0_0.md | 12 ++++++++++++
Packs/XSIAMCompliance_PCI_DSS/pack_metadata.json | 10 ++++------
Packs/XSIAMCompliance_SOX/.pack-ignore | 7 +++++++
Packs/XSIAMCompliance_SOX/README.md | 3 +--
Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_1.md | 5 +++--
Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_2.md | 7 ++++---
Packs/XSIAMCompliance_SOX/ReleaseNotes/2_0_0.md | 12 ++++++++++++
Packs/XSIAMCompliance_SOX/pack_metadata.json | 10 ++++------
36 files changed, 204 insertions(+), 86 deletions(-)
create mode 100644 Packs/XSIAMCompliance_HIPAA/ReleaseNotes/2_0_0.md
create mode 100644 Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/2_0_0.md
create mode 100644 Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/2_0_0.md
create mode 100644 Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/2_0_0.md
create mode 100644 Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/2_0_0.md
create mode 100644 Packs/XSIAMCompliance_SOX/ReleaseNotes/2_0_0.md
diff --git a/Packs/XSIAMCompliance_HIPAA/.pack-ignore b/Packs/XSIAMCompliance_HIPAA/.pack-ignore
index 5ecb5bcafff9..3163d5595c00 100644
--- a/Packs/XSIAMCompliance_HIPAA/.pack-ignore
+++ b/Packs/XSIAMCompliance_HIPAA/.pack-ignore
@@ -1,2 +1,11 @@
[known_words]
-HIPAA
\ No newline at end of file
+HIPAA
+
+[file:1_0_1.md]
+ignore=RN113,RN114
+
+[file:1_0_2.md]
+ignore=RN113,RN114
+
+[file:2_0_0.md]
+ignore=RN113,RN114
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_HIPAA/README.md b/Packs/XSIAMCompliance_HIPAA/README.md
index c00a2469aef4..b503455450f4 100644
--- a/Packs/XSIAMCompliance_HIPAA/README.md
+++ b/Packs/XSIAMCompliance_HIPAA/README.md
@@ -1,6 +1,5 @@
-## **Generate Compliance Dashboard and Reports**
-The HIPAA compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits. The dashboard and report aggregate and reference all data mapped to the Cortex Data Model (XDM).
-
+## **Generate Compliance Dashboards and Reports**
+The HIPAA compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits.
@@ -8,5 +7,4 @@ The HIPAA compliance pack provides a comprehensive dashboard and report template
## **What does this pack do?**
- Install dashboard and report templates for the HIPAA regulations.
-- Reference data that has been mapped to the Cortex Data Model (XDM).
- Produce regulation evidence for audits.
diff --git a/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_1.md b/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_1.md
index 04117346a72b..3252eacb4779 100644
--- a/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_1.md
+++ b/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_1.md
@@ -1,4 +1,7 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### HIPAA Compliance Dashboard
+
- Note: The pack moved to closed source.
+
+
diff --git a/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_2.md b/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_2.md
index 2ad2a755b44c..314e63718ee9 100644
--- a/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_2.md
+++ b/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/1_0_2.md
@@ -1,5 +1,7 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### HIPAA Compliance Dashboard
+
- Added support for lazy loading the widgets.
-- Added support for caching the widgets data.
\ No newline at end of file
+- Added support for caching the widgets data.
+
diff --git a/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/2_0_0.md b/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/2_0_0.md
new file mode 100644
index 000000000000..d08b2b494fef
--- /dev/null
+++ b/Packs/XSIAMCompliance_HIPAA/ReleaseNotes/2_0_0.md
@@ -0,0 +1,12 @@
+#### XSIAM Dashboards
+
+##### HIPAA Compliance Dashboard
+
+- Improved layout of the dashboard.
+- Updated XQL queries to improve dashboard load times.
+
+#### XSIAM Reports
+
+##### HIPAA Compliance Report
+
+- Updated XQL queries to improve report load time.
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_HIPAA/pack_metadata.json b/Packs/XSIAMCompliance_HIPAA/pack_metadata.json
index 4bfa3183afd9..2b8e37615c87 100644
--- a/Packs/XSIAMCompliance_HIPAA/pack_metadata.json
+++ b/Packs/XSIAMCompliance_HIPAA/pack_metadata.json
@@ -2,14 +2,13 @@
"name": "HIPAA Compliance",
"description": "Ensure your organization is following HIPAA guidelines with the relevant dashboard and report evidence.",
"support": "xsoar",
- "currentVersion": "1.0.2",
+ "currentVersion": "2.0.0",
"author": "Cortex XSIAM",
"url": "https://www.paloaltonetworks.com/cortex",
"categories": [
"Analytics & SIEM"
],
- "tags": [
- ],
+ "tags": [],
"created": "2023-03-20T13:16:53Z",
"useCases": [
"Compliance"
@@ -21,7 +20,6 @@
"compliance"
],
"marketplaces": [
- "marketplacev2"
+ "marketplacev2"
]
-
-}
+}
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_800_171/.pack-ignore b/Packs/XSIAMCompliance_NIST_800_171/.pack-ignore
index 480c57d975e5..3041bee4654d 100644
--- a/Packs/XSIAMCompliance_NIST_800_171/.pack-ignore
+++ b/Packs/XSIAMCompliance_NIST_800_171/.pack-ignore
@@ -1,2 +1,11 @@
[known_words]
-NIST
\ No newline at end of file
+NIST
+
+[file:1_0_1.md]
+ignore=RN113,RN114
+
+[file:1_0_2.md]
+ignore=RN113,RN114
+
+[file:2_0_0.md]
+ignore=RN113,RN114
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_800_171/README.md b/Packs/XSIAMCompliance_NIST_800_171/README.md
index daf2d755ea2f..e3d4c2a4390a 100644
--- a/Packs/XSIAMCompliance_NIST_800_171/README.md
+++ b/Packs/XSIAMCompliance_NIST_800_171/README.md
@@ -1,10 +1,8 @@
## **Generate Compliance Dashboards and Reports**
-The NIST 800-171 compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits. The dashboard and report aggregate and reference all data mapped to the Cortex Data Model (XDM).
-
+The NIST 800-171 compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits.
**Note:** This pack is currently offered as a free beta of the Compliance module for a limited time. In the future, this module will be sold separately on top of XSIAM.
## **What does this pack do?**
- Install dashboard and report templates for the NIST 800-171 regulations.
-- Reference data that has been mapped to the Cortex Data Model (XDM).
- Produce regulation evidence for audits.
diff --git a/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/1_0_1.md b/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/1_0_1.md
index 04117346a72b..75a5ad905e85 100644
--- a/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/1_0_1.md
+++ b/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/1_0_1.md
@@ -1,4 +1,5 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### NIST 800-171 Compliance Dashboard
+
- Note: The pack moved to closed source.
diff --git a/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/1_0_2.md b/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/1_0_2.md
index 2ad2a755b44c..acae386c0d46 100644
--- a/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/1_0_2.md
+++ b/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/1_0_2.md
@@ -1,5 +1,6 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### NIST 800-171 Compliance Dashboard
+
- Added support for lazy loading the widgets.
-- Added support for caching the widgets data.
\ No newline at end of file
+- Added support for caching the widgets data.
diff --git a/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/2_0_0.md b/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/2_0_0.md
new file mode 100644
index 000000000000..89e891ca8e31
--- /dev/null
+++ b/Packs/XSIAMCompliance_NIST_800_171/ReleaseNotes/2_0_0.md
@@ -0,0 +1,12 @@
+#### XSIAM Dashboards
+
+##### NIST 800-171 Compliance Dashboard
+
+- Improved layout of the dashboard.
+- Updated XQL queries to improve dashboard load times.
+
+#### XSIAM Reports
+
+##### NIST 800-171 Compliance Report
+
+- Updated XQL queries to improve report load time.
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_800_171/pack_metadata.json b/Packs/XSIAMCompliance_NIST_800_171/pack_metadata.json
index 6908241d1568..4a7b6b6a5e98 100644
--- a/Packs/XSIAMCompliance_NIST_800_171/pack_metadata.json
+++ b/Packs/XSIAMCompliance_NIST_800_171/pack_metadata.json
@@ -2,14 +2,13 @@
"name": "NIST 800-171 Compliance",
"description": "Ensure your organization is following NIST 800-171 guidelines with the relevant dashboard and report evidence.",
"support": "xsoar",
- "currentVersion": "1.0.2",
+ "currentVersion": "2.0.0",
"author": "Cortex XSIAM",
"url": "https://www.paloaltonetworks.com/cortex",
"categories": [
"Analytics & SIEM"
],
- "tags": [
- ],
+ "tags": [],
"created": "2023-03-20T13:16:53Z",
"useCases": [
"Compliance"
@@ -21,7 +20,6 @@
"compliance"
],
"marketplaces": [
- "marketplacev2"
+ "marketplacev2"
]
-
-}
+}
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_800_53/.pack-ignore b/Packs/XSIAMCompliance_NIST_800_53/.pack-ignore
index 480c57d975e5..3041bee4654d 100644
--- a/Packs/XSIAMCompliance_NIST_800_53/.pack-ignore
+++ b/Packs/XSIAMCompliance_NIST_800_53/.pack-ignore
@@ -1,2 +1,11 @@
[known_words]
-NIST
\ No newline at end of file
+NIST
+
+[file:1_0_1.md]
+ignore=RN113,RN114
+
+[file:1_0_2.md]
+ignore=RN113,RN114
+
+[file:2_0_0.md]
+ignore=RN113,RN114
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_800_53/README.md b/Packs/XSIAMCompliance_NIST_800_53/README.md
index fa4208533e91..68db1e19eebc 100644
--- a/Packs/XSIAMCompliance_NIST_800_53/README.md
+++ b/Packs/XSIAMCompliance_NIST_800_53/README.md
@@ -1,11 +1,9 @@
## **Generate Compliance Dashboards and Reports**
-The NIST 800-53 compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits. The dashboard and report aggregate and reference all data mapped to the Cortex Data Model (XDM).
-
+The NIST 800-53 compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits.
**Note:** This pack is currently offered as a free beta of the Compliance module for a limited time. In the future, this module will be sold separately on top of XSIAM.
## **What does this pack do?**
- Install dashboard and report templates for the NIST 800-53 regulations.
-- Reference data that has been mapped to the Cortex Data Model (XDM).
- Produce regulation evidence for audits.
diff --git a/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/1_0_1.md b/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/1_0_1.md
index 04117346a72b..f6065039825d 100644
--- a/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/1_0_1.md
+++ b/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/1_0_1.md
@@ -1,4 +1,5 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### NIST 800-53 Compliance Dashboard
+
- Note: The pack moved to closed source.
diff --git a/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/1_0_2.md b/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/1_0_2.md
index 2ad2a755b44c..657a70f394a6 100644
--- a/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/1_0_2.md
+++ b/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/1_0_2.md
@@ -1,5 +1,6 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### NIST 800-53 Compliance Dashboard
+
- Added support for lazy loading the widgets.
- Added support for caching the widgets data.
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/2_0_0.md b/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/2_0_0.md
new file mode 100644
index 000000000000..99c4da913928
--- /dev/null
+++ b/Packs/XSIAMCompliance_NIST_800_53/ReleaseNotes/2_0_0.md
@@ -0,0 +1,12 @@
+#### XSIAM Dashboards
+
+##### NIST 800-53 Compliance Dashboard
+
+- Improved layout of the dashboard.
+- Updated XQL queries to improve dashboard load times.
+
+#### XSIAM Reports
+
+##### NIST 800-53 Compliance Report
+
+- Updated XQL queries to improve report load time.
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_800_53/pack_metadata.json b/Packs/XSIAMCompliance_NIST_800_53/pack_metadata.json
index ce810eb95c78..a7c01f82d5a5 100644
--- a/Packs/XSIAMCompliance_NIST_800_53/pack_metadata.json
+++ b/Packs/XSIAMCompliance_NIST_800_53/pack_metadata.json
@@ -2,14 +2,13 @@
"name": "NIST 800-53 Compliance",
"description": "Ensure your organization is following NIST 800-53 guidelines with the relevant dashboard and report evidence.",
"support": "xsoar",
- "currentVersion": "1.0.2",
+ "currentVersion": "2.0.0",
"author": "Cortex XSIAM",
"url": "https://www.paloaltonetworks.com/cortex",
"categories": [
"Analytics & SIEM"
],
- "tags": [
- ],
+ "tags": [],
"created": "2023-03-20T13:16:53Z",
"useCases": [
"Compliance"
@@ -21,7 +20,6 @@
"compliance"
],
"marketplaces": [
- "marketplacev2"
+ "marketplacev2"
]
-
-}
+}
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_CSF/.pack-ignore b/Packs/XSIAMCompliance_NIST_CSF/.pack-ignore
index 5497e233e5f4..20db28a97d1d 100644
--- a/Packs/XSIAMCompliance_NIST_CSF/.pack-ignore
+++ b/Packs/XSIAMCompliance_NIST_CSF/.pack-ignore
@@ -1,3 +1,12 @@
[known_words]
NIST
-CSF
\ No newline at end of file
+CSF
+
+[file:1_0_1.md]
+ignore=RN113,RN114
+
+[file:1_0_2.md]
+ignore=RN113,RN114
+
+[file:2_0_0.md]
+ignore=RN113,RN114
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_CSF/README.md b/Packs/XSIAMCompliance_NIST_CSF/README.md
index 4d20a8dddd42..4013d1c3f616 100644
--- a/Packs/XSIAMCompliance_NIST_CSF/README.md
+++ b/Packs/XSIAMCompliance_NIST_CSF/README.md
@@ -1,10 +1,9 @@
## **Generate Compliance Dashboards and Reports**
-The NIST CSF compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits. The dashboard and report aggregate and reference all data mapped to the Cortex Data Model (XDM).
+The NIST CSF compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits.
**Note:** This pack is currently offered as a free beta of the Compliance module for a limited time. In the future, this module will be sold separately on top of XSIAM.
## **What does this pack do?**
- Install dashboard and report templates for the NIST CSF regulations.
-- Reference data that has been mapped to the Cortex Data Model (XDM).
- Produce regulation evidence for audits.
diff --git a/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_1.md b/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_1.md
index 04117346a72b..325e2955c82b 100644
--- a/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_1.md
+++ b/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_1.md
@@ -1,4 +1,5 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### NIST CSF Compliance Dashboard
+
- Note: The pack moved to closed source.
diff --git a/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_2.md b/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_2.md
index 2ad2a755b44c..39054fd4f057 100644
--- a/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_2.md
+++ b/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/1_0_2.md
@@ -1,5 +1,6 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### NIST CSF Compliance Dashboard
+
- Added support for lazy loading the widgets.
-- Added support for caching the widgets data.
\ No newline at end of file
+- Added support for caching the widgets data.
diff --git a/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/2_0_0.md b/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/2_0_0.md
new file mode 100644
index 000000000000..c54f9b199b3f
--- /dev/null
+++ b/Packs/XSIAMCompliance_NIST_CSF/ReleaseNotes/2_0_0.md
@@ -0,0 +1,12 @@
+#### XSIAM Dashboards
+
+##### NIST CSF Compliance Dashboard
+
+- Improved layout of the dashboard.
+- Updated XQL queries to improve dashboard load times.
+
+#### XSIAM Reports
+
+##### NIST CSF Compliance Report
+
+- Updated XQL queries to improve report load time.
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_NIST_CSF/pack_metadata.json b/Packs/XSIAMCompliance_NIST_CSF/pack_metadata.json
index c862ffd688c4..daf5bbf5b653 100644
--- a/Packs/XSIAMCompliance_NIST_CSF/pack_metadata.json
+++ b/Packs/XSIAMCompliance_NIST_CSF/pack_metadata.json
@@ -2,14 +2,13 @@
"name": "NIST CSF Compliance",
"description": "Ensure your organization is following NIST CSF guidelines with the relevant dashboard and report evidence.",
"support": "xsoar",
- "currentVersion": "1.0.2",
+ "currentVersion": "2.0.0",
"author": "Cortex XSIAM",
"url": "https://www.paloaltonetworks.com/cortex",
"categories": [
"Analytics & SIEM"
],
- "tags": [
- ],
+ "tags": [],
"created": "2023-03-20T13:16:53Z",
"useCases": [
"Compliance"
@@ -21,7 +20,6 @@
"compliance"
],
"marketplaces": [
- "marketplacev2"
+ "marketplacev2"
]
-
-}
+}
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_PCI_DSS/.pack-ignore b/Packs/XSIAMCompliance_PCI_DSS/.pack-ignore
index 6a492984e0af..93ac88c1c0c6 100644
--- a/Packs/XSIAMCompliance_PCI_DSS/.pack-ignore
+++ b/Packs/XSIAMCompliance_PCI_DSS/.pack-ignore
@@ -1,3 +1,12 @@
[known_words]
PCI
-DSS
\ No newline at end of file
+DSS
+
+[file:1_0_1.md]
+ignore=RN113,RN114
+
+[file:1_0_2.md]
+ignore=RN113,RN114
+
+[file:2_0_0.md]
+ignore=RN113,RN114
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_PCI_DSS/README.md b/Packs/XSIAMCompliance_PCI_DSS/README.md
index 0e28a706b7d1..e20a9530ac54 100644
--- a/Packs/XSIAMCompliance_PCI_DSS/README.md
+++ b/Packs/XSIAMCompliance_PCI_DSS/README.md
@@ -1,9 +1,8 @@
## **Generate Compliance Dashboards and Reports**
-The PCI DSS compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits. The dashboard and report aggregate and reference all data mapped to the Cortex Data Model (XDM).
+The PCI DSS compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits.
**Note:** This pack is currently offered as a free beta of the Compliance module for a limited time. In the future, this module will be sold separately on top of XSIAM.
## **What does this pack do?**
- Install dashboard and report templates for the PCI DSS regulations.
-- Reference data that has been mapped to the Cortex Data Model (XDM).
- Produce regulation evidence for audits.
diff --git a/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_1.md b/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_1.md
index 04117346a72b..ef990bfc6360 100644
--- a/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_1.md
+++ b/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_1.md
@@ -1,4 +1,5 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### PCI DSS Compliance Dashboard
+
- Note: The pack moved to closed source.
diff --git a/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_2.md b/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_2.md
index 2ad2a755b44c..b86b8fb54083 100644
--- a/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_2.md
+++ b/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/1_0_2.md
@@ -1,5 +1,6 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### PCI DSS Compliance Dashboard
+
- Added support for lazy loading the widgets.
-- Added support for caching the widgets data.
\ No newline at end of file
+- Added support for caching the widgets data.
diff --git a/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/2_0_0.md b/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/2_0_0.md
new file mode 100644
index 000000000000..a16c9334e3a2
--- /dev/null
+++ b/Packs/XSIAMCompliance_PCI_DSS/ReleaseNotes/2_0_0.md
@@ -0,0 +1,12 @@
+#### XSIAM Dashboards
+
+##### PCI DSS Compliance Dashboard
+
+- Improved layout of the dashboard.
+- Updated XQL queries to improve dashboard load times.
+
+#### XSIAM Reports
+
+##### PCI DSS Compliance Report
+
+- Updated XQL queries to improve report load time.
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_PCI_DSS/pack_metadata.json b/Packs/XSIAMCompliance_PCI_DSS/pack_metadata.json
index 2728e8f6bbc0..74388402b982 100644
--- a/Packs/XSIAMCompliance_PCI_DSS/pack_metadata.json
+++ b/Packs/XSIAMCompliance_PCI_DSS/pack_metadata.json
@@ -2,14 +2,13 @@
"name": "PCI DSS Compliance",
"description": "Ensure your organization is following PCI DSS guidelines with the relevant dashboard and report evidence.",
"support": "xsoar",
- "currentVersion": "1.0.2",
+ "currentVersion": "2.0.0",
"author": "Cortex XSIAM",
"url": "https://www.paloaltonetworks.com/cortex",
"categories": [
"Analytics & SIEM"
],
- "tags": [
- ],
+ "tags": [],
"created": "2023-03-20T13:16:53Z",
"useCases": [
"Compliance"
@@ -21,7 +20,6 @@
"compliance"
],
"marketplaces": [
- "marketplacev2"
+ "marketplacev2"
]
-
-}
+}
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_SOX/.pack-ignore b/Packs/XSIAMCompliance_SOX/.pack-ignore
index 8b137891791f..5fc5c37c39d5 100644
--- a/Packs/XSIAMCompliance_SOX/.pack-ignore
+++ b/Packs/XSIAMCompliance_SOX/.pack-ignore
@@ -1 +1,8 @@
+[file:1_0_1.md]
+ignore=RN113,RN114
+[file:1_0_2.md]
+ignore=RN113,RN114
+
+[file:2_0_0.md]
+ignore=RN113,RN114
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_SOX/README.md b/Packs/XSIAMCompliance_SOX/README.md
index 303ee0d5eae8..39e2ccdd16e7 100644
--- a/Packs/XSIAMCompliance_SOX/README.md
+++ b/Packs/XSIAMCompliance_SOX/README.md
@@ -1,10 +1,9 @@
## **Generate Compliance Dashboards and Reports**
-The SOX compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits. The dashboard and report aggregate and reference all data mapped to the Cortex Data Model (XDM).
+The SOX compliance pack provides a comprehensive dashboard and report template to easily monitor your Cortex XSIAM data compliance regulations and provide evidence for compliance audits.
**Note:** This pack is currently offered as a free beta of the Compliance module for a limited time. In the future, this module will be sold separately on top of XSIAM.
## **What does this pack do?**
- Install dashboard and report templates for the SOX regulations.
-- Reference data that has been mapped to the Cortex Data Model (XDM).
- Produce regulation evidence for audits.
diff --git a/Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_1.md b/Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_1.md
index 04117346a72b..285ecfc9c132 100644
--- a/Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_1.md
+++ b/Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_1.md
@@ -1,4 +1,5 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### SOX Compliance Dashboard
+
- Note: The pack moved to closed source.
diff --git a/Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_2.md b/Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_2.md
index 2ad2a755b44c..963234bbed78 100644
--- a/Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_2.md
+++ b/Packs/XSIAMCompliance_SOX/ReleaseNotes/1_0_2.md
@@ -1,5 +1,6 @@
-
#### XSIAM Dashboards
-##### XSIAMCompliance_HIPAA_Dashboard
+
+##### SOX Compliance Dashboard
+
- Added support for lazy loading the widgets.
-- Added support for caching the widgets data.
\ No newline at end of file
+- Added support for caching the widgets data.
diff --git a/Packs/XSIAMCompliance_SOX/ReleaseNotes/2_0_0.md b/Packs/XSIAMCompliance_SOX/ReleaseNotes/2_0_0.md
new file mode 100644
index 000000000000..a008d77b2132
--- /dev/null
+++ b/Packs/XSIAMCompliance_SOX/ReleaseNotes/2_0_0.md
@@ -0,0 +1,12 @@
+#### XSIAM Dashboards
+
+##### SOX Compliance Dashboard
+
+- Improved layout of the dashboard.
+- Updated XQL queries to improve dashboard load times.
+
+#### XSIAM Reports
+
+##### SOX Compliance Report
+
+- Updated XQL queries to improve report load time.
\ No newline at end of file
diff --git a/Packs/XSIAMCompliance_SOX/pack_metadata.json b/Packs/XSIAMCompliance_SOX/pack_metadata.json
index 9db1363896ae..2455566b30d4 100644
--- a/Packs/XSIAMCompliance_SOX/pack_metadata.json
+++ b/Packs/XSIAMCompliance_SOX/pack_metadata.json
@@ -2,14 +2,13 @@
"name": "SOX Compliance",
"description": "Ensure your organization is following SOX guidelines with the relevant dashboard and report evidence.",
"support": "xsoar",
- "currentVersion": "1.0.2",
+ "currentVersion": "2.0.0",
"author": "Cortex XSIAM",
"url": "https://www.paloaltonetworks.com/cortex",
"categories": [
"Analytics & SIEM"
],
- "tags": [
- ],
+ "tags": [],
"created": "2023-03-20T13:16:53Z",
"useCases": [
"Compliance"
@@ -21,7 +20,6 @@
"compliance"
],
"marketplaces": [
- "marketplacev2"
+ "marketplacev2"
]
-
-}
+}
\ No newline at end of file
From 425775f6729825202d93c307502c68eb00624800 Mon Sep 17 00:00:00 2001
From: Adi Daud <46249224+adi88d@users.noreply.github.com>
Date: Mon, 19 Feb 2024 22:50:36 +0200
Subject: [PATCH 026/272] PhishTank v2 - Added the username parameter (#32951)
* added the username parameter
* update docker
* set username as optional
* doc review
* add test_user_agent_header
* flake8
---
.../Integrations/PhishTankV2/PhishTankV2.py | 12 ++++++++--
.../Integrations/PhishTankV2/PhishTankV2.yml | 5 +++-
.../PhishTankV2/PhishTankV2_test.py | 24 +++++++++++++++++--
Packs/PhishTank/ReleaseNotes/2_0_30.md | 4 ++++
Packs/PhishTank/pack_metadata.json | 2 +-
5 files changed, 41 insertions(+), 6 deletions(-)
create mode 100644 Packs/PhishTank/ReleaseNotes/2_0_30.md
diff --git a/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2.py b/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2.py
index ce548a66c622..6ab9ff78b225 100644
--- a/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2.py
+++ b/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2.py
@@ -35,19 +35,26 @@ class Client(BaseClient):
use_https (bool): Whether to use HTTPS URL or HTTP URL.
"""
- def __init__(self, proxy: bool, verify: bool, fetch_interval_hours: str, use_https: str, reliability: str):
+ def __init__(self, proxy: bool, verify: bool, fetch_interval_hours: str, use_https: str, reliability: str,
+ username: str = ''):
super().__init__(proxy=proxy, verify=verify, base_url=HTTPS_BASE_URL if use_https else BASE_URL)
self.fetch_interval_hours = fetch_interval_hours
+ self.username = username
+
if DBotScoreReliability.is_valid_type(reliability):
self.reliability = DBotScoreReliability.get_dbot_score_reliability_from_str(reliability)
else:
return_error("PhishTankV2 error: Please provide a valid value for the Source Reliability parameter.")
def get_http_request(self, url_suffix: str):
+ headers = {}
+ if self.username:
+ headers = {'User-Agent': f'phishtank/{self.username}'}
result = self._http_request(
method='GET',
url_suffix=url_suffix,
resp_type="text",
+ headers=headers,
error_handler=handle_error
)
return result
@@ -316,13 +323,14 @@ def main() -> None:
verify = not params.get('insecure')
fetch_interval_hours = params.get('fetchIntervalHours')
reliability = params.get('integrationReliability')
+ username = params.get('username')
if not is_number(fetch_interval_hours):
return_error("PhishTankV2 error: Please provide a numeric value (and bigger than 0) for Database refresh "
"interval (hours)")
# initialize a client
- client = Client(proxy, verify, fetch_interval_hours, use_https, reliability)
+ client = Client(proxy, verify, fetch_interval_hours, use_https, reliability, username)
command = demisto.command()
demisto.debug(f'PhishTankV2: command is {command}')
diff --git a/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2.yml b/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2.yml
index 0dee64c88ad5..f07f3ec3d33c 100644
--- a/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2.yml
+++ b/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2.yml
@@ -3,6 +3,9 @@ commonfields:
id: PhishTank V2
version: -1
configuration:
+- display: Username
+ name: username
+ type: 0
- defaultvalue: 'false'
display: Use HTTPS connection
name: use_https
@@ -78,7 +81,7 @@ script:
name: phishtank-reload
- description: Shows the status (timestamp) of the last time that PhishTank database was loaded.
name: phishtank-status
- dockerimage: demisto/python3:3.10.13.73190
+ dockerimage: demisto/python3:3.10.13.87159
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2_test.py b/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2_test.py
index 441f99ca6bb5..d60969578281 100644
--- a/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2_test.py
+++ b/Packs/PhishTank/Integrations/PhishTankV2/PhishTankV2_test.py
@@ -10,9 +10,9 @@
def create_client(proxy: bool = False, verify: bool = False, fetch_interval_hours: str = "1",
- reliability: str = DBotScoreReliability.A_PLUS):
+ reliability: str = DBotScoreReliability.A_PLUS, username: str = ''):
return Client(proxy=proxy, verify=verify, fetch_interval_hours=fetch_interval_hours, use_https=False,
- reliability=reliability)
+ reliability=reliability, username=username)
@pytest.mark.parametrize('number, output', [("True", False), ('432', True), ("str", False),
@@ -243,3 +243,23 @@ def test_url_command(mocker, data, url, expected_score, expected_table):
# validate human readable
hr_ = command_results[0].to_context().get('HumanReadable', {})
assert hr_ == expected_table
+
+
+@pytest.mark.parametrize('username, expected_headers', [
+ ('test', {'User-Agent': 'phishtank/test'}),
+ ('', {})])
+def test_user_agent_header(mocker, username, expected_headers):
+ """
+ Given:
+ - phishtank username
+
+ When:
+ - After reload or url command
+
+ Then:
+ - validating that the User-Agent header is populated as expected
+ """
+ http_request = mocker.patch.object(Client, "_http_request", return_value='')
+ client = create_client(False, False, "1", DBotScoreReliability.B, username)
+ reload(client)
+ assert http_request.call_args.kwargs['headers'] == expected_headers
diff --git a/Packs/PhishTank/ReleaseNotes/2_0_30.md b/Packs/PhishTank/ReleaseNotes/2_0_30.md
new file mode 100644
index 000000000000..509d1527f406
--- /dev/null
+++ b/Packs/PhishTank/ReleaseNotes/2_0_30.md
@@ -0,0 +1,4 @@
+#### Integrations
+##### PhishTank v2
+- Added a new parameter *username*. Allows adding the PhishTank user to the requests header in order to increase the rate limit.
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
\ No newline at end of file
diff --git a/Packs/PhishTank/pack_metadata.json b/Packs/PhishTank/pack_metadata.json
index 3a22155cbba4..eab9df634856 100644
--- a/Packs/PhishTank/pack_metadata.json
+++ b/Packs/PhishTank/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "PhishTank",
"description": "PhishTank is a free community site where anyone can submit, verify, track and share phishing data",
"support": "xsoar",
- "currentVersion": "2.0.29",
+ "currentVersion": "2.0.30",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From f792bfcb4b25d1cf05bf389393483e4f9d4e96c0 Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Tue, 20 Feb 2024 02:53:39 +0200
Subject: [PATCH 027/272] [CortexXpanse] Update Integration Fetch Offset
(#32868) (#33002)
* Remove 3 second offset
* Add debug logging and remove comments
* changes after convo with John
* docket and RN
* bump ver
* edit RN
* readd old RN
* Update Packs/CortexXpanse/Integrations/CortexXpanse/CortexXpanse.py
---------
Co-authored-by: johnnywilkes <32227961+johnnywilkes@users.noreply.github.com>
Co-authored-by: bigeasyj
Co-authored-by: John <40349459+BigEasyJ@users.noreply.github.com>
Co-authored-by: Moshe Galitzky <112559840+moishce@users.noreply.github.com>
---
.../Integrations/CortexXpanse/CortexXpanse.py | 19 ++++++++++++++-----
Packs/CortexXpanse/ReleaseNotes/1_0_19.md | 3 +++
Packs/CortexXpanse/pack_metadata.json | 2 +-
3 files changed, 18 insertions(+), 6 deletions(-)
create mode 100644 Packs/CortexXpanse/ReleaseNotes/1_0_19.md
diff --git a/Packs/CortexXpanse/Integrations/CortexXpanse/CortexXpanse.py b/Packs/CortexXpanse/Integrations/CortexXpanse/CortexXpanse.py
index dab56bcfb32f..6dee0708b5f7 100644
--- a/Packs/CortexXpanse/Integrations/CortexXpanse/CortexXpanse.py
+++ b/Packs/CortexXpanse/Integrations/CortexXpanse/CortexXpanse.py
@@ -9,7 +9,6 @@
DEFAULT_SEARCH_LIMIT = 100
MAX_ALERTS = 100 # max alerts per fetch
-ONE_HOUR = 3600
TIME_FORMAT = "%Y-%m-%dT%H:%M:%S"
V1_URL_SUFFIX = "/public_api/v1"
V2_URL_SUFFIX = "/public_api/v2"
@@ -1290,11 +1289,9 @@ def fetch_incidents(client: Client, max_fetch: int, last_run: dict[str, int],
# Handle first time fetch
last_fetch = first_fetch_time if last_fetch is None else int(last_fetch)
-
latest_created_time = cast(int, last_fetch)
- # because some values are not populated immediately at alert creation time,
- # we will add an additional offset to increase the likelihood that these are available
- latest_created_time = latest_created_time + ONE_HOUR
+
+ demisto.debug(f"CortexXpanse - last fetched alert timestamp: {str(last_fetch)}")
incidents = []
@@ -1330,6 +1327,10 @@ def fetch_incidents(client: Client, max_fetch: int, last_run: dict[str, int],
latest_created_time = incident_created_time
next_run = {'last_fetch': latest_created_time}
+
+ demisto.debug(f"CortexXpanse - Number of incidents: {len(incidents)}")
+ demisto.debug(f"CortexXpanse - Next run after incidents fetching: : {next_run}")
+
return next_run, incidents
@@ -1416,6 +1417,14 @@ def main() -> None:
headers=headers,
proxy=proxy)
+ # To debug integration instance configuration.
+ integration_context = demisto.getIntegrationContext()
+ if 'xpanse_integration_severity' in integration_context:
+ xpanse_integration_severity = integration_context.get('xpanse_integration_severity')
+ if xpanse_integration_severity != severity:
+ demisto.setIntegrationContext({"xpanse_integration_severity": severity})
+ demisto.debug(demisto.debug(f"CortexXpanse - Integration Severity: {severity}"))
+
commands = {
'asm-list-external-service': list_external_service_command,
'asm-get-external-service': get_external_service_command,
diff --git a/Packs/CortexXpanse/ReleaseNotes/1_0_19.md b/Packs/CortexXpanse/ReleaseNotes/1_0_19.md
new file mode 100644
index 000000000000..589524adfc01
--- /dev/null
+++ b/Packs/CortexXpanse/ReleaseNotes/1_0_19.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Cortex Xpanse
+Updated the fetch logic to no longer contain a one hour offset.
diff --git a/Packs/CortexXpanse/pack_metadata.json b/Packs/CortexXpanse/pack_metadata.json
index 4b1bf85a265a..c9a700d8355b 100644
--- a/Packs/CortexXpanse/pack_metadata.json
+++ b/Packs/CortexXpanse/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Cortex Xpanse",
"description": "Content for working with Attack Surface Management (ASM).",
"support": "xsoar",
- "currentVersion": "1.0.18",
+ "currentVersion": "1.0.19",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From adaba25b71ad61c1a4f1c5b278f75ef21d73025f Mon Sep 17 00:00:00 2001
From: Dan Tavori <38749041+dantavori@users.noreply.github.com>
Date: Tue, 20 Feb 2024 07:10:27 +0200
Subject: [PATCH 028/272] metrics in csp (#32383)
---
Packs/Base/ReleaseNotes/1_33_33.md | 6 +
.../CommonServerPython/CommonServerPython.py | 201 +++++++++++++---
.../CommonServerPython_test.py | 221 ++++++++++++++++++
Packs/Base/pack_metadata.json | 2 +-
.../Integrations/EmailHippo/EmailHippo.py | 51 ++--
.../EmailHippo/EmailHippo_test.py | 54 ++++-
Packs/EmailHippo/ReleaseNotes/1_0_4.md | 6 +
Packs/EmailHippo/pack_metadata.json | 2 +-
8 files changed, 479 insertions(+), 64 deletions(-)
create mode 100644 Packs/Base/ReleaseNotes/1_33_33.md
create mode 100644 Packs/EmailHippo/ReleaseNotes/1_0_4.md
diff --git a/Packs/Base/ReleaseNotes/1_33_33.md b/Packs/Base/ReleaseNotes/1_33_33.md
new file mode 100644
index 000000000000..f9cfc0c1bc55
--- /dev/null
+++ b/Packs/Base/ReleaseNotes/1_33_33.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### CommonServerPython
+
+- Added support for execution metrics in the *BaseClient* class.
diff --git a/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py b/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py
index e44e32aff057..fc52b1e430d5 100644
--- a/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py
+++ b/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py
@@ -199,7 +199,7 @@ def __del__(self):
import requests
from requests.adapters import HTTPAdapter
from urllib3.util import Retry
- from typing import Optional, Dict, List, Any, Union, Set
+ from typing import Optional, Dict, List, Any, Union, Set, cast
from urllib3 import disable_warnings
disable_warnings()
@@ -512,6 +512,7 @@ class ErrorTypes(object):
PROXY_ERROR = 'ProxyError'
SSL_ERROR = 'SSLError'
TIMEOUT_ERROR = 'TimeoutError'
+ RETRY_ERROR = "RetryError"
class FeedIndicatorType(object):
@@ -7322,7 +7323,7 @@ class ExecutionMetrics(object):
"""
def __init__(self, success=0, quota_error=0, general_error=0, auth_error=0, service_error=0, connection_error=0,
- proxy_error=0, ssl_error=0, timeout_error=0):
+ proxy_error=0, ssl_error=0, timeout_error=0, retry_error=0):
self._metrics = []
self.metrics = None
self.success = success
@@ -7334,6 +7335,7 @@ def __init__(self, success=0, quota_error=0, general_error=0, auth_error=0, serv
self.proxy_error = proxy_error
self.ssl_error = ssl_error
self.timeout_error = timeout_error
+ self.retry_error = retry_error
"""
Initializes an ExecutionMetrics object. Once initialized, you may increment each metric type according to the
metric you'd like to report. Afterwards, pass the `metrics` value to CommandResults.
@@ -7365,6 +7367,9 @@ def __init__(self, success=0, quota_error=0, general_error=0, auth_error=0, serv
:type timeout_error: ``int``
:param timeout_error: Quantity of Timeout Error metrics
+ :type retry_error: ``int``
+ :param retry_error: Quantity of Retry Error metrics
+
:type metrics: ``CommandResults``
:param metrics: Append this value to your CommandResults list to report the metrics to your server.
"""
@@ -7456,6 +7461,15 @@ def timeout_error(self, value):
self._timeout_error = value
self.update_metrics(ErrorTypes.TIMEOUT_ERROR, self._timeout_error)
+ @property
+ def retry_error(self):
+ return self._retry_error
+
+ @retry_error.setter
+ def retry_error(self, value):
+ self._retry_error = value
+ self.update_metrics(ErrorTypes.RETRY_ERROR, self._retry_error)
+
def get_metric_list(self):
return self._metrics
@@ -8772,7 +8786,10 @@ def __init__(
system_timeout = os.getenv('REQUESTS_TIMEOUT', '')
self.timeout = float(entity_timeout or system_timeout or timeout)
+ self.execution_metrics = ExecutionMetrics()
+
def __del__(self):
+ self._return_execution_metrics_results()
try:
self._session.close()
except AttributeError:
@@ -8862,7 +8879,8 @@ def _http_request(self, method, url_suffix='', full_url=None, headers=None, auth
params=None, data=None, files=None, timeout=None, resp_type='json', ok_codes=None,
return_empty_response=False, retries=0, status_list_to_retry=None,
backoff_factor=5, raise_on_redirect=False, raise_on_status=False,
- error_handler=None, empty_valid_codes=None, params_parser=None, **kwargs):
+ error_handler=None, empty_valid_codes=None, params_parser=None, with_metrics=False,
+ **kwargs):
"""A wrapper for requests lib to send our requests and handle requests and responses better.
:type method: ``str``
@@ -8960,6 +8978,9 @@ def _http_request(self, method, url_suffix='', full_url=None, headers=None, auth
see here for more info: https://docs.python.org/3/library/urllib.parse.html#urllib.parse.urlencode
Note! supported only in python3.
+ :type with_metrics ``bool``
+ :param with_metrics: Whether or not to calculate execution metrics from the response
+
:return: Depends on the resp_type parameter
:rtype: ``dict`` or ``str`` or ``bytes`` or ``xml.etree.ElementTree.Element`` or ``requests.Response``
"""
@@ -8989,40 +9010,20 @@ def _http_request(self, method, url_suffix='', full_url=None, headers=None, auth
timeout=timeout,
**kwargs
)
- # Handle error responses gracefully
if not self._is_status_code_valid(res, ok_codes):
- if error_handler:
- error_handler(res)
- else:
- self.client_error_handler(res)
+ self._handle_error(error_handler, res, with_metrics)
- if not empty_valid_codes:
- empty_valid_codes = [204]
- is_response_empty_and_successful = (res.status_code in empty_valid_codes)
- if is_response_empty_and_successful and return_empty_response:
- return res
+ return self._handle_success(res, resp_type, empty_valid_codes, return_empty_response, with_metrics)
- resp_type = resp_type.lower()
- try:
- if resp_type == 'json':
- return res.json()
- if resp_type == 'text':
- return res.text
- if resp_type == 'content':
- return res.content
- if resp_type == 'xml':
- ET.fromstring(res.text)
- if resp_type == 'response':
- return res
- return res
- except ValueError as exception:
- raise DemistoException('Failed to parse {} object from response: {}' # type: ignore[str-bytes-safe]
- .format(resp_type, res.content), exception, res)
except requests.exceptions.ConnectTimeout as exception:
+ if with_metrics:
+ self.execution_metrics.timeout_error += 1
err_msg = 'Connection Timeout Error - potential reasons might be that the Server URL parameter' \
' is incorrect or that the Server is not accessible from your host.'
raise DemistoException(err_msg, exception)
except requests.exceptions.SSLError as exception:
+ if with_metrics:
+ self.execution_metrics.ssl_error += 1
# in case the "Trust any certificate" is already checked
if not self._verify:
raise
@@ -9030,10 +9031,14 @@ def _http_request(self, method, url_suffix='', full_url=None, headers=None, auth
' the integration configuration.'
raise DemistoException(err_msg, exception)
except requests.exceptions.ProxyError as exception:
+ if with_metrics:
+ self.execution_metrics.proxy_error += 1
err_msg = 'Proxy Error - if the \'Use system proxy\' checkbox in the integration configuration is' \
' selected, try clearing the checkbox.'
raise DemistoException(err_msg, exception)
except requests.exceptions.ConnectionError as exception:
+ if with_metrics:
+ self.execution_metrics.connection_error += 1
# Get originating Exception in Exception chain
error_class = str(exception.__class__)
err_type = '<' + error_class[error_class.find('\'') + 1: error_class.rfind('\'')] + '>'
@@ -9043,6 +9048,8 @@ def _http_request(self, method, url_suffix='', full_url=None, headers=None, auth
.format(err_type, exception.errno, exception.strerror)
raise DemistoException(err_msg, exception)
except requests.exceptions.RetryError as exception:
+ if with_metrics:
+ self.execution_metrics.retry_error += 1
try:
reason = 'Reason: {}'.format(exception.args[0].reason.args[0])
except Exception: # noqa: disable=broad-except
@@ -9050,6 +9057,136 @@ def _http_request(self, method, url_suffix='', full_url=None, headers=None, auth
err_msg = 'Max Retries Error- Request attempts with {} retries failed. \n{}'.format(retries, reason)
raise DemistoException(err_msg, exception)
+ def _handle_error(self, error_handler, res, should_update_metrics):
+ """ Handles error response by calling error handler or default handler.
+ If an exception is raised, update metrics with failure. Otherwise, proceeds.
+
+ :type res: ``requests.Response``
+ :param res: Response from API after the request for which to check error type
+
+ :type error_handler ``callable``
+ :param error_handler: Given an error entry, the error handler outputs the
+ new formatted error message.
+
+ :type should_update_metrics ``bool``
+ :param should_update_metrics: Whether or not to update execution metrics according to response
+ """
+ try:
+ if error_handler:
+ error_handler(res)
+ else:
+ self.client_error_handler(res)
+ except Exception:
+ if should_update_metrics:
+ self._update_metrics(res, success=False)
+ raise
+
+ def _handle_success(self, res, resp_type, empty_valid_codes, return_empty_response, should_update_metrics):
+ """ Handles successful response
+
+ :type res: ``requests.Response``
+ :param res: Response from API after the request for which to check error type
+
+ :type resp_type: ``str``
+ :param resp_type:
+ Determines which data format to return from the HTTP request. The default
+ is 'json'. Other options are 'text', 'content', 'xml' or 'response'. Use 'response'
+ to return the full response object.
+
+ :type empty_valid_codes: ``list``
+ :param empty_valid_codes: A list of all valid status codes of empty responses (usually only 204, but
+ can vary)
+
+ :type return_empty_response: ``bool``
+ :param response: Whether to return an empty response body if the response code is in empty_valid_codes
+
+ :type should_update_metrics ``bool``
+ :param should_update_metrics: Whether or not to update execution metrics according to response
+ """
+ if should_update_metrics:
+ self._update_metrics(res, success=True)
+
+ if not empty_valid_codes:
+ empty_valid_codes = [204]
+ is_response_empty_and_successful = (res.status_code in empty_valid_codes)
+ if is_response_empty_and_successful and return_empty_response:
+ return res
+
+ return self.cast_response(res, resp_type)
+
+ def cast_response(self, res, resp_type, raise_on_error=True):
+ resp_type = resp_type.lower()
+ try:
+ if resp_type == 'json':
+ return res.json()
+ if resp_type == 'text':
+ return res.text
+ if resp_type == 'content':
+ return res.content
+ if resp_type == 'xml':
+ ET.fromstring(res.text)
+ if resp_type == 'response':
+ return res
+ return res
+ except ValueError as exception:
+ if raise_on_error:
+ raise DemistoException('Failed to parse {} object from response: {}' # type: ignore[str-bytes-safe]
+ .format(resp_type, res.content), exception, res)
+
+ def _update_metrics(self, res, success):
+ """ Updates execution metrics based on response and success flag.
+
+ :type response: ``requests.Response``
+ :param response: Response from API after the request for which to check error type
+
+ :type success: ``bool``
+ :param success: Wheter the request succeeded or failed
+ """
+ if success:
+ if not self.is_polling_in_progress(res):
+ self.execution_metrics.success += 1
+ else:
+ error_type = self.determine_error_type(res)
+ if error_type == ErrorTypes.QUOTA_ERROR:
+ self.execution_metrics.quota_error += 1
+ elif error_type == ErrorTypes.AUTH_ERROR:
+ self.execution_metrics.auth_error += 1
+ elif error_type == ErrorTypes.SERVICE_ERROR:
+ self.execution_metrics.service_error += 1
+ elif error_type == ErrorTypes.GENERAL_ERROR:
+ self.execution_metrics.general_error += 1
+
+ def determine_error_type(self, response):
+ """ Determines the type of error based on response status code and content.
+ Note: this method can be overriden by subclass when implementing execution metrics.
+
+ :type response: ``requests.Response``
+ :param response: Response from API after the request for which to check error type
+
+ :return: The error type if found, otherwise None
+ :rtype: ``ErrorTypes``
+ """
+ if response.status_code == 401:
+ return ErrorTypes.AUTH_ERROR
+ elif response.status_code == 429:
+ return ErrorTypes.QUOTA_ERROR
+ elif response.status_code == 500:
+ return ErrorTypes.SERVICE_ERROR
+ return ErrorTypes.GENERAL_ERROR
+
+ def is_polling_in_progress(self, response):
+ """If thie response indicates polling operation in progress, return True.
+ Note: this method should be overriden by subclass when implementing polling reputation commands
+ with execution metrics.
+
+ :type response: ``requests.Response``
+ :param response: Response from API after the request for which to check the polling status
+
+ :return: Whether the response indicates polling in progress
+ :rtype: ``bool``
+ """
+ return False
+
def _is_status_code_valid(self, response, ok_codes=None):
"""If the status code is OK, return 'True'.
@@ -9087,6 +9224,12 @@ def client_error_handler(self, res):
err_msg += '\n{}'.format(res.text)
raise DemistoException(err_msg, res=res)
+ def _return_execution_metrics_results(self):
+ """ Returns execution metrics results.
+ """
+ if self.execution_metrics.metrics:
+ return_results(cast(CommandResults, self.execution_metrics.metrics))
+
def batch(iterable, batch_size=1):
"""Gets an iterable and yields slices of it.
diff --git a/Packs/Base/Scripts/CommonServerPython/CommonServerPython_test.py b/Packs/Base/Scripts/CommonServerPython/CommonServerPython_test.py
index 74de2379560d..f320123f3cc8 100644
--- a/Packs/Base/Scripts/CommonServerPython/CommonServerPython_test.py
+++ b/Packs/Base/Scripts/CommonServerPython/CommonServerPython_test.py
@@ -3134,6 +3134,227 @@ def test_http_request_params_parser_none(self, requests_mock):
assert mock_request.last_request.query == 'key=value+with+spaces'
+ def test_http_request_execution_metrics_success(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A successful response.
+ Then: Verify the successful execution metrics is incremented.
+ """
+ requests_mock.get('http://example.com/api/v2/event', text="success")
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ client._http_request('get', 'event', resp_type='response', with_metrics=True)
+ assert client.execution_metrics.success == 1
+
+ def test_http_request_execution_metrics_success_but_polling_in_progress(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A successful response.
+ - Response is determined as polling in progress.
+ Then: Verify the successful execution metrics is not incremented.
+ """
+ requests_mock.get('http://example.com/api/v2/event', text="success")
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ client.is_polling_in_progress = lambda _: True
+ client._http_request('get', 'event', resp_type='response', with_metrics=True)
+ assert client.execution_metrics.success == 0
+
+ def test_http_request_execution_metrics_timeout(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A timeout error is returned.
+ Then: Verify the timeout error execution metrics is incremented.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', exc=requests.exceptions.ConnectTimeout)
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException):
+ client._http_request('get', 'event', resp_type='response', with_metrics=True)
+ assert client.execution_metrics.timeout_error == 1
+
+ def test_http_request_execution_metrics_ssl_error(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - An SSL error is returned.
+ Then: Verify the ssl error execution metrics is incremented.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', exc=requests.exceptions.SSLError)
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201))
+ with raises(DemistoException):
+ client._http_request('get', 'event', resp_type='response', with_metrics=True)
+ assert client.execution_metrics.ssl_error == 1
+
+ def test_http_request_execution_metrics_proxy_error(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A proxy error is returned.
+ Then: Verify the proxy error execution metrics is incremented.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', exc=requests.exceptions.ProxyError)
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException):
+ client._http_request('get', 'event', resp_type='response', with_metrics=True)
+ assert client.execution_metrics.proxy_error == 1
+
+ def test_http_request_execution_metrics_connection_error(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A connection error is returned.
+ Then: Verify the connection error execution metrics is incremented.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', exc=requests.exceptions.ConnectionError)
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException):
+ client._http_request('get', 'event', resp_type='response', with_metrics=True)
+ assert client.execution_metrics.connection_error == 1
+
+ def test_http_request_execution_metrics_retry_error(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A retry error is returned.
+ Then: Verify the retry error execution metrics is incremented.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', exc=requests.exceptions.RetryError)
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException):
+ client._http_request('get', 'event', resp_type='response', with_metrics=True)
+ assert client.execution_metrics.retry_error == 1
+
+ def test_http_request_execution_metrics_auth_error(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - An auth error (401 status code) is returned.
+ Then: Verify the auth error execution metrics is incremented.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', status_code=401, text="err")
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException, match="Error in API call"):
+ client._http_request('get', 'event', with_metrics=True)
+ assert client.execution_metrics.auth_error == 1
+
+ def test_http_request_execution_metrics_quota_error(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A quota error (429 status code) is returned.
+ Then: Verify the quota error execution metrics is incremented.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', status_code=429, text="err")
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException, match="Error in API call"):
+ client._http_request('get', 'event', with_metrics=True)
+ assert client.execution_metrics.quota_error == 1
+
+ def test_http_request_execution_metrics_service_error(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A service error (500 status code) is returned.
+ Then: Verify the service error execution metrics is incremented.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', status_code=500, text="err")
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException, match="Error in API call"):
+ client._http_request('get', 'event', with_metrics=True)
+ assert client.execution_metrics.service_error == 1
+
+ def test_http_request_execution_metrics_general_error(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A general error (400 status code) is returned.
+ Then: Verify the general error execution metrics is incremented.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', status_code=400, text="err")
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException, match="Error in API call"):
+ client._http_request('get', 'event', with_metrics=True)
+ assert client.execution_metrics.general_error == 1
+
+ def test_http_request_execution_metrics_not_found_error_but_ok(cls, requests_mock):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - A not found error (404 status code) is returned.
+ - 404 is considered ok
+ Then: Verify the success execution metrics is incremented, and not the general error metrics.
+ """
+ requests_mock.get('http://example.com/api/v2/event', status_code=404, text="err")
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201, 404), verify=False)
+ res = client._http_request('get', 'event', resp_type='response', with_metrics=True)
+ assert res.status_code == 404
+ assert client.execution_metrics.success == 1
+ assert client.execution_metrics.general_error == 0
+
+ def test_http_request_execution_metrics_results(cls, requests_mock, mocker):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function with metrics
+ - An general error is returned
+ - The client object is then deleted
+ Then: Verify an execution metrics entry is sent to demisto.results() accordingly.
+ """
+ from CommonServerPython import DemistoException, EntryType, ErrorTypes
+ requests_mock.get('http://example.com/api/v2/event', status_code=400, text="err")
+ demisto_results_mock = mocker.patch.object(demisto, 'results')
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException, match="Error in API call"):
+ client._http_request('get', 'event', with_metrics=True)
+ del client
+ demisto_results_mock.assert_called_once
+ entry = demisto_results_mock.call_args[0][0]
+ assert entry["Type"] == EntryType.EXECUTION_METRICS
+ assert entry["APIExecutionMetrics"] == [{
+ "Type": ErrorTypes.GENERAL_ERROR,
+ "APICallsCount": 1,
+ }]
+
+ def test_http_request_no_execution_metrics_results(cls, requests_mock, mocker):
+ """
+ Given: A BaseClient object
+ When:
+ - Calling _http_request function without metrics
+ - An general error is returned
+ - The client object is then deleted
+ Then: Verify demisto.results() is not called.
+ """
+ from CommonServerPython import DemistoException
+ requests_mock.get('http://example.com/api/v2/event', status_code=400, text="err")
+ demisto_results_mock = mocker.patch.object(demisto, 'results')
+ client = cls.BaseClient('http://example.com/api/v2/', ok_codes=(200, 201), verify=False)
+ with raises(DemistoException, match="Error in API call"):
+ client._http_request('get', 'event')
+ del client
+ demisto_results_mock.assert_not_called
+
@pytest.mark.skipif(not IS_PY3, reason='test not supported in py2')
def test_http_request_params_parser_quote(self, requests_mock):
"""
diff --git a/Packs/Base/pack_metadata.json b/Packs/Base/pack_metadata.json
index 21eda318c044..626f953c6d96 100644
--- a/Packs/Base/pack_metadata.json
+++ b/Packs/Base/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Base",
"description": "The base pack for Cortex XSOAR.",
"support": "xsoar",
- "currentVersion": "1.33.32",
+ "currentVersion": "1.33.33",
"author": "Cortex XSOAR",
"serverMinVersion": "6.0.0",
"url": "https://www.paloaltonetworks.com/cortex",
diff --git a/Packs/EmailHippo/Integrations/EmailHippo/EmailHippo.py b/Packs/EmailHippo/Integrations/EmailHippo/EmailHippo.py
index 57a5e567c39d..6f9dd03acc88 100644
--- a/Packs/EmailHippo/Integrations/EmailHippo/EmailHippo.py
+++ b/Packs/EmailHippo/Integrations/EmailHippo/EmailHippo.py
@@ -34,7 +34,6 @@ def __init__(self, more_api_key, whois_api_key, more_server_url, whois_server_ur
self._whois_api_key = whois_api_key
self._more_server_url = more_server_url.rstrip("/")
self._whois_server_url = f'{whois_server_url.rstrip("/")}/v1/{whois_api_key}'
- self.execution_metrics = ExecutionMetrics()
super().__init__(base_url='', **kwargs)
@@ -48,8 +47,11 @@ def get_email_reputation(self, email: str) -> dict[str, Any]:
dict: dict containing the Email reputation as returned from the API
"""
- return self._http_request(method='GET',
- full_url=f'{self._more_server_url}/v3/more/json/{self._more_api_key}/{email}')
+ return self._http_request(
+ method='GET',
+ full_url=f'{self._more_server_url}/v3/more/json/{self._more_api_key}/{email}',
+ with_metrics=True,
+ )
def get_domain_reputation(self, domain: str) -> dict[str, Any]:
"""
@@ -62,39 +64,34 @@ def get_domain_reputation(self, domain: str) -> dict[str, Any]:
dict: dict containing the domain reputation as returned from the API.
"""
- return self._http_request(method='GET', full_url=f'{self._whois_server_url}/{domain}')
+ return self._http_request(
+ method='GET',
+ full_url=f'{self._whois_server_url}/{domain}',
+ with_metrics=True,
+ )
def get_email_quota(self) -> dict[str, Any]:
"""
Get the email quota remaining for the API key
"""
- return self._http_request(method='GET',
- full_url=f'{self._more_server_url}/customer/reports/v3/quota/{self._more_api_key}')
+ return self._http_request(
+ method='GET',
+ full_url=f'{self._more_server_url}/customer/reports/v3/quota/{self._more_api_key}',
+ with_metrics=True,
+ )
- def error_handler(self, res: Response):
- """
- Error handling for http responses, to support the API Execution Metrics.
+ def determine_error_type(self, res: Response):
+ """ Determines the error type based on response.
Args:
res (Response): The response object from the http request.
- """
- if res.status_code == 429 or 'Insufficient quota' in res.text:
- self.execution_metrics.quota_error += 1
- elif res.status_code == 401:
- self.execution_metrics.auth_error += 1
- else:
- self.execution_metrics.general_error += 1
-
- self.client_error_handler(res)
- def _http_request(self, **kwargs):
- """
- Wrapper for BaseClient._http_request for supporting API Execution Metrics.
+ Returns:
+ (ErrorTypes): The error type determined.
"""
- try:
- return super()._http_request(error_handler=self.error_handler, **kwargs)
- finally:
- self.execution_metrics.success += 1
+ if 'Insufficient quota' in res.text:
+ return ErrorTypes.QUOTA_ERROR
+ return super().determine_error_type(res)
def parse_domain_date(domain_date: list[str] | str, date_format: str = '%Y-%m-%dT%H:%M:%S.000Z') -> str | None:
@@ -391,12 +388,10 @@ def main() -> None: # pragma: no cover
else:
raise NotImplementedError(f'Command {command} is not implemented')
if res:
- return_results(append_metrics(client.execution_metrics, res))
+ return_results(res)
# Log exceptions and return errors
except Exception as e:
- if client:
- return_results(client.execution_metrics.metrics)
return_error(f'Failed to execute {command} command.\nError:\n{str(e)}')
diff --git a/Packs/EmailHippo/Integrations/EmailHippo/EmailHippo_test.py b/Packs/EmailHippo/Integrations/EmailHippo/EmailHippo_test.py
index cd3f7abf074f..5bdfe55271fa 100644
--- a/Packs/EmailHippo/Integrations/EmailHippo/EmailHippo_test.py
+++ b/Packs/EmailHippo/Integrations/EmailHippo/EmailHippo_test.py
@@ -16,14 +16,15 @@ def load_test_data(path):
class TestHappyPath:
- def test_get_email_reputation_success(self, requests_mock, client):
+ def test_get_email_reputation_success(self, requests_mock, client: Client):
"""
Given:
a Client instance and a mocked API response
When:
get_email_reputation is called with a valid email address
Then:
- result returned as expected
+ - result returned as expected
+ - execution metrics success is raised by 1
"""
requests_mock.get('https://test.com/v3/more/json/test/test@example.com',
json=load_test_data('test_data/get_email_output.json')['api_result'])
@@ -37,8 +38,9 @@ def test_get_email_reputation_success(self, requests_mock, client):
actual_entry_context = command_res[0].to_context()['EntryContext']
assert expected_entry_context == actual_entry_context
assert all(key in command_res[0].readable_output for key in hr_keys)
+ assert client.execution_metrics.success == 1
- def test_domain_reputation_command_success(self, requests_mock, client):
+ def test_domain_reputation_command_success(self, requests_mock, client: Client):
"""
Given:
- a Client instance and a mocked API response
@@ -46,6 +48,7 @@ def test_domain_reputation_command_success(self, requests_mock, client):
- domain_reputation_command is called with a valid domain
Then:
- result returned as expected
+ - execution metrics success is raised by 1
"""
requests_mock.get('https://test.com/v1/test/example.com',
json=load_test_data('test_data/get_domain_output.json')['api_result'])
@@ -64,8 +67,9 @@ def test_domain_reputation_command_success(self, requests_mock, client):
actual_entry_context = command_res[0].to_context()['EntryContext']
assert expected_entry_context == actual_entry_context
assert all(key in command_res[0].readable_output for key in hr_keys)
+ assert client.execution_metrics.success == 1
- def test_quota_command_success(self, requests_mock, client):
+ def test_quota_command_success(self, requests_mock, client: Client):
"""
Given:
- a Client instance and a mocked API response
@@ -73,6 +77,7 @@ def test_quota_command_success(self, requests_mock, client):
- get_email_quota_command is called with a valid domain
Then:
- result returned as expected
+ - execution metrics success is raised by 1
"""
requests_mock.get('https://test.com/customer/reports/v3/quota/test',
json=load_test_data('test_data/get_quota_output.json'))
@@ -86,11 +91,12 @@ def test_quota_command_success(self, requests_mock, client):
assert command_res
assert all(key in command_res.readable_output for key in hr_keys)
assert 'licenseKey' not in command_res.outputs
+ assert client.execution_metrics.success == 1
class TestFailure:
- def test_get_email_reputation_failure_quota_limit(self, requests_mock, client):
+ def test_get_email_reputation_failure_quota_limit(self, requests_mock, client: Client):
"""
Given:
a Client instance and a mocked failed quota limit API response
@@ -108,3 +114,41 @@ def test_get_email_reputation_failure_quota_limit(self, requests_mock, client):
with pytest.raises(DemistoException):
client.get_email_reputation('test@example.com')
assert client.execution_metrics.quota_error == 1
+
+ def test_get_email_reputation_failure_auth_error(self, requests_mock, client: Client):
+ """
+ Given:
+ a Client instance and a mocked failed auth limit API response
+ When:
+ get_email_reputation is called with a valid email address
+ Then:
+ - a DemistoException is raised
+ - matrix auth_error increased
+ """
+ requests_mock.get(
+ 'https://test.com/v3/more/json/test/test@example.com',
+ status_code=401,
+ )
+
+ with pytest.raises(DemistoException):
+ client.get_email_reputation('test@example.com')
+ assert client.execution_metrics.auth_error == 1
+
+ def test_get_email_reputation_failure_general_error(self, requests_mock, client: Client):
+ """
+ Given:
+ a Client instance and a mocked 400 API response
+ When:
+ get_email_reputation is called with a valid email address
+ Then:
+ - a DemistoException is raised
+ - matrix general_error increased
+ """
+ requests_mock.get(
+ 'https://test.com/v3/more/json/test/test@example.com',
+ status_code=400,
+ )
+
+ with pytest.raises(DemistoException):
+ client.get_email_reputation('test@example.com')
+ assert client.execution_metrics.general_error == 1
diff --git a/Packs/EmailHippo/ReleaseNotes/1_0_4.md b/Packs/EmailHippo/ReleaseNotes/1_0_4.md
new file mode 100644
index 000000000000..df804f622c59
--- /dev/null
+++ b/Packs/EmailHippo/ReleaseNotes/1_0_4.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Email Hippo
+
+- Internal improvements in execution metrics collection.
diff --git a/Packs/EmailHippo/pack_metadata.json b/Packs/EmailHippo/pack_metadata.json
index 31e23d3c01e7..60e811d836b7 100644
--- a/Packs/EmailHippo/pack_metadata.json
+++ b/Packs/EmailHippo/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Email Hippo",
"description": "Use this tool to verify email sources as fake emails that were used as part of phishing attacks.",
"support": "xsoar",
- "currentVersion": "1.0.3",
+ "currentVersion": "1.0.4",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 0b947a0333858b2fbc2d5e810c07669be7792b7a Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Tue, 20 Feb 2024 09:00:29 +0200
Subject: [PATCH 029/272] Update Docker Image To demisto/boto3py3 (#33008)
* Updated Metadata Of Pack AWS-CloudTrail
* Added release notes to pack AWS-CloudTrail
* Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.yml Docker image update
---
.../Integrations/AWS-CloudTrail/AWS-CloudTrail.yml | 2 +-
Packs/AWS-CloudTrail/ReleaseNotes/1_0_11.md | 3 +++
Packs/AWS-CloudTrail/pack_metadata.json | 2 +-
3 files changed, 5 insertions(+), 2 deletions(-)
create mode 100644 Packs/AWS-CloudTrail/ReleaseNotes/1_0_11.md
diff --git a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.yml b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.yml
index 898dc1bc0ead..833ea287a3b9 100644
--- a/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.yml
+++ b/Packs/AWS-CloudTrail/Integrations/AWS-CloudTrail/AWS-CloudTrail.yml
@@ -371,7 +371,7 @@ script:
- contextPath: AWS.CloudTrail.Events.CloudTrailEvent
description: A JSON string that contains a representation of the event returned.
type: string
- dockerimage: demisto/boto3py3:1.0.0.86958
+ dockerimage: demisto/boto3py3:1.0.0.88114
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/AWS-CloudTrail/ReleaseNotes/1_0_11.md b/Packs/AWS-CloudTrail/ReleaseNotes/1_0_11.md
new file mode 100644
index 000000000000..9885337e7ce1
--- /dev/null
+++ b/Packs/AWS-CloudTrail/ReleaseNotes/1_0_11.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### AWS - CloudTrail
+- Updated the Docker image to: *demisto/boto3py3:1.0.0.88114*.
diff --git a/Packs/AWS-CloudTrail/pack_metadata.json b/Packs/AWS-CloudTrail/pack_metadata.json
index 15c81b4fd6e0..9080c6a6e3aa 100644
--- a/Packs/AWS-CloudTrail/pack_metadata.json
+++ b/Packs/AWS-CloudTrail/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "AWS - CloudTrail",
"description": "Amazon Web Services CloudTrail.",
"support": "xsoar",
- "currentVersion": "1.0.10",
+ "currentVersion": "1.0.11",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From e4ee446b3681f3479c32a80bafd66efa50ccb2b7 Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Tue, 20 Feb 2024 09:02:50 +0200
Subject: [PATCH 030/272] Update Docker Image To demisto/python3 (#33007)
* Updated Metadata Of Pack DomainToolsIrisDetect
* Added release notes to pack DomainToolsIrisDetect
* Packs/DomainToolsIrisDetect/Integrations/DomainToolsIrisDetect/DomainToolsIrisDetect.yml Docker image update
* Updated Metadata Of Pack AtlassianConfluenceCloud
* Added release notes to pack AtlassianConfluenceCloud
* Packs/AtlassianConfluenceCloud/Integrations/AtlassianConfluenceCloud/AtlassianConfluenceCloud.yml Docker image update
* Updated Metadata Of Pack Gatewatcher-AionIQ
* Added release notes to pack Gatewatcher-AionIQ
* Packs/Gatewatcher-AionIQ/Integrations/GCenter/GCenter.yml Docker image update
* Updated Metadata Of Pack McAfeeNSM
* Added release notes to pack McAfeeNSM
* Packs/McAfeeNSM/Integrations/McAfeeNSMv2/McAfeeNSMv2.yml Docker image update
* Updated Metadata Of Pack RecordedFutureASI
* Added release notes to pack RecordedFutureASI
* Packs/RecordedFutureASI/Integrations/RecordedFutureASI/RecordedFutureASI.yml Docker image update
* Updated Metadata Of Pack Securonix
* Added release notes to pack Securonix
* Packs/Securonix/Integrations/Securonix/Securonix.yml Docker image update
* Updated Metadata Of Pack NetBox
* Added release notes to pack NetBox
* Packs/NetBox/Integrations/NetBoxEventCollector/NetBoxEventCollector.yml Docker image update
* Updated Metadata Of Pack SentinelOne
* Added release notes to pack SentinelOne
* Packs/SentinelOne/Integrations/SentinelOneEventCollector/SentinelOneEventCollector.yml Docker image update
* Updated Metadata Of Pack illuminate
* Added release notes to pack illuminate
* Packs/illuminate/Integrations/Analyst1/Analyst1.yml Docker image update
* Updated Metadata Of Pack DeHashed
* Added release notes to pack DeHashed
* Packs/DeHashed/Integrations/DeHashed/DeHashed.yml Docker image update
---
.../AtlassianConfluenceCloud/AtlassianConfluenceCloud.yml | 2 +-
Packs/AtlassianConfluenceCloud/ReleaseNotes/1_0_24.md | 3 +++
Packs/AtlassianConfluenceCloud/pack_metadata.json | 2 +-
Packs/DeHashed/Integrations/DeHashed/DeHashed.yml | 2 +-
Packs/DeHashed/ReleaseNotes/1_1_25.md | 3 +++
Packs/DeHashed/pack_metadata.json | 2 +-
.../DomainToolsIrisDetect/DomainToolsIrisDetect.yml | 2 +-
Packs/DomainToolsIrisDetect/ReleaseNotes/1_0_11.md | 3 +++
Packs/DomainToolsIrisDetect/pack_metadata.json | 2 +-
Packs/Gatewatcher-AionIQ/Integrations/GCenter/GCenter.yml | 2 +-
Packs/Gatewatcher-AionIQ/ReleaseNotes/1_1_20.md | 3 +++
Packs/Gatewatcher-AionIQ/pack_metadata.json | 2 +-
Packs/McAfeeNSM/Integrations/McAfeeNSMv2/McAfeeNSMv2.yml | 2 +-
Packs/McAfeeNSM/ReleaseNotes/1_2_16.md | 3 +++
Packs/McAfeeNSM/pack_metadata.json | 2 +-
.../Integrations/NetBoxEventCollector/NetBoxEventCollector.yml | 2 +-
Packs/NetBox/ReleaseNotes/1_0_17.md | 3 +++
Packs/NetBox/pack_metadata.json | 2 +-
.../Integrations/RecordedFutureASI/RecordedFutureASI.yml | 2 +-
Packs/RecordedFutureASI/ReleaseNotes/2_0_14.md | 3 +++
Packs/RecordedFutureASI/pack_metadata.json | 2 +-
Packs/Securonix/Integrations/Securonix/Securonix.yml | 2 +-
Packs/Securonix/ReleaseNotes/2_0_19.md | 3 +++
Packs/Securonix/pack_metadata.json | 2 +-
.../SentinelOneEventCollector/SentinelOneEventCollector.yml | 2 +-
Packs/SentinelOne/ReleaseNotes/3_2_21.md | 3 +++
Packs/SentinelOne/pack_metadata.json | 2 +-
Packs/illuminate/Integrations/Analyst1/Analyst1.yml | 2 +-
Packs/illuminate/ReleaseNotes/1_1_8.md | 3 +++
Packs/illuminate/pack_metadata.json | 2 +-
30 files changed, 50 insertions(+), 20 deletions(-)
create mode 100644 Packs/AtlassianConfluenceCloud/ReleaseNotes/1_0_24.md
create mode 100644 Packs/DeHashed/ReleaseNotes/1_1_25.md
create mode 100644 Packs/DomainToolsIrisDetect/ReleaseNotes/1_0_11.md
create mode 100644 Packs/Gatewatcher-AionIQ/ReleaseNotes/1_1_20.md
create mode 100644 Packs/McAfeeNSM/ReleaseNotes/1_2_16.md
create mode 100644 Packs/NetBox/ReleaseNotes/1_0_17.md
create mode 100644 Packs/RecordedFutureASI/ReleaseNotes/2_0_14.md
create mode 100644 Packs/Securonix/ReleaseNotes/2_0_19.md
create mode 100644 Packs/SentinelOne/ReleaseNotes/3_2_21.md
create mode 100644 Packs/illuminate/ReleaseNotes/1_1_8.md
diff --git a/Packs/AtlassianConfluenceCloud/Integrations/AtlassianConfluenceCloud/AtlassianConfluenceCloud.yml b/Packs/AtlassianConfluenceCloud/Integrations/AtlassianConfluenceCloud/AtlassianConfluenceCloud.yml
index 758df2f41e7e..0faaf6cabda5 100644
--- a/Packs/AtlassianConfluenceCloud/Integrations/AtlassianConfluenceCloud/AtlassianConfluenceCloud.yml
+++ b/Packs/AtlassianConfluenceCloud/Integrations/AtlassianConfluenceCloud/AtlassianConfluenceCloud.yml
@@ -1915,7 +1915,7 @@ script:
- contextPath: ConfluenceCloud.Group._links.self
description: Link to the group.
type: String
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/AtlassianConfluenceCloud/ReleaseNotes/1_0_24.md b/Packs/AtlassianConfluenceCloud/ReleaseNotes/1_0_24.md
new file mode 100644
index 000000000000..b52379b8a23d
--- /dev/null
+++ b/Packs/AtlassianConfluenceCloud/ReleaseNotes/1_0_24.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Atlassian Confluence Cloud
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/AtlassianConfluenceCloud/pack_metadata.json b/Packs/AtlassianConfluenceCloud/pack_metadata.json
index d00cb055a8e2..862ecd626a25 100644
--- a/Packs/AtlassianConfluenceCloud/pack_metadata.json
+++ b/Packs/AtlassianConfluenceCloud/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Atlassian Confluence Cloud",
"description": "Atlassian Confluence Cloud allows users to interact with confluence entities like content, space, users and groups. Users can also manage the space permissions.",
"support": "xsoar",
- "currentVersion": "1.0.23",
+ "currentVersion": "1.0.24",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/DeHashed/Integrations/DeHashed/DeHashed.yml b/Packs/DeHashed/Integrations/DeHashed/DeHashed.yml
index 675537c7f64d..c0906311829e 100644
--- a/Packs/DeHashed/Integrations/DeHashed/DeHashed.yml
+++ b/Packs/DeHashed/Integrations/DeHashed/DeHashed.yml
@@ -179,7 +179,7 @@ script:
- contextPath: DBotScore.Reliability
description: Reliability of the source providing the intelligence data.
type: String
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/DeHashed/ReleaseNotes/1_1_25.md b/Packs/DeHashed/ReleaseNotes/1_1_25.md
new file mode 100644
index 000000000000..871cb0d978f0
--- /dev/null
+++ b/Packs/DeHashed/ReleaseNotes/1_1_25.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### DeHashed
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/DeHashed/pack_metadata.json b/Packs/DeHashed/pack_metadata.json
index 872dd52e2c40..9d28344c2d2a 100644
--- a/Packs/DeHashed/pack_metadata.json
+++ b/Packs/DeHashed/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "DeHashed",
"description": "This integration allows you to check if your personal information such as your email, username, or password is being compromised.",
"support": "xsoar",
- "currentVersion": "1.1.24",
+ "currentVersion": "1.1.25",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/DomainToolsIrisDetect/Integrations/DomainToolsIrisDetect/DomainToolsIrisDetect.yml b/Packs/DomainToolsIrisDetect/Integrations/DomainToolsIrisDetect/DomainToolsIrisDetect.yml
index 215e25f84186..a736f4c956d1 100644
--- a/Packs/DomainToolsIrisDetect/Integrations/DomainToolsIrisDetect/DomainToolsIrisDetect.yml
+++ b/Packs/DomainToolsIrisDetect/Integrations/DomainToolsIrisDetect/DomainToolsIrisDetect.yml
@@ -1044,7 +1044,7 @@ script:
type: String
- description: This command will reset your fetch history.
name: domaintools-iris-detect-reset-fetch-indicators
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/DomainToolsIrisDetect/ReleaseNotes/1_0_11.md b/Packs/DomainToolsIrisDetect/ReleaseNotes/1_0_11.md
new file mode 100644
index 000000000000..217ca7caee2e
--- /dev/null
+++ b/Packs/DomainToolsIrisDetect/ReleaseNotes/1_0_11.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### DomainTools Iris Detect
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/DomainToolsIrisDetect/pack_metadata.json b/Packs/DomainToolsIrisDetect/pack_metadata.json
index a056185b9366..4c3c332391e8 100644
--- a/Packs/DomainToolsIrisDetect/pack_metadata.json
+++ b/Packs/DomainToolsIrisDetect/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "DomainTools Iris Detect",
"description": "Iris Detect protects against malicious domains impersonating your brands and supply chain.",
"support": "partner",
- "currentVersion": "1.0.10",
+ "currentVersion": "1.0.11",
"author": "DomainTools Integrations",
"url": "http://www.domaintools.com",
"email": "enterprisesupport@domaintools.com",
diff --git a/Packs/Gatewatcher-AionIQ/Integrations/GCenter/GCenter.yml b/Packs/Gatewatcher-AionIQ/Integrations/GCenter/GCenter.yml
index ee80881eabb3..3436a167bfe2 100644
--- a/Packs/Gatewatcher-AionIQ/Integrations/GCenter/GCenter.yml
+++ b/Packs/Gatewatcher-AionIQ/Integrations/GCenter/GCenter.yml
@@ -1312,7 +1312,7 @@ script:
script: '-'
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
fromversion: 6.2.0
tests:
- Gcenter Test Playbook
diff --git a/Packs/Gatewatcher-AionIQ/ReleaseNotes/1_1_20.md b/Packs/Gatewatcher-AionIQ/ReleaseNotes/1_1_20.md
new file mode 100644
index 000000000000..ef5a67a424cd
--- /dev/null
+++ b/Packs/Gatewatcher-AionIQ/ReleaseNotes/1_1_20.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### GCenter
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/Gatewatcher-AionIQ/pack_metadata.json b/Packs/Gatewatcher-AionIQ/pack_metadata.json
index 36a921d2e03b..c3387c6af759 100644
--- a/Packs/Gatewatcher-AionIQ/pack_metadata.json
+++ b/Packs/Gatewatcher-AionIQ/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Gatewatcher AionIQ",
"description": "This pack provide integration with Gatewatcher NDR solution : AIonIQ",
"support": "partner",
- "currentVersion": "1.1.19",
+ "currentVersion": "1.1.20",
"author": "Gatewatcher",
"url": "https://www.gatewatcher.com/",
"email": "integration@gatewatcher.com",
diff --git a/Packs/McAfeeNSM/Integrations/McAfeeNSMv2/McAfeeNSMv2.yml b/Packs/McAfeeNSM/Integrations/McAfeeNSMv2/McAfeeNSMv2.yml
index 0f469cbee0a0..85fb62e2d1ef 100644
--- a/Packs/McAfeeNSM/Integrations/McAfeeNSMv2/McAfeeNSMv2.yml
+++ b/Packs/McAfeeNSM/Integrations/McAfeeNSMv2/McAfeeNSMv2.yml
@@ -2045,7 +2045,7 @@ script:
script: '-'
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
fromversion: 6.5.0
tests:
- Test_McAfeeNSMv2_using_v9
diff --git a/Packs/McAfeeNSM/ReleaseNotes/1_2_16.md b/Packs/McAfeeNSM/ReleaseNotes/1_2_16.md
new file mode 100644
index 000000000000..c2e4341e3453
--- /dev/null
+++ b/Packs/McAfeeNSM/ReleaseNotes/1_2_16.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### McAfee NSM v2
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/McAfeeNSM/pack_metadata.json b/Packs/McAfeeNSM/pack_metadata.json
index 368918588d24..da60f8f9d38a 100644
--- a/Packs/McAfeeNSM/pack_metadata.json
+++ b/Packs/McAfeeNSM/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "McAfee NSM",
"description": "McAfee Network Security Manager",
"support": "xsoar",
- "currentVersion": "1.2.15",
+ "currentVersion": "1.2.16",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/NetBox/Integrations/NetBoxEventCollector/NetBoxEventCollector.yml b/Packs/NetBox/Integrations/NetBoxEventCollector/NetBoxEventCollector.yml
index f12869e45cfc..9b29c7b382cb 100644
--- a/Packs/NetBox/Integrations/NetBoxEventCollector/NetBoxEventCollector.yml
+++ b/Packs/NetBox/Integrations/NetBoxEventCollector/NetBoxEventCollector.yml
@@ -58,7 +58,7 @@ script:
name: limit
description: Gets events from NetBox.
name: netbox-get-events
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetchevents: true
script: '-'
subtype: python3
diff --git a/Packs/NetBox/ReleaseNotes/1_0_17.md b/Packs/NetBox/ReleaseNotes/1_0_17.md
new file mode 100644
index 000000000000..30e5c4f31c56
--- /dev/null
+++ b/Packs/NetBox/ReleaseNotes/1_0_17.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### NetBox Event Collector
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/NetBox/pack_metadata.json b/Packs/NetBox/pack_metadata.json
index ca8d7f51a653..2e3139cd6b87 100644
--- a/Packs/NetBox/pack_metadata.json
+++ b/Packs/NetBox/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "NetBox",
"description": "This is the NetBox event collector integration for XSIAM",
"support": "xsoar",
- "currentVersion": "1.0.16",
+ "currentVersion": "1.0.17",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/RecordedFutureASI/Integrations/RecordedFutureASI/RecordedFutureASI.yml b/Packs/RecordedFutureASI/Integrations/RecordedFutureASI/RecordedFutureASI.yml
index 4b623189ef4d..2cd8bf3c2738 100644
--- a/Packs/RecordedFutureASI/Integrations/RecordedFutureASI/RecordedFutureASI.yml
+++ b/Packs/RecordedFutureASI/Integrations/RecordedFutureASI/RecordedFutureASI.yml
@@ -77,7 +77,7 @@ script:
- name: expand_issues
description: true/false to make an incident per host & per new issue.
description: Gets the issues for a project from a particular snapshot (defaults to recent).
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
subtype: python3
fromversion: 6.5.0
diff --git a/Packs/RecordedFutureASI/ReleaseNotes/2_0_14.md b/Packs/RecordedFutureASI/ReleaseNotes/2_0_14.md
new file mode 100644
index 000000000000..a8c795914f9d
--- /dev/null
+++ b/Packs/RecordedFutureASI/ReleaseNotes/2_0_14.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Recorded Future Attack Surface Intelligence
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/RecordedFutureASI/pack_metadata.json b/Packs/RecordedFutureASI/pack_metadata.json
index 6bb72621ec73..1534038082e5 100644
--- a/Packs/RecordedFutureASI/pack_metadata.json
+++ b/Packs/RecordedFutureASI/pack_metadata.json
@@ -3,7 +3,7 @@
"prevName": "Recorded Future ASI",
"description": "Helps you take risk prioritization to the next level by helping you identify the biggest weaknesses within your attack surface.",
"support": "partner",
- "currentVersion": "2.0.13",
+ "currentVersion": "2.0.14",
"author": "Recorded Future",
"url": "",
"email": "support@recordedfuture.com",
diff --git a/Packs/Securonix/Integrations/Securonix/Securonix.yml b/Packs/Securonix/Integrations/Securonix/Securonix.yml
index 1da626cbdb21..265cbdb28437 100644
--- a/Packs/Securonix/Integrations/Securonix/Securonix.yml
+++ b/Packs/Securonix/Integrations/Securonix/Securonix.yml
@@ -1546,7 +1546,7 @@ script:
required: true
description: Deletes the entries from the lookup table.
name: securonix-lookup-table-entries-delete
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/Securonix/ReleaseNotes/2_0_19.md b/Packs/Securonix/ReleaseNotes/2_0_19.md
new file mode 100644
index 000000000000..dbf7bad0ab50
--- /dev/null
+++ b/Packs/Securonix/ReleaseNotes/2_0_19.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Securonix
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/Securonix/pack_metadata.json b/Packs/Securonix/pack_metadata.json
index 16707e559048..0a5c18a45c04 100644
--- a/Packs/Securonix/pack_metadata.json
+++ b/Packs/Securonix/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Securonix",
"description": "Use the Securonix integration to manage incidents, threats, lookup tables, whitelists and watchlists.",
"support": "partner",
- "currentVersion": "2.0.18",
+ "currentVersion": "2.0.19",
"author": "Securonix",
"url": "https://www.securonix.com",
"email": "support@securonix.com",
diff --git a/Packs/SentinelOne/Integrations/SentinelOneEventCollector/SentinelOneEventCollector.yml b/Packs/SentinelOne/Integrations/SentinelOneEventCollector/SentinelOneEventCollector.yml
index 44565878a681..e5cd27c26aab 100644
--- a/Packs/SentinelOne/Integrations/SentinelOneEventCollector/SentinelOneEventCollector.yml
+++ b/Packs/SentinelOne/Integrations/SentinelOneEventCollector/SentinelOneEventCollector.yml
@@ -72,7 +72,7 @@ script:
name: limit
description: Gets events from SentinelOne.
name: sentinelone-get-events
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetchevents: true
script: '-'
subtype: python3
diff --git a/Packs/SentinelOne/ReleaseNotes/3_2_21.md b/Packs/SentinelOne/ReleaseNotes/3_2_21.md
new file mode 100644
index 000000000000..12defbb398f1
--- /dev/null
+++ b/Packs/SentinelOne/ReleaseNotes/3_2_21.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### SentinelOne Event Collector
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/SentinelOne/pack_metadata.json b/Packs/SentinelOne/pack_metadata.json
index c289eeee9799..f3ecb46894a6 100644
--- a/Packs/SentinelOne/pack_metadata.json
+++ b/Packs/SentinelOne/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "SentinelOne",
"description": "Endpoint protection",
"support": "partner",
- "currentVersion": "3.2.20",
+ "currentVersion": "3.2.21",
"author": "SentinelOne",
"url": "https://www.sentinelone.com/support/",
"email": "support@sentinelone.com",
diff --git a/Packs/illuminate/Integrations/Analyst1/Analyst1.yml b/Packs/illuminate/Integrations/Analyst1/Analyst1.yml
index fcea93a36d0a..4c5d253433c3 100644
--- a/Packs/illuminate/Integrations/Analyst1/Analyst1.yml
+++ b/Packs/illuminate/Integrations/Analyst1/Analyst1.yml
@@ -746,7 +746,7 @@ script:
- contextPath: Analyst1.EvidenceStatus.processingComplete
description: True or false to indicate if processing of the Evidence upload is done. Determined by evaluating the id or message are present and populated. If an id is returned but blank, this is false, indicating the upload is still in progress.
description: Check on the status of the analyst1-evidence-submit action by using its output UUID.
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
subtype: python3
runonce: false
fromversion: 5.0.0
diff --git a/Packs/illuminate/ReleaseNotes/1_1_8.md b/Packs/illuminate/ReleaseNotes/1_1_8.md
new file mode 100644
index 000000000000..8ff5b58e8c3a
--- /dev/null
+++ b/Packs/illuminate/ReleaseNotes/1_1_8.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Analyst1
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/illuminate/pack_metadata.json b/Packs/illuminate/pack_metadata.json
index c1f94dda5dde..d1e7f40cfd4d 100644
--- a/Packs/illuminate/pack_metadata.json
+++ b/Packs/illuminate/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Analyst1",
"description": "This integration utilizes Analyst1's system to support multiple operations to assist the cyber analyst. These include intelligence collection from any source, deployment of configured indicator or signature sets for improved boundary/host defense, and enriching XSOAR indicators with data provided by the Analyst1 REST API, such as actor and malware information, activity and reported dates, evidence and hit counts, and more. For assistance with this app and any use cases please contact support@analyst1.com.",
"support": "partner",
- "currentVersion": "1.1.7",
+ "currentVersion": "1.1.8",
"author": "Analyst1",
"url": "",
"email": "support@analyst1.com",
From f1dc701e867861bac1d4fc422d5ed5cc67c642e0 Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Tue, 20 Feb 2024 09:05:02 +0200
Subject: [PATCH 031/272] Update Docker Image To demisto/googleapi-python3
(#33009)
* Updated Metadata Of Pack GSuiteAdmin
* Added release notes to pack GSuiteAdmin
* Packs/GSuiteAdmin/Integrations/GSuiteAdmin/GSuiteAdmin.yml Docker image update
* Updated Metadata Of Pack GoogleSheets
* Added release notes to pack GoogleSheets
* Packs/GoogleSheets/Integrations/GoogleSheets/GoogleSheets.yml Docker image update
* Updated Metadata Of Pack GoogleChronicleBackstory
* Added release notes to pack GoogleChronicleBackstory
* Packs/GoogleChronicleBackstory/Integrations/GoogleChronicleBackstory/GoogleChronicleBackstory.yml Docker image update
* Updated Metadata Of Pack GSuiteSecurityAlertCenter
* Added release notes to pack GSuiteSecurityAlertCenter
* Packs/GSuiteSecurityAlertCenter/Integrations/GSuiteSecurityAlertCenter/GSuiteSecurityAlertCenter.yml Docker image update
* Updated Metadata Of Pack GoogleDrive
* Added release notes to pack GoogleDrive
* Packs/GoogleDrive/Integrations/GoogleDrive/GoogleDrive.yml Docker image update
* Updated Metadata Of Pack GoogleCalendar
* Added release notes to pack GoogleCalendar
* Packs/GoogleCalendar/Integrations/GoogleCalendar/GoogleCalendar.yml Docker image update
---
Packs/GSuiteAdmin/Integrations/GSuiteAdmin/GSuiteAdmin.yml | 2 +-
Packs/GSuiteAdmin/ReleaseNotes/1_1_35.md | 3 +++
Packs/GSuiteAdmin/pack_metadata.json | 2 +-
.../GSuiteSecurityAlertCenter/GSuiteSecurityAlertCenter.yml | 2 +-
Packs/GSuiteSecurityAlertCenter/ReleaseNotes/1_1_42.md | 3 +++
Packs/GSuiteSecurityAlertCenter/pack_metadata.json | 2 +-
.../Integrations/GoogleCalendar/GoogleCalendar.yml | 2 +-
Packs/GoogleCalendar/ReleaseNotes/1_1_44.md | 3 +++
Packs/GoogleCalendar/pack_metadata.json | 2 +-
.../GoogleChronicleBackstory/GoogleChronicleBackstory.yml | 2 +-
Packs/GoogleChronicleBackstory/ReleaseNotes/3_1_2.md | 3 +++
Packs/GoogleChronicleBackstory/pack_metadata.json | 2 +-
Packs/GoogleDrive/Integrations/GoogleDrive/GoogleDrive.yml | 2 +-
Packs/GoogleDrive/ReleaseNotes/1_3_3.md | 3 +++
Packs/GoogleDrive/pack_metadata.json | 2 +-
Packs/GoogleSheets/Integrations/GoogleSheets/GoogleSheets.yml | 2 +-
Packs/GoogleSheets/ReleaseNotes/1_0_42.md | 3 +++
Packs/GoogleSheets/pack_metadata.json | 2 +-
18 files changed, 30 insertions(+), 12 deletions(-)
create mode 100644 Packs/GSuiteAdmin/ReleaseNotes/1_1_35.md
create mode 100644 Packs/GSuiteSecurityAlertCenter/ReleaseNotes/1_1_42.md
create mode 100644 Packs/GoogleCalendar/ReleaseNotes/1_1_44.md
create mode 100644 Packs/GoogleChronicleBackstory/ReleaseNotes/3_1_2.md
create mode 100644 Packs/GoogleDrive/ReleaseNotes/1_3_3.md
create mode 100644 Packs/GoogleSheets/ReleaseNotes/1_0_42.md
diff --git a/Packs/GSuiteAdmin/Integrations/GSuiteAdmin/GSuiteAdmin.yml b/Packs/GSuiteAdmin/Integrations/GSuiteAdmin/GSuiteAdmin.yml
index 2bd3d2727ec0..6f30062c5c6d 100644
--- a/Packs/GSuiteAdmin/Integrations/GSuiteAdmin/GSuiteAdmin.yml
+++ b/Packs/GSuiteAdmin/Integrations/GSuiteAdmin/GSuiteAdmin.yml
@@ -2229,7 +2229,7 @@ script:
- contextPath: GSuite.Group.nonEditableAliases
description: List of the group's non-editable alias email addresses that are outside of the account's primary domain or subdomains.
type: String
- dockerimage: demisto/googleapi-python3:1.0.0.86179
+ dockerimage: demisto/googleapi-python3:1.0.0.87804
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/GSuiteAdmin/ReleaseNotes/1_1_35.md b/Packs/GSuiteAdmin/ReleaseNotes/1_1_35.md
new file mode 100644
index 000000000000..5bfd59996574
--- /dev/null
+++ b/Packs/GSuiteAdmin/ReleaseNotes/1_1_35.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Google Workspace Admin
+- Updated the Docker image to: *demisto/googleapi-python3:1.0.0.87804*.
diff --git a/Packs/GSuiteAdmin/pack_metadata.json b/Packs/GSuiteAdmin/pack_metadata.json
index e967158ba738..137b8726f3cb 100644
--- a/Packs/GSuiteAdmin/pack_metadata.json
+++ b/Packs/GSuiteAdmin/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "G Suite Admin",
"description": "G Suite Admin integration with Cortex XSOAR. G Suite or Google Workspace Admin is an integration to perform an action on IT infrastructure, create users, update settings, and more administrative tasks.",
"support": "xsoar",
- "currentVersion": "1.1.34",
+ "currentVersion": "1.1.35",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/GSuiteSecurityAlertCenter/Integrations/GSuiteSecurityAlertCenter/GSuiteSecurityAlertCenter.yml b/Packs/GSuiteSecurityAlertCenter/Integrations/GSuiteSecurityAlertCenter/GSuiteSecurityAlertCenter.yml
index 560568651fcb..1d32875a8b1a 100644
--- a/Packs/GSuiteSecurityAlertCenter/Integrations/GSuiteSecurityAlertCenter/GSuiteSecurityAlertCenter.yml
+++ b/Packs/GSuiteSecurityAlertCenter/Integrations/GSuiteSecurityAlertCenter/GSuiteSecurityAlertCenter.yml
@@ -767,7 +767,7 @@ script:
- contextPath: GSuiteSecurityAlert.Recover.failedAlerts.status
description: Status of the failed alert recovery.
type: String
- dockerimage: demisto/googleapi-python3:1.0.0.86179
+ dockerimage: demisto/googleapi-python3:1.0.0.87804
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/GSuiteSecurityAlertCenter/ReleaseNotes/1_1_42.md b/Packs/GSuiteSecurityAlertCenter/ReleaseNotes/1_1_42.md
new file mode 100644
index 000000000000..0e3a9fdba6c3
--- /dev/null
+++ b/Packs/GSuiteSecurityAlertCenter/ReleaseNotes/1_1_42.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### G Suite Security Alert Center
+- Updated the Docker image to: *demisto/googleapi-python3:1.0.0.87804*.
diff --git a/Packs/GSuiteSecurityAlertCenter/pack_metadata.json b/Packs/GSuiteSecurityAlertCenter/pack_metadata.json
index 4ed5316d9829..4d080083f00c 100644
--- a/Packs/GSuiteSecurityAlertCenter/pack_metadata.json
+++ b/Packs/GSuiteSecurityAlertCenter/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "G Suite Security Alert Center",
"description": "Fetch alert types, delete or recover alerts, retrieve an alert's metadata, and create or view alert feedback.",
"support": "xsoar",
- "currentVersion": "1.1.41",
+ "currentVersion": "1.1.42",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/GoogleCalendar/Integrations/GoogleCalendar/GoogleCalendar.yml b/Packs/GoogleCalendar/Integrations/GoogleCalendar/GoogleCalendar.yml
index 6d4e31395ae8..15514490168f 100644
--- a/Packs/GoogleCalendar/Integrations/GoogleCalendar/GoogleCalendar.yml
+++ b/Packs/GoogleCalendar/Integrations/GoogleCalendar/GoogleCalendar.yml
@@ -173,7 +173,7 @@ script:
- contextPath: GoogleCalendar.PageToken.Acl.nextSyncToken
description: Token used at a later point in time to retrieve only the entries that have changed since this result was returned.
type: String
- dockerimage: demisto/googleapi-python3:1.0.0.86179
+ dockerimage: demisto/googleapi-python3:1.0.0.87804
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/GoogleCalendar/ReleaseNotes/1_1_44.md b/Packs/GoogleCalendar/ReleaseNotes/1_1_44.md
new file mode 100644
index 000000000000..8786d4c06422
--- /dev/null
+++ b/Packs/GoogleCalendar/ReleaseNotes/1_1_44.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Google Calendar
+- Updated the Docker image to: *demisto/googleapi-python3:1.0.0.87804*.
diff --git a/Packs/GoogleCalendar/pack_metadata.json b/Packs/GoogleCalendar/pack_metadata.json
index bb6ecdddeeaf..57ab053d7b5c 100644
--- a/Packs/GoogleCalendar/pack_metadata.json
+++ b/Packs/GoogleCalendar/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Calendar",
"description": "Google Calendar integration with Cortex XSOAR.",
"support": "xsoar",
- "currentVersion": "1.1.43",
+ "currentVersion": "1.1.44",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/GoogleChronicleBackstory/Integrations/GoogleChronicleBackstory/GoogleChronicleBackstory.yml b/Packs/GoogleChronicleBackstory/Integrations/GoogleChronicleBackstory/GoogleChronicleBackstory.yml
index e3e2efe5480b..6b4061d728ef 100644
--- a/Packs/GoogleChronicleBackstory/Integrations/GoogleChronicleBackstory/GoogleChronicleBackstory.yml
+++ b/Packs/GoogleChronicleBackstory/Integrations/GoogleChronicleBackstory/GoogleChronicleBackstory.yml
@@ -6698,7 +6698,7 @@ script:
- contextPath: GoogleChronicleBackstory.Events.securityResult.urlBackToProduct
description: URL to direct you to the source product console for this security event.
type: String
- dockerimage: demisto/googleapi-python3:1.0.0.86179
+ dockerimage: demisto/googleapi-python3:1.0.0.87804
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/GoogleChronicleBackstory/ReleaseNotes/3_1_2.md b/Packs/GoogleChronicleBackstory/ReleaseNotes/3_1_2.md
new file mode 100644
index 000000000000..31ae40093a33
--- /dev/null
+++ b/Packs/GoogleChronicleBackstory/ReleaseNotes/3_1_2.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Chronicle
+- Updated the Docker image to: *demisto/googleapi-python3:1.0.0.87804*.
diff --git a/Packs/GoogleChronicleBackstory/pack_metadata.json b/Packs/GoogleChronicleBackstory/pack_metadata.json
index 6cbd6cbfacc7..302195ec5a5c 100644
--- a/Packs/GoogleChronicleBackstory/pack_metadata.json
+++ b/Packs/GoogleChronicleBackstory/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Chronicle",
"description": "Retrieve Chronicle detections, impacted assets, IOC matches, and 3P alerts to enrich your XSOAR workflows.",
"support": "partner",
- "currentVersion": "3.1.1",
+ "currentVersion": "3.1.2",
"certification": "certified",
"author": "Chronicle",
"url": "https://go.chronicle.security/contact",
diff --git a/Packs/GoogleDrive/Integrations/GoogleDrive/GoogleDrive.yml b/Packs/GoogleDrive/Integrations/GoogleDrive/GoogleDrive.yml
index f140d1a75350..3b07628af964 100644
--- a/Packs/GoogleDrive/Integrations/GoogleDrive/GoogleDrive.yml
+++ b/Packs/GoogleDrive/Integrations/GoogleDrive/GoogleDrive.yml
@@ -3103,7 +3103,7 @@ script:
- contextPath: GoogleDrive.File.Parents
description: The IDs of the parent folders which contain the file.
type: String
- dockerimage: demisto/googleapi-python3:1.0.0.86179
+ dockerimage: demisto/googleapi-python3:1.0.0.87804
isfetch: true
runonce: false
script: "-"
diff --git a/Packs/GoogleDrive/ReleaseNotes/1_3_3.md b/Packs/GoogleDrive/ReleaseNotes/1_3_3.md
new file mode 100644
index 000000000000..8403a7e195d1
--- /dev/null
+++ b/Packs/GoogleDrive/ReleaseNotes/1_3_3.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Google Drive
+- Updated the Docker image to: *demisto/googleapi-python3:1.0.0.87804*.
diff --git a/Packs/GoogleDrive/pack_metadata.json b/Packs/GoogleDrive/pack_metadata.json
index 59b0efe67385..f528342fa6ce 100644
--- a/Packs/GoogleDrive/pack_metadata.json
+++ b/Packs/GoogleDrive/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Drive",
"description": "Google Drive allows users to store files on their servers, synchronize files across devices, and share files. This integration helps you to create a new drive, query past activity and view change logs performed by the users, as well as list drives and files, and manage their permissions.",
"support": "xsoar",
- "currentVersion": "1.3.2",
+ "currentVersion": "1.3.3",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/GoogleSheets/Integrations/GoogleSheets/GoogleSheets.yml b/Packs/GoogleSheets/Integrations/GoogleSheets/GoogleSheets.yml
index 599dff95d47c..681a63cc15d0 100644
--- a/Packs/GoogleSheets/Integrations/GoogleSheets/GoogleSheets.yml
+++ b/Packs/GoogleSheets/Integrations/GoogleSheets/GoogleSheets.yml
@@ -665,7 +665,7 @@ script:
- contextPath: GoogleSheets.Spreadsheet.updatedSpreadsheet.sheets.title
description: Sheet title.
type: String
- dockerimage: demisto/googleapi-python3:1.0.0.86179
+ dockerimage: demisto/googleapi-python3:1.0.0.87804
runonce: false
script: "-"
subtype: python3
diff --git a/Packs/GoogleSheets/ReleaseNotes/1_0_42.md b/Packs/GoogleSheets/ReleaseNotes/1_0_42.md
new file mode 100644
index 000000000000..2648c427c005
--- /dev/null
+++ b/Packs/GoogleSheets/ReleaseNotes/1_0_42.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Google Sheets
+- Updated the Docker image to: *demisto/googleapi-python3:1.0.0.87804*.
diff --git a/Packs/GoogleSheets/pack_metadata.json b/Packs/GoogleSheets/pack_metadata.json
index 5df81408c64f..f1fcd368506b 100644
--- a/Packs/GoogleSheets/pack_metadata.json
+++ b/Packs/GoogleSheets/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Sheets",
"description": "The Google Sheets API is a RESTful interface that lets you read and modify a spreadsheet's data. The most common uses of this API include the following tasks- create spreadsheets, read and write spreadsheets cells, update spreadsheet formatting",
"support": "xsoar",
- "currentVersion": "1.0.41",
+ "currentVersion": "1.0.42",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From b8c5256890c64bcb6ff7706b5b4ea913dbd28d18 Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Tue, 20 Feb 2024 09:07:25 +0200
Subject: [PATCH 032/272] Update Docker Image To demisto/btfl-soup (#33010)
* Updated Metadata Of Pack EmailCommunication
* Added release notes to pack EmailCommunication
* Packs/EmailCommunication/Scripts/DisplayEmailHtmlThread/DisplayEmailHtmlThread.yml Docker image update
---
Packs/EmailCommunication/ReleaseNotes/2_0_25.md | 4 ++++
.../Scripts/DisplayEmailHtmlThread/DisplayEmailHtmlThread.yml | 2 +-
Packs/EmailCommunication/pack_metadata.json | 2 +-
3 files changed, 6 insertions(+), 2 deletions(-)
create mode 100644 Packs/EmailCommunication/ReleaseNotes/2_0_25.md
diff --git a/Packs/EmailCommunication/ReleaseNotes/2_0_25.md b/Packs/EmailCommunication/ReleaseNotes/2_0_25.md
new file mode 100644
index 000000000000..f5c98b7a69a6
--- /dev/null
+++ b/Packs/EmailCommunication/ReleaseNotes/2_0_25.md
@@ -0,0 +1,4 @@
+
+#### Scripts
+##### DisplayEmailHtmlThread
+- Updated the Docker image to: *demisto/btfl-soup:1.0.1.87353*.
\ No newline at end of file
diff --git a/Packs/EmailCommunication/Scripts/DisplayEmailHtmlThread/DisplayEmailHtmlThread.yml b/Packs/EmailCommunication/Scripts/DisplayEmailHtmlThread/DisplayEmailHtmlThread.yml
index ae84113cc0d1..60a9d52bbbda 100644
--- a/Packs/EmailCommunication/Scripts/DisplayEmailHtmlThread/DisplayEmailHtmlThread.yml
+++ b/Packs/EmailCommunication/Scripts/DisplayEmailHtmlThread/DisplayEmailHtmlThread.yml
@@ -12,7 +12,7 @@ comment: |-
enabled: true
scripttarget: 0
subtype: python3
-dockerimage: demisto/btfl-soup:1.0.1.84814
+dockerimage: demisto/btfl-soup:1.0.1.87353
runas: DBotWeakRole
fromversion: 6.2.0
tests:
diff --git a/Packs/EmailCommunication/pack_metadata.json b/Packs/EmailCommunication/pack_metadata.json
index 426d51ca0886..8cf8a4722aa4 100644
--- a/Packs/EmailCommunication/pack_metadata.json
+++ b/Packs/EmailCommunication/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Email Communication",
"description": "Do you have to send multiple emails to end users? This content pack helps you streamline the process and automate updates, notifications and more.\n",
"support": "xsoar",
- "currentVersion": "2.0.24",
+ "currentVersion": "2.0.25",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"videos": [
From f5821aec1ebef21ae90600fb50e3a05eb6bd78b9 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 10:14:29 +0200
Subject: [PATCH 033/272] update docker + RN (#32995)
---
.../Integrations/Elasticsearch_v2/Elasticsearch_v2.yml | 2 +-
Packs/Elasticsearch/ReleaseNotes/1_3_20.md | 6 ++++++
Packs/Elasticsearch/pack_metadata.json | 2 +-
.../Integrations/FeedElasticsearch/FeedElasticsearch.yml | 2 +-
Packs/FeedElasticsearch/ReleaseNotes/1_1_4.md | 6 ++++++
Packs/FeedElasticsearch/pack_metadata.json | 2 +-
6 files changed, 16 insertions(+), 4 deletions(-)
create mode 100644 Packs/Elasticsearch/ReleaseNotes/1_3_20.md
create mode 100644 Packs/FeedElasticsearch/ReleaseNotes/1_1_4.md
diff --git a/Packs/Elasticsearch/Integrations/Elasticsearch_v2/Elasticsearch_v2.yml b/Packs/Elasticsearch/Integrations/Elasticsearch_v2/Elasticsearch_v2.yml
index b05eaf7bbb15..fba0774cad6b 100644
--- a/Packs/Elasticsearch/Integrations/Elasticsearch_v2/Elasticsearch_v2.yml
+++ b/Packs/Elasticsearch/Integrations/Elasticsearch_v2/Elasticsearch_v2.yml
@@ -381,7 +381,7 @@ script:
description: The result of the index operation.
type: string
description: Indexes a document into an Elasticsearch index.
- dockerimage: demisto/elasticsearch:1.0.0.85878
+ dockerimage: demisto/elasticsearch:1.0.0.87483
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/Elasticsearch/ReleaseNotes/1_3_20.md b/Packs/Elasticsearch/ReleaseNotes/1_3_20.md
new file mode 100644
index 000000000000..bfda7a04233e
--- /dev/null
+++ b/Packs/Elasticsearch/ReleaseNotes/1_3_20.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Elasticsearch v2
+
+- Updated the Docker image to: *demisto/elasticsearch:1.0.0.87483*.
diff --git a/Packs/Elasticsearch/pack_metadata.json b/Packs/Elasticsearch/pack_metadata.json
index 8c7de67f71cf..5aa29cd759c7 100644
--- a/Packs/Elasticsearch/pack_metadata.json
+++ b/Packs/Elasticsearch/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Elasticsearch",
"description": "Search for and analyze data in real time. \n Supports version 6 and later.",
"support": "xsoar",
- "currentVersion": "1.3.19",
+ "currentVersion": "1.3.20",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch.yml b/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch.yml
index cd7156ad38a1..4f036fc394ca 100644
--- a/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch.yml
+++ b/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch.yml
@@ -172,7 +172,7 @@ script:
required: true
description: Gets indicators available in the configured Elasticsearch database.
name: es-get-indicators
- dockerimage: demisto/elasticsearch:1.0.0.83352
+ dockerimage: demisto/elasticsearch:1.0.0.87483
feed: true
runonce: false
script: '-'
diff --git a/Packs/FeedElasticsearch/ReleaseNotes/1_1_4.md b/Packs/FeedElasticsearch/ReleaseNotes/1_1_4.md
new file mode 100644
index 000000000000..9a47e58a0247
--- /dev/null
+++ b/Packs/FeedElasticsearch/ReleaseNotes/1_1_4.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Elasticsearch Feed
+
+- Updated the Docker image to: *demisto/elasticsearch:1.0.0.87483*.
diff --git a/Packs/FeedElasticsearch/pack_metadata.json b/Packs/FeedElasticsearch/pack_metadata.json
index 39a575efb118..120f74204d14 100644
--- a/Packs/FeedElasticsearch/pack_metadata.json
+++ b/Packs/FeedElasticsearch/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Elasticsearch Feed",
"description": "Indicators feed from Elasticsearch database",
"support": "xsoar",
- "currentVersion": "1.1.3",
+ "currentVersion": "1.1.4",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 4238d8f8ad6908d85f0cb47b7935c6763952a42f Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 10:15:04 +0200
Subject: [PATCH 034/272] update docker + RN (#32996)
---
Packs/GenericSQL/Integrations/GenericSQL/GenericSQL.yml | 2 +-
Packs/GenericSQL/ReleaseNotes/1_1_7.md | 6 ++++++
Packs/GenericSQL/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/GenericSQL/ReleaseNotes/1_1_7.md
diff --git a/Packs/GenericSQL/Integrations/GenericSQL/GenericSQL.yml b/Packs/GenericSQL/Integrations/GenericSQL/GenericSQL.yml
index 30549611468b..4ddc1ba476d1 100644
--- a/Packs/GenericSQL/Integrations/GenericSQL/GenericSQL.yml
+++ b/Packs/GenericSQL/Integrations/GenericSQL/GenericSQL.yml
@@ -159,7 +159,7 @@ script:
name: bind_variables_values
description: Running a sql query
name: sql-command
- dockerimage: demisto/genericsql:1.1.0.87288
+ dockerimage: demisto/genericsql:1.1.0.87817
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/GenericSQL/ReleaseNotes/1_1_7.md b/Packs/GenericSQL/ReleaseNotes/1_1_7.md
new file mode 100644
index 000000000000..6deed8d88996
--- /dev/null
+++ b/Packs/GenericSQL/ReleaseNotes/1_1_7.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Generic SQL
+
+- Updated the Docker image to: *demisto/genericsql:1.1.0.87817*.
diff --git a/Packs/GenericSQL/pack_metadata.json b/Packs/GenericSQL/pack_metadata.json
index 7e800620f6b2..21b7cee151d0 100644
--- a/Packs/GenericSQL/pack_metadata.json
+++ b/Packs/GenericSQL/pack_metadata.json
@@ -3,7 +3,7 @@
"description": "Connect and execute sql queries in 4 Databases: MySQL, PostgreSQL, Microsoft SQL Server and Oracle",
"support": "xsoar",
"serverMinVersion": "5.0.0",
- "currentVersion": "1.1.6",
+ "currentVersion": "1.1.7",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 031d0b394f57751551f2681166b178eeebc8e8e2 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 10:15:39 +0200
Subject: [PATCH 035/272] update docker + RN (#32999)
---
Packs/PAN-OS/Integrations/Panorama/Panorama.yml | 2 +-
Packs/PAN-OS/ReleaseNotes/2_1_21.md | 6 ++++++
Packs/PAN-OS/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/PAN-OS/ReleaseNotes/2_1_21.md
diff --git a/Packs/PAN-OS/Integrations/Panorama/Panorama.yml b/Packs/PAN-OS/Integrations/Panorama/Panorama.yml
index 3f06e3bf9f7f..b4f78830a80f 100644
--- a/Packs/PAN-OS/Integrations/Panorama/Panorama.yml
+++ b/Packs/PAN-OS/Integrations/Panorama/Panorama.yml
@@ -9368,7 +9368,7 @@ script:
description: The job ID to use when polling.
description: Exports a tech support file (TSF).
polling: true
- dockerimage: demisto/pan-os-python:1.0.0.85910
+ dockerimage: demisto/pan-os-python:1.0.0.87401
isfetch: true
runonce: false
script: ''
diff --git a/Packs/PAN-OS/ReleaseNotes/2_1_21.md b/Packs/PAN-OS/ReleaseNotes/2_1_21.md
new file mode 100644
index 000000000000..54e6c97c674b
--- /dev/null
+++ b/Packs/PAN-OS/ReleaseNotes/2_1_21.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Palo Alto Networks PAN-OS
+
+- Updated the Docker image to: *demisto/pan-os-python:1.0.0.87401*.
diff --git a/Packs/PAN-OS/pack_metadata.json b/Packs/PAN-OS/pack_metadata.json
index c1df639e6830..5382494f2859 100644
--- a/Packs/PAN-OS/pack_metadata.json
+++ b/Packs/PAN-OS/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "PAN-OS by Palo Alto Networks",
"description": "Manage Palo Alto Networks Firewall and Panorama. Use this pack to manage Prisma Access through Panorama. For more information see Panorama documentation.",
"support": "xsoar",
- "currentVersion": "2.1.20",
+ "currentVersion": "2.1.21",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From b6bd2fb5f120a1766e6e6e30043694f8e98a015d Mon Sep 17 00:00:00 2001
From: samuelFain <65926551+samuelFain@users.noreply.github.com>
Date: Tue, 20 Feb 2024 10:34:46 +0200
Subject: [PATCH 036/272] [Okta Event Collector] Add next pagination token
logic (#32393)
* Update last fetch logic
* Implemented 'next' pagination token logic
* Handle resetting next_link token
* Update release notes
* FIxed failing UTs
* Remove pragma no cover
* Rename 3_2_10.md to 3_2_12.md
* add 3_2_10.md
* Add UTs
* Add UTs
---
.../OktaEventCollector/OktaEventCollector.py | 101 ++++++++++++------
.../OktaEventCollector_test.py | 82 ++++++++++++--
Packs/Okta/ReleaseNotes/3_2_12.md | 7 ++
Packs/Okta/pack_metadata.json | 2 +-
4 files changed, 146 insertions(+), 46 deletions(-)
create mode 100644 Packs/Okta/ReleaseNotes/3_2_12.md
diff --git a/Packs/Okta/Integrations/OktaEventCollector/OktaEventCollector.py b/Packs/Okta/Integrations/OktaEventCollector/OktaEventCollector.py
index 3efff82c4949..93a4cb78de37 100644
--- a/Packs/Okta/Integrations/OktaEventCollector/OktaEventCollector.py
+++ b/Packs/Okta/Integrations/OktaEventCollector/OktaEventCollector.py
@@ -1,6 +1,8 @@
-from CommonServerPython import *
from http import HTTPStatus
from typing import cast
+
+from CommonServerPython import *
+
VENDOR = "okta"
PRODUCT = "okta"
FETCH_LIMIT = 1000
@@ -16,17 +18,21 @@ def __init__(self, base_url, api_key, verify=True, proxy=False):
}
super().__init__(base_url=base_url, headers=headers, verify=verify, proxy=proxy)
- def get_events(self, since: int, limit: int = FETCH_LIMIT):
- params = {
- "sortOrder": "ASCENDING",
- "since": since,
- "limit": limit,
- }
- return self._http_request(url_suffix='/api/v1/logs', method='GET', headers=self._headers, params=params)
+ def get_events(self, since: int, limit: int = FETCH_LIMIT, next_link_url: str = ''):
+ if next_link_url:
+ return self._http_request(full_url=next_link_url, method='GET', headers=self._headers, resp_type='response')
+ else:
+ params = {
+ "sortOrder": "ASCENDING",
+ "since": since,
+ "limit": limit,
+ }
+ return self._http_request(url_suffix='/api/v1/logs', method='GET', headers=self._headers, params=params,
+ resp_type='response')
def get_events_command(client: Client, total_events_to_fetch, since,
- last_object_ids: List[str] = None) -> tuple[List[dict], int]: # pragma: no cover
+ last_object_ids: list[str] = [], next_link: str = '') -> tuple[list[dict], int, str]:
"""
Fetches events from the okta api until the total_events_to_fetch is reached or no more events are available.
if 429:TOO_MANY_REQUESTS is returned, will return the stored_events so far and the x-rate-limit-reset
@@ -44,24 +50,35 @@ def get_events_command(client: Client, total_events_to_fetch, since,
stored_events: list = []
num_of_events_to_fetch = FETCH_LIMIT if total_events_to_fetch > FETCH_LIMIT else total_events_to_fetch
demisto.debug(f"num of events to fetch: {num_of_events_to_fetch} since: {since}")
- while len(stored_events) < total_events_to_fetch:
+ should_continue = True
+ while len(stored_events) < total_events_to_fetch and should_continue:
demisto.debug(f"stored_events collected: {len(stored_events)}")
try:
- events = client.get_events(since=since, limit=num_of_events_to_fetch) # type: ignore
- if events:
+ if next_link:
+ demisto.debug("Running get_events using next_link")
+ response = client.get_events(since=since, limit=num_of_events_to_fetch, next_link_url=next_link) # type: ignore
+ else:
+ demisto.debug("Running get_events using since")
+ response = client.get_events(since=since, limit=num_of_events_to_fetch) # type: ignore
+
+ if events := json.loads(response.text):
demisto.debug(f'received {len(events)} number of events.')
+ if len(events) < num_of_events_to_fetch:
+ demisto.debug(f"Number of events collected is smaller than: {num_of_events_to_fetch} \
+ will stop after current fetch.")
+ should_continue = False
since = events[-1]['published']
if last_object_ids:
events = remove_duplicates(events, last_object_ids) # type: ignore
+ demisto.debug(f'Number of events after dedup {len(events)}')
if not events:
- demisto.debug('Events are empty after dedup will break.')
+ demisto.debug('Events are empty after dedup - will break. Resetting next_link token.')
+ next_link = ''
break
stored_events.extend(events)
- if len(events) < num_of_events_to_fetch:
- demisto.debug(f"Number of events collected is smaller than: {num_of_events_to_fetch} will break.")
- break
else:
- demisto.debug('Didnt receive any events from the api.')
+ demisto.debug('Didnt receive any events from the api. Resetting next_link token.')
+ next_link = ''
break
except DemistoException as exc:
msg = f'something went wrong: {exc}'
@@ -74,14 +91,22 @@ def get_events_command(client: Client, total_events_to_fetch, since,
demisto.debug(f'fetch-events Got 429. okta rate limit headers:\n \
x-rate-limit-remaining: {res.headers["x-rate-limit-remaining"]}\n \
x-rate-limit-reset: {res.headers["x-rate-limit-reset"]}\n')
- return stored_events, int(res.headers['x-rate-limit-reset'])
- return stored_events, 0
+ return stored_events, int(res.headers['x-rate-limit-reset']), next_link
+ return stored_events, 0, next_link
except Exception as exc:
demisto.error(f'Unexpected error.\n{traceback.format_exc()}')
if len(stored_events) == 0:
raise exc
- return stored_events, 0
- return stored_events, 0
+ return stored_events, 0, next_link
+
+ if url := response.links.get('next'):
+ next_link = url.get('url')
+ demisto.debug("next next_link url found and set as current next_link")
+ else:
+ next_link = ''
+ demisto.debug("next_link set to empty value")
+
+ return stored_events, 0, next_link
def remove_duplicates(events: list, ids: list) -> list:
@@ -91,9 +116,13 @@ def remove_duplicates(events: list, ids: list) -> list:
return [event for event in events if event['uuid'] not in ids]
-def get_last_run(events: List[dict], last_run_after) -> dict:
+def get_last_run(events: List[dict], last_run_after, next_link) -> dict:
"""
- Get the info from the last run, it returns the time to query from and a list of ids to prevent duplications
+ Build the last_run dictionary for the next fetch:
+ it returns 3 keys:
+ - after: the time to query from.
+ - ids: a list of ids to prevent duplications.
+ - next_link: a string representing the next request link if available, or an empty string if not.
"""
ids = []
# gets the last event time
@@ -103,19 +132,21 @@ def get_last_run(events: List[dict], last_run_after) -> dict:
break
ids.append(event.get('uuid'))
last_time = datetime.strptime(str(last_time).lower().replace('z', ''), '%Y-%m-%dt%H:%M:%S.%f')
- return {'after': last_time.isoformat(), 'ids': ids}
+ return {'after': last_time.isoformat(), 'ids': ids, 'next_link': next_link}
def fetch_events(client: Client,
start_time_epoch: int,
events_limit: int,
last_run_after,
- last_object_ids: List[str] = None) -> List[dict]: # pragma: no cover
+ last_object_ids: list[str] = [],
+ next_link: str = '') -> tuple[list[dict], str]:
while True:
- events, epoch_time_to_continue_fetch = get_events_command(client=client,
- total_events_to_fetch=events_limit,
- since=last_run_after,
- last_object_ids=last_object_ids)
+ events, epoch_time_to_continue_fetch, next_link = get_events_command(client=client,
+ total_events_to_fetch=events_limit,
+ since=last_run_after,
+ last_object_ids=last_object_ids,
+ next_link=next_link)
if epoch_time_to_continue_fetch == 0:
break
@@ -126,7 +157,7 @@ def fetch_events(client: Client,
time.sleep(sleep_time) # pylint: disable=E9003
else:
break
- return events
+ return events, next_link
def main(): # pragma: no cover
@@ -150,7 +181,7 @@ def main(): # pragma: no cover
if command == 'okta-get-events':
after = cast(datetime, dateparser.parse(demisto_args.get('from_date').strip()))
- events, _ = get_events_command(client, events_limit, since=after.isoformat())
+ events, _, _ = get_events_command(client, events_limit, since=after.isoformat())
command_results = CommandResults(
readable_output=tableToMarkdown('Okta Logs', events, headerTransform=pascalToSpace),
raw_response=events,
@@ -164,15 +195,17 @@ def main(): # pragma: no cover
after = cast(datetime, dateparser.parse(demisto_params['after'].strip()))
last_run = demisto.getLastRun()
last_object_ids = last_run.get('ids')
+ next_link = last_run.get('next_link')
if 'after' not in last_run:
last_run_after = after.isoformat() # type: ignore
else:
last_run_after = last_run['after']
- events = fetch_events(client, start_time_epoch, events_limit,
- last_run_after=last_run_after, last_object_ids=last_object_ids)
+ demisto.debug(f'{last_run=}')
+ events, next_link = fetch_events(client, start_time_epoch, events_limit,
+ last_run_after=last_run_after, last_object_ids=last_object_ids, next_link=next_link)
demisto.debug(f'sending_events_to_xsiam: {len(events)}')
send_events_to_xsiam(events[:events_limit], vendor=VENDOR, product=PRODUCT)
- demisto.setLastRun(get_last_run(events, last_run_after))
+ demisto.setLastRun(get_last_run(events, last_run_after, next_link))
except Exception as e:
return_error(f'Failed to execute {demisto.command()} command. Error: {str(e)}')
diff --git a/Packs/Okta/Integrations/OktaEventCollector/OktaEventCollector_test.py b/Packs/Okta/Integrations/OktaEventCollector/OktaEventCollector_test.py
index 99c6edb77a02..da96791f0dfe 100644
--- a/Packs/Okta/Integrations/OktaEventCollector/OktaEventCollector_test.py
+++ b/Packs/Okta/Integrations/OktaEventCollector/OktaEventCollector_test.py
@@ -1,13 +1,25 @@
-from OktaEventCollector import Client, remove_duplicates, get_last_run, get_events_command, main
-import pytest
from unittest.mock import MagicMock
+
+import pytest
from freezegun import freeze_time
+from OktaEventCollector import Client, DemistoException, fetch_events, get_events_command, get_last_run, main, remove_duplicates
+
import demistomock as demisto
-id1_pub = [[{'uuid': 'a5b57ec5feaa', 'published': '2022-04-17T12:32:36.667'}]]
+
+class MockResponse:
+ def __init__(self, data=None, text='', status_code=200, links={}):
+ self.data = data
+ self.text = str(data) if data else text
+ self.status_code = status_code
+ self.links = links
+
+
+id1_pub = '[{"uuid": "a5b57ec5feaa", "published": "2022-04-17T12:32:36.667"}]'
id2_pub = [{'uuid': 'a5b57ec5febb', 'published': '2022-04-17T12:32:36.667'}]
id3_pub = [{'uuid': 'a5b57ec5fecc', 'published': '2022-04-17T12:32:36.667'}]
id4_pub = [{'uuid': 'a5b57ec5fedd', 'published': '2022-04-17T12:32:36.667'}]
+empty_response = '[]'
id1 = {'uuid': 'a5b57ec5febb'}
id2 = {'uuid': 'a5b57ec5fecc'}
@@ -46,7 +58,7 @@ def test_remove_duplicates(events, ids, result):
{'published': '2022-04-17T12:33:36.667',
'uuid': '1d0844b6-3148-11ec-9027-a5b57ec5fccc'}],
'2022-04-17T11:30:00.000',
- {'after': '2022-04-17T12:33:36.667000', 'ids': ['1d0844b6-3148-11ec-9027-a5b57ec5fccc']}),
+ {'after': '2022-04-17T12:33:36.667000', 'ids': ['1d0844b6-3148-11ec-9027-a5b57ec5fccc'], 'next_link': ''}),
([{'published': '2022-04-17T12:31:36.667',
'uuid': '1d0844b6-3148-11ec-9027-a5b57ec5faaa'},
{'published': '2022-04-17T12:32:36.667',
@@ -56,12 +68,12 @@ def test_remove_duplicates(events, ids, result):
'2022-04-17T11:30:00.000',
{'after': '2022-04-17T12:32:36.667000',
'ids': ['1d0844b6-3148-11ec-9027-a5b57ec5fccc',
- '1d0844b6-3148-11ec-9027-a5b57ec5fbbb']}),
+ '1d0844b6-3148-11ec-9027-a5b57ec5fbbb'], 'next_link': ''}),
([],
'2022-04-17T12:31:36.667',
- {'after': '2022-04-17T12:31:36.667000', 'ids': []})])
+ {'after': '2022-04-17T12:31:36.667000', 'ids': [], 'next_link': ''})])
def test_get_last_run(events, last_run_after, result):
- assert get_last_run(events, last_run_after) == result
+ assert get_last_run(events, last_run_after, next_link='') == result
def test_get_events_success(dummy_client, mocker):
@@ -69,19 +81,67 @@ def test_get_events_success(dummy_client, mocker):
mock_remove_duplicates.return_value = [{'id': 1,
'published': '2022-04-17T12:32:36.667'}]
mocker.patch('OktaEventCollector.remove_duplicates', mock_remove_duplicates)
- mocker.patch.object(dummy_client, 'get_events', side_effect=id1_pub)
- events, epoch = get_events_command(dummy_client, 1, 'since', ['id1'])
+ mocker.patch.object(dummy_client, 'get_events', side_effect=[MockResponse(text=id1_pub)])
+ events, epoch, _ = get_events_command(dummy_client, 1, 'since', ['id1'])
assert len(events) == 1
assert epoch == 0
+def test_get_events_with_next_link_success(dummy_client, mocker):
+ mock_remove_duplicates = MagicMock()
+ mock_remove_duplicates.return_value = [{'id': 1,
+ 'published': '2022-04-17T12:32:36.667'}]
+ mocker.patch('OktaEventCollector.remove_duplicates', mock_remove_duplicates)
+ mocker.patch.object(dummy_client, 'get_events', side_effect=[
+ MockResponse(text=id1_pub, links={'next': {'url': 'next_link'}})])
+ events, epoch, next_link = get_events_command(dummy_client, 1, 'since', ['id1'], next_link='next_link')
+ assert len(events) == 1
+ assert epoch == 0
+ assert next_link == 'next_link'
+
+
def test_get_events_no_events(dummy_client, mocker):
- mocker.patch.object(dummy_client, 'get_events', return_value=None)
- events, epoch = get_events_command(dummy_client, 1, 'since')
+ mocker.patch.object(dummy_client, 'get_events', side_effect=[MockResponse(text=empty_response)])
+ events, epoch, _ = get_events_command(dummy_client, 1, 'since')
assert len(events) == 0
assert epoch == 0
+def test_get_events_429_error_failure(dummy_client, mocker):
+ mock_remove_duplicates = MagicMock()
+ mock_remove_duplicates.return_value = [{'id': 1,
+ 'published': '2022-04-17T12:32:36.667'}]
+ mocker.patch('OktaEventCollector.remove_duplicates', mock_remove_duplicates)
+ mocker.patch.object(dummy_client, 'get_events', side_effect=[DemistoException('exception')])
+ with pytest.raises(DemistoException):
+ get_events_command(dummy_client, 1, 'since', ['id1'])
+
+
+def test_get_events_general_failure(dummy_client, mocker):
+ mock_remove_duplicates = MagicMock()
+ mock_remove_duplicates.return_value = [{'id': 1,
+ 'published': '2022-04-17T12:32:36.667'}]
+ mocker.patch('OktaEventCollector.remove_duplicates', mock_remove_duplicates)
+ mocker.patch.object(dummy_client, 'get_events', side_effect=BaseException())
+ with pytest.raises(BaseException):
+ get_events_command(dummy_client, 1, 'since', ['id1'])
+
+
+def test_fetch_event(dummy_client, mocker):
+ response = {
+ 'events': [{'id': 1, 'published': '2022-04-17T12:32:36.667'}],
+ 'epoch_time_to_continue_fetch': 0,
+ 'next_link': 'next_link'
+ }
+ mocker.patch('OktaEventCollector.get_events_command', side_effect=[
+ ([], 1, response['next_link']),
+ (response['events'], response['epoch_time_to_continue_fetch'], response['next_link']),
+ ])
+ events, next_link = fetch_events(dummy_client, 0, 1, '')
+ assert events == [{'id': 1, 'published': '2022-04-17T12:32:36.667'}]
+ assert next_link == 'next_link'
+
+
@freeze_time('2022-04-17T12:32:36.667Z')
def test_429_too_many_requests(mocker, requests_mock):
diff --git a/Packs/Okta/ReleaseNotes/3_2_12.md b/Packs/Okta/ReleaseNotes/3_2_12.md
new file mode 100644
index 000000000000..8133974cf635
--- /dev/null
+++ b/Packs/Okta/ReleaseNotes/3_2_12.md
@@ -0,0 +1,7 @@
+
+#### Integrations
+
+##### Okta Event Collector
+
+- Fixed an issue where the same events were fetched repeatedly instead of progressing to the next set of events.
+- Added support for token based pagination while fetching.
diff --git a/Packs/Okta/pack_metadata.json b/Packs/Okta/pack_metadata.json
index 74bd96b59ff7..56d073a9bacb 100644
--- a/Packs/Okta/pack_metadata.json
+++ b/Packs/Okta/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Okta",
"description": "Integration with Okta's cloud-based identity management service.",
"support": "xsoar",
- "currentVersion": "3.2.11",
+ "currentVersion": "3.2.12",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 7704e82ecc4628632f46f450a1cae23a6b83a6d2 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:07:14 +0200
Subject: [PATCH 037/272] Update `demisto/sklearn` 0-10 coverage rate (#32760)
* upgrade images
* update RN
* Bump pack from version Base to 1.33.26.
* Bump pack from version Base to 1.33.27.
* Bump pack from version Base to 1.33.28.
* Bump pack from version Base to 1.33.29.
* Bump pack from version Base to 1.33.30.
* Bump pack from version Base to 1.33.31.
* Bump pack from version Base to 1.33.32.
* Bump pack from version Base to 1.33.33.
* Bump pack from version Base to 1.33.34.
---------
Co-authored-by: Content Bot
---
Packs/Base/ReleaseNotes/1_33_34.md | 6 ++++++
.../DrawRelatedIncidentsCanvas.yml | 2 +-
Packs/Base/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/Base/ReleaseNotes/1_33_34.md
diff --git a/Packs/Base/ReleaseNotes/1_33_34.md b/Packs/Base/ReleaseNotes/1_33_34.md
new file mode 100644
index 000000000000..a2279792e8d2
--- /dev/null
+++ b/Packs/Base/ReleaseNotes/1_33_34.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### DrawRelatedIncidentsCanvas
+
+- Updated the Docker image to: *demisto/sklearn:1.0.0.86554*.
diff --git a/Packs/Base/Scripts/DrawRelatedIncidentsCanvas/DrawRelatedIncidentsCanvas.yml b/Packs/Base/Scripts/DrawRelatedIncidentsCanvas/DrawRelatedIncidentsCanvas.yml
index 7bc75ecff922..8ae465269b6a 100644
--- a/Packs/Base/Scripts/DrawRelatedIncidentsCanvas/DrawRelatedIncidentsCanvas.yml
+++ b/Packs/Base/Scripts/DrawRelatedIncidentsCanvas/DrawRelatedIncidentsCanvas.yml
@@ -34,7 +34,7 @@ script: '-'
subtype: python3
timeout: '0'
type: python
-dockerimage: demisto/sklearn:1.0.0.49796
+dockerimage: demisto/sklearn:1.0.0.86554
runas: DBotWeakRole
tests:
- No tests (auto formatted)
diff --git a/Packs/Base/pack_metadata.json b/Packs/Base/pack_metadata.json
index 626f953c6d96..6b58869f6b55 100644
--- a/Packs/Base/pack_metadata.json
+++ b/Packs/Base/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Base",
"description": "The base pack for Cortex XSOAR.",
"support": "xsoar",
- "currentVersion": "1.33.33",
+ "currentVersion": "1.33.34",
"author": "Cortex XSOAR",
"serverMinVersion": "6.0.0",
"url": "https://www.paloaltonetworks.com/cortex",
From d629084f8fbe62dd16cdb1ccff1780ac3dfeac34 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:07:27 +0200
Subject: [PATCH 038/272] Update `demisto/tidy` 0-10 coverage rate (#32671)
* upgrade images
* update RN
---
Packs/Tidy/Integrations/Tidy/Tidy.yml | 2 +-
Packs/Tidy/ReleaseNotes/1_0_11.md | 6 ++++++
Packs/Tidy/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/Tidy/ReleaseNotes/1_0_11.md
diff --git a/Packs/Tidy/Integrations/Tidy/Tidy.yml b/Packs/Tidy/Integrations/Tidy/Tidy.yml
index 9aad4805d6d8..28355e7e456f 100644
--- a/Packs/Tidy/Integrations/Tidy/Tidy.yml
+++ b/Packs/Tidy/Integrations/Tidy/Tidy.yml
@@ -602,7 +602,7 @@ script:
- arguments: []
description: Install python environment.
name: tidy-python-env
- dockerimage: demisto/tidy:1.0.0.62989
+ dockerimage: demisto/tidy:1.0.0.86483
script: ''
subtype: python3
type: python
diff --git a/Packs/Tidy/ReleaseNotes/1_0_11.md b/Packs/Tidy/ReleaseNotes/1_0_11.md
new file mode 100644
index 000000000000..acc8945e364b
--- /dev/null
+++ b/Packs/Tidy/ReleaseNotes/1_0_11.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Tidy
+
+- Updated the Docker image to: *demisto/tidy:1.0.0.86483*.
diff --git a/Packs/Tidy/pack_metadata.json b/Packs/Tidy/pack_metadata.json
index dbe518119cc6..7e3a4d22f03f 100644
--- a/Packs/Tidy/pack_metadata.json
+++ b/Packs/Tidy/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Tidy",
"description": "Tidy integration handle endpoints environment installation.",
"support": "xsoar",
- "currentVersion": "1.0.10",
+ "currentVersion": "1.0.11",
"author": "Cortex XSOAR",
"url": "",
"email": "https://www.paloaltonetworks.com/cortex",
From 6bb49be5f038deb37540c3a04cad70d198e6207f Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:10:52 +0200
Subject: [PATCH 039/272] Update `demisto/snowflake` 0-10 coverage rate
(#32667)
* upgrade images
* update RN
---
Packs/Snowflake/Integrations/Snowflake/Snowflake.yml | 2 +-
Packs/Snowflake/ReleaseNotes/1_0_4.md | 6 ++++++
Packs/Snowflake/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/Snowflake/ReleaseNotes/1_0_4.md
diff --git a/Packs/Snowflake/Integrations/Snowflake/Snowflake.yml b/Packs/Snowflake/Integrations/Snowflake/Snowflake.yml
index adc66ebc478e..b81eeae7cc51 100644
--- a/Packs/Snowflake/Integrations/Snowflake/Snowflake.yml
+++ b/Packs/Snowflake/Integrations/Snowflake/Snowflake.yml
@@ -129,7 +129,7 @@ script:
description: Makes a DML change in the database.
execution: true
name: snowflake-update
- dockerimage: demisto/snowflake:1.0.0.2505
+ dockerimage: demisto/snowflake:1.0.0.86257
isfetch: true
script: '-'
type: python
diff --git a/Packs/Snowflake/ReleaseNotes/1_0_4.md b/Packs/Snowflake/ReleaseNotes/1_0_4.md
new file mode 100644
index 000000000000..f08c2a458a0e
--- /dev/null
+++ b/Packs/Snowflake/ReleaseNotes/1_0_4.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Snowflake
+
+- Updated the Docker image to: *demisto/snowflake:1.0.0.86257*.
diff --git a/Packs/Snowflake/pack_metadata.json b/Packs/Snowflake/pack_metadata.json
index 6dff2027bf7c..b2a82de18398 100644
--- a/Packs/Snowflake/pack_metadata.json
+++ b/Packs/Snowflake/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Snowflake",
"description": "Analytic data warehouse provided as Software-as-a-Service.",
"support": "xsoar",
- "currentVersion": "1.0.3",
+ "currentVersion": "1.0.4",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From e18959d8e985a3bada2f107814b4141a3d880a52 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:11:50 +0200
Subject: [PATCH 040/272] Update `demisto/smbprotocol` 0-10 coverage rate
(#32666)
* upgrade images
* update RN
---
Packs/SMB/Integrations/SMB_v2/SMB_v2.yml | 2 +-
Packs/SMB/ReleaseNotes/2_0_17.md | 6 ++++++
Packs/SMB/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/SMB/ReleaseNotes/2_0_17.md
diff --git a/Packs/SMB/Integrations/SMB_v2/SMB_v2.yml b/Packs/SMB/Integrations/SMB_v2/SMB_v2.yml
index 6c612106df61..e100617452fe 100644
--- a/Packs/SMB/Integrations/SMB_v2/SMB_v2.yml
+++ b/Packs/SMB/Integrations/SMB_v2/SMB_v2.yml
@@ -162,7 +162,7 @@ script:
- name: password
description: The password to use for authentication. If empty, the password from the instance configuration is used.
description: Removes a directory from the given path.
- dockerimage: demisto/smbprotocol:1.0.0.63639
+ dockerimage: demisto/smbprotocol:1.0.0.85835
runonce: false
script: '-'
type: python
diff --git a/Packs/SMB/ReleaseNotes/2_0_17.md b/Packs/SMB/ReleaseNotes/2_0_17.md
new file mode 100644
index 000000000000..c2d0a413059e
--- /dev/null
+++ b/Packs/SMB/ReleaseNotes/2_0_17.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Server Message Block (SMB) v2
+
+- Updated the Docker image to: *demisto/smbprotocol:1.0.0.85835*.
diff --git a/Packs/SMB/pack_metadata.json b/Packs/SMB/pack_metadata.json
index c8d8de223c58..2a1a0e480e54 100644
--- a/Packs/SMB/pack_metadata.json
+++ b/Packs/SMB/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Server Message Block (SMB)",
"description": "File exchange with an SMB server.",
"support": "xsoar",
- "currentVersion": "2.0.16",
+ "currentVersion": "2.0.17",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 779e49ab085e1fd565b7e2b3de9864014002b77c Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:12:07 +0200
Subject: [PATCH 041/272] Update `demisto/resilient` 10-25 coverage rate
(#32659)
* upgrade images
* update RN
---
.../IBMResilientSystems/IBMResilientSystems.yml | 2 +-
Packs/IBMResilientSystems/ReleaseNotes/1_1_9.md | 6 ++++++
Packs/IBMResilientSystems/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/IBMResilientSystems/ReleaseNotes/1_1_9.md
diff --git a/Packs/IBMResilientSystems/Integrations/IBMResilientSystems/IBMResilientSystems.yml b/Packs/IBMResilientSystems/Integrations/IBMResilientSystems/IBMResilientSystems.yml
index 148a20d779bc..afbced834f40 100644
--- a/Packs/IBMResilientSystems/Integrations/IBMResilientSystems/IBMResilientSystems.yml
+++ b/Packs/IBMResilientSystems/Integrations/IBMResilientSystems/IBMResilientSystems.yml
@@ -735,7 +735,7 @@ script:
- contextPath: Resilient.IncidentArtifact.ip.destination
description: Whether the IP address is a destination.
type: Boolean
- dockerimage: demisto/resilient:2.0.0.45701
+ dockerimage: demisto/resilient:2.0.0.86430
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/IBMResilientSystems/ReleaseNotes/1_1_9.md b/Packs/IBMResilientSystems/ReleaseNotes/1_1_9.md
new file mode 100644
index 000000000000..c58dc6b826e4
--- /dev/null
+++ b/Packs/IBMResilientSystems/ReleaseNotes/1_1_9.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### IBM Resilient Systems
+
+- Updated the Docker image to: *demisto/resilient:2.0.0.86430*.
diff --git a/Packs/IBMResilientSystems/pack_metadata.json b/Packs/IBMResilientSystems/pack_metadata.json
index 40e58672f8aa..a3425be46475 100644
--- a/Packs/IBMResilientSystems/pack_metadata.json
+++ b/Packs/IBMResilientSystems/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "IBM Resilient Systems",
"description": "Case management that enables visibility across your tools for continual IR improvement",
"support": "xsoar",
- "currentVersion": "1.1.8",
+ "currentVersion": "1.1.9",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 618091097b2a3c86f9cd280a39ec1184f242eb55 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:12:36 +0200
Subject: [PATCH 042/272] Update `demisto/google-vision-api` 0-10 coverage rate
(#32658)
* upgrade images
* update RN
---
.../Integrations/GoogleVisionAPI/GoogleVisionAPI.yml | 2 +-
Packs/GoogleVisionAPI/ReleaseNotes/1_0_21.md | 6 ++++++
Packs/GoogleVisionAPI/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/GoogleVisionAPI/ReleaseNotes/1_0_21.md
diff --git a/Packs/GoogleVisionAPI/Integrations/GoogleVisionAPI/GoogleVisionAPI.yml b/Packs/GoogleVisionAPI/Integrations/GoogleVisionAPI/GoogleVisionAPI.yml
index 663f50338387..2232a7f6aa6a 100644
--- a/Packs/GoogleVisionAPI/Integrations/GoogleVisionAPI/GoogleVisionAPI.yml
+++ b/Packs/GoogleVisionAPI/Integrations/GoogleVisionAPI/GoogleVisionAPI.yml
@@ -44,7 +44,7 @@ script:
- contextPath: GoogleVisionAPI.Logo.Score
description: The certainty score provided by the Google Vision API.
type: Unknown
- dockerimage: demisto/google-vision-api:1.0.0.63870
+ dockerimage: demisto/google-vision-api:1.0.0.86505
runonce: false
script: '-'
type: python
diff --git a/Packs/GoogleVisionAPI/ReleaseNotes/1_0_21.md b/Packs/GoogleVisionAPI/ReleaseNotes/1_0_21.md
new file mode 100644
index 000000000000..852ec08609a6
--- /dev/null
+++ b/Packs/GoogleVisionAPI/ReleaseNotes/1_0_21.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Google Vision AI
+
+- Updated the Docker image to: *demisto/google-vision-api:1.0.0.86505*.
diff --git a/Packs/GoogleVisionAPI/pack_metadata.json b/Packs/GoogleVisionAPI/pack_metadata.json
index 76cefd59ae05..c4445a6e072f 100644
--- a/Packs/GoogleVisionAPI/pack_metadata.json
+++ b/Packs/GoogleVisionAPI/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Vision AI",
"description": "Image processing with Google Vision API",
"support": "xsoar",
- "currentVersion": "1.0.20",
+ "currentVersion": "1.0.21",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 9064b4d62061884571c953786f9898a82102de8f Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:12:55 +0200
Subject: [PATCH 043/272] Update `demisto/google-kms` 10-25 coverage rate
(#32656)
* upgrade images
* update RN
---
.../GoogleKeyManagementService.yml | 2 +-
Packs/GoogleKeyManagementService/ReleaseNotes/1_0_22.md | 6 ++++++
Packs/GoogleKeyManagementService/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/GoogleKeyManagementService/ReleaseNotes/1_0_22.md
diff --git a/Packs/GoogleKeyManagementService/Integrations/GoogleKeyManagementService/GoogleKeyManagementService.yml b/Packs/GoogleKeyManagementService/Integrations/GoogleKeyManagementService/GoogleKeyManagementService.yml
index a76d5304f41a..9126065d289b 100644
--- a/Packs/GoogleKeyManagementService/Integrations/GoogleKeyManagementService/GoogleKeyManagementService.yml
+++ b/Packs/GoogleKeyManagementService/Integrations/GoogleKeyManagementService/GoogleKeyManagementService.yml
@@ -1237,7 +1237,7 @@ script:
- contextPath: GoogleKMS.PublicKey.Algorithm
description: The algorithm used in the CryptoKey
type: String
- dockerimage: demisto/google-kms:1.0.0.62005
+ dockerimage: demisto/google-kms:1.0.0.86683
runonce: false
script: '-'
type: python
diff --git a/Packs/GoogleKeyManagementService/ReleaseNotes/1_0_22.md b/Packs/GoogleKeyManagementService/ReleaseNotes/1_0_22.md
new file mode 100644
index 000000000000..3d8cbe64bdb2
--- /dev/null
+++ b/Packs/GoogleKeyManagementService/ReleaseNotes/1_0_22.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Google Key Management Service
+
+- Updated the Docker image to: *demisto/google-kms:1.0.0.86683*.
diff --git a/Packs/GoogleKeyManagementService/pack_metadata.json b/Packs/GoogleKeyManagementService/pack_metadata.json
index 775b0e74854a..463c9f8898e9 100644
--- a/Packs/GoogleKeyManagementService/pack_metadata.json
+++ b/Packs/GoogleKeyManagementService/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Key Management Service",
"description": "Use the Google Key Management Service API for CryptoKey management and encrypt/decrypt functionality.",
"support": "xsoar",
- "currentVersion": "1.0.21",
+ "currentVersion": "1.0.22",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From e84d7dd4ea570ee9040bc06925cfd36c3c75b67c Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:13:14 +0200
Subject: [PATCH 044/272] Update `demisto/google-cloud-translate` 25-40
coverage rate (#32655)
* upgrade images
* update RN
---
.../GoogleCloudTranslate/GoogleCloudTranslate.yml | 2 +-
Packs/GoogleCloudTranslate/ReleaseNotes/1_0_9.md | 6 ++++++
Packs/GoogleCloudTranslate/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/GoogleCloudTranslate/ReleaseNotes/1_0_9.md
diff --git a/Packs/GoogleCloudTranslate/Integrations/GoogleCloudTranslate/GoogleCloudTranslate.yml b/Packs/GoogleCloudTranslate/Integrations/GoogleCloudTranslate/GoogleCloudTranslate.yml
index 259ff2791485..109106233a03 100644
--- a/Packs/GoogleCloudTranslate/Integrations/GoogleCloudTranslate/GoogleCloudTranslate.yml
+++ b/Packs/GoogleCloudTranslate/Integrations/GoogleCloudTranslate/GoogleCloudTranslate.yml
@@ -67,7 +67,7 @@ script:
- contextPath: GoogleCloudTranslate.TranslateText.translated_text
description: The translated text.
type: String
- dockerimage: demisto/google-cloud-translate:1.0.0.63615
+ dockerimage: demisto/google-cloud-translate:1.0.0.85793
runonce: false
script: '-'
type: python
diff --git a/Packs/GoogleCloudTranslate/ReleaseNotes/1_0_9.md b/Packs/GoogleCloudTranslate/ReleaseNotes/1_0_9.md
new file mode 100644
index 000000000000..e6412af84378
--- /dev/null
+++ b/Packs/GoogleCloudTranslate/ReleaseNotes/1_0_9.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Google Cloud Translate
+
+- Updated the Docker image to: *demisto/google-cloud-translate:1.0.0.85793*.
diff --git a/Packs/GoogleCloudTranslate/pack_metadata.json b/Packs/GoogleCloudTranslate/pack_metadata.json
index 7509bb28e024..852842948f69 100644
--- a/Packs/GoogleCloudTranslate/pack_metadata.json
+++ b/Packs/GoogleCloudTranslate/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Google Cloud Translate",
"description": "A Google API cloud based translation service.",
"support": "xsoar",
- "currentVersion": "1.0.8",
+ "currentVersion": "1.0.9",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 40d91ade0d37e71bb907e1557cccc30f324d44b4 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:13:31 +0200
Subject: [PATCH 045/272] Update `demisto/pwsh-exchangev3` 0-10 coverage rate
(#32654)
* upgrade images
* update RN
* Bump pack from version Microsoft365Defender to 4.5.18.
* Bump pack from version Microsoft365Defender to 4.5.19.
---------
Co-authored-by: Content Bot
---
.../O365DefenderSafeLinks/O365DefenderSafeLinks.yml | 2 +-
Packs/Microsoft365Defender/ReleaseNotes/4_5_19.md | 6 ++++++
Packs/Microsoft365Defender/pack_metadata.json | 2 +-
.../MicrosoftPolicyAndComplianceAuditLog.yml | 2 +-
Packs/Office365AndAzureAuditLog/ReleaseNotes/2_0_1.md | 6 ++++++
Packs/Office365AndAzureAuditLog/pack_metadata.json | 2 +-
6 files changed, 16 insertions(+), 4 deletions(-)
create mode 100644 Packs/Microsoft365Defender/ReleaseNotes/4_5_19.md
create mode 100644 Packs/Office365AndAzureAuditLog/ReleaseNotes/2_0_1.md
diff --git a/Packs/Microsoft365Defender/Integrations/O365DefenderSafeLinks/O365DefenderSafeLinks.yml b/Packs/Microsoft365Defender/Integrations/O365DefenderSafeLinks/O365DefenderSafeLinks.yml
index 71c9ef1617be..d6aec1ab30e1 100644
--- a/Packs/Microsoft365Defender/Integrations/O365DefenderSafeLinks/O365DefenderSafeLinks.yml
+++ b/Packs/Microsoft365Defender/Integrations/O365DefenderSafeLinks/O365DefenderSafeLinks.yml
@@ -939,7 +939,7 @@ script:
runonce: false
script: "-"
type: powershell
- dockerimage: demisto/pwsh-exchangev3:1.0.0.49863
+ dockerimage: demisto/pwsh-exchangev3:1.0.0.80547
fromversion: 6.0.0
tests:
- No Test
diff --git a/Packs/Microsoft365Defender/ReleaseNotes/4_5_19.md b/Packs/Microsoft365Defender/ReleaseNotes/4_5_19.md
new file mode 100644
index 000000000000..cc43c24909a4
--- /dev/null
+++ b/Packs/Microsoft365Defender/ReleaseNotes/4_5_19.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### O365 Defender SafeLinks
+
+- Updated the Docker image to: *demisto/pwsh-exchangev3:1.0.0.80547*.
diff --git a/Packs/Microsoft365Defender/pack_metadata.json b/Packs/Microsoft365Defender/pack_metadata.json
index fca1264e5ef1..8589ef24ce1d 100644
--- a/Packs/Microsoft365Defender/pack_metadata.json
+++ b/Packs/Microsoft365Defender/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Microsoft 365 Defender",
"description": "Microsoft 365 Defender is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.",
"support": "xsoar",
- "currentVersion": "4.5.18",
+ "currentVersion": "4.5.19",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Office365AndAzureAuditLog/Integrations/MicrosoftPolicyAndComplianceAuditLog/MicrosoftPolicyAndComplianceAuditLog.yml b/Packs/Office365AndAzureAuditLog/Integrations/MicrosoftPolicyAndComplianceAuditLog/MicrosoftPolicyAndComplianceAuditLog.yml
index 53563019c7c5..4e44fba622fa 100644
--- a/Packs/Office365AndAzureAuditLog/Integrations/MicrosoftPolicyAndComplianceAuditLog/MicrosoftPolicyAndComplianceAuditLog.yml
+++ b/Packs/Office365AndAzureAuditLog/Integrations/MicrosoftPolicyAndComplianceAuditLog/MicrosoftPolicyAndComplianceAuditLog.yml
@@ -153,7 +153,7 @@ script:
runonce: false
script: '-'
type: powershell
- dockerimage: demisto/pwsh-exchangev3:1.0.0.49863
+ dockerimage: demisto/pwsh-exchangev3:1.0.0.80547
fromversion: 5.5.0
tests:
- Audit Log - Test
diff --git a/Packs/Office365AndAzureAuditLog/ReleaseNotes/2_0_1.md b/Packs/Office365AndAzureAuditLog/ReleaseNotes/2_0_1.md
new file mode 100644
index 000000000000..7dbac10e9bdb
--- /dev/null
+++ b/Packs/Office365AndAzureAuditLog/ReleaseNotes/2_0_1.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Microsoft Policy And Compliance (Audit Log)
+
+- Updated the Docker image to: *demisto/pwsh-exchangev3:1.0.0.80547*.
diff --git a/Packs/Office365AndAzureAuditLog/pack_metadata.json b/Packs/Office365AndAzureAuditLog/pack_metadata.json
index 14e1778f3a67..2d88e4397a19 100644
--- a/Packs/Office365AndAzureAuditLog/pack_metadata.json
+++ b/Packs/Office365AndAzureAuditLog/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Office 365 and Azure (Audit Log)",
"description": "Search the unified audit log to view user and administrator activity in your organization.",
"support": "xsoar",
- "currentVersion": "2.0.0",
+ "currentVersion": "2.0.1",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 855006624828326102547289917e08104afcb7eb Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:35:46 +0200
Subject: [PATCH 046/272] Update `demisto/fastapi` 25-40 coverage rate (#32572)
* upgrade images
* update RN
---
.../GitHubEventCollector/GitHubEventCollector.yml | 2 +-
Packs/GitHub/ReleaseNotes/2_0_28.md | 6 ++++++
Packs/GitHub/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/GitHub/ReleaseNotes/2_0_28.md
diff --git a/Packs/GitHub/Integrations/GitHubEventCollector/GitHubEventCollector.yml b/Packs/GitHub/Integrations/GitHubEventCollector/GitHubEventCollector.yml
index 8d7de56bb25c..ad9785c08631 100644
--- a/Packs/GitHub/Integrations/GitHubEventCollector/GitHubEventCollector.yml
+++ b/Packs/GitHub/Integrations/GitHubEventCollector/GitHubEventCollector.yml
@@ -73,7 +73,7 @@ script:
required: true
description: Manual command to fetch events and display them.
name: github-get-events
- dockerimage: demisto/fastapi:1.0.0.64474
+ dockerimage: demisto/fastapi:1.0.0.86524
isfetchevents: true
subtype: python3
marketplaces:
diff --git a/Packs/GitHub/ReleaseNotes/2_0_28.md b/Packs/GitHub/ReleaseNotes/2_0_28.md
new file mode 100644
index 000000000000..f76d312ace88
--- /dev/null
+++ b/Packs/GitHub/ReleaseNotes/2_0_28.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Github Event Collector
+
+- Updated the Docker image to: *demisto/fastapi:1.0.0.86524*.
diff --git a/Packs/GitHub/pack_metadata.json b/Packs/GitHub/pack_metadata.json
index 4429f9c58998..e207af58630f 100644
--- a/Packs/GitHub/pack_metadata.json
+++ b/Packs/GitHub/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "GitHub",
"description": "Manage GitHub issues and pull requests directly from Cortex XSOAR",
"support": "xsoar",
- "currentVersion": "2.0.27",
+ "currentVersion": "2.0.28",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From ab43da0f8a9e235835e1946b690a16894bcf63dd Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:43:38 +0200
Subject: [PATCH 047/272] Update `demisto/etl2pcap` 25-40 coverage rate
(#32674)
* upgrade images
* update RN
---
Packs/WindowsForensics/ReleaseNotes/1_0_5.md | 6 ++++++
Packs/WindowsForensics/Scripts/Etl2Pcap/Etl2Pcap.yml | 2 +-
Packs/WindowsForensics/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/WindowsForensics/ReleaseNotes/1_0_5.md
diff --git a/Packs/WindowsForensics/ReleaseNotes/1_0_5.md b/Packs/WindowsForensics/ReleaseNotes/1_0_5.md
new file mode 100644
index 000000000000..7f4e7db2b42d
--- /dev/null
+++ b/Packs/WindowsForensics/ReleaseNotes/1_0_5.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### Etl2Pcap
+
+- Updated the Docker image to: *demisto/etl2pcap:1.0.0.86370*.
diff --git a/Packs/WindowsForensics/Scripts/Etl2Pcap/Etl2Pcap.yml b/Packs/WindowsForensics/Scripts/Etl2Pcap/Etl2Pcap.yml
index 222a87d16052..d7b65c504b08 100644
--- a/Packs/WindowsForensics/Scripts/Etl2Pcap/Etl2Pcap.yml
+++ b/Packs/WindowsForensics/Scripts/Etl2Pcap/Etl2Pcap.yml
@@ -6,7 +6,7 @@ args:
commonfields:
id: Etl2Pcap
version: -1
-dockerimage: demisto/etl2pcap:1.0.0.19032
+dockerimage: demisto/etl2pcap:1.0.0.86370
enabled: true
name: Etl2Pcap
outputs:
diff --git a/Packs/WindowsForensics/pack_metadata.json b/Packs/WindowsForensics/pack_metadata.json
index ddf6c0842b05..8fbbab8c3182 100644
--- a/Packs/WindowsForensics/pack_metadata.json
+++ b/Packs/WindowsForensics/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Windows Forensics",
"description": "Acquires forensic data from Windows hosts by leveraging Windows built-in capabilities.",
"support": "xsoar",
- "currentVersion": "1.0.4",
+ "currentVersion": "1.0.5",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 076e0c9ec700140c284da33cb220f5d2e4f30a48 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 11:48:10 +0200
Subject: [PATCH 048/272] Update `demisto/btfl-soup` 25-40 coverage rate
(#32627)
* upgrade images
* update RN
---
.../AzureADConnectHealthFeed/AzureADConnectHealthFeed.yml | 2 +-
Packs/FeedAzureADConnectHealth/ReleaseNotes/1_0_20.md | 6 ++++++
Packs/FeedAzureADConnectHealth/pack_metadata.json | 2 +-
Packs/FeedZoom/Integrations/FeedZoom/FeedZoom.yml | 2 +-
Packs/FeedZoom/ReleaseNotes/1_1_14.md | 6 ++++++
Packs/FeedZoom/pack_metadata.json | 2 +-
6 files changed, 16 insertions(+), 4 deletions(-)
create mode 100644 Packs/FeedAzureADConnectHealth/ReleaseNotes/1_0_20.md
create mode 100644 Packs/FeedZoom/ReleaseNotes/1_1_14.md
diff --git a/Packs/FeedAzureADConnectHealth/Integrations/AzureADConnectHealthFeed/AzureADConnectHealthFeed.yml b/Packs/FeedAzureADConnectHealth/Integrations/AzureADConnectHealthFeed/AzureADConnectHealthFeed.yml
index 741f1852ee37..b3382a253ef7 100644
--- a/Packs/FeedAzureADConnectHealth/Integrations/AzureADConnectHealthFeed/AzureADConnectHealthFeed.yml
+++ b/Packs/FeedAzureADConnectHealth/Integrations/AzureADConnectHealthFeed/AzureADConnectHealthFeed.yml
@@ -101,6 +101,6 @@ script:
description: The maximum number of results to return. The default value is 10.
defaultValue: "0"
description: Gets indicators from the feed.
- dockerimage: demisto/btfl-soup:1.0.1.45563
+ dockerimage: demisto/btfl-soup:1.0.1.86352
feed: true
subtype: python3
diff --git a/Packs/FeedAzureADConnectHealth/ReleaseNotes/1_0_20.md b/Packs/FeedAzureADConnectHealth/ReleaseNotes/1_0_20.md
new file mode 100644
index 000000000000..45d09082bbfa
--- /dev/null
+++ b/Packs/FeedAzureADConnectHealth/ReleaseNotes/1_0_20.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Azure AD Connect Health Feed
+
+- Updated the Docker image to: *demisto/btfl-soup:1.0.1.86352*.
diff --git a/Packs/FeedAzureADConnectHealth/pack_metadata.json b/Packs/FeedAzureADConnectHealth/pack_metadata.json
index 426948658f3f..f05e861a3857 100644
--- a/Packs/FeedAzureADConnectHealth/pack_metadata.json
+++ b/Packs/FeedAzureADConnectHealth/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Microsoft Azure AD Connect Health Feed",
"description": "Indicator feed from Microsoft Azure AD Connect Health endpoints, fetching URLs and DomainGlobs used by Azure AD, with which you can create a list (allowlist, EDL, etc.) for your SIEM or firewall service to ingest and apply to its policy rules.",
"support": "xsoar",
- "currentVersion": "1.0.19",
+ "currentVersion": "1.0.20",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/FeedZoom/Integrations/FeedZoom/FeedZoom.yml b/Packs/FeedZoom/Integrations/FeedZoom/FeedZoom.yml
index 70847d605621..83d84847b6bf 100644
--- a/Packs/FeedZoom/Integrations/FeedZoom/FeedZoom.yml
+++ b/Packs/FeedZoom/Integrations/FeedZoom/FeedZoom.yml
@@ -122,7 +122,7 @@ script:
description: The maximum number of results to return. The default value is 10.
defaultValue: "10"
description: Gets indicators from the feed.
- dockerimage: demisto/btfl-soup:1.0.1.45563
+ dockerimage: demisto/btfl-soup:1.0.1.86352
feed: true
subtype: python3
tests:
diff --git a/Packs/FeedZoom/ReleaseNotes/1_1_14.md b/Packs/FeedZoom/ReleaseNotes/1_1_14.md
new file mode 100644
index 000000000000..a160cae173c7
--- /dev/null
+++ b/Packs/FeedZoom/ReleaseNotes/1_1_14.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Zoom Feed
+
+- Updated the Docker image to: *demisto/btfl-soup:1.0.1.86352*.
diff --git a/Packs/FeedZoom/pack_metadata.json b/Packs/FeedZoom/pack_metadata.json
index 7018029975f7..ff6abcc95394 100644
--- a/Packs/FeedZoom/pack_metadata.json
+++ b/Packs/FeedZoom/pack_metadata.json
@@ -5,7 +5,7 @@
"videos": [
"https://www.youtube.com/embed/s9lRtJltTGI"
],
- "currentVersion": "1.1.13",
+ "currentVersion": "1.1.14",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From a6e7972d7b5c47bc0d041c3c19bdf44a0c2499b0 Mon Sep 17 00:00:00 2001
From: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
Date: Tue, 20 Feb 2024 12:34:42 +0200
Subject: [PATCH 049/272] [Microsoft Graph Security] Update msg-update-alert
documentation (#32983)
* update docs
* update dockers
* add "MSG-ediscovery-tpb" to skipped_tests
---
.../MicrosoftGraphSecurity.yml | 6 ++---
.../MicrosoftGraphSecurity/README.md | 26 +++++++++----------
.../ReleaseNotes/2_2_8.md | 6 +++++
.../MicrosoftGraphSecurity/pack_metadata.json | 2 +-
Tests/conf.json | 3 ++-
5 files changed, 24 insertions(+), 19 deletions(-)
create mode 100644 Packs/MicrosoftGraphSecurity/ReleaseNotes/2_2_8.md
diff --git a/Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml b/Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
index 0549545d5769..26b8e904938d 100644
--- a/Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
+++ b/Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
@@ -689,17 +689,15 @@ script:
- unknown
- truePositive
- falsePositive
- - benignPositive
+ - informationalExpectedActivity
- auto: PREDEFINED
description: Relevant only for Alerts v2. Use this field to update the alert's determination.
name: determination
predefined:
- unknown
- - apt
- malware
- phishing
- other
- - securityPersonnel
- securityTesting
- multiStagedAttack
- maliciousUserActivity
@@ -2038,7 +2036,7 @@ script:
- contextPath: MSGraphMail.AssessmentRequest.ResultMessage
description: The result message of the assessment request.
type: String
- dockerimage: demisto/crypto:1.0.0.82826
+ dockerimage: demisto/crypto:1.0.0.87358
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/README.md b/Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/README.md
index dd810ab4fd86..575463ac0e3d 100644
--- a/Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/README.md
+++ b/Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/README.md
@@ -377,19 +377,19 @@ Update an editable alert property within any integrated solution to keep alert s
#### Input
-| **Argument Name** | **Description** | **Required** |
-| --- | --- | --- |
-| alert_id | The Alert ID. Provider-generated GUID/unique identifier. | Required |
-| assigned_to | Name of the analyst the alert is assigned to for triage, investigation, or remediation. | Optional |
-| closed_date_time | Relevant only for Legacy Alerts. Time the alert was closed in the string format MM/DD/YYYY. | Optional |
-| comments | Relevant only for Legacy Alerts. Analyst comments on the alert (for customer alert management). | Optional |
-| feedback | Relevant only for Legacy Alerts. Analyst feedback on the alert. Possible values are: unknown, truePositive, falsePositive, benignPositive. | Optional |
-| status | Alert lifecycle status (stage). Possible values are: unknown, newAlert, inProgress, resolved, new. | Optional |
-| tags | Relevant only for Legacy Alerts. User-definable labels that can be applied to an alert and can serve as filter conditions, for example "HVA", "SAW). | Optional |
-| vendor_information | Relevant only for Legacy Alerts. Details about the security service vendor, for example Microsoft. | Optional |
-| provider_information | Relevant only for Legacy Alerts. Details about the security service vendor, for example Windows Defender ATP. | Optional |
-| classification | Relevant only for Alerts v2. Use this field to update the alert's classification. Possible values are: unknown, truePositive, falsePositive, benignPositive. | Optional |
-| determination | Relevant only for Alerts v2. Use this field to update the alert's determination. Possible values are: unknown, apt, malware, phishing, other, securityPersonnel, securityTesting, multiStagedAttack, maliciousUserActivity, lineOfBusinessApplication, unwantedSoftware. | Optional |
+| **Argument Name** | **Description** | **Required** |
+|----------------------|--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|--------------|
+| alert_id | The Alert ID. Provider-generated GUID/unique identifier. | Required |
+| assigned_to | Name of the analyst the alert is assigned to for triage, investigation, or remediation. | Optional |
+| closed_date_time | Relevant only for Legacy Alerts. Time the alert was closed in the string format MM/DD/YYYY. | Optional |
+| comments | Relevant only for Legacy Alerts. Analyst comments on the alert (for customer alert management). | Optional |
+| feedback | Relevant only for Legacy Alerts. Analyst feedback on the alert. Possible values are: unknown, truePositive, falsePositive, benignPositive. | Optional |
+| status | Alert lifecycle status (stage). Possible values are: unknown, newAlert, inProgress, resolved, new. | Optional |
+| tags | Relevant only for Legacy Alerts. User-definable labels that can be applied to an alert and can serve as filter conditions, for example "HVA", "SAW). | Optional |
+| vendor_information | Relevant only for Legacy Alerts. Details about the security service vendor, for example Microsoft. | Optional |
+| provider_information | Relevant only for Legacy Alerts. Details about the security service vendor, for example Windows Defender ATP. | Optional |
+| classification | Relevant only for Alerts v2. Use this field to update the alert's classification. Possible values are: unknown, truePositive, falsePositive, informationalExpectedActivity. | Optional |
+| determination | Relevant only for Alerts v2. Use this field to update the alert's determination. Possible values are: unknown, malware, phishing, other, securityTesting, multiStagedAttack, maliciousUserActivity, lineOfBusinessApplication, unwantedSoftware. | Optional |
#### Context Output
diff --git a/Packs/MicrosoftGraphSecurity/ReleaseNotes/2_2_8.md b/Packs/MicrosoftGraphSecurity/ReleaseNotes/2_2_8.md
new file mode 100644
index 000000000000..173bed488262
--- /dev/null
+++ b/Packs/MicrosoftGraphSecurity/ReleaseNotes/2_2_8.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Microsoft Graph Security
+- Updated the documentation for the ***msg-update-alert*** command to include only the determination and classification options supported by Microsoft.
+- Updated the Docker image to: *demisto/crypto:1.0.0.87358*.
\ No newline at end of file
diff --git a/Packs/MicrosoftGraphSecurity/pack_metadata.json b/Packs/MicrosoftGraphSecurity/pack_metadata.json
index 32e829feb988..0cefa88a578c 100644
--- a/Packs/MicrosoftGraphSecurity/pack_metadata.json
+++ b/Packs/MicrosoftGraphSecurity/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Microsoft Graph Security",
"description": "Unified gateway to security insights - all from a unified Microsoft Graph\n Security API.",
"support": "xsoar",
- "currentVersion": "2.2.7",
+ "currentVersion": "2.2.8",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Tests/conf.json b/Tests/conf.json
index fdc83215ea3d..0cfb66b0a6c3 100644
--- a/Tests/conf.json
+++ b/Tests/conf.json
@@ -5865,7 +5865,8 @@
"ThreatStream-Test": "Issue CRTX-96526",
"MSG-Threat-Assessment-test": "API limitation",
"BambenekConsultingFeed_Test": "Issue CRTX-99480",
- "AWS SNS Listener - Test": "Cant validate mock msg against AWS-SNS in TBP"
+ "AWS SNS Listener - Test": "Cant validate mock msg against AWS-SNS in TBP",
+ "MSG-ediscovery-tpb": "Issue CIAC-9763"
},
"skipped_integrations": {
"EWS Mail Sender": "The integration is deprecated",
From f3b883c5df1c823f97629cebd6cff3432b4975a8 Mon Sep 17 00:00:00 2001
From: Moshe Eichler <78307768+MosheEichler@users.noreply.github.com>
Date: Tue, 20 Feb 2024 13:13:44 +0200
Subject: [PATCH 050/272] Ignore E2E jobs in check jobs are really done
(#32963)
---
Tests/scripts/check_jobs_done.py | 4 ++--
1 file changed, 2 insertions(+), 2 deletions(-)
diff --git a/Tests/scripts/check_jobs_done.py b/Tests/scripts/check_jobs_done.py
index 85047318ee47..2138ccbbe6a3 100644
--- a/Tests/scripts/check_jobs_done.py
+++ b/Tests/scripts/check_jobs_done.py
@@ -15,7 +15,7 @@
'xpanse-prepare-testing-bucket',
'xsoar-prepare-testing-bucket',
'xsiam_server_ga',
- 'xsoar_ng_server_ga',
+ # 'xsoar_ng_server_ga',
'tests_xsoar_server: [Server 6.9]',
'tests_xsoar_server: [Server 6.10]',
'tests_xsoar_server: [Server 6.11]',
@@ -25,7 +25,7 @@
'xsiam-test_playbooks_results',
'xsiam-test_modeling_rule_results',
'cloning-content-repo-last-upload-commit',
- 'xsoar-saas_test_e2e_results',
+ # 'xsoar-saas_test_e2e_results',
]
SDK_NIGHTLY_JOBS = [
From 151317ce37c59ca044a8ec5f2f66095301e09922 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 13:32:31 +0200
Subject: [PATCH 051/272] update docker + RN (#33000)
---
.../Active_Directory_Query/Active_Directory_Query.yml | 2 +-
Packs/Active_Directory_Query/ReleaseNotes/1_6_29.md | 6 ++++++
Packs/Active_Directory_Query/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/Active_Directory_Query/ReleaseNotes/1_6_29.md
diff --git a/Packs/Active_Directory_Query/Integrations/Active_Directory_Query/Active_Directory_Query.yml b/Packs/Active_Directory_Query/Integrations/Active_Directory_Query/Active_Directory_Query.yml
index 6ea4292169a2..92b344faf982 100644
--- a/Packs/Active_Directory_Query/Integrations/Active_Directory_Query/Active_Directory_Query.yml
+++ b/Packs/Active_Directory_Query/Integrations/Active_Directory_Query/Active_Directory_Query.yml
@@ -800,7 +800,7 @@ script:
outputs:
- contextPath: ActiveDirectory.ValidCredentials
description: List of usernames that successfully logged in.
- dockerimage: demisto/ldap:2.9.1.87300
+ dockerimage: demisto/ldap:2.9.1.87744
ismappable: true
isremotesyncout: true
runonce: false
diff --git a/Packs/Active_Directory_Query/ReleaseNotes/1_6_29.md b/Packs/Active_Directory_Query/ReleaseNotes/1_6_29.md
new file mode 100644
index 000000000000..6083963f08a8
--- /dev/null
+++ b/Packs/Active_Directory_Query/ReleaseNotes/1_6_29.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Active Directory Query v2
+
+- Updated the Docker image to: *demisto/ldap:2.9.1.87744*.
diff --git a/Packs/Active_Directory_Query/pack_metadata.json b/Packs/Active_Directory_Query/pack_metadata.json
index 28985171074b..c5b7d124933e 100644
--- a/Packs/Active_Directory_Query/pack_metadata.json
+++ b/Packs/Active_Directory_Query/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Active Directory Query",
"description": "Active Directory Query integration enables you to access and manage Active Directory objects (users, contacts, and computers).",
"support": "xsoar",
- "currentVersion": "1.6.28",
+ "currentVersion": "1.6.29",
"author": "Cortex XSOAR",
"url": "",
"email": "",
From 24fbd75ea4bc5451db539487fe2bf32bcf0a2114 Mon Sep 17 00:00:00 2001
From: JudithB <132264628+jbabazadeh@users.noreply.github.com>
Date: Tue, 20 Feb 2024 14:29:19 +0200
Subject: [PATCH 052/272] troubleshooting splunk cloud (#33019)
* troubleshooting splunk cloud
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---
Packs/SplunkPy/Integrations/SplunkPy/README.md | 13 +++++++++++++
1 file changed, 13 insertions(+)
diff --git a/Packs/SplunkPy/Integrations/SplunkPy/README.md b/Packs/SplunkPy/Integrations/SplunkPy/README.md
index 611cc4ad63a9..405f5439bebb 100644
--- a/Packs/SplunkPy/Integrations/SplunkPy/README.md
+++ b/Packs/SplunkPy/Integrations/SplunkPy/README.md
@@ -1132,3 +1132,16 @@ The default port is 8088.
## Troubleshooting
In case you encounter HTTP errors (e.g., IncompleteRead), we recommend using Python requests handler.
+
+If you encounter connectivity issues while using **Splunk Cloud** within Cortex XSOAR8 or Cortex XSIAM you may receive the following error:
+
+ requests.exceptions.ConnectTimeout:
+ HTTPSConnectionPool(host='.splunkcloud.com', port=8089)
+ : Max retries exceeded with url: /services/auth/login (Caused by ConnectTimeoutError(,
+ 'Connection to .splunkcloud.com timed out.
+ (connect timeout=None)'))
+
+To resolve this issue, add the IP addresses of Cortex XSOAR8 or Cortex XSIAM to the Splunk Cloud whitelist.
+You can find the relevant IP addresses at:
+[Cortex XSOAR Administrator Guide](https://docs-cortex.paloaltonetworks.com/r/Cortex-XSOAR/8/Cortex-XSOAR-Administrator-Guide/Enable-Access-to-Cortex-XSOAR)
+under **Used for communication between Cortex XSOAR and customer resources**. Choose the IP address corresponding to your Cortex XSOAR region.
\ No newline at end of file
From 2abddeb516aaed6424ef5775d88c5022d39559b5 Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Tue, 20 Feb 2024 14:30:31 +0200
Subject: [PATCH 053/272] AWS Cloud Watch logs - fix proxy issue (#32956)
(#33024)
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
* fix proxy issue
* format yml
* Update Packs/AWS-CloudWatchLogs/Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml
* Update Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md
* format and ReleaseNotes
* ReleaseNotes
* add 1_2_20
---------
Co-authored-by: Fábio Dias
Co-authored-by: merit-maita <49760643+merit-maita@users.noreply.github.com>
Co-authored-by: Moshe Eichler <78307768+MosheEichler@users.noreply.github.com>
---
Packs/AWS-CloudWatchLogs/CONTRIBUTORS.json | 3 +++
.../AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml | 9 +++++++--
Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md | 3 ++-
Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_20.md | 7 +++++++
Packs/AWS-CloudWatchLogs/pack_metadata.json | 4 ++--
5 files changed, 21 insertions(+), 5 deletions(-)
create mode 100644 Packs/AWS-CloudWatchLogs/CONTRIBUTORS.json
create mode 100644 Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_20.md
diff --git a/Packs/AWS-CloudWatchLogs/CONTRIBUTORS.json b/Packs/AWS-CloudWatchLogs/CONTRIBUTORS.json
new file mode 100644
index 000000000000..ce9d08a30890
--- /dev/null
+++ b/Packs/AWS-CloudWatchLogs/CONTRIBUTORS.json
@@ -0,0 +1,3 @@
+[
+ "Fabio Dias"
+]
diff --git a/Packs/AWS-CloudWatchLogs/Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml b/Packs/AWS-CloudWatchLogs/Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml
index 688073e08848..5d9018f63cc4 100644
--- a/Packs/AWS-CloudWatchLogs/Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml
+++ b/Packs/AWS-CloudWatchLogs/Integrations/AWS-CloudWatchLogs/AWS-CloudWatchLogs.yml
@@ -65,6 +65,11 @@ configuration:
section: Connect
advanced: true
required: false
+- display: Use system proxy settings
+ name: proxy
+ type: 8
+ required: false
+ section: Connect
script:
script: ''
type: python
@@ -335,7 +340,7 @@ script:
description: The name of the log stream.
- name: timestamp
required: true
- description: The time the event occurred, expressed as the number of milliseconds fter Jan 1, 1970 00:00:00 UTC. (Unix Time)
+ description: The time the event occurred, expressed as the number of milliseconds fter Jan 1, 1970 00:00:00 UTC. (Unix Time).
- name: message
required: true
description: The raw event message.
@@ -447,7 +452,7 @@ script:
description: The name of the log group.
type: string
description: Lists the specified metric filters. You can list all the metric filters or filter the results by log name, prefix, metric name, or metric namespace.
- dockerimage: demisto/boto3py3:1.0.0.87655
+ dockerimage: demisto/boto3py3:1.0.0.88114
tests:
- No Tests
fromversion: 5.0.0
diff --git a/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md b/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md
index 9078c2c905c1..1a451b1b6985 100644
--- a/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md
+++ b/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_19.md
@@ -3,4 +3,5 @@
##### AWS - CloudWatchLogs
-- Updated the Docker image to: *demisto/boto3py3:1.0.0.87655*.
+- Updated the Docker image to: demisto/boto3py3:1.0.0.87655.
+
diff --git a/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_20.md b/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_20.md
new file mode 100644
index 000000000000..deb4c79ae5aa
--- /dev/null
+++ b/Packs/AWS-CloudWatchLogs/ReleaseNotes/1_2_20.md
@@ -0,0 +1,7 @@
+
+#### Integrations
+
+##### AWS - CloudWatchLogs
+
+- Added the *Use system proxy settings* parameter.
+- Updated the Docker image to: *demisto/boto3py3:1.0.0.88114*.
diff --git a/Packs/AWS-CloudWatchLogs/pack_metadata.json b/Packs/AWS-CloudWatchLogs/pack_metadata.json
index ac7edd3c9b04..8168a7f79e79 100644
--- a/Packs/AWS-CloudWatchLogs/pack_metadata.json
+++ b/Packs/AWS-CloudWatchLogs/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "AWS - CloudWatchLogs",
"description": "Amazon Web Services CloudWatch Logs (logs).",
"support": "xsoar",
- "currentVersion": "1.2.19",
+ "currentVersion": "1.2.20",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
@@ -18,4 +18,4 @@
"marketplacev2",
"xpanse"
]
-}
\ No newline at end of file
+}
From 2510e4cedbeb3f18dcf9f4cf2d63811ed45d0c46 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Tue, 20 Feb 2024 14:54:05 +0200
Subject: [PATCH 054/272] fix + RN (#32990)
---
Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.py | 6 ++----
.../ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.yml | 2 +-
Packs/ServiceNow/ReleaseNotes/2_5_54.md | 7 +++++++
Packs/ServiceNow/pack_metadata.json | 2 +-
4 files changed, 11 insertions(+), 6 deletions(-)
create mode 100644 Packs/ServiceNow/ReleaseNotes/2_5_54.md
diff --git a/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.py b/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.py
index e16f4af02853..dade0ad6689d 100644
--- a/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.py
+++ b/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.py
@@ -1,7 +1,6 @@
import demistomock as demisto # noqa: F401
from CommonServerPython import * # noqa: F401
import re
-import shutil
from collections.abc import Callable, Iterable
@@ -709,8 +708,8 @@ def send_request(self, path: str, method: str = 'GET', body: dict | None = None,
try:
file_entry = file['id']
file_name = file['name']
- shutil.copy(demisto.getFilePath(file_entry)['path'], file_name)
- with open(file_name, 'rb') as f:
+ file_path = demisto.getFilePath(file_entry)['path']
+ with open(file_path, 'rb') as f:
file_info = (file_name, f, self.get_content_type(file_name))
if self.use_oauth:
access_token = self.snow_client.get_access_token()
@@ -723,7 +722,6 @@ def send_request(self, path: str, method: str = 'GET', body: dict | None = None,
res = requests.request(method, url, headers=headers, data=body, params=params,
files={'file': file_info}, auth=self._auth,
verify=self._verify, proxies=self._proxies)
- shutil.rmtree(demisto.getFilePath(file_entry)['name'], ignore_errors=True)
except Exception as err:
raise Exception('Failed to upload file - ' + str(err))
else:
diff --git a/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.yml b/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.yml
index aea11526c403..203187ff0d66 100644
--- a/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.yml
+++ b/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.yml
@@ -1610,7 +1610,7 @@ script:
- contextPath: ServiceNow.Generic.Response
description: Generic response to servicenow api.
type: string
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
ismappable: true
isremotesyncin: true
diff --git a/Packs/ServiceNow/ReleaseNotes/2_5_54.md b/Packs/ServiceNow/ReleaseNotes/2_5_54.md
new file mode 100644
index 000000000000..4e3fd141b79d
--- /dev/null
+++ b/Packs/ServiceNow/ReleaseNotes/2_5_54.md
@@ -0,0 +1,7 @@
+
+#### Integrations
+
+##### ServiceNow v2
+
+- Fixed an issue where the ***servicenow-upload-file*** command failed in case the file name contained invalid characters.
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
\ No newline at end of file
diff --git a/Packs/ServiceNow/pack_metadata.json b/Packs/ServiceNow/pack_metadata.json
index 24af09c0df5f..876ef3d88ae7 100644
--- a/Packs/ServiceNow/pack_metadata.json
+++ b/Packs/ServiceNow/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "ServiceNow",
"description": "Use The ServiceNow IT Service Management (ITSM) solution to modernize the way you manage and deliver services to your users.",
"support": "xsoar",
- "currentVersion": "2.5.53",
+ "currentVersion": "2.5.54",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 6b2e5afe980bc182350ab1cae957ca0f237355b8 Mon Sep 17 00:00:00 2001
From: Moshe Eichler <78307768+MosheEichler@users.noreply.github.com>
Date: Tue, 20 Feb 2024 15:29:08 +0200
Subject: [PATCH 055/272] Add nightly ok label workflow (#32876)
* Add nightly ran GitHub workflow
* change label name
* change label name
* update message
* remove continue on error
* changed gitlab
* update workflow
* change name
* typo
* Update on call to Edri&Polishuk (#32964)
* bug - Cortex IR resolved incidents not mirrored correctly (#32856)
* bug - Cortex IR resolved incidents not mirrored correctly
* Possible fix
* RN
* Bump pack from version CortexXDR to 6.1.16.
* pre commit
* rn
* pre-commit
* fix test
* pre commit
---------
Co-authored-by: Content Bot
* Update Docker Image To demisto/taxii-server (#32897)
* Updated Metadata Of Pack CybleThreatIntel
* Added release notes to pack CybleThreatIntel
* Packs/CybleThreatIntel/Integrations/CybleThreatIntel/CybleThreatIntel.yml Docker image update
* EXPANDR-8026: Azure Remediation Bug Fix and Improvements (#32882) (#32941)
* update files
* RN
* RN part 2
* Apply suggestions from code review
---------
Co-authored-by: johnnywilkes <32227961+johnnywilkes@users.noreply.github.com>
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
Co-authored-by: Yuval Cohen <86777474+yucohen@users.noreply.github.com>
* change to run
* cr fixes
* fix git diff
* add git checkout
* origin
* github event
* chckout
* master
* GITHUB_REF
* change name
* only master
* fetch origin master
* remove print
* chekcout
* 0
* fi
* add origin
* fix syntax
* revert gitlab
* add if
* change else
* curl brackets
* remove n
* $GITHUB_OUTPUT
* gitlab change
* print
* revert
* add changed files null
* commit
* echo
* comment
* without grep
* fix
* new line
* gitlab changed
* remove ^
* remove "
* gitlab/ci
* use *
* GITLAB_CHANGED_FILES
* fix check
* console log outputs
* fix logs
* add $
* remove logs
* remove true
* revert
* log
* impement if
* add brackets
* gitlab
* revert gitlab
---------
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
Co-authored-by: Content Bot
Co-authored-by: content-bot <55035720+content-bot@users.noreply.github.com>
Co-authored-by: johnnywilkes <32227961+johnnywilkes@users.noreply.github.com>
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
Co-authored-by: Yuval Cohen <86777474+yucohen@users.noreply.github.com>
---
.github/workflows/ckeck-nightly-ok-label.yml | 50 ++++++++++++++++++++
1 file changed, 50 insertions(+)
create mode 100644 .github/workflows/ckeck-nightly-ok-label.yml
diff --git a/.github/workflows/ckeck-nightly-ok-label.yml b/.github/workflows/ckeck-nightly-ok-label.yml
new file mode 100644
index 000000000000..70959ad08eac
--- /dev/null
+++ b/.github/workflows/ckeck-nightly-ok-label.yml
@@ -0,0 +1,50 @@
+name: Check nightly-ok label
+
+on:
+ pull_request:
+ types: [opened, synchronize, labeled, unlabeled]
+
+jobs:
+ check_label:
+ runs-on: ubuntu-latest
+
+ steps:
+ - name: Checkout repo
+ uses: actions/checkout@v4
+ with:
+ fetch-depth: 0
+
+ - name: Check if files under .gitlab directory are changed
+ id: check-changes
+ run: |
+ CHANGED_FILES=$(git diff --name-only origin/master origin/${{ github.head_ref || github.ref_name }})
+ echo "All changed files:"
+ echo "${CHANGED_FILES}"
+ GITLAB_CHANGED_FILES=$( [[ $CHANGED_FILES == *".gitlab/ci"* ]] && echo true || echo false)
+ echo "Files in the.gitlab folder have changed: ${GITLAB_CHANGED_FILES}"
+ echo "gitlab_changed_files=$GITLAB_CHANGED_FILES" >> $GITHUB_OUTPUT
+ if [[ $GITLAB_CHANGED_FILES == true ]]; then
+ echo 'Files under .gitlab folder has changed, Will check if the PR has the `nightly-ok` label.'
+ else
+ echo 'Files in the.gitlab folder have not been changed.'
+ fi
+
+ - name: Check if PR has the nightly-ok label
+ uses: actions/github-script@v7
+ id: check-label
+ with:
+ script: |
+ const gitlabChangedFiles = ${{ steps.check-changes.outputs.gitlab_changed_files }};
+ if(gitlabChangedFiles) {
+ console.log('Files under .gitlab folder has changed, Will check if the PR has the `nightly-ok` label.');
+ const labels = context.payload.pull_request.labels.map(label => label.name);
+ const hasLabel = labels.includes('nightly-ok');
+ if (hasLabel) {
+ console.log('All good, the PR has the `nightly-ok` label.');
+ } else {
+ console.log('PR does not have the `nightly-ok` label. It is required when changing files under the `.gitlab` directory. Please run nightly using the Utils/gitlab_triggers/trigger_content_nightly_build.sh script, check that succeeded, and add the `nightly-ok` label');
+ process.exit(1); // Exit with failure status if label is missing
+ }
+ } else {
+ console.log('Files in the.gitlab folder have not been changed.');
+ }
From 2d351cec065344c955940c57aa40db026a77bfc8 Mon Sep 17 00:00:00 2001
From: ilaner <88267954+ilaner@users.noreply.github.com>
Date: Tue, 20 Feb 2024 17:18:44 +0200
Subject: [PATCH 056/272] [FeedElasticSearch] Fix ids in last run (#32778)
---
.../FeedElasticsearch/FeedElasticsearch.py | 35 +++++++++++++------
.../FeedElasticsearch_test.py | 2 +-
Packs/FeedElasticsearch/ReleaseNotes/1_1_5.md | 6 ++++
Packs/FeedElasticsearch/pack_metadata.json | 2 +-
4 files changed, 33 insertions(+), 12 deletions(-)
create mode 100644 Packs/FeedElasticsearch/ReleaseNotes/1_1_5.md
diff --git a/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch.py b/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch.py
index b217bd9e652e..ce7edf37783e 100644
--- a/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch.py
+++ b/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch.py
@@ -210,23 +210,33 @@ def get_demisto_indicators(search, tags, tlp_color):
def update_last_fetch(client, ioc_lst):
- last_calculated_time = None
+ demisto.debug(f"ElasticSearchFeed: Length of the indicators to fetch is: {len(ioc_lst)}")
+ last_calculated_timestamp = None
last_ids = []
for ioc in reversed(ioc_lst):
calculate_time = dateparser.parse(ioc.get(client.time_field))
- if calculate_time and (not last_calculated_time or calculate_time >= last_calculated_time):
- last_calculated_time = calculate_time
+ if not calculate_time:
+ demisto.info(f"ioc {ioc.get('name')} if missing {client.time_field}")
+ break
+ calculate_timestamp = int(calculate_time.timestamp() * 1000)
+ if not last_calculated_timestamp or calculate_timestamp >= last_calculated_timestamp:
+ last_calculated_timestamp = calculate_timestamp
last_ids.append(ioc.get('id'))
else:
+ demisto.debug(f"FeedElasticSearch: {last_calculated_timestamp=}")
+ demisto.debug(f"FeedElasticSearch: {calculate_timestamp=}")
break
- if last_calculated_time is None:
- last_calculated_time = datetime.now()
- return last_calculated_time, last_ids
+ if last_calculated_timestamp is None:
+ last_calculated_timestamp = int(datetime.now().timestamp() * 1000)
+ demisto.info(f"FeedElasticSearch: The length of the indicators of the last time: {len(last_ids)}")
+ demisto.debug(f"FeedElasticSearch: The last ids which were fetched with the same last time: {last_ids}")
+ return last_calculated_timestamp, last_ids
def fetch_indicators_command(client, feed_type, src_val, src_type, default_type, last_fetch, fetch_limit):
"""Implements fetch-indicators command"""
last_fetch_timestamp = get_last_fetch_timestamp(last_fetch, client.time_method, client.fetch_time)
+ demisto.debug(f"FeedElasticSearch: last_fetch_timestamp is: {last_fetch_timestamp}")
prev_iocs_ids = demisto.getLastRun().get("ids", [])
now = datetime.now()
ioc_lst: list = []
@@ -248,14 +258,16 @@ def fetch_indicators_command(client, feed_type, src_val, src_type, default_type,
if ioc_lst:
for b in batch(ioc_lst, batch_size=2000):
demisto.createIndicators(b)
- last_calculated_time, last_ids = update_last_fetch(client, ioc_lst)
+ last_calculated_timestamp, last_ids = update_last_fetch(client, ioc_lst)
+ if str(last_calculated_timestamp) == last_fetch:
+ last_ids.extend(prev_iocs_ids)
if ioc_enrch_lst:
ioc_enrch_batches = create_enrichment_batches(ioc_enrch_lst)
for enrch_batch in ioc_enrch_batches:
# ensure batch sizes don't exceed 2000
for b in batch(enrch_batch, batch_size=2000):
demisto.createIndicators(b)
- demisto.setLastRun({'time': int(last_calculated_time.timestamp() * 1000), 'ids': last_ids})
+ demisto.setLastRun({'time': str(last_calculated_timestamp), 'ids': last_ids})
def get_last_fetch_timestamp(last_fetch, time_method, fetch_time):
@@ -263,7 +275,9 @@ def get_last_fetch_timestamp(last_fetch, time_method, fetch_time):
if last_fetch:
last_fetch_timestamp = last_fetch
else:
- last_fetch, _ = parse_date_range(date_range=fetch_time, utc=False)
+ last_fetch = dateparser.parse(fetch_time)
+ if not last_fetch:
+ raise ValueError("Failed to parse the fetch time")
# if timestamp: get the last fetch to the correct format of timestamp
last_fetch_timestamp = int(last_fetch.timestamp() * 1000)
if 'Timestamp - Seconds' in time_method:
@@ -284,7 +298,8 @@ def get_scan_generic_format(client, now, last_fetch_timestamp=None, fetch_limit=
range_field = {
time_field: {'gte': last_fetch_timestamp, 'lte': now}} if last_fetch_timestamp else {
time_field: {'lte': now}}
- search = Search(using=es, index=fetch_index).filter({'range': range_field}).extra(size=fetch_limit).sort().query(query)
+ search = Search(using=es, index=fetch_index).filter({'range': range_field}).extra(
+ size=fetch_limit).sort({time_field: {'order': 'asc'}}).query(query)
else:
search = Search(using=es, index=fetch_index).query(QueryString(query=client.query))
return search
diff --git a/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch_test.py b/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch_test.py
index 88b4b494de4c..f5f4f05f644f 100644
--- a/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch_test.py
+++ b/Packs/FeedElasticsearch/Integrations/FeedElasticsearch/FeedElasticsearch_test.py
@@ -307,4 +307,4 @@ def test_last_run():
{"id": "4", "calculatedTime": "2023-01-17T14:33:00.000Z"}]
last_update, last_ids = update_last_fetch(MockClient(), ioc_lst)
assert set(last_ids) == {"4", "3"}
- assert last_update.isoformat() == "2023-01-17T14:33:00+00:00"
+ assert datetime.fromtimestamp(last_update // 1000).isoformat() == "2023-01-17T14:33:00"
diff --git a/Packs/FeedElasticsearch/ReleaseNotes/1_1_5.md b/Packs/FeedElasticsearch/ReleaseNotes/1_1_5.md
new file mode 100644
index 000000000000..99155146fc6f
--- /dev/null
+++ b/Packs/FeedElasticsearch/ReleaseNotes/1_1_5.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Elasticsearch Feed
+
+- Fixed an issue where the `fetch-indicators` time calculation was inaccurate.
diff --git a/Packs/FeedElasticsearch/pack_metadata.json b/Packs/FeedElasticsearch/pack_metadata.json
index 120f74204d14..0c6bfa76440f 100644
--- a/Packs/FeedElasticsearch/pack_metadata.json
+++ b/Packs/FeedElasticsearch/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Elasticsearch Feed",
"description": "Indicators feed from Elasticsearch database",
"support": "xsoar",
- "currentVersion": "1.1.4",
+ "currentVersion": "1.1.5",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From b1329c7404c5639d2d6aabd13688f912f1393173 Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Wed, 21 Feb 2024 08:59:31 +0200
Subject: [PATCH 057/272] Update Docker Image To demisto/crypto (#33042)
* Updated Metadata Of Pack MicrosoftTeams
* Added release notes to pack MicrosoftTeams
* Packs/MicrosoftTeams/Integrations/MicrosoftTeamsManagement/MicrosoftTeamsManagement.yml Docker image update
---
.../MicrosoftTeamsManagement/MicrosoftTeamsManagement.yml | 2 +-
Packs/MicrosoftTeams/ReleaseNotes/1_4_51.md | 3 +++
Packs/MicrosoftTeams/pack_metadata.json | 2 +-
3 files changed, 5 insertions(+), 2 deletions(-)
create mode 100644 Packs/MicrosoftTeams/ReleaseNotes/1_4_51.md
diff --git a/Packs/MicrosoftTeams/Integrations/MicrosoftTeamsManagement/MicrosoftTeamsManagement.yml b/Packs/MicrosoftTeams/Integrations/MicrosoftTeamsManagement/MicrosoftTeamsManagement.yml
index 8aa876359f85..86cbd5b5ce27 100644
--- a/Packs/MicrosoftTeams/Integrations/MicrosoftTeamsManagement/MicrosoftTeamsManagement.yml
+++ b/Packs/MicrosoftTeams/Integrations/MicrosoftTeamsManagement/MicrosoftTeamsManagement.yml
@@ -679,7 +679,7 @@ script:
- contextPath: MicrosoftTeams.Team.description
description: An optional description for the group.
type: String
- dockerimage: demisto/crypto:1.0.0.83343
+ dockerimage: demisto/crypto:1.0.0.87358
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/MicrosoftTeams/ReleaseNotes/1_4_51.md b/Packs/MicrosoftTeams/ReleaseNotes/1_4_51.md
new file mode 100644
index 000000000000..f71b8dfc6313
--- /dev/null
+++ b/Packs/MicrosoftTeams/ReleaseNotes/1_4_51.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Microsoft Teams Management
+- Updated the Docker image to: *demisto/crypto:1.0.0.87358*.
diff --git a/Packs/MicrosoftTeams/pack_metadata.json b/Packs/MicrosoftTeams/pack_metadata.json
index f33c6c004c7d..440c13ba4b05 100644
--- a/Packs/MicrosoftTeams/pack_metadata.json
+++ b/Packs/MicrosoftTeams/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Microsoft Teams",
"description": "Send messages and notifications to your team members.",
"support": "xsoar",
- "currentVersion": "1.4.50",
+ "currentVersion": "1.4.51",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 0b9e16427221dfdc54dbfa271a94356c9a5449ef Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Wed, 21 Feb 2024 09:02:18 +0200
Subject: [PATCH 058/272] Update Docker Image To demisto/python3 (#33040)
* Updated Metadata Of Pack Darktrace
* Added release notes to pack Darktrace
* Packs/Darktrace/Integrations/DarktraceAdmin/DarktraceAdmin.yml Docker image update
* Packs/Darktrace/Integrations/DarktraceMBs/DarktraceMBs.yml Docker image update
* Packs/Darktrace/Integrations/DarktraceAIA/DarktraceAIA.yml Docker image update
* Updated Metadata Of Pack ForescoutEyeInspect
* Added release notes to pack ForescoutEyeInspect
* Packs/ForescoutEyeInspect/Integrations/ForescoutEyeInspect/ForescoutEyeInspect.yml Docker image update
* Updated Metadata Of Pack Stairwell
* Added release notes to pack Stairwell
* Packs/Stairwell/Integrations/Inception/Inception.yml Docker image update
* Updated Metadata Of Pack SecureWorks
* Added release notes to pack SecureWorks
* Packs/SecureWorks/Integrations/TaegisXDRv2/TaegisXDRv2.yml Docker image update
* Updated Metadata Of Pack BmcITSM
* Added release notes to pack BmcITSM
* Packs/BmcITSM/Integrations/BmcITSM/BmcITSM.yml Docker image update
* Updated Metadata Of Pack Tessian
* Added release notes to pack Tessian
* Packs/Tessian/Integrations/Tessian/Tessian.yml Docker image update
* Updated Metadata Of Pack Cisco-umbrella-cloud-security
* Added release notes to pack Cisco-umbrella-cloud-security
* Packs/Cisco-umbrella-cloud-security/Integrations/CiscoUmbrellaCloudSecurityv2/CiscoUmbrellaCloudSecurityv2.yml Docker image update
* Updated Metadata Of Pack SingleConnect
* Added release notes to pack SingleConnect
* Packs/SingleConnect/Integrations/SingleConnect/SingleConnect.yml Docker image update
---
Packs/BmcITSM/Integrations/BmcITSM/BmcITSM.yml | 2 +-
Packs/BmcITSM/ReleaseNotes/1_0_21.md | 3 +++
Packs/BmcITSM/pack_metadata.json | 2 +-
.../CiscoUmbrellaCloudSecurityv2.yml | 2 +-
Packs/Cisco-umbrella-cloud-security/ReleaseNotes/2_0_8.md | 3 +++
Packs/Cisco-umbrella-cloud-security/pack_metadata.json | 2 +-
Packs/Darktrace/Integrations/DarktraceAIA/DarktraceAIA.yml | 2 +-
.../Integrations/DarktraceAdmin/DarktraceAdmin.yml | 2 +-
Packs/Darktrace/Integrations/DarktraceMBs/DarktraceMBs.yml | 2 +-
Packs/Darktrace/ReleaseNotes/3_0_10.md | 7 +++++++
Packs/Darktrace/pack_metadata.json | 2 +-
.../ForescoutEyeInspect/ForescoutEyeInspect.yml | 2 +-
Packs/ForescoutEyeInspect/ReleaseNotes/1_0_21.md | 3 +++
Packs/ForescoutEyeInspect/pack_metadata.json | 2 +-
Packs/SecureWorks/Integrations/TaegisXDRv2/TaegisXDRv2.yml | 2 +-
Packs/SecureWorks/ReleaseNotes/5_0_8.md | 3 +++
Packs/SecureWorks/pack_metadata.json | 2 +-
.../Integrations/SingleConnect/SingleConnect.yml | 2 +-
Packs/SingleConnect/ReleaseNotes/1_0_15.md | 3 +++
Packs/SingleConnect/pack_metadata.json | 2 +-
Packs/Stairwell/Integrations/Inception/Inception.yml | 2 +-
Packs/Stairwell/ReleaseNotes/1_0_16.md | 3 +++
Packs/Stairwell/pack_metadata.json | 2 +-
Packs/Tessian/Integrations/Tessian/Tessian.yml | 2 +-
Packs/Tessian/ReleaseNotes/1_0_4.md | 3 +++
Packs/Tessian/pack_metadata.json | 2 +-
26 files changed, 46 insertions(+), 18 deletions(-)
create mode 100644 Packs/BmcITSM/ReleaseNotes/1_0_21.md
create mode 100644 Packs/Cisco-umbrella-cloud-security/ReleaseNotes/2_0_8.md
create mode 100644 Packs/Darktrace/ReleaseNotes/3_0_10.md
create mode 100644 Packs/ForescoutEyeInspect/ReleaseNotes/1_0_21.md
create mode 100644 Packs/SecureWorks/ReleaseNotes/5_0_8.md
create mode 100644 Packs/SingleConnect/ReleaseNotes/1_0_15.md
create mode 100644 Packs/Stairwell/ReleaseNotes/1_0_16.md
create mode 100644 Packs/Tessian/ReleaseNotes/1_0_4.md
diff --git a/Packs/BmcITSM/Integrations/BmcITSM/BmcITSM.yml b/Packs/BmcITSM/Integrations/BmcITSM/BmcITSM.yml
index 960566803b57..c6677cdfae79 100644
--- a/Packs/BmcITSM/Integrations/BmcITSM/BmcITSM.yml
+++ b/Packs/BmcITSM/Integrations/BmcITSM/BmcITSM.yml
@@ -168,7 +168,7 @@ script:
script: ""
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
commands:
- name: bmc-itsm-user-list
description: Retrieves a list of user profiles from BMC Helix ITSM. The records are retrieved by the query argument or by the filtering arguments. When using filtering arguments, each one defines a 'LIKE' operation and an 'AND' operator is used between them. To see the entire JSON then you can use the raw_response=true at the end of the command.
diff --git a/Packs/BmcITSM/ReleaseNotes/1_0_21.md b/Packs/BmcITSM/ReleaseNotes/1_0_21.md
new file mode 100644
index 000000000000..cdbe3660a348
--- /dev/null
+++ b/Packs/BmcITSM/ReleaseNotes/1_0_21.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### BMC Helix ITSM
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/BmcITSM/pack_metadata.json b/Packs/BmcITSM/pack_metadata.json
index 8d096e7c5795..db114ce4f13c 100644
--- a/Packs/BmcITSM/pack_metadata.json
+++ b/Packs/BmcITSM/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "BMC Helix ITSM",
"description": "BMC Helix ITSM allows customers to manage service request, incident, change request, task, problem investigation and known error tickets.",
"support": "xsoar",
- "currentVersion": "1.0.20",
+ "currentVersion": "1.0.21",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Cisco-umbrella-cloud-security/Integrations/CiscoUmbrellaCloudSecurityv2/CiscoUmbrellaCloudSecurityv2.yml b/Packs/Cisco-umbrella-cloud-security/Integrations/CiscoUmbrellaCloudSecurityv2/CiscoUmbrellaCloudSecurityv2.yml
index f3b7588ab93e..77601f3559c7 100644
--- a/Packs/Cisco-umbrella-cloud-security/Integrations/CiscoUmbrellaCloudSecurityv2/CiscoUmbrellaCloudSecurityv2.yml
+++ b/Packs/Cisco-umbrella-cloud-security/Integrations/CiscoUmbrellaCloudSecurityv2/CiscoUmbrellaCloudSecurityv2.yml
@@ -483,7 +483,7 @@ script:
script: ''
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: false
fromversion: 6.9.0
tests:
diff --git a/Packs/Cisco-umbrella-cloud-security/ReleaseNotes/2_0_8.md b/Packs/Cisco-umbrella-cloud-security/ReleaseNotes/2_0_8.md
new file mode 100644
index 000000000000..bebf1a6fb2fd
--- /dev/null
+++ b/Packs/Cisco-umbrella-cloud-security/ReleaseNotes/2_0_8.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Cisco Umbrella Cloud Security v2
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/Cisco-umbrella-cloud-security/pack_metadata.json b/Packs/Cisco-umbrella-cloud-security/pack_metadata.json
index 353597663e1f..26375fc39992 100644
--- a/Packs/Cisco-umbrella-cloud-security/pack_metadata.json
+++ b/Packs/Cisco-umbrella-cloud-security/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Cisco Umbrella cloud security",
"description": "Basic integration with Cisco Umbrella that allows you to add domains to destination lists (e.g. global block / allow)",
"support": "xsoar",
- "currentVersion": "2.0.7",
+ "currentVersion": "2.0.8",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/Darktrace/Integrations/DarktraceAIA/DarktraceAIA.yml b/Packs/Darktrace/Integrations/DarktraceAIA/DarktraceAIA.yml
index d74f5c3f6e00..22c63300f7ba 100644
--- a/Packs/Darktrace/Integrations/DarktraceAIA/DarktraceAIA.yml
+++ b/Packs/Darktrace/Integrations/DarktraceAIA/DarktraceAIA.yml
@@ -205,7 +205,7 @@ script:
- contextPath: Darktrace.AIAnalyst.groupCategory
description: Group category.
type: String
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/Darktrace/Integrations/DarktraceAdmin/DarktraceAdmin.yml b/Packs/Darktrace/Integrations/DarktraceAdmin/DarktraceAdmin.yml
index ffc7e4515582..cbd53562446d 100644
--- a/Packs/Darktrace/Integrations/DarktraceAdmin/DarktraceAdmin.yml
+++ b/Packs/Darktrace/Integrations/DarktraceAdmin/DarktraceAdmin.yml
@@ -263,7 +263,7 @@ script:
- contextPath: Darktrace.Device.response
description: POST action message response.
type: String
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/Darktrace/Integrations/DarktraceMBs/DarktraceMBs.yml b/Packs/Darktrace/Integrations/DarktraceMBs/DarktraceMBs.yml
index d50eb00c82b0..0c4fadb679fa 100644
--- a/Packs/Darktrace/Integrations/DarktraceMBs/DarktraceMBs.yml
+++ b/Packs/Darktrace/Integrations/DarktraceMBs/DarktraceMBs.yml
@@ -238,7 +238,7 @@ script:
- contextPath: Darktrace.Model.Component
description: A dictionary of the details of the model. Each model might have different keys. It is recommended to run the command once to check the relevant outputs in context.
type: Unknown
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
runonce: false
script: '-'
diff --git a/Packs/Darktrace/ReleaseNotes/3_0_10.md b/Packs/Darktrace/ReleaseNotes/3_0_10.md
new file mode 100644
index 000000000000..500c440301a8
--- /dev/null
+++ b/Packs/Darktrace/ReleaseNotes/3_0_10.md
@@ -0,0 +1,7 @@
+#### Integrations
+##### Darktrace Admin
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
+##### Darktrace Model Breaches
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
+##### Darktrace AI Analyst
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/Darktrace/pack_metadata.json b/Packs/Darktrace/pack_metadata.json
index 0c141a2b0095..0635f12a65c2 100644
--- a/Packs/Darktrace/pack_metadata.json
+++ b/Packs/Darktrace/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Darktrace",
"description": "Populates Darktrace Model Breaches and AI Analyst Events in Cortex XSOAR, allowing for cross-platform automated investigation and response.",
"support": "partner",
- "currentVersion": "3.0.9",
+ "currentVersion": "3.0.10",
"fromVersion": "5.0.0",
"author": "Darktrace",
"githubUser": "",
diff --git a/Packs/ForescoutEyeInspect/Integrations/ForescoutEyeInspect/ForescoutEyeInspect.yml b/Packs/ForescoutEyeInspect/Integrations/ForescoutEyeInspect/ForescoutEyeInspect.yml
index 10487bffaceb..04ce7065411e 100644
--- a/Packs/ForescoutEyeInspect/Integrations/ForescoutEyeInspect/ForescoutEyeInspect.yml
+++ b/Packs/ForescoutEyeInspect/Integrations/ForescoutEyeInspect/ForescoutEyeInspect.yml
@@ -1113,7 +1113,7 @@ script:
- contextPath: ForescoutEyeInspect.HostChangeLog.host_mac_addresses
description: The MAC addresses associated to the host.
type: String
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
runonce: false
script: "-"
diff --git a/Packs/ForescoutEyeInspect/ReleaseNotes/1_0_21.md b/Packs/ForescoutEyeInspect/ReleaseNotes/1_0_21.md
new file mode 100644
index 000000000000..87794da30223
--- /dev/null
+++ b/Packs/ForescoutEyeInspect/ReleaseNotes/1_0_21.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Forescout EyeInspect
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/ForescoutEyeInspect/pack_metadata.json b/Packs/ForescoutEyeInspect/pack_metadata.json
index 899cb4c29805..550b2fa3c6bb 100644
--- a/Packs/ForescoutEyeInspect/pack_metadata.json
+++ b/Packs/ForescoutEyeInspect/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Forescout EyeInspect",
"description": "Get in-depth device visibility for OT networks",
"support": "xsoar",
- "currentVersion": "1.0.20",
+ "currentVersion": "1.0.21",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
diff --git a/Packs/SecureWorks/Integrations/TaegisXDRv2/TaegisXDRv2.yml b/Packs/SecureWorks/Integrations/TaegisXDRv2/TaegisXDRv2.yml
index f084765aa6db..b6be3280a953 100644
--- a/Packs/SecureWorks/Integrations/TaegisXDRv2/TaegisXDRv2.yml
+++ b/Packs/SecureWorks/Integrations/TaegisXDRv2/TaegisXDRv2.yml
@@ -547,7 +547,7 @@ script:
- contextPath: TaegisXDR.InvestigationEvidenceUpdate
description: The investigation that received the update.
description: Add alerts and events to an existing investigation.
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
runonce: false
subtype: python3
diff --git a/Packs/SecureWorks/ReleaseNotes/5_0_8.md b/Packs/SecureWorks/ReleaseNotes/5_0_8.md
new file mode 100644
index 000000000000..868e637918fb
--- /dev/null
+++ b/Packs/SecureWorks/ReleaseNotes/5_0_8.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### TaegisXDR v2
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/SecureWorks/pack_metadata.json b/Packs/SecureWorks/pack_metadata.json
index 092a131d8d27..acb42c7a8ea7 100644
--- a/Packs/SecureWorks/pack_metadata.json
+++ b/Packs/SecureWorks/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Secureworks",
"description": "Provides access to the Secureworks CTP and Taegis XDR systems",
"support": "partner",
- "currentVersion": "5.0.7",
+ "currentVersion": "5.0.8",
"author": "Secureworks",
"url": "https://ctpx.secureworks.com",
"email": "support@secureworks.com",
diff --git a/Packs/SingleConnect/Integrations/SingleConnect/SingleConnect.yml b/Packs/SingleConnect/Integrations/SingleConnect/SingleConnect.yml
index a294976f6ea4..b1563b1effc1 100644
--- a/Packs/SingleConnect/Integrations/SingleConnect/SingleConnect.yml
+++ b/Packs/SingleConnect/Integrations/SingleConnect/SingleConnect.yml
@@ -269,7 +269,7 @@ script:
- contextPath: SingleConnect.SapmAccount.groupFullPath
description: The full path of the SAPM group that the account is under.
type: String
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
runonce: false
script: '-'
subtype: python3
diff --git a/Packs/SingleConnect/ReleaseNotes/1_0_15.md b/Packs/SingleConnect/ReleaseNotes/1_0_15.md
new file mode 100644
index 000000000000..aab381f2b3a7
--- /dev/null
+++ b/Packs/SingleConnect/ReleaseNotes/1_0_15.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Single Connect
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/SingleConnect/pack_metadata.json b/Packs/SingleConnect/pack_metadata.json
index ad74a1356567..1d463af0dffa 100644
--- a/Packs/SingleConnect/pack_metadata.json
+++ b/Packs/SingleConnect/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Single Connect",
"description": "Single Connect enables enterprises to remove static passwords stored in applications by instead keeping passwords in a secure password vault. It secures access to passwords through token-based authentication",
"support": "partner",
- "currentVersion": "1.0.14",
+ "currentVersion": "1.0.15",
"author": "Krontech",
"url": "https://kron.com.tr/en/single-connect",
"email": "",
diff --git a/Packs/Stairwell/Integrations/Inception/Inception.yml b/Packs/Stairwell/Integrations/Inception/Inception.yml
index a84d7805f826..aacb8cb2bb21 100644
--- a/Packs/Stairwell/Integrations/Inception/Inception.yml
+++ b/Packs/Stairwell/Integrations/Inception/Inception.yml
@@ -48,7 +48,7 @@ script:
script: '-'
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
fromversion: 6.5.0
tests:
- No tests (auto formatted)
diff --git a/Packs/Stairwell/ReleaseNotes/1_0_16.md b/Packs/Stairwell/ReleaseNotes/1_0_16.md
new file mode 100644
index 000000000000..d927a7af91c9
--- /dev/null
+++ b/Packs/Stairwell/ReleaseNotes/1_0_16.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Stairwell Inception
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/Stairwell/pack_metadata.json b/Packs/Stairwell/pack_metadata.json
index daf876c2047a..7d3e9c257c19 100644
--- a/Packs/Stairwell/pack_metadata.json
+++ b/Packs/Stairwell/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Stairwell",
"description": "Inception is a security intelligence engine that automates the continuous capture, storage, and analysis of executable files.",
"support": "partner",
- "currentVersion": "1.0.15",
+ "currentVersion": "1.0.16",
"author": "Stairwell",
"url": "https://www.stairwell.com",
"email": "support@stairwell.com",
diff --git a/Packs/Tessian/Integrations/Tessian/Tessian.yml b/Packs/Tessian/Integrations/Tessian/Tessian.yml
index 13b8a7995c45..ce7b0f88c93a 100644
--- a/Packs/Tessian/Integrations/Tessian/Tessian.yml
+++ b/Packs/Tessian/Integrations/Tessian/Tessian.yml
@@ -110,7 +110,7 @@ script:
script: '-'
type: python
subtype: python3
- dockerimage: demisto/python3:3.10.13.86272
+ dockerimage: demisto/python3:3.10.13.87159
fromversion: 6.10.0
tests:
- No tests (auto formatted)
diff --git a/Packs/Tessian/ReleaseNotes/1_0_4.md b/Packs/Tessian/ReleaseNotes/1_0_4.md
new file mode 100644
index 000000000000..7889c09e5d97
--- /dev/null
+++ b/Packs/Tessian/ReleaseNotes/1_0_4.md
@@ -0,0 +1,3 @@
+#### Integrations
+##### Tessian
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/Tessian/pack_metadata.json b/Packs/Tessian/pack_metadata.json
index 8a92a622c6e2..192f113972a9 100644
--- a/Packs/Tessian/pack_metadata.json
+++ b/Packs/Tessian/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Tessian",
"description": "Tessian's complete cloud email security platform defends customers against advanced phishing threats, and protects their sensitive data on email.",
"support": "partner",
- "currentVersion": "1.0.3",
+ "currentVersion": "1.0.4",
"author": "Tessian",
"url": "",
"email": "support@tessian.com",
From 07da899fcadd6601d5fe98a9c137f718c2f3be31 Mon Sep 17 00:00:00 2001
From: Dan Tavori <38749041+dantavori@users.noreply.github.com>
Date: Wed, 21 Feb 2024 11:55:11 +0200
Subject: [PATCH 059/272] fix base client execution metrics (#33044)
* fix base client execution metrics
* added test
---
Packs/Base/ReleaseNotes/1_33_35.md | 6 ++++++
.../CommonServerPython/CommonServerPython.py | 8 ++++++--
.../CommonServerPython/CommonServerPython_test.py | 15 +++++++++++++++
Packs/Base/pack_metadata.json | 2 +-
4 files changed, 28 insertions(+), 3 deletions(-)
create mode 100644 Packs/Base/ReleaseNotes/1_33_35.md
diff --git a/Packs/Base/ReleaseNotes/1_33_35.md b/Packs/Base/ReleaseNotes/1_33_35.md
new file mode 100644
index 000000000000..699fb5330fc2
--- /dev/null
+++ b/Packs/Base/ReleaseNotes/1_33_35.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### CommonServerPython
+
+- Fixed an issue where, in some cases, an AttributeError was raised during the destruction of a BaseClient object.
diff --git a/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py b/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py
index fc52b1e430d5..1d636774f7c8 100644
--- a/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py
+++ b/Packs/Base/Scripts/CommonServerPython/CommonServerPython.py
@@ -9226,9 +9226,13 @@ def client_error_handler(self, res):
def _return_execution_metrics_results(self):
""" Returns execution metrics results.
+ Might raise an AttributeError exception if execution_metrics is not initialized.
"""
- if self.execution_metrics.metrics:
- return_results(cast(CommandResults, self.execution_metrics.metrics))
+ try:
+ if self.execution_metrics.metrics:
+ return_results(cast(CommandResults, self.execution_metrics.metrics))
+ except AttributeError:
+ pass
def batch(iterable, batch_size=1):
diff --git a/Packs/Base/Scripts/CommonServerPython/CommonServerPython_test.py b/Packs/Base/Scripts/CommonServerPython/CommonServerPython_test.py
index f320123f3cc8..5786abb9feb8 100644
--- a/Packs/Base/Scripts/CommonServerPython/CommonServerPython_test.py
+++ b/Packs/Base/Scripts/CommonServerPython/CommonServerPython_test.py
@@ -3355,6 +3355,21 @@ def test_http_request_no_execution_metrics_results(cls, requests_mock, mocker):
del client
demisto_results_mock.assert_not_called
+ def test_base_client_subclass_without_execution_metrics_initialized(self):
+ """
+ Given: A BaseClient object and a subclass of it that does not initialize execution_metrics
+ When: deleting the client object
+ Then: Ensure the deletion does not raise any exception
+ """
+ from CommonServerPython import BaseClient
+
+ class Client(BaseClient):
+ def __init__(self):
+ pass
+
+ client = Client()
+ del client
+
@pytest.mark.skipif(not IS_PY3, reason='test not supported in py2')
def test_http_request_params_parser_quote(self, requests_mock):
"""
diff --git a/Packs/Base/pack_metadata.json b/Packs/Base/pack_metadata.json
index 6b58869f6b55..c96905e352c6 100644
--- a/Packs/Base/pack_metadata.json
+++ b/Packs/Base/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Base",
"description": "The base pack for Cortex XSOAR.",
"support": "xsoar",
- "currentVersion": "1.33.34",
+ "currentVersion": "1.33.35",
"author": "Cortex XSOAR",
"serverMinVersion": "6.0.0",
"url": "https://www.paloaltonetworks.com/cortex",
From 47e780b603ba83a103ef8ea4508a31031cc90008 Mon Sep 17 00:00:00 2001
From: samuelFain <65926551+samuelFain@users.noreply.github.com>
Date: Wed, 21 Feb 2024 13:53:30 +0200
Subject: [PATCH 060/272] [pre commit] Update coverage-analyze hook (#33035)
* change coverage-analyze to coverage-pytest-analyze
* Update hook
* Update .pre-commit-config_template.yaml
---
.pre-commit-config_template.yaml | 4 ++--
1 file changed, 2 insertions(+), 2 deletions(-)
diff --git a/.pre-commit-config_template.yaml b/.pre-commit-config_template.yaml
index 711b2748d49b..d58b53d9551c 100644
--- a/.pre-commit-config_template.yaml
+++ b/.pre-commit-config_template.yaml
@@ -204,8 +204,8 @@ repos:
pass_filenames: false
needs:
- pytest-in-docker
- - id: coverage-analyze
- name: coverage-analyze
+ - id: coverage-pytest-analyze
+ name: coverage-pytest-analyze
entry: demisto-sdk coverage-analyze
description: Running demisto-sdk coverage-analyze and showing a coverage report.
language: system
From 31845e438f93a099509d6ddc9e842a1741c9a1d3 Mon Sep 17 00:00:00 2001
From: merit-maita <49760643+merit-maita@users.noreply.github.com>
Date: Wed, 21 Feb 2024 15:58:44 +0200
Subject: [PATCH 061/272] Teams docs (#32949)
* updated readme
* edited description
* added rn
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
* lr
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/MicrosoftTeams_description.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* added unittest
---------
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---
.../MicrosoftTeams_description.md | 2 +-
.../Integrations/MicrosoftTeams/README.md | 145 ++++++++----------
Packs/MicrosoftTeams/ReleaseNotes/1_4_52.md | 6 +
Packs/MicrosoftTeams/pack_metadata.json | 2 +-
4 files changed, 74 insertions(+), 81 deletions(-)
create mode 100644 Packs/MicrosoftTeams/ReleaseNotes/1_4_52.md
diff --git a/Packs/MicrosoftTeams/Integrations/MicrosoftTeams/MicrosoftTeams_description.md b/Packs/MicrosoftTeams/Integrations/MicrosoftTeams/MicrosoftTeams_description.md
index 5170310217b0..97bcaecce186 100644
--- a/Packs/MicrosoftTeams/Integrations/MicrosoftTeams/MicrosoftTeams_description.md
+++ b/Packs/MicrosoftTeams/Integrations/MicrosoftTeams/MicrosoftTeams_description.md
@@ -1,5 +1,5 @@
Use the Microsoft Teams integration to send messages and notifications to your team members and create meetings.
-Note: the integration is supported in Cortex XSOAR 8 without using an engine.
+Note: The integration is supported in Cortex XSOAR 8 and Cortex XSIAM without using an engine.
To create an instance of the Microsoft Teams integration in Cortex XSOAR, complete the following:
diff --git a/Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md b/Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
index f097d239802c..8f4389b61c0d 100644
--- a/Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
+++ b/Packs/MicrosoftTeams/Integrations/MicrosoftTeams/README.md
@@ -2,15 +2,12 @@ Use the Microsoft Teams integration to send messages and notifications to your t
This integration was integrated and tested with version 1.0 of Microsoft Teams.
**Note:**
-- This integration is supported in Cortex XSOAR 8 and up without using an engine.
+- This integration is supported in Cortex XSOAR 8 and up and Cortex XSIAM without using an engine.
- The integration has the ability to run built-in Cortex XSOAR commands, through a mirrored channel. Make sure to pass the command in the chat exactly as typed in the CORTEX XSOAR CLI. For example: `!DeleteContext all=yes`. Use the command `mirror-investigation` to mirror/create a mirrored channel.
- For use cases where it is only needed to send messages to a specific channel, we recommend checking the [Microsoft Teams via Webhook Integration](https://xsoar.pan.dev/docs/reference/integrations/microsoft-teams-via-webhook), which has a simpler setup.
## Integration Architecture
Data is passed between Microsoft Teams and Cortex XSOAR through the bot that you will configure in Microsoft Teams. A webhook (that you will configure) receives the data from Teams and passes it to the messaging endpoint. The web server on which the integration runs in Cortex XSOAR listens to the messaging endpoint and processes the data from Teams. You can use an engine for communication between Teams and the Cortex XSOAR server. In order to mirror messages from Teams to Cortex XSOAR, the bot must be mentioned, using the @ symbol, in the message.
-- *Note* - In order to avoid mentioning the bot, if this was previously configured without adding the Bot ID, repeat the authentication flow and pay particular attention to the following steps:
- * Step 14 in [Using the App Studio](#using-the-app-studio).
- * Step 5 in [Using the Developer Portal](#using-the-developer-portal-1).
The web server for the integration runs within a long-running Docker container. Cortex XSOAR maps the Docker port to which the server listens, to the host port (to which Teams posts messages). For more information, see [our documentation](https://xsoar.pan.dev/docs/integrations/long-running#invoking-http-integrations-via-cortex-xsoar-servers-route-handling) and [Docker documentation](https://docs.docker.com/config/containers/container-networking/).
### Protocol Diagram
@@ -20,7 +17,7 @@ The web server for the integration runs within a long-running Docker container.
- The messaging endpoint must be one of the following:
- the URL of the Cortex XSOAR server, including the configured port
- the Cortex XSOAR rerouting URL that you've defined for your Microsoft Teams instance (see the [Using Cortex XSOAR rerouting](#1-using-cortex-xsoar-rerouting) section for more details)
- - or a proxy that redirects the messages received from Teams to the Cortex XSOAR server (see the [Using NGINX as reverse proxy](#2-using-nginx-as-reverse-proxy) section for more details)
+ - a proxy that redirects the messages received from Teams to the Cortex XSOAR or Cortex XSIAM server (see the [Using NGINX as reverse proxy](#2-using-nginx-as-reverse-proxy) section for more details)
- Microsoft Teams will send events to the messaging endpoints via HTTPS request, which means the messaging endpoint must be accessible for Microsoft Teams to reach to it. As follows, the messaging endpoint can not contain private IP address or any DNS that will block the request from Microsoft Teams.
In order to verify that the messaging endpoint is open as expected, you can surf to the messaging endpoint from a browser in an environment which is disconnected from the Cortex XSOAR environment.
- It's important that the port is opened for outside communication and that the port is not being used, meaning that no service is listening on it. Therefore, the default port, 443, should not be used.
@@ -53,16 +50,16 @@ In order to verify that the messaging endpoint is open as expected, you can surf
## Setup Examples
-### 1. Using Cortex XSOAR rerouting
-In this configuration, we will use Cortex XSOAR functionality, which reroutes HTTPS requests that hit the default port (443) to the web server that the integration spins up.
+### 1. Using Cortex XSOAR or Cortex XSIAM rerouting
+In this configuration, we will use Cortex XSOAR/Cortex XSIAM functionality, which reroutes HTTPS requests that hit the default port (443) to the web server that the integration spins up.
The messaging endpoint needs to be:
For Cortex XSOAR version 6.x: `/instance/execute/`, e.g., `https://my.demisto.live/instance/execute/teams`.
-For Cortex XSOAR version 8: `https://ext-/xsoar/instance/execute/`, e.g., `https://ext-my.demisto.live/xsoar/instance/execute/teams`.
+For Cortex XSOAR version 8 and XSIAM: `https://ext-/xsoar/instance/execute/`, e.g., `https://ext-my.demisto.live/xsoar/instance/execute/teams`.
-The integration instance name, `teams` in this example, needs to be configured in the [Configure Microsoft Teams on Cortex XSOAR](#configure-microsoft-teams-on-cortex-xsoar) step.
+The integration instance name, `teams` in this example, needs to be configured in the [Configure Microsoft Teams on Cortex XSOAR](#configure-microsoft-teams-on-cortex-xsoar) step. Make sure to set the instance name in all lowercase letters and as one word.
The port to be configured in [Configure Microsoft Teams on Cortex XSOAR](#configure-microsoft-teams-on-cortex-xsoar) step should be any available port that is not used by another service.
@@ -73,8 +70,8 @@ In addition, make sure ***Instance execute external*** is enabled (for Cortex XS
### 2. Using NGINX as reverse proxy
-In this configuration, the inbound connection, from Microsoft Teams to Cortex XSOAR, goes through a reverse proxy (e.g. NGINX) which relays the HTTPS requests posted from Microsoft Teams
-to the Cortex XSOAR server on HTTP.
+In this configuration, the inbound connection, from Microsoft Teams to Cortex XSOAR/Cortex XSIAM, goes through a reverse proxy (e.g., NGINX) which relays the HTTPS requests posted from Microsoft Teams
+to the Cortex XSOAR/Cortex XSIAM server on HTTP.
On NGINX, configure the following:
- SSL certificate under `ssl_certificate` and `ssl_certificate_key`
@@ -89,8 +86,8 @@ The port (`7000` in this example), to which the reverse proxy should forward the

### 3. Using Apache reverse proxy and Cortex XSOAR engine
-In this configuration, the inbound connection, from Microsoft Teams to Cortex XSOAR, goes through a reverse proxy (e.g., [Apache](https://httpd.apache.org/docs/2.4/howto/reverse_proxy.html)) and possibly a load balancer, which relays the HTTPS requests posted from Microsoft Teams
-to a Cortex XSOAR engine, which can be put in a DMZ, on HTTP.
+In this configuration, the inbound connection, from Microsoft Teams to Cortex XSOAR/Cortex XSIAM, goes through a reverse proxy (e.g., [Apache](https://httpd.apache.org/docs/2.4/howto/reverse_proxy.html)) and possibly a load balancer, which relays the HTTPS requests posted from Microsoft Teams
+to a Cortex XSOAR/Cortex XSIAM engine, which can be put in a DMZ, on HTTP.
The port (`7000` in this example), to which the reverse proxy should forward the traffic on HTTP, should be the same port you specify in the integration instance configuration, as the web server the integration spins up, listens on that port.
@@ -102,7 +99,7 @@ The port (`7000` in this example), to which the reverse proxy should forward the
### 4. Using Cloudflare
In this configuration, we will use [Cloudflare proxy](https://support.cloudflare.com/hc/en-us/articles/360039824852-Cloudflare-and-the-Cloud-Conceptual-overview-videos).
-The messaging endpoint should be the Cortex XSOAR URL, which need to be hosted on Cloudflare, with the port to which Cloudflare proxy directs the HTTPS traffic, e.g. `https://mysite.com:8443`
+The messaging endpoint should be the Cortex XSOAR/Cortex XSIAM URL, which needs to be hosted on Cloudflare, with the port to which Cloudflare proxy directs the HTTPS traffic, e.g., `https://mysite.com:8443`
In the [Configure Microsoft Teams on Cortex XSOAR](#configure-microsoft-teams-on-cortex-xsoar) step, the following need to be configured:
- The port selected above.
@@ -131,19 +128,17 @@ The information in this video is for Cortex XSOAR 6 only.
## Prerequisites
-Before you can create an instance of the Microsoft Teams integration in Cortex XSOAR, you need to complete the following procedures.
+Before you can create an instance of the Microsoft Teams integration in Cortex XSOAR/Cortex XSIAM, you need to complete the following procedures.
1. [Create the Demisto Bot in Microsoft Teams](#create-the-demisto-bot-in-microsoft-teams)
2. [Grant the Demisto Bot Permissions in Microsoft Graph](#grant-the-demisto-bot-permissions-in-microsoft-graph)
-3. [Configure Microsoft Teams on Cortex XSOAR](#configure-microsoft-teams-on-cortex-xsoar)
+3. [Configure Microsoft Teams on Cortex XSOAR or Cortex XSIAM](#configure-microsoft-teams-on-cortex-xsoar)
4. [Add the Demisto Bot to a Team](#add-the-demisto-bot-to-a-team)
-#### *Note:* Microsoft App Studio is being phased out and will be deprecated on January 1, 2022. It is replaced by Microsoft Developer Portal. Steps 1 and 4 differ if using the App Studio or the Developer Portal.
-
### Create the Demisto Bot in Microsoft Teams
-#### Creating the Demisto Bot for Production environment using Microsoft Azure Portal (Recommended)
+#### Creating the Demisto Bot using Microsoft Azure Portal
1. Navigate to the [Create an Azure Bot page](https://portal.azure.com/#create/Microsoft.AzureBot).
2. In the Bot Handle field, type **Demisto Bot**.
3. Fill in the required Subscription and Resource Group, relevant links: [Subscription](https://learn.microsoft.com/en-us/azure/cost-management-billing/manage/create-subscription), [Resource Groups](https://learn.microsoft.com/en-us/azure/azure-resource-manager/management/manage-resource-groups-portal).
@@ -161,26 +156,17 @@ Before you can create an instance of the Microsoft Teams integration in Cortex X
Note: in step 5, if you choose **Use existing app registration**, make sure to delete the previous created bot with the same app id, remove it from the team it was added to as well.
-#### Creating the Demisto Bot for development environment using the Developer Portal (Recommended to use `Azure portal` method mentioned above, this method will be removed soon)
-1. Navigate to the [Tools in the Microsoft Developer Portal](https://dev.teams.microsoft.com/tools).
-2. Navigate to **Bot management**.
-3. Click the **+New Bot** button.
-4. Fill in `Demisto Bot` in the prompt, click the *Add* button, and wait a few seconds until the bot is created.
-5. Record the **Bot ID** of `Demisto Bot` for the next steps.
-6. Click on the line where `Demisto Bot` shows under the **Bot Name**.
-
-7. Navigate to **Configure** and fill in the **Bot endpoint address**.
-8. Navigate to **Client Secrets** and click the **Add a client secret for your bot** button, and wait a few seconds to allow the secret to be generated.
-9. Store the generated secret securely for the next steps.
+### Grant the Demisto Bot Permissions in Microsoft Graph
-### In order to connect to the Azure Network Security Groups use one of the following methods:
+In order to connect to Microsoft Teams use one of the following authentication methods:
1. *Client Credentials Flow*
2. *Authorization Code Flow*
-### Client Credentials Flow
-#### Grant the Demisto Bot Permissions in Microsoft Graph
+##### Client Credentials Flow
+
+Note: [The chat commands](#chat-commands) are only supported when using the `Authorization Code flow`.
1. Go to your Microsoft Azure portal, and from the left navigation pane select **Azure Active Directory > App registrations**.
2. Search for and click **Demisto Bot**.
@@ -197,30 +183,27 @@ Note: in step 5, if you choose **Use existing app registration**, make sure to d
5. Verify that all permissions were added, and click **Grant admin consent for Demisto**.
6. When prompted to verify granting permissions, click **Yes**, and verify that permissions were successfully added.
-#### Authentication Using the Client Credentials Flow
-
-1. Choose the 'Client Credentials' option in the **Authentication Type** parameter.
-2. Enter your Client/Application ID in the **Bot ID** parameter.
-3. Enter your Client Secret in the **Bot Password** parameter.
-4. Save the instance.
+#### Authorization Code Flow
-### Authorization Code Flow
-#### Grant the Demisto Bot Permissions in Microsoft Graph
+Note: The [microsoft-teams-ring-user](https://learn.microsoft.com/en-us/graph/api/application-post-calls?view=graph-rest-1.0&tabs=http) command is only supported when using the `Client Credentials flow` due to a limitation in Microsoft's permissions system.
1. Go to your Microsoft Azure portal, and from the left navigation pane select **Azure Active Directory > App registrations**.
2. Search for and click **Demisto Bot**.
3. Click **API permissions > Add a permission > Microsoft Graph > Application permissions**.
4. For the following permissions, search for the permission, select the checkbox and click **Add permissions**.
- ##### Required Application Permissions:
+ ###### Required Application Permissions:
- User.Read.All
- Group.ReadWrite.All
- OnlineMeetings.ReadWrite.All
- ChannelMember.ReadWrite.All
- Channel.Create
- Chat.Create
+ - TeamsAppInstallation.ReadWriteSelfForChat.All
+ - TeamsAppInstallation.ReadWriteForChat.All
+ - AppCatalog.Read.All
- ##### Required Delegated Permissions:
+ ###### Required Delegated Permissions:
- OnlineMeetings.ReadWrite
- ChannelMessage.Send
- Chat.ReadWrite
@@ -230,6 +213,8 @@ Note: in step 5, if you choose **Use existing app registration**, make sure to d
- ChannelSettings.ReadWrite.All
- ChatMember.ReadWrite
- Chat.Create
+ - TeamsAppInstallation.ReadWriteForChat
+ - TeamsAppInstallation.ReadWriteSelfForChat
5. Verify that all permissions were added, and click **Grant admin consent for Demisto**.
6. When prompted to verify granting permissions, click **Yes**, and verify that permissions were successfully added.
7. Click **Expose an API** and add **Application ID URI**
@@ -240,20 +225,6 @@ Note: in step 5, if you choose **Use existing app registration**, make sure to d
- ChannelMember.Read.All
9. Click **Authentication > Platform configurations > Add a platform.** Choose **Web** and add Redirect URIs: https://login.microsoftonline.com/common/oauth2/nativeclient
-#### Authentication Using the Authorization Code Flow
-
-1. Choose the 'Authorization Code' option in the **Authentication Type** parameter.
-2. Enter your Client/Application ID in the **Bot ID** parameter.
-3. Enter your Client Secret in the **Bot Password** parameter.
-4. Enter your Application redirect URI in the **Application redirect URI** parameter.
-5. Copy the following URL and replace the **TENANT_ID**, **CLIENT_ID** and **REDIRECT_URI** with your own client ID and redirect URI, accordingly.
-https://login.microsoftonline.com/TENANT_ID/oauth2/v2.0/authorize?response_type=code&response_mode=query&scope=offline_access%20https%3A%2F%2Fgraph.microsoft.com%2F.default&client_id=CLIENT_ID&redirect_uri=REDIRECT_URI&state=12345. When prompted, accept the Microsoft authorization request for the required permissions. You will be automatically redirected to a link with the following structure:
-```REDIRECT_URI?code=AUTH_CODE&state=12345&session_state=SESSION_STATE```
-6. Copy the **AUTH_CODE** (without the “code=” prefix) and paste it in your instance configuration under the **Authorization code** parameter.
-7. Save the instance.
-8. Run the ***!microsoft-teams-auth-test*** command. A 'Success' message should be printed to the War Room.
-
-
### Configure Microsoft Teams on Cortex XSOAR
@@ -278,20 +249,39 @@ https://login.microsoftonline.com/TENANT_ID/oauth2/v2.0/authorize?response_type=
| Disable Automatic Notifications | Whether to disable automatic notifications to the configured notifications channel. | False |
| Allow external users to create incidents via direct message | | False |
| The header of an external form hyperlink. | | False |
- | Trust any certificate (not secure) | Do not check for Cortex XSOAR version 8 | False |
+ | Trust any certificate (not secure) | Do not check for Cortex XSOAR version 8 and Cortex XSIAM. | False |
| Use system proxy settings | | False |
- | Long running instance | | False |
+ | Long running instance | | True |
| Listen port, e.g., 7000 (Required for investigation mirroring and direct messages) | longRunningPort | False |
| Incident type | Incident type. | False |
4. Click **Test** to validate the URLs, token, and connection.
5. Click the **Save & exit** button.
+#### Configuring the instance with the chosen authentication flow
+
+##### Authentication Using the Client Credentials Flow
+
+1. Choose the 'Client Credentials' option in the *Authentication Type* parameter.
+2. Enter your Client/Application ID in the *Bot ID* parameter.
+3. Enter your Client Secret in the *Bot Password* parameter.
+4. Save the instance.
+
+##### Authentication Using the Authorization Code Flow
+
+1. Choose the 'Authorization Code' option in the *Authentication Type* parameter.
+2. Enter your Client/Application ID in the *Bot ID* parameter.
+3. Enter your Client Secret in the *Bot Password* parameter.
+4. Enter your Application redirect URI in the *Application redirect URI* parameter.
+5. Run the ***!microsoft-teams-generate-login-url*** command in the War Room and follow the instructions.
+6. Save the instance.
+7. Run the ***!microsoft-teams-auth-test*** command. A 'Success' message should be printed to the War Room.
+
+
### Add the Demisto Bot to a Team
-- Note: the following need to be done after configuring the integration on Cortex XSOAR (the previous step).
+- Note: The following needs to be done after configuring the integration on Cortex XSOAR/Cortex XSIAM (the previous step).
-#### Using the Developer Portal and Microsoft Azure Portal
1. Download the ZIP file located at the bottom of this article.
2. Uncompress the ZIP file. You should see 3 files (`manifest.json`, `color.png` and `outline.png`).
3. Open the `manifest.json` file that was extracted from the ZIP file.
@@ -324,6 +314,7 @@ https://login.microsoftonline.com/TENANT_ID/oauth2/v2.0/authorize?response_type=
## Commands
You can execute these commands from the Cortex XSOAR CLI, as part of an automation, or in a playbook.
After you successfully execute a command, a DBot message appears in the War Room with the command details.
+
### send-notification
***
Sends a message to the specified teams.
@@ -336,7 +327,7 @@ To mention a user in the message, add a semicolon ";" at the end of the user men
##### Required Permissions
-`Group.Read.All`
+`Group.ReadWrite.All`
##### Input
@@ -363,9 +354,9 @@ Message was sent successfully.
### mirror-investigation
***
-Mirrors the Cortex XSOAR investigation to the specified Microsoft Teams channel. Supports only standard channels.
+Mirrors the Cortex XSOAR/Cortex XSIAM investigation to the specified Microsoft Teams channel. Supports only standard channels.
-**Note**: Mirrored channels could be used to run Cortex XSOAR built-in commands.
+**Note**: Mirrored channels could be used to run Cortex XSOAR/Cortex XSIAM built-in commands.
##### Base Command
@@ -691,6 +682,9 @@ Retrieves a list of members from a channel.
|--------------------------------------|----------------|--------------------------------------|------------------------------------------------------------------------------------------------------|------------|--------------|----------------------|
| 359d2c3c-162b-414c-b2eq-386461e5l050 | test@gmail.com | pbae9ao6-01ql-249o-5me3-4738p3e1m941 | MmFiOWM3OTYtMjkwMi00NWY4LWI3MTItN2M1YTYzY2Y0MWM0IyNlZWY5Y2IzNi0wNmRlLTQ2OWItODdjZC03MGY0Y2JlMzJkMTQ= | owner | itayadmin | 0001-01-01T00:00:00Z |
+
+### Chat Commands
+
### microsoft-teams-chat-create
***
Creates a new chat.
@@ -1078,18 +1072,10 @@ There is no context output for this command.
>2. Copy the `AUTH_CODE` (without the `code=` prefix, and the `session_state` parameter)
>and paste it in your instance configuration under the **Authorization code** parameter.
>
-## Running commands from Microsoft Teams
-You can run Cortex XSOAR commands, according to the user permissions, from Microsoft Teams in a mirrored investigation channel.
-
-Note: Like every message in a mirrored channel, in order for it to be passed to the bot, the bot must be mentioned.
-In order to avoid mentioning the bot, if this was previously configured without adding the Bot ID, repeat the authentication flow and pay particular attention to the following steps:
- * Step 14 in [Using the App Studio](#using-the-app-studio).
- * Step 5 in [Using the Developer Portal](#using-the-developer-portal-1).
-For example, in order to check the reputation of the IP address 8.8.8.8, run the following: `@Demisto Bot !ip ip=8.8.8.8`
-
-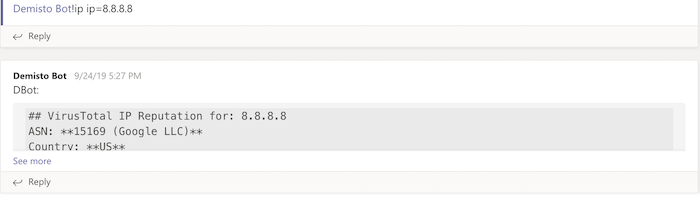
+## Running commands from Microsoft Teams
+You can run Cortex XSOAR/Cortex XSIAM commands, according to the user permissions, from Microsoft Teams in a mirrored investigation channel.
## Direct messages commands
You can chat with the bot in direct messages in order to retrieve data (list incidents and tasks) and run operations (create incident and mirror an investigation) related to Cortex XSOAR.
@@ -1109,7 +1095,8 @@ Note: To enrich an incident created via the Demisto BOT (`new incident` command)
This probably means that there is a connection issue, and the web server does not intercept the HTTPS queries from Microsoft Teams.
To troubleshoot:
- 1. first verify the Docker container is up and running and publish the configured port to the outside world:
+ 1. Verify that the messaging endpoint is configured correctly according to the method you chose in the [Setup Examples](#setup-examples) step.
+ 2. Verify the Docker container is up and running and publish the configured port to the outside world:
From the Cortex XSOAR / Cortex XSOAR engine machine run: `docker ps | grep teams`
@@ -1123,15 +1110,15 @@ Note: To enrich an incident created via the Demisto BOT (`new incident` command)
- From the Cortex XSOAR machine to localhost.
- Note: The web server supports only POST method queries.
- 2. If the cURL queries were sent successfully, you should see the following line in Cortex XSOAR logs: `Finished processing Microsoft Teams activity successfully`.
+ 3. If the cURL queries were sent successfully, you should see the following line in Cortex XSOAR logs: `Finished processing Microsoft Teams activity successfully`.
- 3. If you're working with secured communication (HTTPS), make sure that you provided a valid certificate.
+ 4. If you're working with secured communication (HTTPS), make sure that you provided a valid certificate. (Not for Cortex XSOAR/Cortex XSIAM Rerouting ).
1. Run `openssl s_client -connect :443` .
2. Verify that the returned value of the `Verify return code` field is `0 (ok)`, otherwise, it's not a valid certificate.
- 4. Try inserting your configured message endpoint in a browser and click **Enter**. If `Method Not Allowed` is returned, the endpoint is valid and ready to communicate, otherwise, it needs to be handled according to the returned error's message.
+ 5. Try inserting your configured message endpoint in a browser and click **Enter**. If `Method Not Allowed` is returned, the endpoint is valid and ready to communicate, otherwise, it needs to be handled according to the returned error's message. (Not for Cortex XSOAR 8 OR Cortex XSIAM).
- 5. In some cases, a connection is not created between Teams and the messaging endpoint when adding a bot to the team. You can work around this problem by adding any member to the team the bot was added to (the bot should be already added to the team). This will trigger a connection and solve the issue. You can then remove the member that was added.
+ 6. In some cases, a connection is not created between Teams and the messaging endpoint when adding a bot to the team. You can work around this problem by adding any member to the team the bot was added to (the bot should be already added to the team). This will trigger a connection and solve the issue. You can then remove the member that was added.
2. If you see the following error message: `Error in API call to Microsoft Teams: [403] - UnknownError`, then it means the AAD application has insufficient permissions.
diff --git a/Packs/MicrosoftTeams/ReleaseNotes/1_4_52.md b/Packs/MicrosoftTeams/ReleaseNotes/1_4_52.md
new file mode 100644
index 000000000000..11864a7638b2
--- /dev/null
+++ b/Packs/MicrosoftTeams/ReleaseNotes/1_4_52.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Microsoft Teams
+
+- Documentation and metadata improvements.
\ No newline at end of file
diff --git a/Packs/MicrosoftTeams/pack_metadata.json b/Packs/MicrosoftTeams/pack_metadata.json
index 440c13ba4b05..287d1fc63d90 100644
--- a/Packs/MicrosoftTeams/pack_metadata.json
+++ b/Packs/MicrosoftTeams/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Microsoft Teams",
"description": "Send messages and notifications to your team members.",
"support": "xsoar",
- "currentVersion": "1.4.51",
+ "currentVersion": "1.4.52",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From a8c7174504c30306ecb8dcbaf7ed995d02bc6bb3 Mon Sep 17 00:00:00 2001
From: MLainer1 <93524335+MLainer1@users.noreply.github.com>
Date: Wed, 21 Feb 2024 17:10:52 +0200
Subject: [PATCH 062/272] [bug] - threatconnect feed missing indicator type
parser (#32993)
* [bug] - threatconnect feed missing indicator type parser
* test
* rn
* debug logs
* DI
* revert
* precommit
---
.../FeedThreatConnect/FeedThreatConnect.py | 22 +++++++++++--------
.../FeedThreatConnect/FeedThreatConnect.yml | 3 +--
.../FeedThreatConnect_test.py | 5 +++--
.../ReleaseNotes/2_1_20.json | 4 ++++
.../FeedThreatConnect/ReleaseNotes/2_1_20.md | 6 +++++
Packs/FeedThreatConnect/pack_metadata.json | 2 +-
6 files changed, 28 insertions(+), 14 deletions(-)
create mode 100644 Packs/FeedThreatConnect/ReleaseNotes/2_1_20.json
create mode 100644 Packs/FeedThreatConnect/ReleaseNotes/2_1_20.md
diff --git a/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect.py b/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect.py
index b46db363e844..04d69cfe444e 100644
--- a/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect.py
+++ b/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect.py
@@ -7,7 +7,6 @@
from contextlib import contextmanager
from enum import Enum
from math import ceil
-from typing import Tuple
# Local packages
from CommonServerPython import * # noqa: E402 lgtm [py/polluting-import]
@@ -29,7 +28,7 @@
INTEGRATION_NAME = 'ThreatConnect Feed'
INTEGRATION_COMMAND_NAME = 'tc'
INTEGRATION_CONTEXT_NAME = 'ThreatConnect'
-COMMAND_OUTPUT = Tuple[str, Union[Dict[str, Any], List[Any]], Union[Dict[str, Any], List[Any]]]
+COMMAND_OUTPUT = tuple[str, Union[Dict[str, Any], List[Any]], Union[Dict[str, Any], List[Any]]]
INDICATOR_MAPPING_NAMES = {
'Address': FeedIndicatorType.IP,
'CIDR': FeedIndicatorType.CIDR,
@@ -149,7 +148,6 @@
'URL',
'ASN',
'CIDR',
- 'Email Subject',
'Hashtag',
'Mutex',
'Registry Key',
@@ -203,7 +201,7 @@ def create_types_query(params: dict, endpoint: str) -> str:
raise DemistoException('No indicator type or group type were chosen, please choose at least one.')
if endpoint == 'indicators':
if 'All' in indicator_types:
- return ''
+ types.extend(INDICATOR_TYPES)
else:
types.extend(indicator_types)
else:
@@ -236,7 +234,7 @@ def calculate_dbot_score(threat_assess_score: Optional[Union[int, str]] = None)
def parse_indicator(indicator: Dict[str, str]) -> Dict[str, Any]:
- """ Parsing indicator by indicators demisto convension.
+ """ Parsing indicator by indicators demisto convention.
Args:
indicator: Indicator as raw response.
Returns:
@@ -261,7 +259,8 @@ def parse_indicator(indicator: Dict[str, str]) -> Dict[str, Any]:
def create_indicator_fields(indicator, indicator_type):
"""Creating an indicator fields from a raw indicator"""
params = demisto.params()
- indicator_fields_mapping = TC_INDICATOR_TO_XSOAR_INDICATOR[indicator_type]
+ indicator_fields_mapping = TC_INDICATOR_TO_XSOAR_INDICATOR.get(indicator_type, {})
+
fields: dict = {}
for indicator_key, xsoar_indicator_key in indicator_fields_mapping.items():
@@ -415,7 +414,7 @@ def module_test_command(client: Client, args): # pragma: no cover # noqa
return_error(str(e))
-def fetch_indicators_command(client: Client, params: dict, last_run: dict) -> Tuple[
+def fetch_indicators_command(client: Client, params: dict, last_run: dict) -> tuple[
List[Dict[str, Any]], List[Dict[str, Any]]]: # noqa # pragma: no cover
""" Fetch indicators from ThreatConnect
@@ -581,8 +580,12 @@ def get_indicators_command(client: Client, args: dict) -> dict: # type: ignore
types = argToList(args.get("indicator_type"))
query = ''
- if types and 'All' not in types:
- query = 'AND typeName IN ("' + '","'.join(types) + '")'
+
+ if types:
+ if 'All' in types:
+ query = 'AND typeName IN ("' + '","'.join(INDICATOR_TYPES) + '")'
+ else:
+ query = 'AND typeName IN ("' + '","'.join(types) + '")'
tql = active_only + confidence + threat_score + confidence + owners + query
tql = tql.replace('AND ', '', 1)
@@ -604,6 +607,7 @@ def get_indicators_command(client: Client, args: dict) -> dict: # type: ignore
t=t, removeNull=True) # type: ignore # noqa
return readable_output, {}, list(response) # type: ignore
+ return {}
def get_owners_command(client: Client, args: dict) -> COMMAND_OUTPUT: # pragma: no cover
diff --git a/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect.yml b/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect.yml
index ce02ce8269df..dafc994daa67 100644
--- a/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect.yml
+++ b/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect.yml
@@ -99,7 +99,6 @@ configuration:
- URL
- ASN
- CIDR
- - EmailSubject
- Hashtag
- Mutex
- Registry Key
@@ -237,7 +236,7 @@ script:
name: tc-get-indicators
- description: Gets available indicators owners.
name: tc-get-owners
- dockerimage: demisto/python3:3.10.13.84405
+ dockerimage: demisto/python3:3.10.13.87159
feed: true
runonce: false
script: '-'
diff --git a/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect_test.py b/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect_test.py
index 914308b7f8cf..1eb470608971 100644
--- a/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect_test.py
+++ b/Packs/FeedThreatConnect/Integrations/FeedThreatConnect/FeedThreatConnect_test.py
@@ -6,7 +6,7 @@
def load_json_file(path):
- with open(path, 'r') as _json_file:
+ with open(path) as _json_file:
return json.load(_json_file)
@@ -38,7 +38,8 @@ def test_create_or_query():
@pytest.mark.parametrize("params, expected_result, endpoint",
[({'indicator_active': False, "indicator_type": ['All'],
- 'createRelationships': False, "confidence": 0, "threat_assess_score": 0}, '', 'indicators'),
+ 'createRelationships': False, "confidence": 0, "threat_assess_score": 0},
+ 'typeName IN ("EmailAddress","File","Host","URL","ASN","CIDR","Hashtag","Mutex","Registry Key","User Agent","Address")', 'indicators'), # noqa: E501
({'indicator_active': True, "group_type": ['File'],
'createRelationships': False, "confidence": 0, "threat_assess_score": 0},
'typeName IN ("File")', 'groups'),
diff --git a/Packs/FeedThreatConnect/ReleaseNotes/2_1_20.json b/Packs/FeedThreatConnect/ReleaseNotes/2_1_20.json
new file mode 100644
index 000000000000..b8dc5d29b59c
--- /dev/null
+++ b/Packs/FeedThreatConnect/ReleaseNotes/2_1_20.json
@@ -0,0 +1,4 @@
+{
+ "breakingChanges": true,
+ "breakingChangesNotes": "The *EmailSubject* option was removed from the *Indicator Types* feed parameter."
+}
\ No newline at end of file
diff --git a/Packs/FeedThreatConnect/ReleaseNotes/2_1_20.md b/Packs/FeedThreatConnect/ReleaseNotes/2_1_20.md
new file mode 100644
index 000000000000..a668e536d124
--- /dev/null
+++ b/Packs/FeedThreatConnect/ReleaseNotes/2_1_20.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### ThreatConnect Feed
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
+- Fixed an issue where selecting indicators of type *EmailSubject* to pull caused an error. This type is no longer supported.
diff --git a/Packs/FeedThreatConnect/pack_metadata.json b/Packs/FeedThreatConnect/pack_metadata.json
index e82f6458e06c..b40d22f0d378 100644
--- a/Packs/FeedThreatConnect/pack_metadata.json
+++ b/Packs/FeedThreatConnect/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "ThreatConnect Feed",
"description": "ThreatConnect indicators feed for Cortex XSOAR TIM.",
"support": "xsoar",
- "currentVersion": "2.1.19",
+ "currentVersion": "2.1.20",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 1e9a4001c84e64d260392d41c8dcf9537bea86db Mon Sep 17 00:00:00 2001
From: Dean Arbel
Date: Wed, 21 Feb 2024 17:18:48 +0200
Subject: [PATCH 063/272] [Sleep] Removed Polling in 6 (#33056)
---
Packs/CommonScripts/ReleaseNotes/1_14_1.md | 6 ++++
Packs/CommonScripts/Scripts/Sleep/Sleep.js | 36 ++++++++++++----------
Packs/CommonScripts/pack_metadata.json | 2 +-
3 files changed, 26 insertions(+), 18 deletions(-)
create mode 100644 Packs/CommonScripts/ReleaseNotes/1_14_1.md
diff --git a/Packs/CommonScripts/ReleaseNotes/1_14_1.md b/Packs/CommonScripts/ReleaseNotes/1_14_1.md
new file mode 100644
index 000000000000..0264bf8275dd
--- /dev/null
+++ b/Packs/CommonScripts/ReleaseNotes/1_14_1.md
@@ -0,0 +1,6 @@
+
+#### Scripts
+
+##### Sleep
+
+Fixed an issue where sometimes tasks using Sleep did not continue as expected.
diff --git a/Packs/CommonScripts/Scripts/Sleep/Sleep.js b/Packs/CommonScripts/Scripts/Sleep/Sleep.js
index fdb524ccc18a..214141fa5c05 100644
--- a/Packs/CommonScripts/Scripts/Sleep/Sleep.js
+++ b/Packs/CommonScripts/Scripts/Sleep/Sleep.js
@@ -1,22 +1,24 @@
-pollingThreshold = 300;
-
-if (isDemistoVersionGE('8.4.0', 649563)) {
- configThreshold = executeCommand('getServerConfig', {key: 'content.automation.sleep.threshold.seconds'});
- if (configThreshold[0] && !isError(configThreshold[0])) {
- pollingThreshold = parseInt(configThreshold[0].Contents);
+if (isDemistoVersionGE('8.0.0')) {
+ pollingThreshold = 300;
+ if (isDemistoVersionGE('8.4.0', 649563)) {
+ configThreshold = executeCommand('getServerConfig', {key: 'content.automation.sleep.threshold.seconds'});
+ if (configThreshold[0] && !isError(configThreshold[0])) {
+ pollingThreshold = parseInt(configThreshold[0].Contents);
+ }
}
-}
-
-if (parseInt(args.seconds) >= pollingThreshold) {
- // Polling implementation
- return {
- Type: entryTypes.note,
- Contents: 'Sleep will complete in ' + args.seconds + ' seconds',
- PollingCommand: 'Print',
- NextRun: args.seconds + '',
- PollingArgs: {value: 'Sleep completed in ' + args.seconds + ' seconds'},
- Timeout: String(parseInt(args.seconds) + 60)
+
+ if (parseInt(args.seconds) >= pollingThreshold) {
+ // Polling implementation
+ return {
+ Type: entryTypes.note,
+ Contents: 'Sleep will complete in ' + args.seconds + ' seconds',
+ PollingCommand: 'Print',
+ NextRun: args.seconds + '',
+ PollingArgs: {value: 'Sleep completed in ' + args.seconds + ' seconds'},
+ Timeout: String(parseInt(args.seconds) + 60)
+ }
}
+
}
// Sleep for the given number of seconds
diff --git a/Packs/CommonScripts/pack_metadata.json b/Packs/CommonScripts/pack_metadata.json
index 293d37cc7cee..1ec25f809949 100644
--- a/Packs/CommonScripts/pack_metadata.json
+++ b/Packs/CommonScripts/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Common Scripts",
"description": "Frequently used scripts pack.",
"support": "xsoar",
- "currentVersion": "1.14.0",
+ "currentVersion": "1.14.1",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 65ee944b854165e5f10f05cafa723d2c32c1befa Mon Sep 17 00:00:00 2001
From: Darya Koval <72339940+daryakoval@users.noreply.github.com>
Date: Wed, 21 Feb 2024 20:04:11 +0200
Subject: [PATCH 064/272] ad-modify-user-ou adds backslash to CN (#31491)
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
* Update shift management scripts (#31130)
* fixed the bug and added unit tests
* updated docker image
* RN
* updated docker image
* cr updates
* EWS rule commands - MS graph python integrations (#30943)
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* MS IIS Update (#31132)
* Updated ModelingRules
* Updated ReleaseNotes
* Updated ReleaseNotes
* Anomali ThreatStream change DBot verdict from Benign to Unknown for Low Confidence Indicators (#30993) (#31151)
* change DBot verdict from Benign to Unknown for Low Confidence Indicators
Indicators found in Anomali that are below Confidence thresholds should be created as Unknown and not Benign.
Anomali ThreatStream documentation regarding Confidence
https://ui.threatstream.com/optic-doc/Content/Features/threat_model/Observables/details_indicator.htm
Confidence - Confidence indicates the certainty that an observable exhibits or is connected to malicious behavior.
If Anomali has indicators with low Confidence, that doesn't mean the indicator is Benign/Safe. It means Anomali is unsure that the indicator is Malicious and as such the more appropriate verdict in XSOAR should be Unknown.
* add indicator_default_score param
* changed values to Benign and Unknown
* update README and RN
* update RN
* update docker
set required to false
* update docker
* fix docs comments
---------
Co-authored-by: zdrouse
Co-authored-by: adi88d
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* generate empty junit files (#31153)
* Update 1_6_0.json (#31164)
* fix splunkpy splunk_submit_event_hec_command string issue (#30978)
* fix splunkpy splunk_submit_event_hec_command string issue
* test
* add fix
* update rn
* [xsoar saas] - fix ports taxii2 e2e (#31163)
* Hello world saas (#30901)
* added a new incident field only for saas mp
* added an incident field to xsoar_saas only for demonstration
* format incident field
* format incident field
* added saas word to known words
* version
* merge with master
* fixed the xsoar_saas end tag
* Added tests to validate result
* modified RN
* pre commit changes
* RN tags
* ignoe long line
* MS IIS README (#31158)
* Updated README
* Updated README
* Fixes For IP Enrichment Playbooks (#31114)
* Fixes For IP Enrichment Playbooks
* RN
* Removed the mapping rule from both playbooks. Updated the default value of the internal range playbook input according to RFC 1918.
* Removed the value of 'UseReputationCommand' playbook input and fixes the YML files
* Fixed RN
* Removed the value set for the 'UseReputationCommand' sub-playbook input.
Re-added the default value for 'UseReputationCommand' playbook input
* skip ThreatStream-Test (#31172)
* [transformers] Enhance to be more durable (#30897)
[transformers] Enhance to be more durable
* Fixes For 'Email Address Enrichment - Generic v2.1' (#31122)
* Fixes For 'Email Address Enrichment - Generic v2.1'
* Re-added the test playbook and marketplace configs to the playbook YML file
* changed the 'domain' playbook input value
* removed the 'domain' playbook input value and added RN
* Fixed RN
* Bump pack from version CommonPlaybooks to 2.4.34.
---------
Co-authored-by: Content Bot
* DisplayMappedFields - Fix dark mode text color (#31085)
* removed the hardcoded color
* removed the hardcoded color
* update RN
* update docker image
* Bump pack from version CommonScripts to 1.12.48.
* Unittest fixes
* Bump pack from version CommonScripts to 1.12.49.
* Unittest fixes
* Bump pack from version CommonScripts to 1.12.50.
* Bump pack from version CommonScripts to 1.12.51.
* Bump pack from version CommonScripts to 1.12.52.
* Bump pack from version CommonScripts to 1.12.53.
---------
Co-authored-by: Content Bot
* Updated the layout to exclude integration incident fields that are not pertinent to Vectra XDR (#31127) (#31182)
Co-authored-by: Crest Data Systems <60967033+crestdatasystems@users.noreply.github.com>
Co-authored-by: crestdatasystems
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
* Taxii2 server relationship bug (#31162)
* [taxii2-server] - code fixes
* bump rn
* docker update
* remove debug-log because may wanted
* [ASM] EXPANDER-7096 - ASM Remediation Guidance Fields (#30955) (#31178)
Co-authored-by: John <40349459+BigEasyJ@users.noreply.github.com>
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* Created pack for F5 BIG-IP APM (#31017)
* Created pack for f5 apm
* Added modeling rule files.
* adding modeling rules and schema.
* modified modeling rules
* update yml file for modeling rule.
* Update Packs/F5APM/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/F5APM/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/F5APM/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/F5APM/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/F5APM/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/F5APM/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* update readme.
* Modified the read me file.
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* HelloWorld - delete old classifier (#31185)
* Add support for is array for rep commands (#31169)
* added support for isArray for python Xsoar supported reputation commands
* added rn
* Empty-Commit
* python files fixes
* fix docker issue
* cr fixes
* added logs and cache fix (#30577)
* added logs and cache fix
* Fixed another executeCommand results handling.
* Updated docker image
* Added rn
* Update Packs/Phishing/ReleaseNotes/3_6_2.md
Co-authored-by: Dan Tavori <38749041+dantavori@users.noreply.github.com>
* Update Packs/Phishing/Scripts/FindDuplicateEmailIncidents/FindDuplicateEmailIncidents.py
---------
Co-authored-by: Dan Tavori <38749041+dantavori@users.noreply.github.com>
* Add support for is array for rep commands js (#31184)
* JS files fixes
* added rn
* pre commit fixes
* pre commit fixes
* cr fixes
* xsiam-avaya-siem-content-ciac-8502 (#31128)
* init-pack
* modeling-rules
* add-docs
* fix-pid-parsing
* fix-README.md
* Fixed For Endpoint Enrichment Playbooks (#31147)
* Fixed For 'Endpoint Enrichment - Generic v2.1' Playbook
* RN
* RN
* Fixes for Endpoint_Enrichment_-_Generic_v2.1_6_8 playbook
* Bump pack from version CommonPlaybooks to 2.4.34.
* Bump pack from version CommonPlaybooks to 2.4.35.
* Fixed version for 'Endpoint Enrichment - Generic v2.1.6.8' playbook
* Fixes for 'Endpoint Enrichment - Generic v2.1' playbook
* Revert changes in 'Endpoint Enrichment - Generic v2.1' playbook
---------
Co-authored-by: Content Bot
* Update Docker Image To demisto/python3 (#31198)
* Updated Metadata Of Pack DeveloperTools
* Added release notes to pack DeveloperTools
* Packs/DeveloperTools/Integrations/CreateIncidents/CreateIncidents.yml Docker image update
* Updated Metadata Of Pack FlashpointFeed
* Added release notes to pack FlashpointFeed
* Packs/FlashpointFeed/Integrations/FlashpointFeed/FlashpointFeed.yml Docker image update
* Updated Metadata Of Pack AbnormalSecurity
* Added release notes to pack AbnormalSecurity
* Packs/AbnormalSecurity/Integrations/AbnormalSecurity/AbnormalSecurity.yml Docker image update
* Updated Metadata Of Pack FeedLOLBAS
* Added release notes to pack FeedLOLBAS
* Packs/FeedLOLBAS/Integrations/FeedLOLBAS/FeedLOLBAS.yml Docker image update
* Updated Metadata Of Pack Hackuity
* Added release notes to pack Hackuity
* Packs/Hackuity/Integrations/Hackuity/Hackuity.yml Docker image update
* Updated Metadata Of Pack Grafana
* Added release notes to pack Grafana
* Packs/Grafana/Integrations/Grafana/Grafana.yml Docker image update
* Updated Metadata Of Pack Binalyze
* Added release notes to pack Binalyze
* Packs/Binalyze/Integrations/BinalyzeAIR/BinalyzeAIR.yml Docker image update
* Updated Metadata Of Pack ServiceDeskPlus
* Added release notes to pack ServiceDeskPlus
* Packs/ServiceDeskPlus/Integrations/ServiceDeskPlus/ServiceDeskPlus.yml Docker image update
* Updated Metadata Of Pack Oracle_IAM
* Added release notes to pack Oracle_IAM
* Packs/Oracle_IAM/Integrations/OracleIAM/OracleIAM.yml Docker image update
* Updated Metadata Of Pack AccentureCTI
* Added release notes to pack AccentureCTI
* Packs/AccentureCTI/Integrations/ACTIIndicatorQuery/ACTIIndicatorQuery.yml Docker image update
* Update Docker Image To demisto/boto3py3 (#31199)
* Updated Metadata Of Pack SecurityIntelligenceServicesFeed
* Added release notes to pack SecurityIntelligenceServicesFeed
* Packs/SecurityIntelligenceServicesFeed/Integrations/SecurityIntelligenceServicesFeed/SecurityIntelligenceServicesFeed.yml Docker image update
* Updated Metadata Of Pack AWS-IAM
* Added release notes to pack AWS-IAM
* Packs/AWS-IAM/Integrations/AWS-IAM/AWS-IAM.yml Docker image update
* Updated Metadata Of Pack AWS-Route53
* Added release notes to pack AWS-Route53
* Packs/AWS-Route53/Integrations/AWSRoute53/AWSRoute53.yml Docker image update
* Updated Metadata Of Pack AWS-AccessAnalyzer
* Added release notes to pack AWS-AccessAnalyzer
* Packs/AWS-AccessAnalyzer/Integrations/AWS-AccessAnalyzer/AWS-AccessAnalyzer.yml Docker image update
* Updated Metadata Of Pack AWS-GuardDuty
* Added release notes to pack AWS-GuardDuty
* Packs/AWS-GuardDuty/Integrations/AWSGuardDutyEventCollector/AWSGuardDutyEventCollector.yml Docker image update
* Packs/AWS-GuardDuty/Integrations/AWSGuardDuty/AWSGuardDuty.yml Docker image update
* Updated Metadata Of Pack AWS-SecurityHub
* Added release notes to pack AWS-SecurityHub
* Packs/AWS-SecurityHub/Integrations/AWSSecurityHubEventCollector/AWSSecurityHubEventCollector.yml Docker image update
* Updated Metadata Of Pack Aws-SecretsManager
* Added release notes to pack Aws-SecretsManager
* Packs/Aws-SecretsManager/Integrations/AwsSecretsManager/AwsSecretsManager.yml Docker image update
* Update Docker Image To demisto/armorblox (#31203)
* Updated Metadata Of Pack Armorblox
* Added release notes to pack Armorblox
* Packs/Armorblox/Integrations/Armorblox/Armorblox.yml Docker image update
* Update Docker Image To demisto/py3-tools (#31201)
* Updated Metadata Of Pack Intezer
* Added release notes to pack Intezer
* Packs/Intezer/Integrations/IntezerV2/IntezerV2.yml Docker image update
* Updated Metadata Of Pack Zabbix
* Added release notes to pack Zabbix
* Packs/Zabbix/Integrations/Zabbix/Zabbix.yml Docker image update
* Updated Metadata Of Pack FeedMalwareBazaar
* Added release notes to pack FeedMalwareBazaar
* Packs/FeedMalwareBazaar/Integrations/MalwareBazaarFeed/MalwareBazaarFeed.yml Docker image update
* Updated Metadata Of Pack FeedGCPWhitelist
* Added release notes to pack FeedGCPWhitelist
* Packs/FeedGCPWhitelist/Integrations/FeedGoogleIPRanges/FeedGoogleIPRanges.yml Docker image update
* Updated Metadata Of Pack AccentureCTI_Feed
* Added release notes to pack AccentureCTI_Feed
* Packs/AccentureCTI_Feed/Integrations/ACTIIndicatorFeed/ACTIIndicatorFeed.yml Docker image update
* Updated Metadata Of Pack SEKOIAIntelligenceCenter
* Added release notes to pack SEKOIAIntelligenceCenter
* Packs/SEKOIAIntelligenceCenter/Integrations/SEKOIAIntelligenceCenter/SEKOIAIntelligenceCenter.yml Docker image update
* Updated Metadata Of Pack JARM
* Added release notes to pack JARM
* Packs/JARM/Integrations/JARM/JARM.yml Docker image update
* Updated Metadata Of Pack CommonWidgets
* Added release notes to pack CommonWidgets
* Packs/CommonWidgets/Scripts/RSSWidget/RSSWidget.yml Docker image update
* Updated Metadata Of Pack FiltersAndTransformers
* Added release notes to pack FiltersAndTransformers
* Packs/FiltersAndTransformers/Scripts/Jmespath/Jmespath.yml Docker image update
* Update Docker Image To demisto/oci (#31202)
* Updated Metadata Of Pack OracleCloudInfrastructure
* Added release notes to pack OracleCloudInfrastructure
* Packs/OracleCloudInfrastructure/Integrations/OracleCloudInfrastructureEventCollector/OracleCloudInfrastructureEventCollector.yml Docker image update
* Update Docker Image To demisto/accessdata (#31200)
* Updated Metadata Of Pack Exterro
* Added release notes to pack Exterro
* Packs/Exterro/Integrations/Exterro/Exterro.yml Docker image update
* Fix DS108
---------
Co-authored-by: israelpolishook
* Update Docker Image To demisto/carbon-black-cloud (#31206)
* Updated Metadata Of Pack CarbonBlackDefense
* Added release notes to pack CarbonBlackDefense
* Packs/CarbonBlackDefense/Integrations/CarbonBlackLiveResponseCloud/CarbonBlackLiveResponseCloud.yml Docker image update
* Update Docker Image To demisto/taxii2 (#31205)
* Updated Metadata Of Pack FeedUnit42v2
* Added release notes to pack FeedUnit42v2
* Packs/FeedUnit42v2/Integrations/FeedUnit42v2/FeedUnit42v2.yml Docker image update
* Update Docker Image To demisto/crypto (#31204)
* Updated Metadata Of Pack AzureKeyVault
* Added release notes to pack AzureKeyVault
* Packs/AzureKeyVault/Integrations/AzureKeyVault/AzureKeyVault.yml Docker image update
* Updated Metadata Of Pack AzureSentinel
* Added release notes to pack AzureSentinel
* Packs/AzureSentinel/Integrations/AzureSentinel/AzureSentinel.yml Docker image update
* Updated Metadata Of Pack AzureDevOps
* Added release notes to pack AzureDevOps
* Packs/AzureDevOps/Integrations/AzureDevOps/AzureDevOps.yml Docker image update
* Updated Metadata Of Pack MicrosoftCloudAppSecurity
* Added release notes to pack MicrosoftCloudAppSecurity
* Packs/MicrosoftCloudAppSecurity/Integrations/MicrosoftCloudAppSecurity/MicrosoftCloudAppSecurity.yml Docker image update
* Updated Metadata Of Pack AzureRiskyUsers
* Added release notes to pack AzureRiskyUsers
* Packs/AzureRiskyUsers/Integrations/AzureRiskyUsers/AzureRiskyUsers.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphGroups
* Added release notes to pack MicrosoftGraphGroups
* Packs/MicrosoftGraphGroups/Integrations/MicrosoftGraphGroups/MicrosoftGraphGroups.yml Docker image update
* Updated Metadata Of Pack AzureSQLManagement
* Added release notes to pack AzureSQLManagement
* Packs/AzureSQLManagement/Integrations/AzureSQLManagement/AzureSQLManagement.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphAPI
* Added release notes to pack MicrosoftGraphAPI
* Packs/MicrosoftGraphAPI/Integrations/MicrosoftGraphAPI/MicrosoftGraphAPI.yml Docker image update
* Updated Metadata Of Pack MicrosoftTeams
* Added release notes to pack MicrosoftTeams
* Packs/MicrosoftTeams/Integrations/MicrosoftTeamsManagement/MicrosoftTeamsManagement.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphApplications
* Added release notes to pack MicrosoftGraphApplications
* Packs/MicrosoftGraphApplications/Integrations/MicrosoftGraphApplications/MicrosoftGraphApplications.yml Docker image update
* Update Docker Image To demisto/opnsense (#31208)
* Updated Metadata Of Pack OPNSense
* Added release notes to pack OPNSense
* Packs/OPNSense/Integrations/OPNSense/OPNSense.yml Docker image update
* Update Docker Image To demisto/auth-utils (#31207)
* Updated Metadata Of Pack Cylance_Protect
* Added release notes to pack Cylance_Protect
* Packs/Cylance_Protect/Integrations/Cylance_Protect_v2/Cylance_Protect_v2.yml Docker image update
* Updated Metadata Of Pack Zoom
* Added release notes to pack Zoom
* Packs/Zoom/Integrations/ZoomEventCollector/ZoomEventCollector.yml Docker image update
* Updated Metadata Of Pack Silverfort
* Added release notes to pack Silverfort
* Packs/Silverfort/Integrations/Silverfort/Silverfort.yml Docker image update
* Updated Metadata Of Pack AzureDataExplorer
* Added release notes to pack AzureDataExplorer
* Packs/AzureDataExplorer/Integrations/AzureDataExplorer/AzureDataExplorer.yml Docker image update
* Updated Metadata Of Pack MicrosoftManagementActivity
* Added release notes to pack MicrosoftManagementActivity
* Packs/MicrosoftManagementActivity/Integrations/MicrosoftManagementActivity/MicrosoftManagementActivity.yml Docker image update
* Updated Metadata Of Pack Box
* Added release notes to pack Box
* Packs/Box/Integrations/BoxEventsCollector/BoxEventsCollector.yml Docker image update
* Packs/Box/Integrations/BoxV2/BoxV2.yml Docker image update
* Updated Metadata Of Pack Troubleshoot
* Added release notes to pack Troubleshoot
* Packs/Troubleshoot/Scripts/CertificatesTroubleshoot/CertificatesTroubleshoot.yml Docker image update
* commit
---------
Co-authored-by: israelpolishook
* Update Docker Image To demisto/ippysocks-py3 (#31211)
* Updated Metadata Of Pack Whois
* Added release notes to pack Whois
* Packs/Whois/Integrations/Whois/Whois.yml Docker image update
* Update Docker Image To demisto/python3 (#31214)
* Updated Metadata Of Pack QualysFIM
* Added release notes to pack QualysFIM
* Packs/QualysFIM/Integrations/QualysFIM/QualysFIM.yml Docker image update
* Updated Metadata Of Pack FortiSIEM
* Added release notes to pack FortiSIEM
* Packs/FortiSIEM/Integrations/FortiSIEMV2/FortiSIEMV2.yml Docker image update
* Updated Metadata Of Pack FreshworksFreshservice
* Added release notes to pack FreshworksFreshservice
* Packs/FreshworksFreshservice/Integrations/FreshworksFreshservice/FreshworksFreshservice.yml Docker image update
* Updated Metadata Of Pack KnowBe4_KMSAT
* Added release notes to pack KnowBe4_KMSAT
* Packs/KnowBe4_KMSAT/Integrations/KnowBe4KMSATEventCollector/KnowBe4KMSATEventCollector.yml Docker image update
* Packs/KnowBe4_KMSAT/Integrations/KnowBe4KMSAT/KnowBe4KMSAT.yml Docker image update
* Updated Metadata Of Pack SafeNet_Trusted_Access
* Added release notes to pack SafeNet_Trusted_Access
* Packs/SafeNet_Trusted_Access/Integrations/SafeNetTrustedAccessEventCollector/SafeNetTrustedAccessEventCollector.yml Docker image update
* Updated Metadata Of Pack DelineaSS
* Added release notes to pack DelineaSS
* Packs/DelineaSS/Integrations/DelineaSS/DelineaSS.yml Docker image update
* Updated Metadata Of Pack Cryptocurrency
* Added release notes to pack Cryptocurrency
* Packs/Cryptocurrency/Integrations/Cryptocurrency/Cryptocurrency.yml Docker image update
* Updated Metadata Of Pack PANOSPolicyOptimizer
* Added release notes to pack PANOSPolicyOptimizer
* Packs/PANOSPolicyOptimizer/Integrations/PANOSPolicyOptimizer/PANOSPolicyOptimizer.yml Docker image update
* Updated Metadata Of Pack DeveloperTools
* Added release notes to pack DeveloperTools
* Packs/DeveloperTools/Integrations/CreateIncidents/CreateIncidents.yml Docker image update
* Update Docker Image To demisto/boto3py3 (#31215)
* Updated Metadata Of Pack SecurityIntelligenceServicesFeed
* Added release notes to pack SecurityIntelligenceServicesFeed
* Packs/SecurityIntelligenceServicesFeed/Integrations/SecurityIntelligenceServicesFeed/SecurityIntelligenceServicesFeed.yml Docker image update
* Updated Metadata Of Pack AWS-IAM
* Added release notes to pack AWS-IAM
* Packs/AWS-IAM/Integrations/AWS-IAM/AWS-IAM.yml Docker image update
* Updated Metadata Of Pack AWS-Route53
* Added release notes to pack AWS-Route53
* Packs/AWS-Route53/Integrations/AWSRoute53/AWSRoute53.yml Docker image update
* Updated Metadata Of Pack AWS-AccessAnalyzer
* Added release notes to pack AWS-AccessAnalyzer
* Packs/AWS-AccessAnalyzer/Integrations/AWS-AccessAnalyzer/AWS-AccessAnalyzer.yml Docker image update
* Updated Metadata Of Pack AWS-GuardDuty
* Added release notes to pack AWS-GuardDuty
* Packs/AWS-GuardDuty/Integrations/AWSGuardDutyEventCollector/AWSGuardDutyEventCollector.yml Docker image update
* Packs/AWS-GuardDuty/Integrations/AWSGuardDuty/AWSGuardDuty.yml Docker image update
* Updated Metadata Of Pack AWS-SecurityHub
* Added release notes to pack AWS-SecurityHub
* Packs/AWS-SecurityHub/Integrations/AWSSecurityHubEventCollector/AWSSecurityHubEventCollector.yml Docker image update
* Updated Metadata Of Pack Aws-SecretsManager
* Added release notes to pack Aws-SecretsManager
* Packs/Aws-SecretsManager/Integrations/AwsSecretsManager/AwsSecretsManager.yml Docker image update
* Update Docker Image To demisto/accessdata (#31216)
* Updated Metadata Of Pack Exterro
* Added release notes to pack Exterro
* Packs/Exterro/Integrations/Exterro/Exterro.yml Docker image update
* Update Docker Image To demisto/oci (#31218)
* Updated Metadata Of Pack OracleCloudInfrastructure
* Added release notes to pack OracleCloudInfrastructure
* Packs/OracleCloudInfrastructure/Integrations/OracleCloudInfrastructureEventCollector/OracleCloudInfrastructureEventCollector.yml Docker image update
* Update Docker Image To demisto/py3-tools (#31217)
* Updated Metadata Of Pack Intezer
* Added release notes to pack Intezer
* Packs/Intezer/Integrations/IntezerV2/IntezerV2.yml Docker image update
* Updated Metadata Of Pack Zabbix
* Added release notes to pack Zabbix
* Packs/Zabbix/Integrations/Zabbix/Zabbix.yml Docker image update
* Updated Metadata Of Pack FeedMalwareBazaar
* Added release notes to pack FeedMalwareBazaar
* Packs/FeedMalwareBazaar/Integrations/MalwareBazaarFeed/MalwareBazaarFeed.yml Docker image update
* Updated Metadata Of Pack FeedGCPWhitelist
* Added release notes to pack FeedGCPWhitelist
* Packs/FeedGCPWhitelist/Integrations/FeedGoogleIPRanges/FeedGoogleIPRanges.yml Docker image update
* Updated Metadata Of Pack AccentureCTI_Feed
* Added release notes to pack AccentureCTI_Feed
* Packs/AccentureCTI_Feed/Integrations/ACTIIndicatorFeed/ACTIIndicatorFeed.yml Docker image update
* Updated Metadata Of Pack SEKOIAIntelligenceCenter
* Added release notes to pack SEKOIAIntelligenceCenter
* Packs/SEKOIAIntelligenceCenter/Integrations/SEKOIAIntelligenceCenter/SEKOIAIntelligenceCenter.yml Docker image update
* Updated Metadata Of Pack JARM
* Added release notes to pack JARM
* Packs/JARM/Integrations/JARM/JARM.yml Docker image update
* Updated Metadata Of Pack Anomali_ThreatStream
* Added release notes to pack Anomali_ThreatStream
* Packs/Anomali_ThreatStream/Integrations/AnomaliThreatStreamv3/AnomaliThreatStreamv3.yml Docker image update
* Updated Metadata Of Pack CommonWidgets
* Added release notes to pack CommonWidgets
* Packs/CommonWidgets/Scripts/RSSWidget/RSSWidget.yml Docker image update
* Updated Metadata Of Pack FiltersAndTransformers
* Added release notes to pack FiltersAndTransformers
* Packs/FiltersAndTransformers/Scripts/Jmespath/Jmespath.yml Docker image update
* CortexXDRIR-generic-polling (#31082)
* - Added new playbook for quarantine_file
- Old playbook deprecated
- New image added
* release notes added
* - New playbook for _Retrieve_File_Playbook_v2 created
- Old playbook _Retrieve_File_Playbook deprecated
- Image was added
* Release notes were added
* Changed the name of the playbook
* Readme file added
* Added image
* fixed image location in readme file
* Update Packs/CortexXDR/Playbooks/Cortex_XDR_-_Retrieve_File_v2.yml
Co-authored-by: Sasha Sokolovich <88268646+ssokolovich@users.noreply.github.com>
* Bump pack from version CortexXDR to 6.0.4.
* Removed unnecessary tests
* Readme files were updated
* Fixes for the playbooks
* fixed Tests/conf.json file
* image issue fixed
* Added new images
* Update Packs/CortexXDR/Playbooks/Cortex_XDR_-_Retrieve_File_Playbook_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/Cortex_XDR_-_Retrieve_File_Playbook_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/ReleaseNotes/6_0_4.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/ReleaseNotes/6_0_4.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/ReleaseNotes/6_0_4.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/ReleaseNotes/6_0_4.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/Cortex_XDR_-_Retrieve_File_Playbook_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/Cortex_XDR_-_quarantine_file_v2_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* PR fixes - new condition to check if the task finished successfully
* release notes updated
* image path fixed
* Added new outputs for playbook
* release notes updated
* fix
* readme files fixed
* image issue
* image issue
* fix
* fix
* fix
* fix
* uploaded new playbook because of the image issue
* fix for image issue
* delete photo
* fixes
* test playbooks fixed
* test playbooks removed
---------
Co-authored-by: Sasha Sokolovich <88268646+ssokolovich@users.noreply.github.com>
Co-authored-by: Content Bot
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Docker Image To demisto/crypto (#31219)
* Updated Metadata Of Pack AzureKeyVault
* Added release notes to pack AzureKeyVault
* Packs/AzureKeyVault/Integrations/AzureKeyVault/AzureKeyVault.yml Docker image update
* Updated Metadata Of Pack AzureSentinel
* Added release notes to pack AzureSentinel
* Packs/AzureSentinel/Integrations/AzureSentinel/AzureSentinel.yml Docker image update
* Updated Metadata Of Pack AzureDevOps
* Added release notes to pack AzureDevOps
* Packs/AzureDevOps/Integrations/AzureDevOps/AzureDevOps.yml Docker image update
* Updated Metadata Of Pack MicrosoftCloudAppSecurity
* Added release notes to pack MicrosoftCloudAppSecurity
* Packs/MicrosoftCloudAppSecurity/Integrations/MicrosoftCloudAppSecurity/MicrosoftCloudAppSecurity.yml Docker image update
* Updated Metadata Of Pack AzureRiskyUsers
* Added release notes to pack AzureRiskyUsers
* Packs/AzureRiskyUsers/Integrations/AzureRiskyUsers/AzureRiskyUsers.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphGroups
* Added release notes to pack MicrosoftGraphGroups
* Packs/MicrosoftGraphGroups/Integrations/MicrosoftGraphGroups/MicrosoftGraphGroups.yml Docker image update
* Updated Metadata Of Pack AzureSQLManagement
* Added release notes to pack AzureSQLManagement
* Packs/AzureSQLManagement/Integrations/AzureSQLManagement/AzureSQLManagement.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphAPI
* Added release notes to pack MicrosoftGraphAPI
* Packs/MicrosoftGraphAPI/Integrations/MicrosoftGraphAPI/MicrosoftGraphAPI.yml Docker image update
* Updated Metadata Of Pack MicrosoftTeams
* Added release notes to pack MicrosoftTeams
* Packs/MicrosoftTeams/Integrations/MicrosoftTeamsManagement/MicrosoftTeamsManagement.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphApplications
* Added release notes to pack MicrosoftGraphApplications
* Packs/MicrosoftGraphApplications/Integrations/MicrosoftGraphApplications/MicrosoftGraphApplications.yml Docker image update
* update pack ignore (#31193)
* Slack event collector: fixed an issue where we get a Bad Request error (#31135)
* fixed an issue where we get a Bad Request error.
* pre-commit
* added test
* fixed Flake8 error
* fixed cr comments
* fixed cr comments
* update Docker image
* YR/Remove-fields-with-one-letter-DBotFindSimilarIncidents/XSUP-29299 (#31161)
* fixes
* code and test
* remove Json feed from this pr
* test
* note
* pre commit
* RN
* CR and Flake8
* format
* pre commit
* Fixes For 'URL Enrichment - Generic v2' Playbook (#31195)
* Fixes For 'URL Enrichment - Generic v2' Playbook
* RN
* Bump pack from version CommonPlaybooks to 2.4.36.
---------
Co-authored-by: Content Bot
* F5 APM Remove XSIAM tags (#31221)
* remove ls from test_e2e_results.sh (#31186)
* [IsEmailAddressInternal] Fix an issue with **domain** argument (#31222)
* First commit
* Added RN
* Update Packs/CommonScripts/ReleaseNotes/1_12_54.md
Co-authored-by: Dean Arbel
---------
Co-authored-by: Dean Arbel
* Deprecate 'Get endpoint details - Generic' Playbook (#31196)
* Deprecate 'Get endpoint details - Generic' Playbook
* RN
* Bump pack from version CommonPlaybooks to 2.4.36.
* Bump pack from version CommonPlaybooks to 2.4.37.
---------
Co-authored-by: Content Bot
* Replacing the deprecated sub-playbook within the 'NGFW Internal Scan'… (#31197)
* Replacing the deprecated sub-playbook within the 'NGFW Internal Scan' XSIAM playbook
* RN
* [Marketplace Contribution] CISO Metrics (#30641) (#31213)
* "pack contribution initial commit"
* Update pack_metadata.json
* Update and rename dashboard-98f353a2-312b-49f2-8e58-d71f60daf3a7-CISO_Metrics.json to dashboard-98f353a2-312b-49f2-8e58-d71f60daf3a7-CommunityCommonDashboards.json
Rename to CommunityCommonDashboards
* Update pack_metadata.json
Renamed "name": "CommunityCommonDashboards"
* Update README.md
Added description
* Update README.md
* Update and rename README.md to README.md
* Rename dashboard-98f353a2-312b-49f2-8e58-d71f60daf3a7-CommunityCommonDashboards.json to dashboard-98f353a2-312b-49f2-8e58-d71f60daf3a7-CommunityCommonDashboards.json
* Rename .pack-ignore to .pack-ignore
* Rename .secrets-ignore to .secrets-ignore
* Rename pack_metadata.json to pack_metadata.json
* Update .pack-ignore
* Update pack_metadata.json
* Update .pack-ignore
* Update and rename dashboard-98f353a2-312b-49f2-8e58-d71f60daf3a7-CommunityCommonDashboards.json to CISOMetrics.json
Renamed to CISOMetrics
* Update pack_metadata.json
* Update pack_metadata.json
* Update README.md
---------
Co-authored-by: xsoar-bot <67315154+xsoar-bot@users.noreply.github.com>
Co-authored-by: Sapir Shuker <49246861+sapirshuker@users.noreply.github.com>
Co-authored-by: David Uhrlaub <90627446+rurhrlaub@users.noreply.github.com>
* Cybereason xsoar v 2.1.14 (#30647) (#31225)
* added v2.1.14 codebase
* fix pr comments
* replace dummy md5 placeholder
* Update Packs/Cybereason/Integrations/Cybereason/Cybereason.py
* updated docker image python version
* updated release notes docker version
* added pagination params
* updated docker image
* fix lint errors
* fix demisto validate errors
* updated release notes
* updated release notes
* updated release notes
* updated command name as per PR comment
* removed manual filtering for response
* updated function name to match the command name format
* updated unit test as per new command name
* added machinename filter to api query
* moved empty output message to the top
* updated docker image tag to latest
* undo changes from unisolate endpoint playbook
---------
Co-authored-by: suraj-metron <87964764+suraj-metron@users.noreply.github.com>
Co-authored-by: Sapir Shuker <49246861+sapirshuker@users.noreply.github.com>
* fixed polling support (#30873)
* fixed polling support
* fixed rn
* added rn
* added rn
* XSUP-30786/Fix (#31168)
* Added failing UT
* Fixed the issue
* Updated docker image
* Updated RN
* Update Packs/PAN-OS/ReleaseNotes/2_1_15.md
Co-authored-by: Dan Tavori <38749041+dantavori@users.noreply.github.com>
* Updated the bug fix and the UT
* updated docker image
---------
Co-authored-by: Dan Tavori <38749041+dantavori@users.noreply.github.com>
* rewrite to js FirstArrayElement and LastArrayElement (#31228)
* rewrite to js
* added tpb
* added empty test case to tpb
* precommit fixes
* change fromversion so build wont fail
* Enable Core REST API with general XSIAM endpoints (#31226)
* mostly works
* added release notes
* fixes from review
* F5 APM fixed the marketplace build failure (#31236)
* F5 APM Remove XSIAM tags
* fix marketplace error
* Add incidents field (#30393) (#31233)
* add rawJSON field to incidents
* release notes
* update docker image tag
* nit
* fetching incident details
* mapper + incident fields
* remove incorrect incident field files
* new incident field files, new mapper
* sdk validate command changes
* update release noteS
* validation errors
* fix validation errors
* undo release notes changes
* undo release notes change
* undo release notes
* undo release notes
* undo release notes
* nit
* new release notes
* remove playbook id
* update docker image tag
* revert release notes
* revert RN
* nit- remove filters used for testing
* add details field to threats
* remove try/except blocks
* changing version
* Update Abnormal_Security_Custom_Incident_types.json change from version
* nit - remove changes used for demo
* updating docker image
* update docker image tag
---------
Co-authored-by: William Olyslager
Co-authored-by: sapirshuker
Co-authored-by: Sapir Shuker <49246861+sapirshuker@users.noreply.github.com>
* Update Docker Image To demisto/python3 (#31242)
* Updated Metadata Of Pack CIRCL
* Added release notes to pack CIRCL
* Packs/CIRCL/Integrations/CirclCVESearch/CirclCVESearch.yml Docker image update
* Updated Metadata Of Pack ipinfo
* Added release notes to pack ipinfo
* Packs/ipinfo/Integrations/ipinfo_v2/ipinfo_v2.yml Docker image update
* Updated Metadata Of Pack AutoFocus
* Added release notes to pack AutoFocus
* Packs/AutoFocus/Integrations/FeedAutofocus/FeedAutofocus.yml Docker image update
* Packs/AutoFocus/Integrations/AutofocusV2/AutofocusV2.yml Docker image update
* Updated Metadata Of Pack MailSenderNew
* Added release notes to pack MailSenderNew
* Packs/MailSenderNew/Integrations/MailSenderNew/MailSenderNew.yml Docker image update
* avoid to update Docker for AutoFocusv2
---------
Co-authored-by: israelpolishook
* Fixes For 'IP Enrichment - Generic v2' Playbook (#31183)
* Fixes For 'IP Enrichment - Generic v2' Playbook
* RN
* RN
* Updated the 'InternalRange' playbook input's default value.
* configured the 'extended_data' and 'threat_model_association' sub-playbook inputs
* Bump pack from version CommonPlaybooks to 2.4.36.
* Bump pack from version CommonPlaybooks to 2.4.37.
* changed the default value of the 'ResolveIP' playbook input
* re-added RN after merging from master
* Fixes RN
---------
Co-authored-by: Content Bot
* Check if should run Instance role (#31245)
* Added the sync from the saas bucket and modified the verify script to take the revision from the correct bucket. (#31254)
* AWS Organizations (#30525)
* init
* commands template
* aws-org-children-list
* more commands
* even more commands
* added account commands
* removed enhancement commands
* use json_transform
* unit-tests init
* unit-tests continued
* unit-tests continued some more
* TPB
* one more unit-test
* one more unit-test
* one more unit-test
* name change
* TPB
* docs complete
* pack readme
* pack readme part 2
* readme modified
* more tests
* more tests
* use get()
* adde description
* removed isFetch
* added image
* name change
* CR changes
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update docker
* put the commands back in
* code complete
* yml part 2
* yml part 3
* test template
* unit-tests continued some more
* unit-tests almost complete
* unit-tests complete
* fixed a few bugs
* fixed unit-tests
* added readme
* update readme
* added missing descriptions to readme
* TPB
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* CR changes
* demo changes
* update docker
* build wars: round 1
* build wars: round 2
* build wars: round 3; add unit-tests
* build wars: round 4
* build wars: round 5
* build wars: round 6
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* NextToken in CommandResults (#30501)
* init
* new design
* added error in case of non nested input
* RN
* a tad more docs
* Bump pack from version Base to 1.32.47.
* Bump pack from version Base to 1.32.48.
* Bump pack from version Base to 1.32.49.
* improved doc-string
* resolve conflicts
* resolve conflicts
* Bump pack from version Base to 1.32.52.
---------
Co-authored-by: Content Bot
* demisto-sdk-release 1.24.0 (#31268)
* poetry files
* update validate manager imports (#31179)
* update validate manager imports
* revert
* Update Tests/configure_and_test_integration_instances.py
* Edit file types test (#31170)
* edited tests
* s
* s
* edit
---------
Co-authored-by: Content Bot
Co-authored-by: Yuval Hayun <70104171+YuvHayun@users.noreply.github.com>
Co-authored-by: merit-maita <49760643+merit-maita@users.noreply.github.com>
Co-authored-by: JudithB <132264628+jbabazadeh@users.noreply.github.com>
* modified modeling rules of clearswift dlp (#31247)
* modified modeling rules of clearswift dlp
* modified the parsing rule of clearswiftdlp
* Added release notes.
* added dlp to pack ignore
* added Clearswift to pack ignore
* QRadar: continue to poll in case of networking issues (#31084)
* Generalize the mode option in pre-commit (#30663)
* args updated to match the update in the sdk
* add merge-coverage-report and coverage-analyze
* updaing pyproject.toml
* poetry lock
* restoring pyproject.toml and poetry.lock
* pre-commit.yml
* updates
* test comment
* use sdk ref
* if
* add github output
* revert ilan changes
* merge-pytest-reports
---------
Co-authored-by: ilan
* EXPANDR-1576 CortexXpanse Remediation Guidance changes (#31190)
* EXPANDR-1576 CortexXpanse Remediation Guidance changes (#30712)
* CortexXpanse RG changes
* Fix flake8 errors
* Fix unit test cases
* Update docker version
* update command name
* Readme updates
* docker update
* Ignore BC error
* fix packignore
* Update release notes
* update breaking change notes
* update breaking change notes
* correct RN
---------
Co-authored-by: Chait A <112722030+capanw@users.noreply.github.com>
Co-authored-by: ilappe
* Feature/cyberint enhancement (#31252)
* Feature/cyberint enhancement (#30493)
* Update Docker Image To demisto/py3-tools (#25523)
* Updated Metadata Of Pack FeedAWS
* Added release notes to pack FeedAWS
* Packs/FeedAWS/Integrations/FeedAWS/FeedAWS.yml Docker image update
* update Cyberint Pack
* update release note and incidentfields
* update CommonType release note
* update CommonType relesenotes
* update CommonType relese notes
* update CyberInt Related entity name
* update release notes
* add new incident field: Alert Data
* foramt alert_data
* update CyberInt Related Entity name to avoid validation errors
* reset the CyberInt Related Entity name
* update incident field name
* Update 3_3_93.md
* pre commit update docker
* added known words
* fixed the RN
* known words
---------
Co-authored-by: TalGumi <101499620+TalGumi@users.noreply.github.com>
Co-authored-by: omerKarkKatz <95565843+omerKarkKatz@users.noreply.github.com>
Co-authored-by: okarkkatz
* [xsoar-8 coverage] - use poll functions from SDK clients (#31144)
* update poetry
* use poll functions
* test against builds
* try to fix ssl issue
* timeout = 300 + verify ssl
* fix ssl issues
* fix incident pull
* fix
* make verify=false by default
* fix ports bug
* use sdk master
* revert poetry
* revert infra used for testing
* [CrowdStrike Falcon Intel v2] Fixed an issue in 'cs-actors' and 'cs-reports' commands (#31265)
* Fix the 'NoneType' object is not iterable issue
* ruff
* Update the docker image; Add RN
* Update Packs/CrowdStrikeIntel/ReleaseNotes/2_0_34.md
Co-authored-by: Dean Arbel
---------
Co-authored-by: Dean Arbel
* oncall- installation orders (#31253)
* test
* test
* revert debugs
* pre-commit
---------
Co-authored-by: Jas Beilin
* Core rest api docs fix (#31262)
* Improved descriptions.
* Added docs
* Added rn.
* Changed i.e to e.g
* bugfix/XSUP-30713/port-scan-pb-issue-incident-failure (#31154)
* Fix playbook input's default value, change to not
required, add check for value not empty
* Update playbook image
* Update release notes
* Bump pack from version CortexXDR to 6.0.5.
* Moved InternalIPRanges input check to better location
* Fix review comments
---------
Co-authored-by: Content Bot
* [PagerDuty v2] Added Support For Pagination (#30959)
* commit init - lint and type annotation
* typing
* pagination function and some typing
* fix api limit and pagination
* added UT and test_data
* added RN and description for args
* generate readme
* update docker
* added UT
* fix flake8
* more docstring, one more UT, fix send unnecessary parameters
* fix f-string
* fix pep8
* revert copy
* fix parameters name
* docs review
* update docker
* [ASM] EXPANDR 7225 - Update Ev1 Integration Display Name (#31234) (#31276)
* Update Display Name
* Update release notes
* Update docker image and add period to descriptions
Co-authored-by: John <40349459+BigEasyJ@users.noreply.github.com>
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
* Update Docker Image To demisto/python3 (#31286)
* Updated Metadata Of Pack QualysFIM
* Added release notes to pack QualysFIM
* Packs/QualysFIM/Integrations/QualysFIM/QualysFIM.yml Docker image update
* Updated Metadata Of Pack FortiSIEM
* Added release notes to pack FortiSIEM
* Packs/FortiSIEM/Integrations/FortiSIEMV2/FortiSIEMV2.yml Docker image update
* Updated Metadata Of Pack FreshworksFreshservice
* Added release notes to pack FreshworksFreshservice
* Packs/FreshworksFreshservice/Integrations/FreshworksFreshservice/FreshworksFreshservice.yml Docker image update
* Updated Metadata Of Pack KnowBe4_KMSAT
* Added release notes to pack KnowBe4_KMSAT
* Packs/KnowBe4_KMSAT/Integrations/KnowBe4KMSATEventCollector/KnowBe4KMSATEventCollector.yml Docker image update
* Packs/KnowBe4_KMSAT/Integrations/KnowBe4KMSAT/KnowBe4KMSAT.yml Docker image update
* Updated Metadata Of Pack SafeNet_Trusted_Access
* Added release notes to pack SafeNet_Trusted_Access
* Packs/SafeNet_Trusted_Access/Integrations/SafeNetTrustedAccessEventCollector/SafeNetTrustedAccessEventCollector.yml Docker image update
* Updated Metadata Of Pack DelineaSS
* Added release notes to pack DelineaSS
* Packs/DelineaSS/Integrations/DelineaSS/DelineaSS.yml Docker image update
* Updated Metadata Of Pack Cryptocurrency
* Added release notes to pack Cryptocurrency
* Packs/Cryptocurrency/Integrations/Cryptocurrency/Cryptocurrency.yml Docker image update
* Updated Metadata Of Pack PANOSPolicyOptimizer
* Added release notes to pack PANOSPolicyOptimizer
* Packs/PANOSPolicyOptimizer/Integrations/PANOSPolicyOptimizer/PANOSPolicyOptimizer.yml Docker image update
* Updated Metadata Of Pack DeveloperTools
* Added release notes to pack DeveloperTools
* Packs/DeveloperTools/Integrations/CreateIncidents/CreateIncidents.yml Docker image update
* Add XSOAR_SAAS section to EDL description (#31264)
* add XSOAR_SAAS section to EDL description
* update RN
* [XSUP 30575] Added full fields query param (#31272)
* get indicators full fields data
* pre-commit
* release notes
* tests and CR fixes
* Update Packs/FeedCrowdstrikeFalconIntel/ReleaseNotes/2_1_13.md
Co-authored-by: Dan Tavori <38749041+dantavori@users.noreply.github.com>
---------
Co-authored-by: Dan Tavori <38749041+dantavori@users.noreply.github.com>
* Update Docker Image To demisto/boto3py3 (#31287)
* Updated Metadata Of Pack SecurityIntelligenceServicesFeed
* Added release notes to pack SecurityIntelligenceServicesFeed
* Packs/SecurityIntelligenceServicesFeed/Integrations/SecurityIntelligenceServicesFeed/SecurityIntelligenceServicesFeed.yml Docker image update
* Updated Metadata Of Pack AWS-IAM
* Added release notes to pack AWS-IAM
* Packs/AWS-IAM/Integrations/AWS-IAM/AWS-IAM.yml Docker image update
* Updated Metadata Of Pack AWS-Route53
* Added release notes to pack AWS-Route53
* Packs/AWS-Route53/Integrations/AWSRoute53/AWSRoute53.yml Docker image update
* Updated Metadata Of Pack AWS-AccessAnalyzer
* Added release notes to pack AWS-AccessAnalyzer
* Packs/AWS-AccessAnalyzer/Integrations/AWS-AccessAnalyzer/AWS-AccessAnalyzer.yml Docker image update
* Updated Metadata Of Pack AWS-GuardDuty
* Added release notes to pack AWS-GuardDuty
* Packs/AWS-GuardDuty/Integrations/AWSGuardDutyEventCollector/AWSGuardDutyEventCollector.yml Docker image update
* Packs/AWS-GuardDuty/Integrations/AWSGuardDuty/AWSGuardDuty.yml Docker image update
* Updated Metadata Of Pack AWS-SecurityHub
* Added release notes to pack AWS-SecurityHub
* Packs/AWS-SecurityHub/Integrations/AWSSecurityHubEventCollector/AWSSecurityHubEventCollector.yml Docker image update
* Updated Metadata Of Pack Aws-SecretsManager
* Added release notes to pack Aws-SecretsManager
* Packs/Aws-SecretsManager/Integrations/AwsSecretsManager/AwsSecretsManager.yml Docker image update
* Update Docker Image To demisto/accessdata (#31288)
* Updated Metadata Of Pack Exterro
* Added release notes to pack Exterro
* Packs/Exterro/Integrations/Exterro/Exterro.yml Docker image update
* Update Docker Image To demisto/oci (#31290)
* Updated Metadata Of Pack OracleCloudInfrastructure
* Added release notes to pack OracleCloudInfrastructure
* Packs/OracleCloudInfrastructure/Integrations/OracleCloudInfrastructureEventCollector/OracleCloudInfrastructureEventCollector.yml Docker image update
* Update Docker Image To demisto/py3-tools (#31289)
* Updated Metadata Of Pack Intezer
* Added release notes to pack Intezer
* Packs/Intezer/Integrations/IntezerV2/IntezerV2.yml Docker image update
* Updated Metadata Of Pack Zabbix
* Added release notes to pack Zabbix
* Packs/Zabbix/Integrations/Zabbix/Zabbix.yml Docker image update
* Updated Metadata Of Pack FeedMalwareBazaar
* Added release notes to pack FeedMalwareBazaar
* Packs/FeedMalwareBazaar/Integrations/MalwareBazaarFeed/MalwareBazaarFeed.yml Docker image update
* Updated Metadata Of Pack FeedGCPWhitelist
* Added release notes to pack FeedGCPWhitelist
* Packs/FeedGCPWhitelist/Integrations/FeedGoogleIPRanges/FeedGoogleIPRanges.yml Docker image update
* Updated Metadata Of Pack AccentureCTI_Feed
* Added release notes to pack AccentureCTI_Feed
* Packs/AccentureCTI_Feed/Integrations/ACTIIndicatorFeed/ACTIIndicatorFeed.yml Docker image update
* Updated Metadata Of Pack SEKOIAIntelligenceCenter
* Added release notes to pack SEKOIAIntelligenceCenter
* Packs/SEKOIAIntelligenceCenter/Integrations/SEKOIAIntelligenceCenter/SEKOIAIntelligenceCenter.yml Docker image update
* Updated Metadata Of Pack JARM
* Added release notes to pack JARM
* Packs/JARM/Integrations/JARM/JARM.yml Docker image update
* Updated Metadata Of Pack Anomali_ThreatStream
* Added release notes to pack Anomali_ThreatStream
* Packs/Anomali_ThreatStream/Integrations/AnomaliThreatStreamv3/AnomaliThreatStreamv3.yml Docker image update
* Updated Metadata Of Pack CommonWidgets
* Added release notes to pack CommonWidgets
* Packs/CommonWidgets/Scripts/RSSWidget/RSSWidget.yml Docker image update
* Updated Metadata Of Pack FiltersAndTransformers
* Added release notes to pack FiltersAndTransformers
* Packs/FiltersAndTransformers/Scripts/Jmespath/Jmespath.yml Docker image update
* Update Docker Image To demisto/armorblox (#31291)
* Updated Metadata Of Pack Armorblox
* Added release notes to pack Armorblox
* Packs/Armorblox/Integrations/Armorblox/Armorblox.yml Docker image update
* Update Docker Image To demisto/crypto (#31292)
* Updated Metadata Of Pack AzureKeyVault
* Added release notes to pack AzureKeyVault
* Packs/AzureKeyVault/Integrations/AzureKeyVault/AzureKeyVault.yml Docker image update
* Updated Metadata Of Pack AzureSentinel
* Added release notes to pack AzureSentinel
* Packs/AzureSentinel/Integrations/AzureSentinel/AzureSentinel.yml Docker image update
* Updated Metadata Of Pack AzureDevOps
* Added release notes to pack AzureDevOps
* Packs/AzureDevOps/Integrations/AzureDevOps/AzureDevOps.yml Docker image update
* Updated Metadata Of Pack MicrosoftCloudAppSecurity
* Added release notes to pack MicrosoftCloudAppSecurity
* Packs/MicrosoftCloudAppSecurity/Integrations/MicrosoftCloudAppSecurity/MicrosoftCloudAppSecurity.yml Docker image update
* Updated Metadata Of Pack AzureRiskyUsers
* Added release notes to pack AzureRiskyUsers
* Packs/AzureRiskyUsers/Integrations/AzureRiskyUsers/AzureRiskyUsers.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphGroups
* Added release notes to pack MicrosoftGraphGroups
* Packs/MicrosoftGraphGroups/Integrations/MicrosoftGraphGroups/MicrosoftGraphGroups.yml Docker image update
* Updated Metadata Of Pack AzureSQLManagement
* Added release notes to pack AzureSQLManagement
* Packs/AzureSQLManagement/Integrations/AzureSQLManagement/AzureSQLManagement.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphAPI
* Added release notes to pack MicrosoftGraphAPI
* Packs/MicrosoftGraphAPI/Integrations/MicrosoftGraphAPI/MicrosoftGraphAPI.yml Docker image update
* Updated Metadata Of Pack MicrosoftTeams
* Added release notes to pack MicrosoftTeams
* Packs/MicrosoftTeams/Integrations/MicrosoftTeamsManagement/MicrosoftTeamsManagement.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphApplications
* Added release notes to pack MicrosoftGraphApplications
* Packs/MicrosoftGraphApplications/Integrations/MicrosoftGraphApplications/MicrosoftGraphApplications.yml Docker image update
* Update Docker Image To demisto/sixgill (#31293)
* Updated Metadata Of Pack Cybersixgill-ActionableAlerts
* Added release notes to pack Cybersixgill-ActionableAlerts
* Packs/Cybersixgill-ActionableAlerts/Integrations/CybersixgillActionableAlerts/CybersixgillActionableAlerts.yml Docker image update
* Updated Metadata Of Pack Sixgill-Darkfeed
* Added release notes to pack Sixgill-Darkfeed
* Packs/Sixgill-Darkfeed/Integrations/Sixgill_Darkfeed_Enrichment/Sixgill_Darkfeed_Enrichment.yml Docker image update
* Packs/Sixgill-Darkfeed/Integrations/Sixgill_Darkfeed/Sixgill_Darkfeed.yml Docker image update
* Update Docker Image To demisto/carbon-black-cloud (#31295)
* Updated Metadata Of Pack CarbonBlackDefense
* Added release notes to pack CarbonBlackDefense
* Packs/CarbonBlackDefense/Integrations/CarbonBlackLiveResponseCloud/CarbonBlackLiveResponseCloud.yml Docker image update
* Update Docker Image To demisto/taxii2 (#31294)
* Updated Metadata Of Pack FeedDHS
* Added release notes to pack FeedDHS
* Packs/FeedDHS/Integrations/DHSFeedV2/DHSFeedV2.yml Docker image update
* Updated Metadata Of Pack FeedUnit42v2
* Added release notes to pack FeedUnit42v2
* Packs/FeedUnit42v2/Integrations/FeedUnit42v2/FeedUnit42v2.yml Docker image update
* MS IIS Update2 (#31256)
* Updated MicrosoftIISWebServerModelingRules_1_3
* Updated ModelingRules filters
* Updated ModelingRules filters
* Updated ReleaseNotes
* Upated ReleaseNotes
* CrowdStrikeFalconX-genreic-polling (#31189)
* old playbooks deprecated and new one added
* readme file edited
* set the interval from the inputs
* fixes for release notes
* added extensions to known words
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_File_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_File_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_File_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_URL_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_File_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_File_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_File_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/ReleaseNotes/1_2_37.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/ReleaseNotes/1_2_37.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/ReleaseNotes/1_2_37.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/ReleaseNotes/1_2_37.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_File_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_File_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_File_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* minor fixes for description
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_URL_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_URL_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CrowdStrikeFalconX/Playbooks/Detonate_URL_-_CrowdStrike_Falcon_Intelligence_Sandbox_v2.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Add Symantec MSS to ignored items (#31296)
* [XSUP 30870] Added full fields option for cs-actors and cs-reports commands (#31271)
* Added the display_full_fields argument
* pre-commit
* release notes
* tests and CR fixes
* resolve conflict
* pre-commit
* CR fixes
* docker
* pre-commit
* add myself as codeowner (#31314)
* ORKL Feed Integration 1.0.0 Initial Release (#31166)
* ORKL Feed Integration 1.0.0 Initial Release (#31101)
Co-authored-by: Martin Ohl
* [VirusTotal] Add suspicious threshold (#31220)
* [VirusTotal] Add suspicious threshold (#31021)
* fixing CimTrak_test.py unit tests (#31308)
fixing CimTrak_test.py unit tests #31308
* Add new command and bug fix. (#31311)
* Anomali ThreatStream v3 - Fix threatstream-get-indicators command (#31269)
* fix get_indicators method
* update RN
* update docker
* update test
* update test
* update get_indicators method
* update RN
* Update Packs/Anomali_ThreatStream/ReleaseNotes/2_2_9.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* update docker
* update docker
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* SentinelOne v2: Add 2 new commands (#31312)
* fixing jira file attachments (#31297)
fixing jira file attachments, fixing mapping of newly created tickets #31297
* CiscoSMA Update (#31315)
* Updated ModelingRules
* Updated ReleaseNotes
* Updated ReleaseNotes
* updated docs (#31192)
* updated docs
* running pre-commit and docker
* docker update
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* remove package-lock file
* cr note
* Update Packs/MicrosoftGraphDeviceManagement/ReleaseNotes/1_1_20.md
Co-authored-by: EyalPintzov <91007713+eyalpalo@users.noreply.github.com>
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
Co-authored-by: EyalPintzov <91007713+eyalpalo@users.noreply.github.com>
* Fix an issue when there is only one incident in fetch_incidents powershell (#31267)
* added -AsArray
* updated the docker image and added .
* RN
* unit tests and docker image
* rn
* docker image and release notes
* Update Packs/Base/ReleaseNotes/1_32_53.md
Co-authored-by: EyalPintzov <91007713+eyalpalo@users.noreply.github.com>
* updated the unit tests
---------
Co-authored-by: EyalPintzov <91007713+eyalpalo@users.noreply.github.com>
* Get Entity Alerts by MITRE Tactics - Performance Improvements (Refactor) (#31232)
* Added playbooks
* New playbooks images, formatted playbooks, and added RN
* Updated pb image to be in light mode
* Further improvements to playbooks, updated docs, and updated playbook images
* Bump pack from version CortexXDR to 6.0.6.
* Changed alert to incident to fix validation
* Descriptions
---------
Co-authored-by: Content Bot
* fix for sdk nightly e2e tests (#31310)
* [qradar-v3] - handle connection errors (#31246)
* [qradar-v3] - handle connection errors
* add uts
* bump rn
* remove irrelevant imports
* update code
* timeout = 300
* bump rn
* update implementation
* docker image
* fixes
* remove imports
* rn
* update debug-message
* update log
* fix docker-image
* fix ut
* oncall-sdk-nightly-create-xsoar-instance (#31300)
* overwrite the filter env file
* remove space
* remove print
* Update .gitlab/ci/.gitlab-ci.on-push.yml
Co-authored-by: Koby Meir
---------
Co-authored-by: Koby Meir
* [ASM] - EXPANDER 7238 - Jira Playbook Support for V2 and V3 Project Key (#31273) (#31322)
* Add support V2 and V3, remove default project key
- Add data collection task for customer
- Leave Jira Project Key input as blank
- Add support for project key passed into Jira V2 and V3 integrations
* Add release notes
* Update Playbook ReadMe
* Add task description
* Update release notes
Co-authored-by: John <40349459+BigEasyJ@users.noreply.github.com>
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
* Support contributions when the name of the repo isn't content (#31320)
* update handle_external_pr.py
* set repo_name arg as optional
* Oncall sdk nightly create xsoar instance (#31324)
Oncall sdk nightly create xsoar instance #31324
* CIAC-4556/xdr-remote-psexec-lolbin-command-execution-playbook (#29092)
* Add playbook and readme files
* Add updated files
* Add playbook image
* Update release notes
* Fix validation error
* Bump pack from version CortexXDR to 5.1.0.
* Bump pack from version CortexXDR to 5.2.0.
* Bump pack from version CortexXDR to 5.2.0.
* Bump pack from version CortexXDR to 5.2.0.
* Add CommandLine verdict to layout
* Update according to demo review comments
* Bump pack from version CortexXDR to 5.2.0.
* Bump pack from version CortexXDR to 5.2.0.
* Add field for cmd line verdict
* Update layout
* Fix review comments
* Update from master
* Update Packs/CortexXDR/ReleaseNotes/5_2_0.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/ReleaseNotes/5_2_0.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Remote_PsExec_with_LOLBIN_command_execution_alert_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Fix review comments and validations
* Apply suggestions from code review
Fix docs review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Remote_PsExec_with_LOLBIN_command_execution_alert.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Remote_PsExec_with_LOLBIN_command_execution_alert.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Remote_PsExec_with_LOLBIN_command_execution_alert.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Remote_PsExec_with_LOLBIN_command_execution_alert.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Remote_PsExec_with_LOLBIN_command_execution_alert.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Remote_PsExec_with_LOLBIN_command_execution_alert.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/Playbooks/playbook-Cortex_XDR_-_Remote_PsExec_with_LOLBIN_command_execution_alert.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Fix review comments
* Remove duplicate task for alert details, update playbook image
* Fix skipifunavailable validations and update release notes
* Fix review comments
* Update release notes
* Update release notes
* Bump pack from version CortexXDR to 5.2.0.
* Fix review comments
* Update release notes
* Bump pack from version CortexXDR to 5.2.2.
* Bump pack from version CortexXDR to 5.2.3.
* Fix review comments
* Fix validation error
* Fix validation errors
* Update release notes
* Fix conflicts
* removed already added incident field
* Update release notes
* Fix validation errors
* Fix validation errors
* revert file changes
* Fix validation errors
* Fix validation errors
* Bump pack from version CortexXDR to 6.0.4.
* Fix review comments
* Fix review comments
* Update to correct playbook image
* Bump pack from version CortexXDR to 6.0.5.
* Update 6_0_5.md
* Update release notes
* Update 6_0_5.md
* Bump pack from version CortexXDR to 6.0.7.
* Fix precommit errors
---------
Co-authored-by: Content Bot
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update README.md (#31299)
* Last Mirrored New Field & Qradar fix (#31251)
* add field
* Bump pack from version CommonTypes to 3.3.95.
* fix
* review fix
---------
Co-authored-by: Content Bot
* Update native candidate to py3-native:8.4.0.82817 (#31319)
* SplunkPy missing incidents (#30783)
* Used exclusion of even ids
* Reverted changes in unit tests
* Fixed unbound issue
* Added last fetched notables
* Added potential solution
* Comments in UTs
* Added UTs
* Added UTs with explanation
* Added RNs
* Fixed UTs and updated how we exclude ids
* Fixed conflicts
* Fixed CR
* Fixed conflicts
* Updated docker image
* Fixed pre-commit in test file
* Removed second pytest
* Fixed comments in test file
* MATI - Supporting multiple inputs for generic enrichment commands (#30940) (#31334)
* Supporting multiple inputs for generic enrichment commands
* Return list of CommandResults
* Re-adding rawJSON
* Bumping docker version
* Relesase Notes
* Tests
* Tests
* Adding details to contexts
* Fixing tests
* Bumping docker
* Bumping docker
* Fixing spacing
* Fixing spacing
* Fixing fetch
---------
Co-authored-by: Christopher Hultin
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
* [Cortex Data Lake] Update the Docker Image (#31337)
* Support Threat Assessment functionality in MS Graph Security (#30110)
* added yml and the first command in code
* added commands
* added to description in yml
* added readme for first command
* added readme to second command
* added third command to readme
* added url command to readme
* added list command to readme
* added tests files
* minor edits
* added unittests
* added unittest
* updated docker image
* added rn
* edited readme
* edit
* fixed lint errors
* fixed validation errors
* fixed rn
* edits precommits errors
* fixed unittest for test auth code
* edited tpb
* added unittests
* to revert some of these changes
* update after doc review
* added unittests
* removed checking server version in CSP
* updated docker image
* added rn
* Bump pack from version Base to 1.32.41.
* reverted changes for csp
* reveeted changes
* deleted rn
* added fromversion field
* added unittest
* updated for pre commit
* updated for pre commit
* edits after build failed
* removed file
* edits
* added the tpb
* fixed tpb
* edited the list command
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/ReleaseNotes/2_2_5.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/MicrosoftGraphSecurity/Integrations/MicrosoftGraphSecurity/MicrosoftGraphSecurity.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* updated docker image
* edited after build failed
* reverted changes
* updated do
* added arg
* added rn
* updated docker image
* edit
* edits after cr
* updated do
* edited the get user call
* checked the 2 other commands
* edited yml
* updated do
* edited test
* removed comments
* updated do
* edit
* edit
---------
Co-authored-by: Content Bot
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* incident field helloworld onprem (#31340)
* update ParseEmailFilesV2 to 0.1.19 (#31331)
* update Docker image and added bcc
* update rn
* update tests
* Update Packs/CommonScripts/ReleaseNotes/1_12_55.md
Co-authored-by: Shahaf Ben Yakir <44666568+ShahafBenYakir@users.noreply.github.com>
---------
Co-authored-by: Shahaf Ben Yakir <44666568+ShahafBenYakir@users.noreply.github.com>
* update readme (#31343)
* [CommonServer.js] Update emailRegex (#31148)
change email regex
* Ciac 3790/add auto determine LDAP vendor (#31124)
* Added auto determine LDAP vendor
* Added test and RN
* fix lint and rn
* added to readme
* docker
* changed default vendor param to auto
* [Versa Director] Update response data formats (#31327)
* Remove accept: application/xml from get requests
* Remove redundant get() from request responses
* Update UTs
* Release notes; pre-commit updates
* Update UTs; Revert relevant get() functions
* Revert relevant get() functions
* Fix syntax error
* Update Packs/VersaDirector/ReleaseNotes/1_0_7.md
Co-authored-by: Jasmine Beilin <71636766+JasBeilin@users.noreply.github.com>
* Update 1_0_7.md
---------
Co-authored-by: Jasmine Beilin <71636766+JasBeilin@users.noreply.github.com>
* Replace LastMirroredInTime incident field with Last Mirrored Time Stamp incident field in QRadar (#31281)
* add field
* Last Mirrored Time Stamp
* fix unrelated release notes
* RN
* docker image and release notes
* rn
* rn
* docker image and release notes
* RN
* updates
* update
* unit tests for the script
* update rn and bc
* docstring for the ubit tests
---------
Co-authored-by: arikday
Co-authored-by: ArikDay <115150768+ArikDay@users.noreply.github.com>
* Tessian integration setup (#31350)
* Tessian integration setup (#31028)
* revert package-lock.json
---------
Co-authored-by: NicBunn-PlutoFlume <112942358+NicBunn-PlutoFlume@users.noreply.github.com>
Co-authored-by: adi88d
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* Kiteworks Modeling CIAC-6377 (#31230)
* init-pack
* parsing-rules
* json-format-modeling
* README.md
* modeling-rules
* refactor-modeling-rules
* fix-modeling-rules-issues
* single-line-format-modeling
* activity-group-type-modeling
* refactor-modeling-rules
* refactor-modeling-rules
* Update Packs/Kiteworks/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* refactor-modeling-rules
* refactor-modeling-rules
* modeling-rules-json-fix
* modeling-rules-json-refactor
* modeling-rules-remove-unused-field
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Prisma SASE - Quarantine Host With Active Threat (#31346)
* New playbook for Prisma SASE
* update RN
* update RN
* update playbook description
* update playbook readme
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* update RN
* update playbook readme
* update RN
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Symantec web security service pack long running (#30990)
* first commit
* commit
* commit
* first commit
* update pack_metadata file
* extract_logs_from_response changes
* get_events_command changes
* commit
* commit
* add logs
* commit
* commit
* commit
* commit
* commit
* commit
* commit
* commit
* commit
* commit
* commit
* commit
* commit
* Fixed the memory load on Docker
* commit
* first commit for rewrite
* commit
* commit
* add UT and finish implementation
* design
* Change pack name
* add-modeling-rules
* add-parsing-rules
* siem-content-minor-fixes
* add UT and docstring
* add-siem-documentation
* update-siem-documentation
* update-siem-documentation
* commit
* Change readme file
* fix UT and add description to pack_metadata
* commit
* fix mypy flake8
* add UT
* refactor-siem-content
* Apply suggestions from code review
Comment corrections
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* comment corrections
* comment corrections and add UT for it
* comment correction
* mypy
* update Docker
* comment corrections
* comment corrections
* update docker
* fix UT and pre-commit
* commit
* commit
* fix pre commit
* commit
---------
Co-authored-by: Chanan Welt
Co-authored-by: cweltPA <129675344+cweltPA@users.noreply.github.com>
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* FireEye ETP Event Collector fixes (#30819)
* Fixed date parsing
* format and tests
* fixed date parsing from and to the api
* fixed tests
* fixed invalid date order
* fetch in asc order
* fetch in asc order
* fix unitesing
* fix potential formatting issue
* change first_run
* change first_run
* Fix RN
* Fix lint
* Fix lint
* added unitests
* added unitests
* CR fixes
* CR fixes
* Update Docker Image To demisto/accessdata (#31373)
* Updated Metadata Of Pack Exterro
* Added release notes to pack Exterro
* Packs/Exterro/Integrations/Exterro/Exterro.yml Docker image update
* Update Docker Image To demisto/boto3py3 (#31372)
* Updated Metadata Of Pack SecurityIntelligenceServicesFeed
* Added release notes to pack SecurityIntelligenceServicesFeed
* Packs/SecurityIntelligenceServicesFeed/Integrations/SecurityIntelligenceServicesFeed/SecurityIntelligenceServicesFeed.yml Docker image update
* Updated Metadata Of Pack AWS-IAM
* Added release notes to pack AWS-IAM
* Packs/AWS-IAM/Integrations/AWS-IAM/AWS-IAM.yml Docker image update
* Updated Metadata Of Pack AWS-Route53
* Added release notes to pack AWS-Route53
* Packs/AWS-Route53/Integrations/AWSRoute53/AWSRoute53.yml Docker image update
* Updated Metadata Of Pack AWS-AccessAnalyzer
* Added release notes to pack AWS-AccessAnalyzer
* Packs/AWS-AccessAnalyzer/Integrations/AWS-AccessAnalyzer/AWS-AccessAnalyzer.yml Docker image update
* Updated Metadata Of Pack AWS-GuardDuty
* Added release notes to pack AWS-GuardDuty
* Packs/AWS-GuardDuty/Integrations/AWSGuardDutyEventCollector/AWSGuardDutyEventCollector.yml Docker image update
* Packs/AWS-GuardDuty/Integrations/AWSGuardDuty/AWSGuardDuty.yml Docker image update
* Updated Metadata Of Pack AWS-SecurityHub
* Added release notes to pack AWS-SecurityHub
* Packs/AWS-SecurityHub/Integrations/AWSSecurityHubEventCollector/AWSSecurityHubEventCollector.yml Docker image update
* Updated Metadata Of Pack Aws-SecretsManager
* Added release notes to pack Aws-SecretsManager
* Packs/Aws-SecretsManager/Integrations/AwsSecretsManager/AwsSecretsManager.yml Docker image update
* [ASM] - EXPANDER 3741 - XSIAM Layout and Rule (#31352)
* [ASM] - EXPANDER 3741 - XSIAM Layout and Rule (#31212)
* Update Rem. Guidance Playbook, add new fields
Created fields:
- "ASM - Attack Surface Rule Category"
- "ASM - Attack Surface Rule Description"
- "ASM - Attack Surface Rule Priority"
- "ASM - Attack Surface Rule Remediation Guidance"
Set fields in Remediation Guidance playbook
* Update release notes
* Update field descriptions
* Format JSON files
* update unsearchable and fromVersion
* Add ASM layout and rule
* Add release notes
* Update pack ReadMe
* Update server content items
* Add marketplace to layout
* Update release notes version
* Add AlertType to server content items
* Add IncidentType to server content items
* update ASM.json layout
* remove ASM from server_content_items.json
---------
Co-authored-by: John <40349459+BigEasyJ@users.noreply.github.com>
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
Co-authored-by: adi88d
* Feed Recorded Future download all compressed data on disk bug (#30981)
* Hint for solution
* Potential solution
* Tried solution, did not work
* Added potential solution
* Added RNs and updated docker image
* Added debug logs
* Resolved conflicts
* Added handling of cut-off bytes while streaming
* Added unit tests and test data
* Outsourced decoder
* Went over CR comments
* Fixed Chunk Size
* Added description to fixture
* Ran pre-commit
* Refactored decoding mechanism
* Fix chunk size
* Update FeedRecordedFuture.yml
* Update 1_0_32.md
* CISCO SMA u200b Update (#31349)
* Updated ModelingRules
* Updated ReleaseNotes
* Updated ReleaseNotes
* Updated ModelingRules logic
* [e2e xsoar-saas] - fix issue with taxii2-server test (#31362)
* Update Docker Image To demisto/crypto (#31368)
* Updated Metadata Of Pack MicrosoftDefenderAdvancedThreatProtection
* Added release notes to pack MicrosoftDefenderAdvancedThreatProtection
* Packs/MicrosoftDefenderAdvancedThreatProtection/Integrations/MicrosoftDefenderAdvancedThreatProtection/MicrosoftDefenderAdvancedThreatProtection.yml Docker image update
* Updated Metadata Of Pack AzureSecurityCenter
* Added release notes to pack AzureSecurityCenter
* Packs/AzureSecurityCenter/Integrations/AzureSecurityCenter_v2/AzureSecurityCenter_v2.yml Docker image update
* Update Docker Image To demisto/armorblox (#31376)
* Updated Metadata Of Pack Armorblox
* Added release notes to pack Armorblox
* Packs/Armorblox/Integrations/Armorblox/Armorblox.yml Docker image update
* Update Docker Image To demisto/pymisp2 (#31369)
* Updated Metadata Of Pack MISP
* Added release notes to pack MISP
* Packs/MISP/Integrations/MISPV3/MISPV3.yml Docker image update
* Update Docker Image To demisto/genericsql (#31370)
* Updated Metadata Of Pack GenericSQL
* Added release notes to pack GenericSQL
* Packs/GenericSQL/Integrations/GenericSQL/GenericSQL.yml Docker image update
* MS IIS Update3 (#31385)
* Updated ModelingRules
* Updated ReleaseNotes
* Updated ReleaseNotes
* Updated ModelingRules
* Updated ModelingRules
* Add a manual fatch once in 12 hours (#31123)
* fixes
* http module
* CSV
* common server
* tests
* RN
* link
* RN
* change RN
* one more
* pre commit
* update base version
* [known_words]
* removing typing
* swap the known words
* RN
* fix RN
* Bump pack from version FeedMalwareBazaar to 1.0.30.
* Bump pack from version AccentureCTI_Feed to 1.1.27.
* Bump pack from version FeedGCPWhitelist to 2.0.30.
* Bump pack from version Base to 1.32.52.
* make it better
* docs
* CR
* cr
* Fixing dirty merge #1
* fixing dirty merge #2
* fix dirty merge #3
* more
* fox dirty merge #4
* common
* poetry
* fix dirty merge #5
* fix test date
* base rn
* RN
* fix common docstring
* fix rn
* fix errors in build
* shirley
* Bump pack from version Base to 1.32.54.
* RN
* mypy
* fix common server
* ignore type error
* skip test
* fix test name
* add import
* remove the import, test is failing
* fixed function and test
* space
* conf
* add a test for a uniq time zone
* fix test
* move the import into the function
* move the import from the test as well
* replace timezone with pytz, to fit python 2
* Bump pack from version Base to 1.33.1.
* fix test comment
---------
Co-authored-by: Content Bot
* Fix gmail get mail context output (#31342)
* update context path
* added RN
* updated readme
* update docker
* added run get attachments argument
* pre commit fixes
* pre commit fixes
* cr fixes
* cr fixes
* cr fixes
* update RN
* update docker
* Updated README.md (#31347) (#31363)
* [Zscaler] Add URLs to Retaining Parent Category (#30637)
* add retaining parent url
* Update retaining_parent_category_url argument
* Add retaining-parent-category-ip to yml
* Add retaining-parent-category-ip logic
* ip argument no longer marked required
* url argument no longer marked required
* retaining_parent_category args are None by default
* Add retaining-parent-category-url to remove-url
* Add retaining-parent-category-ip to remove-ip
* UT fix; ruff updates
* Remove redundant context output
* Update release notes
* FIx Failed UTs
* Case of only one ip argument in remove commands
* pre-commit updates
* Update release notes
* Change display value to original value
* Update release notes
* UT Coverage
* Add UTs; Remove redundant debug logs
* Update release notes
* Apply suggestions from code review
Co-authored-by: Jasmine Beilin <71636766+JasBeilin@users.noreply.github.com>
* Remove "pragma no cover" from unrelated UTs
* Revert open function's default 'r' value for readability
---------
Co-authored-by: Jasmine Beilin <71636766+JasBeilin@users.noreply.github.com>
* Update Docker Image To demisto/python3 (#31371)
* Updated Metadata Of Pack QualysFIM
* Added release notes to pack QualysFIM
* Packs/QualysFIM/Integrations/QualysFIM/QualysFIM.yml Docker image update
* Updated Metadata Of Pack FortiSIEM
* Added release notes to pack FortiSIEM
* Packs/FortiSIEM/Integrations/FortiSIEMV2/FortiSIEMV2.yml Docker image update
* Updated Metadata Of Pack FreshworksFreshservice
* Added release notes to pack FreshworksFreshservice
* Packs/FreshworksFreshservice/Integrations/FreshworksFreshservice/FreshworksFreshservice.yml Docker image update
* Updated Metadata Of Pack KnowBe4_KMSAT
* Added release notes to pack KnowBe4_KMSAT
* Packs/KnowBe4_KMSAT/Integrations/KnowBe4KMSATEventCollector/KnowBe4KMSATEventCollector.yml Docker image update
* Packs/KnowBe4_KMSAT/Integrations/KnowBe4KMSAT/KnowBe4KMSAT.yml Docker image update
* Updated Metadata Of Pack SafeNet_Trusted_Access
* Added release notes to pack SafeNet_Trusted_Access
* Packs/SafeNet_Trusted_Access/Integrations/SafeNetTrustedAccessEventCollector/SafeNetTrustedAccessEventCollector.yml Docker image update
* Updated Metadata Of Pack DelineaSS
* Added release notes to pack DelineaSS
* Packs/DelineaSS/Integrations/DelineaSS/DelineaSS.yml Docker image update
* Updated Metadata Of Pack Cryptocurrency
* Added release notes to pack Cryptocurrency
* Packs/Cryptocurrency/Integrations/Cryptocurrency/Cryptocurrency.yml Docker image update
* Updated Metadata Of Pack PANOSPolicyOptimizer
* Added release notes to pack PANOSPolicyOptimizer
* Packs/PANOSPolicyOptimizer/Integrations/PANOSPolicyOptimizer/PANOSPolicyOptimizer.yml Docker image update
* Updated Metadata Of Pack DeveloperTools
* Added release notes to pack DeveloperTools
* Packs/DeveloperTools/Integrations/CreateIncidents/CreateIncidents.yml Docker image update
* Updated Metadata Of Pack QualysFIM
* Updated Metadata Of Pack QualysFIM
* [Marketplace Contribution] MicrosoftGraphTeams - Content Pack Update (#31097) (#31387)
* "contribution update to pack "MicrosoftGraphTeams""
* Update MicrosoftGraphTeams.py
uncomment 'topic' to allow subject for group type chat.
* Update MicrosoftGraphTeams.yml
fixed validation error for descriptions.
* Update Packs/MicrosoftGraphTeams/Integrations/MicrosoftGraphTeams/MicrosoftGraphTeams.py
done
* cr
* Update 1_1_0.md
* Update MicrosoftGraphTeams.yml
* Update 1_1_0.md
* Update 1_1_0.md
* Update MicrosoftGraphTeams.yml
---------
Co-authored-by: xsoar-bot <67315154+xsoar-bot@users.noreply.github.com>
Co-authored-by: Vipul Kaneriya <50216620+vipulkaneriya@users.noreply.github.com>
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
Co-authored-by: MLainer1
* Cybersixgill alerts typosquatting (#31386)
* Cybersixgill alerts typosquatting (#30787)
* Added mapper for 2 custom incident fields
* Updated release notes.
* Added typosquatting to known words
* new Incident fields and incomming mapper formated
* Release notes reviewed.
* setting unseachable to true.
* Suspicious and Triggered domain as tables.
* Moved 3 mappings from code to mapper.
* Updated test case
* Updated test case
* Added default mapper and updated docker image version
* Added breaking change note
* Removed breaking change note
* Renamed files as per suggestion
* renamed mapper as per suggestion
* Added new release note.
* Changed id and name for incident fields and updated docker image name
* update RN
* update RN, update fields names, update mapper
* update id, update RN
* Update 1_2_10.md
* Update incidentfield-Cybersixgill_Triggered_Domain.json
* update docker
* ID value contained invalid caps character.
* changing type in fields to tagselect
---------
Co-authored-by: Sapir Shuker <49246861+sapirshuker@users.noreply.github.com>
Co-authored-by: sapirshuker
* docker image update
---------
Co-authored-by: syed-loginsoft <97145640+syed-loginsoft@users.noreply.github.com>
Co-authored-by: Sapir Shuker <49246861+sapirshuker@users.noreply.github.com>
Co-authored-by: sapirshuker
* Armis event collector extend alerts data set (#31378)
* full working alert fetch flow.
* Unify try catch
Different RN phrasing
* Adding unittest to test Alert event flow
* bump docker version.
* Adding doc string and log writes.
* fixed - add-test-xdr-env-ng-nightly (#31155)
* fixed
* added nightly flow_type for NG
* added xsoar_ng_server_ga to CONTENT_NIGHTLY_JOBS for jobs-done-check-nightly
* added xsoar_ng_server_ga to CONTENT_NIGHTLY_JOBS for jobs-done-check-nightly
* [EWS v2] Update docker image with previous exchangelib version (#31357)
* Use "alert" instead of "incident" for XSIAM content (#31223)
* DBotFindSimilarIncidents complete
* FindSimilarIncidents complete
* minor adjustments
* fixed unit-tests
* build wars: round 1
* update docker
* added RN
* fix unit-tests
* CR changes
* Bump pack from version Base to 1.32.53.
* use get() on demistoVersion()
* Bump pack from version Base to 1.32.54.
* update docker
* update docker
* build wars: round 2
* Bump pack from version CommonScripts to 1.12.56.
* Bump pack from version Base to 1.33.1.
* Bump pack from version Base to 1.33.2.
* update docker
---------
Co-authored-by: Content Bot
* [ExtractEmailTransformer] Convert to JS (#31159)
* [transformers] Enhance to be more durable
* Add RN
* Add RN; run format
* Bump pack from version CommonScripts to 1.12.43.
* IsEmailAddressInternal set isArray to true
* Add TPB for SetAndHandleEmpty
* Add TPB for IsEmailAddressInternal
* Bump pack from version CommonScripts to 1.12.44.
* Add TPB for ExtractEmailTransformer
* Update the TPB for SetIfEmpty
* Update the TPB for SetIfEmpty
* Compatibility with XSOAR 6.9.0
* Update Packs/FiltersAndTransformers/Scripts/WhereFieldEquals/WhereFieldEquals.js
* Delete pytest files
* Bump pack from version CommonScripts to 1.12.46.
* Bump pack from version CommonScripts to 1.12.47.
* Bump pack from version CommonScripts to 1.12.48.
* Bump pack from version CommonScripts to 1.12.49.
* Bump pack from version CommonScripts to 1.12.50.
* First commit
* Added RN
* empty
* Test to update emailRegex
* Test to update emailRegex 1
* fix version
* fix RN
* Bump pack from version Base to 1.32.52.
* Fix the regex
* Add two versions: py and JS
* Bump pack from version Base to 1.32.53.
* Split by versions
* Split by versions
* Add ignore from BA109
* Fix the regex
* Bump pack from version Base to 1.32.54.
* Revert
* Revert
* Change the files name
* Update the TPB
* Fix the unit test
* Update the README file
* Add ignore; Update the docker image; Add RN
* Update the docker image
* Fix the conf.json
* Add "pragma: no cover" to main
* Update the TPB
---------
Co-authored-by: Content Bot
* Fix for playbooks that uses deprecated sub-playbooks (#31330)
* The sub-playbook of wildfire detonate file was changed to v2
* Replaced the old version of Cortex XDR - Retrieve File with the new version
* Crowdstrike detonate file was changed to a new version
* release notes update
* release notes update
* readme files updated
* release note
* fix for taskid and task field
* fixes for taskid and task not equal value
* release notes fix
* added new images for the playbooks
* Unique value fix
* RN updated
* fixes for PR
* RN fix
* fix
* fix
* RN fix
* Update Packs/CommonPlaybooks/ReleaseNotes/2_4_39.md
Co-authored-by: Sasha Sokolovich <88268646+ssokolovich@users.noreply.github.com>
* PN fix and unique fix
* fix for error in the build
* Update Packs/CommonPlaybooks/Playbooks/playbook-Detonate_URL_-_Generic_v1.5.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/Playbooks/playbook-Detonate_URL_-_Generic_v1.5.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/Playbooks/playbook-Detonate_URL_-_Generic_v1.5.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/Playbooks/playbook-Detonate_URL_-_Generic_v1.5.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/Playbooks/playbook-Detonate_URL_-_Generic_v1.5.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/Core/Playbooks/playbook-Ransomware_Enrich_and_Contain_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/Core/Playbooks/playbook-Ransomware_Enrich_and_Contain_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/Core/Playbooks/playbook-Ransomware_Enrich_and_Contain_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/Core/ReleaseNotes/3_0_3.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CortexXDR/ReleaseNotes/6_0_8.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/Playbooks/playbook-Detonate_URL_-_Generic_v1.5.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/ReleaseNotes/2_4_39.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/ReleaseNotes/2_4_39.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/Core/Playbooks/playbook-Ransomware_Enrich_and_Contain.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/Core/Playbooks/playbook-Ransomware_Enrich_and_Contain_README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---------
Co-authored-by: Sasha Sokolovich <88268646+ssokolovich@users.noreply.github.com>
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* added the send_data_to_xsiam func (#29709)
* added the send_data_to_xsiam func
* changes
* minor fixes
* change
* edit
* added RN
* added unittests
* added rn
* Bump pack from version Base to 1.32.47.
* fixed import
* Bump pack from version Base to 1.32.48.
* Bump pack from version Base to 1.32.49.
* fix headers names
* added rn
* updated unittest
* added to demistomock
* added rn
* fix rn
* edit
* Bump pack from version Base to 1.32.54.
* Bump pack from version Base to 1.33.1.
* added rn
* edits after cr
* edit
* edit
* Bump pack from version Base to 1.33.3.
* edits for cover analysis
---------
Co-authored-by: Content Bot
* EXPANDR-7181 Fix issues for AWS rule logic (#31401)
* EXPANDR-7181 Fix issues for AWS rule logic (#31237)
* Fix issues
* update release notes
* updated docker image
* Update Packs/AWS-Enrichment-Remediation/ReleaseNotes/1_1_9.md
Co-authored-by: John <40349459+BigEasyJ@users.noreply.github.com>
* scenario 4 and 5 changes
* update test cases
* Update Packs/AWS-Enrichment-Remediation/ReleaseNotes/1_1_9.md
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
---------
Co-authored-by: John <40349459+BigEasyJ@users.noreply.github.com>
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* Update 1_1_9.md
* Update 1_1_9.md
* Update docker
---------
Co-authored-by: Chait A <112722030+capanw@users.noreply.github.com>
Co-authored-by: John <40349459+BigEasyJ@users.noreply.github.com>
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* RSA secureID CIAC-8811 (#31392)
* New pack of RSA secureID
* Update Packs/RSASecureID/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/RSASecureID/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/RSASecureID/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/RSASecureID/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* changes to the README file
* small changes to the README
* mismatch betweeb dataset names
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update "malware investigation and response" and cortex xdr image path (#31403)
* updated path to image
* Updated the pic for cortex xdr
* [Qradar] - add timeout param, update test-module and implement retry for connection errors (#31339)
* add qradar timeout param
* add timeout to client
* add docs and bump rn
* fixes
* refactor test-module
* retry for http_request
* fixes
* elif
* rn and docker image
* rn
* bump rn
* update docker
* logger
* add fetch-interval and set default to 10
* README.md
* readme and udpates
* rn
* arg to number
* update docker-image
* ut
* fix uts
* [AWS Athena] Move From Beta to GA (#30694)
* Remove beta marks
* Structural improvements
* Validation fixes
* Update code
* Add release notes
* Update `defaultRegion` param
* Fixes
* Update context output for the `aws-athena-get-query-results` command
* Update output context keys
* Minor fixes
* Add `query_execution_id` field to results
* Fix `aws-athena-get-query-execution`'s context output
* Update AWS regions
* Minor improvements & add unit-tests
* Format YAML & bump Docker version
* Update release notes with BC message
* Context fixes
* Delete test-playbook
* Disable test-playbook
* Release notes improvements
* Fix test-module
* Change version bump to major
* Add safe code to `parse_rows_response`
* Update unit-test following previous context fix
* Fix tests key on YAML
* Fixes & improvements
* Revert breaking changes
* Update context output to `Query`
* Fix required param
* Fixes
* Add polling support for `aws-athena-get-query-results`
* Bump Docker
* Add missing polling parameters
* Add a `QueryLimit` parameter to the `aws-athena-start-query` command
* Add output fields to `aws-athena-get-query-execution`
* Move polling functionality to `aws-athena-get-query-execution`
* Change output of `aws-athena-start-query` to match `aws-athena-get-query-execution`
* Fix validation errors
* Address core-review requested changes
* Fix polling condition
* Remove polling from `aws-athena-get-query-execution` command
* Add new `aws-athena-execute-query` polling command
* Bump Docker version
* Minor fixes
* Update README
* Update unit-tests
* Bump Docker version
* Update `aws-athena-execute-query` command description
* Add `aws-athena-execute-query` command to release notes
* Code review fixes
* Update Docker version
* Fix output of `aws-athena-start-query` to `Query.Query` key instead of `Query.QueryString`
* Fix unit-test
* Malware Investigation and Response - Added specification for integration brand for the !endpoint command. (#31399)
* Specify dedicated integration brand for !endpoint command
* RN
* Update Docker Image To demisto/tesseract (#31410)
* Updated Metadata Of Pack ImageOCR
* Added release notes to pack ImageOCR
* Packs/ImageOCR/Integrations/ImageOCR/ImageOCR.yml Docker image update
* Fix js get incident tasks by state (#31414)
* fixed js indexof
* Added rn
* [Marketplace Contribution] IP2LocationIO (#31302) (#31406)
* "pack contribution initial commit"
* Update IP2LocationIO.py
* Update pack_metadata.json
* Update IP2LocationIO.py
* Update .secrets-ignore
* Update .secrets-ignore
* Update IP2LocationIO.py
* Update IP2LocationIO.py
* Update IP2LocationIO.yml
* Update Packs/IP2LocationIO/Integrations/IP2LocationIO/IP2LocationIO.py
---------
Co-authored-by: xsoar-bot <67315154+xsoar-bot@users.noreply.github.com>
Co-authored-by: IP2Location
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
* Bugfix/XSUP-30713/add-InternalIPRanges-as-playbook-input (#31329)
* Pass InternalIPRanges as input for alert handling subplaybook
* Add InternalIPRanges playbook input
* Remove unwanted change
* Fix validation error
* Update release notes
* Fix alert handling subplaybook to use InternalIPRanges from inputs
* Fix release notes based on review comments
* Bump pack from version CortexXDR to 6.0.9.
---------
Co-authored-by: Content Bot
* CRTX-96742: Release a new base pack (#31420)
* Azure sentinel assignement options (#31419)
* Azure sentinel assignement options (#31065)
* Azure sentinel updates for assginment (#1)
* added support to unassign incidents and assignment based on AssigneeObjectID
* updated docker images and release notes
* updated containers and sdk format
* Update Packs/AzureSentinel/Integrations/AzureSentinel/AzureSentinel.py
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
* Update Packs/AzureSentinel/Integrations/AzureSentinel/AzureSentinel.yml
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
* Update TestAzureSentinelPlaybookV2.yml
revert demisto sdk format changes
* Update playbook-TestAzureSentinelPlaybook.yml
revert demisto-sdk format changes
* undo json changes
* undo demisto-sdk json changes
* new version
* resolve conflict
* resolve conflict
* resolve conflict
* revert changes
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Apply suggestions from code review
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Docker Image
---------
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
Co-authored-by: MLainer1
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* DI
---------
Co-authored-by: asieberle <121243004+asieberle@users.noreply.github.com>
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
Co-authored-by: MLainer1
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* SetGridField fixes (#31318)
* SetGridField fixes
* update docker
* add support for incident_id
* do only needed change
* revert yml
* docker image
* revert ruff changes
* revert ruff changes
* fixes
* fixes
* fixes
* RN conflicts
* Update SetGridField.py
* add tests
* fix test
* add tests
* Update SetGridField_test.py
* fixes CR
* fix CR review,update docker
* Bump pack from version CommonScripts to 1.12.57.
* fix CR review
* fix CR review
---------
Co-authored-by: Content Bot
* O365 security and compliance - search action - handle no results better (#31062)
* added xsoar-saas_test_e2e_results (#31417)
* Update Docker Image To demisto/auth-utils (#31431)
* Updated Metadata Of Pack Troubleshoot
* Added release notes to pack Troubleshoot
* Packs/Troubleshoot/Scripts/CertificatesTroubleshoot/CertificatesTroubleshoot.yml Docker image update
* Update Docker Image To demisto/python3 (#31427)
* Updated Metadata Of Pack GCP-Enrichment-Remediation
* Added release notes to pack GCP-Enrichment-Remediation
* Packs/GCP-Enrichment-Remediation/Scripts/GCPProjectHierarchy/GCPProjectHierarchy.yml Docker image update
* Updated Metadata Of Pack PaloAltoNetworks_Threat_Vault
* Added release notes to pack PaloAltoNetworks_Threat_Vault
* Packs/PaloAltoNetworks_Threat_Vault/Scripts/SetThreatVaultIncidentMarkdownRepresentation/SetThreatVaultIncidentMarkdownRepresentation.yml Docker image update
* Updated Metadata Of Pack Cryptocurrency
* Added release notes to pack Cryptocurrency
* Packs/Cryptocurrency/Scripts/CryptoCurrenciesFormat/CryptoCurrenciesFormat.yml Docker image update
* Updated Metadata Of Pack DeveloperTools
* Added release notes to pack DeveloperTools
* Packs/DeveloperTools/Scripts/WaitAndCompleteTask/WaitAndCompleteTask.yml Docker image update
* Updated Metadata Of Pack Carbon_Black_Enterprise_Response
* Added release notes to pack Carbon_Black_Enterprise_Response
* Packs/Carbon_Black_Enterprise_Response/Scripts/CBWatchlists/CBWatchlists.yml Docker image update
* Packs/Carbon_Black_Enterprise_Response/Scripts/CBAlerts/CBAlerts.yml Docker image update
* Updated Metadata Of Pack Lokpath_Keylight
* Added release notes to pack Lokpath_Keylight
* Packs/Lokpath_Keylight/Scripts/KeylightCreateIssue/KeylightCreateIssue.yml Docker image update
* Updated Metadata Of Pack XMatters
* Added release notes to pack XMatters
* Packs/XMatters/Scripts/WaitForKey/WaitForKey.yml Docker image update
* Packs/XMatters/Scripts/CloseTaskSetContext/CloseTaskSetContext.yml Docker image update
* Updated Metadata Of Pack AccentureCTI
* Added release notes to pack AccentureCTI
* Packs/AccentureCTI/Scripts/FormatACTIURL/FormatACTIURL.yml Docker image update
* Updated Metadata Of Pack SymantecEndpointProtection
* Added release notes to pack SymantecEndpointProtection
* Packs/SymantecEndpointProtection/Scripts/SEPCheckOutdatedEndpoints/SEPCheckOutdatedEndpoints.yml Docker image update
* Updated Metadata Of Pack Forcepoint
* Added release notes to pack Forcepoint
* Packs/Forcepoint/Scripts/FPDeleteRule/FPDeleteRule.yml Docker image update
* Packs/Forcepoint/Scripts/FPSetRule/FPSetRule.yml Docker image update
* Updated Metadata Of Pack AzureSentinel
* Added release notes to pack AzureSentinel
* Packs/AzureSentinel/Scripts/MicrosoftSentinelConvertAlertsToTable/MicrosoftSentinelConvertAlertsToTable.yml Docker image update
* Packs/AzureSentinel/Scripts/MicrosoftSentinelConvertRelationsToTable/MicrosoftSentinelConvertRelationsToTable.yml Docker image update
* Packs/AzureSentinel/Scripts/MicrosoftSentinelConvertEntitiesToTable/MicrosoftSentinelConvertEntitiesToTable.yml Docker image update
* Packs/AzureSentinel/Scripts/MicrosoftSentinelConvertCommentsToTable/MicrosoftSentinelConvertCommentsToTable.yml Docker image update
* Updated Metadata Of Pack CommonWidgets
* Added release notes to pack CommonWidgets
* Packs/CommonWidgets/Scripts/MyToDoTasksWidget/MyToDoTasksWidget.yml Docker image update
* Packs/CommonWidgets/Scripts/FeedIntegrationErrorWidget/FeedIntegrationErrorWidget.yml Docker image update
* Updated Metadata Of Pack fireeye
* Added release notes to pack fireeye
* Packs/fireeye/Scripts/FireEyeDetonateFile/FireEyeDetonateFile.yml Docker image update
* Updated Metadata Of Pack Campaign
* Added release notes to pack Campaign
* Packs/Campaign/Scripts/SetPhishingCampaignDetails/SetPhishingCampaignDetails.yml Docker image update
* Packs/Campaign/Scripts/GetCampaignDuration/GetCampaignDuration.yml Docker image update
* Packs/Campaign/Scripts/GetCampaignIncidentsInfo/GetCampaignIncidentsInfo.yml Docker image update
* Packs/Campaign/Scripts/ShowCampaignHighestSeverity/ShowCampaignHighestSeverity.yml Docker image update
* Packs/Campaign/Scripts/ShowCampaignSimilarityRange/ShowCampaignSimilarityRange.yml Docker image update
* Packs/Campaign/Scripts/GetCampaignLowSimilarityIncidentsInfo/GetCampaignLowSimilarityIncidentsInfo.yml Docker image update
* Packs/Campaign/Scripts/IsIncidentPartOfCampaign/IsIncidentPartOfCampaign.yml Docker image update
* Packs/Campaign/Scripts/GetCampaignIncidentsIdsAsOptions/GetCampaignIncidentsIdsAsOptions.yml Docker image update
* Packs/Campaign/Scripts/ShowCampaignIncidentsOwners/ShowCampaignIncidentsOwners.yml Docker image update
* Packs/Campaign/Scripts/CollectCampaignRecipients/CollectCampaignRecipients.yml Docker image update
* Packs/Campaign/Scripts/ShowCampaignSenders/ShowCampaignSenders.yml Docker image update
* Packs/Campaign/Scripts/ShowCampaignRecipients/ShowCampaignRecipients.yml Docker image update
* Packs/Campaign/Scripts/GetCampaignLowerSimilarityIncidentsIdsAsOptions/GetCampaignLowerSimilarityIncidentsIdsAsOptions.yml Docker image update
* Packs/Campaign/Scripts/ShowCampaignLastIncidentOccurred/ShowCampaignLastIncidentOccurred.yml Docker image update
* Packs/Campaign/Scripts/SendEmailToCampaignRecipients/SendEmailToCampaignRecipients.yml Docker image update
* Packs/Campaign/Scripts/PerformActionOnCampaignIncidents/PerformActionOnCampaignIncidents.yml Docker image update
* Updated Metadata Of Pack RiskIQDigitalFootprint
* Added release notes to pack RiskIQDigitalFootprint
* Packs/RiskIQDigitalFootprint/Scripts/RiskIQDigitalFootprintAssetDetailsWidgetScript/RiskIQDigitalFootprintAssetDetailsWidgetScript.yml Docker image update
* Updated Metadata Of Pack DomainToolsIrisDetect
* Added release notes to pack DomainToolsIrisDetect
* Packs/DomainToolsIrisDetect/Scripts/DomainToolsIrisDetectStatusUpdate/DomainToolsIrisDetectStatusUpdate.yml Docker image update
* Updated Metadata Of Pack X509Certificate
* Added release notes to pack X509Certificate
* Packs/X509Certificate/Scripts/CertificateReputation/CertificateReputation.yml Docker image update
* Updated Metadata Of Pack CarbonBlackProtect
* Added release notes to pack CarbonBlackProtect
* Packs/CarbonBlackProtect/Scripts/CBPFindComputer/CBPFindComputer.yml Docker image update
* commit
---------
Co-authored-by: israelpolishook
* Fix "unexpected keyword argument" Error (#31418)
* fixed bug
* RN
* ignore pylance error
* update docker
* New script: ReadQRCode (#31323)
* init
* json.loads on the results of extractIndicators
* fix unit-tests
* added docs to unit-tests
* fix unit-tests
* moved script to commonScripts
* capitalize output key 'text'
* no error for non QR code images
* add RN
* fix unit-tests
* demo changes
* added docs
* Update Packs/CommonScripts/Scripts/ReadQRCode/README.md
Co-authored-by: Judah Schwartz
* CR changes
* RN
* remove trailing whitespace
* build wars: round 1
* fixed 'unexpected argument' bug
* unit-tests complete
* Bump pack from version CommonScripts to 1.13.0.
---------
Co-authored-by: Judah Schwartz
Co-authored-by: Content Bot
* Trend micro vision one (#31361)
* Trend micro vision one (#30157)
* removed microsocks
Potentially harmful
* imported urllib3 and removed reference to requests.packages. Updated release notes and TrendMicroVisionOne.yml
* added action to add file entry from incident to sandbox and action to get result of file entry analysis status
* removed redundant action to check sandbox submission status
* added polling command for sandbox submissions
* added unit tests for file entry to sandbox and polling for sandbox submissions
* added unit tests for submit file entry and sandbox polling command
* updated yml to include submit-file-entry-to-sandbox and run-sandbox-submission-polling
* Update README.md
Added hints for command execution order
* Update README.md
Updated Notes for better readability.
* Update README.md
Updated README.md for better readability.
* updated release notes to indicate addition of submit file entry to sandbox and sandbox submission polling command
* formatted files per XSOAR standards
* Added command examples for V2 actions
* added test_data folder containing example responses
* Update README.md
Added link to supported file types in submit file to sandbox and submit file entry to sandbox.
* removed unused mock test case for submit file entry to sandbox and test_data folder with mock responses
* Added submit file entry to sandbox and run sandbox submission polling and their respective unit tests and command_examples
* added demosti.patch.object to get custom data for demisto.getFilePath in submit file entry to sandbox
* updated polling comamnd per XSOAR standards and updated YAML to include polling in sandbox submissing polling command root
* TrendMicroVisionOne_description
* updated sandbox submission command example to include polling arg
* updated yml to include polling in root of sandbox submission polling
* removed unused variable declarations
* updated doc string for sandbox submission polling
* updated min server version to 6.2.0 in sandbox polling unit test
* updated if check to differentiate between cmd instead of args
* added dbotscore for sandbox submissions status and sandbox polling commands
* added doc string for dbot severity helper function
* Updated Vendor Name to match integration pack
* updated risk to look for obj instead of str and updated release notes and updated docker image version
* added dbotscore to VisionOne context data and updated YML and README.md accordingly
* small context output fix
* Update 1_3_0.md
* updated description in YML for V3.
* added pagination for suspicious/exception list as well as endpoint info and fetch incidents
* updated unit test for endpoint info
* updated README.md to reflect name change for 3 context outputs in get endpoint info
* reverted change for get endpoint info to ensure backwards compatibility
* updated docker python image in release notes
* Update docker image.
* Update RN.
* Remove main function from unit test coverage.
* corrected delete from suspicious list endpoint
* updated docker image to latest per circleci test
* fixed precommit error of implicitly concatenated string in regex for macaddress validation
* fixed precommit error of implicitly concatenated string in regex for ipv6 validation
* updated Release Notes
* Add pytmv1 devdemisto image for testing
* updated all actions to use pytmv1 library
* added 2 new actions (get alert details and submit urls to sandbox)
* updated to declare pytmv1 directly in actions instead of passing in action calls
* removed commented code for pytmv1 initialization.
* updated actions using pytmv1 library
* added variable names for replace args and updated isolate and restore endpoint table vars
* updated yml for all actions and added return_error condition for all actions
* removed unused message vars
* updated unit tests and added test_data folder with mock responses.
* updated check_task_status unit test with correct params
* updated base url for unit tests
* updated var declarations to compatible union type
* ran format command to format yml file
* updated release notes
* validated yml file
* added missing default value for polling
* removed commented code and wrapped digest values
* added endpoint and email activity data actions and their fetch count helper functions respectively.
* added unit tests for endpoint and email activity data
* updated yml to include context outputs for endpoint and email activity data, added respective command examples and updated README.md
* updated get_activity_data_count param for respective actions
* updated README.md
* added severity filter to fetch incidents
* added dbotMirrorId and details to incident, added 'any' option for incident severity types and updated yml file for incidentSeverity.
* added any string literal with var
* updated README.md to indicate addition of 2 new actions.
* updated docstrings and added comments
* added comments for workbench histories and updated status check to include task class type to fetch the final task response.
* removed unused vars
* formatted and validated yml and README.md
* updated yml for exception and suspicious list actions to correct the context outputs and updated README.md to match
* updated docker image to match demsito-docker image and updated relase notes per demisto XSOAR standards.
* added tmv1 url and various IPs to secrets-ignore.
* updated return type for get_task_type
* updated test connectivity and updated self.app reference to APP_NAME variable.
* updated yml and generated new README.md
* updated file path default value
* updated command_examples and updated args to reference collect_files variable in collect_file action
* updated yml and generated new readme, also ran command to update release notes with -bc flag
* fixed submit file to sandbox unit test
* Update docker image in TrendMicroVisionOneV3.yml
* added breaking changes details to ReleaseNotes->4_0_0.json
* Update 4_0_0.md
* corrected breaking changes json file
* enabled network for docker unit tests and added type:ignore for poll_time_sec
* updated docker image tag to 0.6.2.79742
* updated context output for sandbox submission polling to remove report_id duplicate and replace with type.
* updated 32 unit tests and added email and endpoint activity actions
* corrected submit_file_to_sandbox unit test
* updated yml and README.md
* removed commented out code for test get endpoint information
* updated endpoint and email activity data count command names and updated yml and README
* added missing white space for table heading
* fixed import for endpoint and email activity data
* updated secretes-ignore list
* updated unit test for get_endpoint_info and update dockerimage to newest.
* removed top var from endpoint and email activity data count actions and updated yml and README.md accordingly.
* fixed docker image tag in release notes
* corrected remaining Ruff errors
* added if check for str to use json loads and added input examples. Added isArray for context inputs and also updated README.md accordingly.
* Added query op detailed description and examples.
* replaced str if check and replaced with in-built safe_load_json method.
* updated docker image to latest
* Update 4_0_0.md
* fixed fetch incident bug where duplicates were fetched because end date was not being set correctly.
---------
Co-authored-by: yaakovpraisler
Co-authored-by: Yaakov Praisler <59408745+yaakovpraisler@users.noreply.github.com>
Co-authored-by: Danny_Fried
Co-authored-by: Kobbi Gal <85439776+kgal-pan@users.noreply.github.com>
Co-authored-by: Israel Lappe <79846863+ilappe@users.noreply.github.com>
* remove pass
* update docker
---------
Co-authored-by: shaqnawe
Co-authored-by: yaakovpraisler
Co-authored-by: Yaakov Praisler <59408745+yaakovpraisler@users.noreply.github.com>
Co-authored-by: Danny_Fried
Co-authored-by: Kobbi Gal <85439776+kgal-pan@users.noreply.github.com>
Co-authored-by: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Co-authored-by: ilappe
* Fix MDE settings description (#31398)
* updated script description
* RN
* updated rn
* updated rn
* updated rn
* Bump pack from version MicrosoftDefenderAdvancedThreatProtection to 1.16.21.
---------
Co-authored-by: Content Bot
* Update Docker Image To demisto/netutils (#31428)
* Updated Metadata Of Pack DeveloperTools
* Added release notes to pack DeveloperTools
* Packs/DeveloperTools/Scripts/CompareIndicators/CompareIndicators.yml Docker image update
* Updated Metadata Of Pack FiltersAndTransformers
* Added release notes to pack FiltersAndTransformers
* Packs/FiltersAndTransformers/Scripts/IPv4Blacklist/IPv4Blacklist.yml Docker image update
* Packs/FiltersAndTransformers/Scripts/IsRFC1918Address/IsRFC1918Address.yml Docker image update
* Packs/FiltersAndTransformers/Scripts/IPv4Whitelist/IPv4Whitelist.yml Docker image update
* Packs/FiltersAndTransformers/Scripts/IsNotInCidrRanges/IsNotInCidrRanges.yml Docker image update
* Bump pack from version FiltersAndTransformers to 1.2.46.
* Add RN and update pack_metadata file
* add README for IsNotInCidrRanges script
---------
Co-authored-by: Content Bot
Co-authored-by: israelpolishook
* Armis fix url suffix (#31434)
* Armis add suffix to base url
* RN
* Add UT
* doc review
* docker
* Update Docker Image To demisto/python3 (#31439)
* Updated Metadata Of Pack Active_Directory_Query
* Added release notes to pack Active_Directory_Query
* Packs/Active_Directory_Query/Scripts/SendEmailToManager/SendEmailToManager.yml Docker image update
* Updated Metadata Of Pack ServiceNow
* Added release notes to pack ServiceNow
* Packs/ServiceNow/Scripts/ServiceNowUpdateIncident/ServiceNowUpdateIncident.yml Docker image update
* Packs/ServiceNow/Scripts/ServiceNowQueryIncident/ServiceNowQueryIncident.yml Docker image update
* Packs/ServiceNow/Scripts/ServiceNowCreateIncident/ServiceNowCreateIncident.yml Docker image update
* Packs/ServiceNow/Scripts/ServiceNowAddComment/ServiceNowAddComment.yml Docker image update
* Fix DS108
---------
Co-authored-by: israelpolishook
* Feed Elastic: fetch in batches (#31377)
* Update Docker Image To demisto/ssdeep (#31446)
* Updated Metadata Of Pack CommonScripts
* Added release notes to pack CommonScripts
* Packs/CommonScripts/Scripts/SSDeepSimilarity/SSDeepSimilarity.yml Docker image update
* Update Docker Image To demisto/taxii (#31459)
* Updated Metadata Of Pack Base
* Added release notes to pack Base
* Packs/Base/Scripts/StixParser/StixParser.yml Docker image update
* Add argument include_resolved_param to sentinelone-get-threats (#31433)
* Add argument include_resolved_param to sentinelone-get-threats (#31355)
* Add argument include_resolved_param to sentinelone-get-threats
* fix: update pack metadatafile version
* Update docker
* Update 3_2_14.md
* Update Packs/SentinelOne/ReleaseNotes/3_2_14.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---------
Co-authored-by: chloerongier <150173582+chloerongier@users.noreply.github.com>
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Docker Image To demisto/office-utils (#31451)
* Updated Metadata Of Pack CommonScripts
* Added release notes to pack CommonScripts
* Packs/CommonScripts/Scripts/ConvertFile/ConvertFile.yml Docker image update
* Bump pack from version CommonScripts to 1.13.2.
---------
Co-authored-by: Content Bot
* Update Docker Image To demisto/python3 (#31442)
* Updated Metadata Of Pack CommonScripts
* Added release notes to pack CommonScripts
* Packs/CommonScripts/Scripts/ScheduleGenericPolling/ScheduleGenericPolling.yml Docker image update
* Packs/CommonScripts/Scripts/ChangeContext/ChangeContext.yml Docker image update
* Packs/CommonScripts/Scripts/MarkAsNoteByTag/MarkAsNoteByTag.yml Docker image update
* Packs/CommonScripts/Scripts/ExportIncidentsToCSV/ExportIncidentsToCSV.yml Docker image update
* Packs/CommonScripts/Scripts/EmailReputation/EmailReputation.yml Docker image update
* Packs/CommonScripts/Scripts/OnionURLReputation/OnionURLReputation.yml Docker image update
* Packs/CommonScripts/Scripts/FileCreateAndUploadV2/FileCreateAndUploadV2.yml Docker image update
* Packs/CommonScripts/Scripts/GetServerURL/GetServerURL.yml Docker image update
* Packs/CommonScripts/Scripts/ShowLocationOnMap/ShowLocationOnMap.yml Docker image update
* Packs/CommonScripts/Scripts/ExportIndicatorsToCSV/ExportIndicatorsToCSV.yml Docker image update
* Packs/CommonScripts/Scripts/CheckContextValue/CheckContextValue.yml Docker image update
* Packs/CommonScripts/Scripts/GetEnabledInstances/GetEnabledInstances.yml Docker image update
* Packs/CommonScripts/Scripts/FileReputation/FileReputation.yml Docker image update
* Packs/CommonScripts/Scripts/ConvertCountryCodeCountryName/ConvertCountryCodeCountryName.yml Docker image update
* Packs/CommonScripts/Scripts/IsUrlPartOfDomain/IsUrlPartOfDomain.yml Docker image update
* Packs/CommonScripts/Scripts/ServerLogs/ServerLogs.yml Docker image update
* Packs/CommonScripts/Scripts/PrintRaw/PrintRaw.yml Docker image update
* Packs/CommonScripts/Scripts/DisplayHTMLWithImages/DisplayHTMLWithImages.yml Docker image update
* Packs/CommonScripts/Scripts/SCPPullFiles/SCPPullFiles.yml Docker image update
* Packs/CommonScripts/Scripts/StopTimeToAssignOnOwnerChange/StopTimeToAssignOnOwnerChange.yml Docker image update
* Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/CreateIndicatorsFromSTIX.yml Docker image update
* Packs/CommonScripts/Scripts/ShowIncidentIndicators/ShowIncidentIndicators.yml Docker image update
* Packs/CommonScripts/Scripts/GetDataCollectionLink/GetDataCollectionLink.yml Docker image update
* Packs/CommonScripts/Scripts/PrintContext/PrintContext.yml Docker image update
* Packs/CommonScripts/Scripts/ServerLogsDocker/ServerLogsDocker.yml Docker image update
* Packs/CommonScripts/Scripts/GetStringsDistance/GetStringsDistance.yml Docker image update
* Packs/CommonScripts/Scripts/GetDockerImageLatestTag/GetDockerImageLatestTag.yml Docker image update
* Packs/CommonScripts/Scripts/GetIndicatorDBotScore/GetIndicatorDBotScore.yml Docker image update
* Packs/CommonScripts/Scripts/CreateNewIndicatorsOnly/CreateNewIndicatorsOnly.yml Docker image update
* Packs/CommonScripts/Scripts/ChangeRemediationSLAOnSevChange/ChangeRemediationSLAOnSevChange.yml Docker image update
* Packs/CommonScripts/Scripts/DBotAverageScore/DBotAverageScore.yml Docker image update
* Packs/CommonScripts/Scripts/PrintErrorEntry/PrintErrorEntry.yml Docker image update
* Packs/CommonScripts/Scripts/ExtractIndicatorsFromTextFile/ExtractIndicatorsFromTextFile.yml Docker image update
* Packs/CommonScripts/Scripts/UtilAnyResults/UtilAnyResults.yml Docker image update
* Packs/CommonScripts/Scripts/ZipStringsArrays/ZipStringsArrays.yml Docker image update
* Packs/CommonScripts/Scripts/GridFieldSetup/GridFieldSetup.yml Docker image update
* Packs/CommonScripts/Scripts/GetByIncidentId/GetByIncidentId.yml Docker image update
* Packs/CommonScripts/Scripts/ProvidesCommand/ProvidesCommand.yml Docker image update
* Packs/CommonScripts/Scripts/ReplaceMatchGroup/ReplaceMatchGroup.yml Docker image update
* Packs/CommonScripts/Scripts/VerifyCIDR/VerifyCIDR.yml Docker image update
* Packs/CommonScripts/Scripts/AppendindicatorFieldWrapper/AppendindicatorFieldWrapper.yml Docker image update
* Packs/CommonScripts/Scripts/URLNumberOfAds/URLNumberOfAds.yml Docker image update
* Packs/CommonScripts/Scripts/FileToBase64List/FileToBase64List.yml Docker image update
* Packs/CommonScripts/Scripts/GetFieldsByIncidentType/GetFieldsByIncidentType.yml Docker image update
* Packs/CommonScripts/Scripts/LoadJSON/LoadJSON.yml Docker image update
* Packs/CommonScripts/Scripts/URLReputation/URLReputation.yml Docker image update
* Packs/CommonScripts/Scripts/IncidentFields/IncidentFields.yml Docker image update
* Packs/CommonScripts/Scripts/HideFieldsOnNewIncident/HideFieldsOnNewIncident.yml Docker image update
* Packs/CommonScripts/Scripts/IPReputation/IPReputation.yml Docker image update
* Packs/CommonScripts/Scripts/DeduplicateValuesbyKey/DeduplicateValuesbyKey.yml Docker image update
* fix DS108
* Bump pack from version CommonScripts to 1.13.2.
---------
Co-authored-by: israelpolishook
Co-authored-by: Content Bot
* Update Docker Image To demisto/crypto (#31471)
* Updated Metadata Of Pack AzureFirewall
* Added release notes to pack AzureFirewall
* Packs/AzureFirewall/Integrations/AzureFirewall/AzureFirewall.yml Docker image update
* Updated Metadata Of Pack MicrosoftGraphIdentityandAccess
* Added release notes to pack MicrosoftGraphIdentityandAccess
* Packs/MicrosoftGraphIdentityandAccess/Integrations/MicrosoftGraphIdentityandAccess/MicrosoftGraphIdentityandAccess.yml Docker image update
* Updated Metadata Of Pack AzureLogAnalytics
* Added release notes to pack AzureLogAnalytics
* Packs/AzureLogAnalytics/Integrations/AzureLogAnalytics/AzureLogAnalytics.yml Docker image update
* Update Docker Image To demisto/opnsense (#31473)
* Updated Metadata Of Pack OPNSense
* Added release notes to pack OPNSense
* Packs/OPNSense/Integrations/OPNSense/OPNSense.yml Docker image update
* added logs (#31229)
* added logs
* Apply suggestions from code review
* add rn
* change image
* EWS o365 eml download/incident creation inconsistencies (#31326)
* EWS o365 eml download/incident creation inconsistencies (#31146)
* Corrects incident occurred time to use datetime_received to match fetch email search parameters. Adjusts header validation in get item as eml and parse incident as item to match header keys in a case-insensitive way. Applies SMTP and SMTPUTF8 email policies when creating eml files based on the presence of non-ascii characters
* corrects tests to expect \r\n and initialize message objects with datetime_received
* corrects contenttype header check to also be lowercase
* fix line length
* updated release notes
* test for header integrity in parse_incident_from_item function
* Test for get_item_as_eml file result
* reduced line lengths
* updating some formatting
* updated to latest version of py3ews and updated release notes to include the change
* adds newline for validation
* Update 1_2_32.md
* updates to release notes based on feedback
* another edit to the release notes
* Update docker
* Update docker
* remove extra blank line
---------
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
Co-authored-by: omerKarkKatz <95565843+omerKarkKatz@users.noreply.github.com>
* remove folder-path from test pb
* Update docker
* Update 1_2_32.md
* Bump pack from version MicrosoftExchangeOnline to 1.2.33.
---------
Co-authored-by: Isaiah Eichen
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
Co-authored-by: omerKarkKatz <95565843+omerKarkKatz@users.noreply.github.com>
Co-authored-by: adi88d
Co-authored-by: Content Bot
* Update Docker Image To demisto/teams (#31448)
* Updated Metadata Of Pack CommonScripts
* Added release notes to pack CommonScripts
* Packs/CommonScripts/Scripts/GenerateAsBuilt/GenerateAsBuilt.yml Docker image update
* Bump pack from version CommonScripts to 1.13.2.
* Bump pack from version CommonScripts to 1.13.4.
---------
Co-authored-by: Content Bot
* Update Docker Image To demisto/python3 (#31470)
* Updated Metadata Of Pack SymantecCloudSecureWebGateway
* Added release notes to pack SymantecCloudSecureWebGateway
* Packs/SymantecCloudSecureWebGateway/Integrations/SymantecCloudSecureWebGatewayEventCollector/SymantecCloudSecureWebGatewayEventCollector.yml Docker image update
* Updated Metadata Of Pack Lumu
* Added release notes to pack Lumu
* Packs/Lumu/Integrations/Lumu/Lumu.yml Docker image update
* Updated Metadata Of Pack FlashpointFeed
* Added release notes to pack FlashpointFeed
* Packs/FlashpointFeed/Integrations/FlashpointFeed/FlashpointFeed.yml Docker image update
* Updated Metadata Of Pack Wiz
* Added release notes to pack Wiz
* Packs/Wiz/Integrations/Wiz/Wiz.yml Docker image update
* Updated Metadata Of Pack AbnormalSecurity
* Added release notes to pack AbnormalSecurity
* Packs/AbnormalSecurity/Integrations/AbnormalSecurity/AbnormalSecurity.yml Docker image update
* Updated Metadata Of Pack FeedLOLBAS
* Added release notes to pack FeedLOLBAS
* Packs/FeedLOLBAS/Integrations/FeedLOLBAS/FeedLOLBAS.yml Docker image update
* Updated Metadata Of Pack Hackuity
* Added release notes to pack Hackuity
* Packs/Hackuity/Integrations/Hackuity/Hackuity.yml Docker image update
* Updated Metadata Of Pack Grafana
* Added release notes to pack Grafana
* Packs/Grafana/Integrations/Grafana/Grafana.yml Docker image update
* Updated Metadata Of Pack Binalyze
* Added release notes to pack Binalyze
* Packs/Binalyze/Integrations/BinalyzeAIR/BinalyzeAIR.yml Docker image update
* Updated Metadata Of Pack ServiceDeskPlus
* Added release notes to pack ServiceDeskPlus
* Packs/ServiceDeskPlus/Integrations/ServiceDeskPlus/ServiceDeskPlus.yml Docker image update
* Updated Metadata Of Pack Oracle_IAM
* Added release notes to pack Oracle_IAM
* Packs/Oracle_IAM/Integrations/OracleIAM/OracleIAM.yml Docker image update
* Updated Metadata Of Pack VMwareWorkspaceONEUEM
* Added release notes to pack VMwareWorkspaceONEUEM
* Packs/VMwareWorkspaceONEUEM/Integrations/VMwareWorkspaceONEUEM/VMwareWorkspaceONEUEM.yml Docker image update
* Updated Metadata Of Pack SalesforceFusion
* Added release notes to pack SalesforceFusion
* Packs/SalesforceFusion/Integrations/SalesforceFusionIAM/SalesforceFusionIAM.yml Docker image update
* Updated Metadata Of Pack RecordedFuture
* Added release notes to pack RecordedFuture
* Packs/RecordedFuture/Integrations/RecordedFuture/RecordedFuture.yml Docker image update
* Packs/RecordedFuture/Integrations/RecordedFutureLists/RecordedFutureLists.yml Docker image update
* Fix DS108
---------
Co-authored-by: israelpolishook
* CS Falcon - Add batch_id argument to run_command (#31394)
* added batch_id argument
* unit tests
* updated unit tests and docker image
* RN
* updated README
* Update Packs/CrowdStrikeFalcon/Integrations/CrowdStrikeFalcon/CrowdStrikeFalcon.py
Co-authored-by: EyalPintzov <91007713+eyalpalo@users.noreply.github.com>
* Bump pack from version CrowdStrikeFalcon to 1.12.8.
* updated the timeout
* updated the timeout
* updated the timeout
* docker image update
---------
Co-authored-by: EyalPintzov <91007713+eyalpalo@users.noreply.github.com>
Co-authored-by: Content Bot
* Update Docker Image To demisto/auth-utils (#31472)
* Updated Metadata Of Pack Cylance_Protect
* Added release notes to pack Cylance_Protect
* Packs/Cylance_Protect/Integrations/Cylance_Protect_v2/Cylance_Protect_v2.yml Docker image update
* Updated Metadata Of Pack Zoom
* Added release notes to pack Zoom
* Packs/Zoom/Integrations/ZoomEventCollector/ZoomEventCollector.yml Docker image update
* Updated Metadata Of Pack Silverfort
* Added release notes to pack Silverfort
* Packs/Silverfort/Integrations/Silverfort/Silverfort.yml Docker image update
* Updated Metadata Of Pack AzureDataExplorer
* Added release notes to pack AzureDataExplorer
* Packs/AzureDataExplorer/Integrations/AzureDataExplorer/AzureDataExplorer.yml Docker image update
* Updated Metadata Of Pack MicrosoftManagementActivity
* Added release notes to pack MicrosoftManagementActivity
* Packs/MicrosoftManagementActivity/Integrations/MicrosoftManagementActivity/MicrosoftManagementActivity.yml Docker image update
* Updated Metadata Of Pack Box
* Added release notes to pack Box
* Packs/Box/Integrations/BoxEventsCollector/BoxEventsCollector.yml Docker image update
* Packs/Box/Integrations/BoxV2/BoxV2.yml Docker image update
* exclude Silverfort pack
---------
Co-authored-by: israelpolishook
* Update Docker Image To demisto/parse-emails (#31457)
* Updated Metadata Of Pack CommonScripts
* Added release notes to pack CommonScripts
* Packs/CommonScripts/Scripts/ParseEmailFilesV2/ParseEmailFilesV2.yml Docker image update
* Bump pack from version CommonScripts to 1.13.2.
* Bump pack from version CommonScripts to 1.13.4.
* Bump pack from version CommonScripts to 1.13.5.
---------
Co-authored-by: Content Bot
* update condition for create link to jira for contributions prs (#31475)
* bug fix (#31476)
* save fix
* save fix
* save debug
* save debug
* [SaaS Security Event Collector] - logs & docs improvements (#31474)
* [SaaS Security Event Collector] - logs improvements
* docs updates
* rn
* pre-commit fixes
* rn
* rn
* Added context output and indicator tagging to CreateIndicatorsFromStix (#31485)
* Added context output and indicator tagging to CreateIndicatorsFromStix (#31140)
* Added context output and tagging to CreateIndicatorsFromSTIX.py
* Removed Spaces in CommandResults
* Added Release Note
Bumped Up Version to 1.12.50
* Update Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/CreateIndicatorsFromSTIX.py
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* Update Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/CreateIndicatorsFromSTIX.py
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* Update Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/CreateIndicatorsFromSTIX.yml
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* Update Packs/CommonScripts/ReleaseNotes/1_12_50.md
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* Update Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/CreateIndicatorsFromSTIX.py
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* fixes in CreateIndicatorsFromSTIX.py
* Updated YML
* Updated CreateIndicatorsFromSTIX_test.py
* Updated CreateIndicatorsFromSTIX_test.py
* Updated Docker Image Version
* Updated Release notes to align with docker version
* Added Tags to context output.
* Added outputs to CreateIndicatorsFromSTIX.yml
* Bumped up Docker Image version in Release Note and YML
Added additional asserts in test
* Adjusted Version
* Updated README.md
* Updated CreateIndicatorsFromSTIX.yml with description periods.
* Added CONTRIBUTORS.json
* Deleted CONTRIBUTORS.json
* Update 1_13_5.md
* Update CreateIndicatorsFromSTIX.yml
* Update README.md
* Update README.md
* Update Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/CreateIndicatorsFromSTIX.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/CreateIndicatorsFromSTIX.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/CreateIndicatorsFromSTIX.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonScripts/Scripts/CreateIndicatorsFromSTIX/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---------
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* merge from master
---------
Co-authored-by: Martin Ohl
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
Co-authored-by: adi88d
* Update Docker Image To demisto/sklearn (#31458)
* Updated Metadata Of Pack Phishing
* Added release notes to pack Phishing
* Packs/Phishing/Scripts/FindDuplicateEmailIncidents/FindDuplicateEmailIncidents.yml Docker image update
---------
Co-authored-by: israelpoli <72099621+israelpoli@users.noreply.github.com>
* Update Docker Image To demisto/chromium (#31460)
* Updated Metadata Of Pack ExpanseV2
* Added release notes to pack ExpanseV2
* Packs/ExpanseV2/Scripts/ExpanseGenerateIssueMapWidgetScript/ExpanseGenerateIssueMapWidgetScript.yml Docker image update
---------
Co-authored-by: israelpoli <72099621+israelpoli@users.noreply.github.com>
* Fixed auto closing tickets in service now (#31194)
* fix
* tests
* rn
* format
* rn
* Bump pack from version ServiceNow to 2.5.48.
* revert and bug fix
* cr
---------
Co-authored-by: Content Bot
* Fix email com (#31481)
* fixes
* added rn
* update docker
* update tests
* cr fixes
* quick fix
* Update Docker Image To demisto/readpdf (#31507)
* Updated Metadata Of Pack CommonScripts
* Added release notes to pack CommonScripts
* Packs/CommonScripts/Scripts/PDFUnlocker/PDFUnlocker.yml Docker image update
* Packs/CommonScripts/Scripts/ReadPDFFileV2/ReadPDFFileV2.yml Docker image update
* Replacing Qradar search PB with the representative command (#31328)
* Changed the QradarSearch PB to the relavent command
* RN
* RN
* Changed the PB to be deprecated
* Changed keys according to the new output
* Resolve conflicts
* Removed un required tests
* Changed from simple to complex
* Bump pack from version CommonPlaybooks to 2.4.40.
* Added BC + updated the PB readme files
* Added BC + updated the PB readme files
* Bump pack from version QRadar to 2.4.46.
* removed un-used script arguments ( ChangeContext script)
---------
Co-authored-by: Content Bot
* [PAN-OS Policy Optimizer] Add pagination support to `pan-os-po-get-rules` (#31402)
* Improve readability
* Add pagination to `policy_optimizer_get_rules`
* Readable output improvements
* Fix `argToBoolean` resulting in error if the optional `exclude` parameter is missing
* Add pagination parameters
* ruff
* Update README
* Add release-notes and bump version
* Fix mypy issues
* Minor release-notes fix
* Fix unit-tests
* Add `page` parameter
* Add pagination unit-test
* Bump Docker version
* adding xsoar-saas_test_e2e_results to needs list (#31510)
* Small fixes to folder names (#31019)
* OpenCVE throws an error when trying to enrich a CVE (#31482)
OpenCVE throws an error when trying to enrich a CVE #31482
* Remove generic polling task (#31411)
* generic polling task was removed and read me file created
* Release notes update
* release notes update
* old playbook deprecated and new version created
* release notes added
* added image to the old playbook version
* deprecated for the playbook
* RN updated
* added image
* removed unnecessary tasks
* added more outputs
* RN updated
* added description
* image replaced
* added an instance to a test PB
* removed tests instances
removed from PB this test
* removed tests
---------
Co-authored-by: Sasha Sokolovich <88268646+ssokolovich@users.noreply.github.com>
Co-authored-by: ssokolovich
* CTF fixes (#31483)
* - Fixed hints and tasks descriptions
- added the "LastArrayElement" to all check your answers tasks ( in case the user will re-open the data collection task and submit the answer through it).
* RN
* Fix command analysis PB (#31461)
* Added another path so the PB won't skip the entire branch.
* Added another path so the PB won't skip the entire branch.
* Removed all tests
* fix validations
* Bump pack from version CommonPlaybooks to 2.4.41.
* Updated RN description
* Updated RN description
---------
Co-authored-by: Content Bot
* Added Plug and Fetch tags (#31136)
* Slack bb fixes (#31393)
* install specific version of neo4j in ci (#31520)
* [Marketplace Contribution] QR Code Read and Decode (offline) (#31523)
* [Marketplace Contribution] QR Code Read and Decode (offline) (#31099)
* "pack contribution initial commit"
* Update Qrcodereader.py
fixed for Multi
* move script to QRCodeReader pack
* format yml file
* update RN
* add CONTRIBUTORS.json
fix flake8
---------
Co-authored-by: Joerg Stephan <7138386+johestephan@users.noreply.github.com>
Co-authored-by: adi88d
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* add disable=no-member
---------
Co-authored-by: xsoar-bot <67315154+xsoar-bot@users.noreply.github.com>
Co-authored-by: Joerg Stephan <7138386+johestephan@users.noreply.github.com>
Co-authored-by: adi88d
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
* Update Elasticsearch pack README.md (#31514)
* Update incident occurred time (#31522)
* Update incident occurred time (#31404)
* updating occurred time for incidents
* release notes
* validation fixes
* nit
* fix formatting
* update RN
---------
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
Co-authored-by: adi88d
* add new line
* update RN
* remove whitespace from blank line
---------
Co-authored-by: William Olyslager
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
Co-authored-by: adi88d
* [Azure Compute v2] Fixed the API version (#31517)
* First sso fix ip task (#31512)
* change skipifunavailable to true - !ip
* RN after change skipifunavailable to true - !ip
* removed unessary poetry changes
* removed unessary poetry changes
* replace \
* remove file
* update docker
* rn
* fix dn also
* new rn
* Add comment
---------
Co-authored-by: RotemAmit
Co-authored-by: eli sharf <57587340+esharf@users.noreply.github.com>
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
Co-authored-by: eepstain <116078117+eepstain@users.noreply.github.com>
Co-authored-by: content-bot <55035720+content-bot@users.noreply.github.com>
Co-authored-by: zdrouse
Co-authored-by: adi88d
Co-authored-by: Adi Daud <46249224+adi88d@users.noreply.github.com>
Co-authored-by: Guy Afik <53861351+GuyAfik@users.noreply.github.com>
Co-authored-by: Yuval Hayun <70104171+YuvHayun@users.noreply.github.com>
Co-authored-by: omerKarkKatz <95565843+omerKarkKatz@users.noreply.github.com>
Co-authored-by: TalNos <112805149+TalNos@users.noreply.github.com>
Co-authored-by: Menachem Weinfeld <90556466+mmhw@users.noreply.github.com>
Co-authored-by: Content Bot
Co-authored-by: Ben Melamed
Co-authored-by: Crest Data Systems <60967033+crestdatasystems@users.noreply.github.com>
Co-authored-by: crestdatasystems
Co-authored-by: MLainer1 <93524335+MLainer1@users.noreply.github.com>
Co-authored-by: John <40349459+BigEasyJ@users.noreply.github.com>
Co-authored-by: yasta5 <112320333+yasta5@users.noreply.github.com>
Co-authored-by: Shahaf Ben Yakir <44666568+ShahafBenYakir@users.noreply.github.com>
Co-authored-by: Dan Tavori <38749041+dantavori@users.noreply.github.com>
Co-authored-by: cweltPA <129675344+cweltPA@users.noreply.github.com>
Co-authored-by: israelpolishook
Co-authored-by: Karina Fishman <147307864+karinafishman@users.noreply.github.com>
Co-authored-by: Sasha Sokolovich <88268646+ssokolovich@users.noreply.github.com>
Co-authored-by: Moshe Galitzky <112559840+moishce@users.noreply.github.com>
Co-authored-by: Yehuda Rosenberg <90599084+RosenbergYehuda@users.noreply.github.com>
Co-authored-by: Moshe Eichler <78307768+MosheEichler@users.noreply.github.com>
Co-authored-by: Dean Arbel
Co-authored-by: xsoar-bot <67315154+xsoar-bot@users.noreply.github.com>
Co-authored-by: Sapir Shuker <49246861+sapirshuker@users.noreply.github.com>
Co-authored-by: David Uhrlaub <90627446+rurhrlaub@users.noreply.github.com>
Co-authored-by: suraj-metron <87964764+suraj-metron@users.noreply.github.com>
Co-authored-by: Jasmine Beilin <71636766+JasBeilin@users.noreply.github.com>
Co-authored-by: Arad Carmi <62752352+AradCarmi@users.noreply.github.com>
Co-authored-by: DinaMeylakh <72339665+DinaMeylakh@users.noreply.github.com>
Co-authored-by: William Olyslager
Co-authored-by: sapirshuker
Co-authored-by: JudithB <132264628+jbabazadeh@users.noreply.github.com>
Co-authored-by: Jacob Levy <129657918+jlevypaloalto@users.noreply.github.com>
Co-authored-by: merit-maita <49760643+merit-maita@users.noreply.github.com>
Co-authored-by: ilaner <88267954+ilaner@users.noreply.github.com>
Co-authored-by: ilan
Co-authored-by: Chait A <112722030+capanw@users.noreply.github.com>
Co-authored-by: ilappe
Co-authored-by: TalGumi <101499620+TalGumi@users.noreply.github.com>
Co-authored-by: okarkkatz
Co-authored-by: Jas Beilin
Co-authored-by: Erez FelmanDar <102903097+efelmandar@users.noreply.github.com>
Co-authored-by: Shmuel Kroizer <69422117+shmuel44@users.noreply.github.com>
Co-authored-by: Yaakov Praisler <59408745+yaakovpraisler@users.noreply.github.com>
Co-authored-by: samuelFain <65926551+samuelFain@users.noreply.github.com>
Co-authored-by: Martin Ohl
Co-authored-by: Koby Meir
Co-authored-by: Mai Morag <81917647+maimorag@users.noreply.github.com>
Co-authored-by: EyalPintzov <91007713+eyalpalo@users.noreply.github.com>
Co-authored-by: Ido van Dijk <43602124+idovandijk@users.noreply.github.com>
Co-authored-by: ArikDay <115150768+ArikDay@users.noreply.github.com>
Co-authored-by: anas-yousef <44998563+anas-yousef@users.noreply.github.com>
Co-authored-by: Christopher Hultin
Co-authored-by: Yuval Cohen <86777474+yucohen@users.noreply.github.com>
Co-authored-by: arikday
Co-authored-by: NicBunn-PlutoFlume <112942358+NicBunn-PlutoFlume@users.noreply.github.com>
Co-authored-by: israelpoli <72099621+israelpoli@users.noreply.github.com>
Co-authored-by: Chanan Welt
Co-authored-by: Vipul Kaneriya <50216620+vipulkaneriya@users.noreply.github.com>
Co-authored-by: MLainer1
Co-authored-by: syed-loginsoft <97145640+syed-loginsoft@users.noreply.github.com>
Co-authored-by: Danny Fried
Co-authored-by: michal-dagan <109464765+michal-dagan@users.noreply.github.com>
Co-authored-by: sharonfi99 <147984773+sharonfi99@users.noreply.github.com>
Co-authored-by: Michael Yochpaz <8832013+MichaelYochpaz@users.noreply.github.com>
Co-authored-by: IP2Location
Co-authored-by: Liron Michalevich <73780437+lmichalevich@users.noreply.github.com>
Co-authored-by: asieberle <121243004+asieberle@users.noreply.github.com>
Co-authored-by: Judah Schwartz
Co-authored-by: shaqnawe
Co-authored-by: yaakovpraisler
Co-authored-by: Kobbi Gal <85439776+kgal-pan@users.noreply.github.com>
Co-authored-by: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Co-authored-by: chloerongier <150173582+chloerongier@users.noreply.github.com>
Co-authored-by: Isaiah Eichen
Co-authored-by: Dror Avrahami
Co-authored-by: ssokolovich
Co-authored-by: Andrew Shamah <42912128+amshamah419@users.noreply.github.com>
Co-authored-by: Joerg Stephan <7138386+johestephan@users.noreply.github.com>
Co-authored-by: OmriItzhak <115150792+OmriItzhak@users.noreply.github.com>
---
.../Active_Directory_Query/Active_Directory_Query.py | 3 +++
Packs/Active_Directory_Query/ReleaseNotes/1_6_30.md | 6 ++++++
Packs/Active_Directory_Query/pack_metadata.json | 2 +-
3 files changed, 10 insertions(+), 1 deletion(-)
create mode 100644 Packs/Active_Directory_Query/ReleaseNotes/1_6_30.md
diff --git a/Packs/Active_Directory_Query/Integrations/Active_Directory_Query/Active_Directory_Query.py b/Packs/Active_Directory_Query/Integrations/Active_Directory_Query/Active_Directory_Query.py
index 5875672fb282..887fd8cabb01 100644
--- a/Packs/Active_Directory_Query/Integrations/Active_Directory_Query/Active_Directory_Query.py
+++ b/Packs/Active_Directory_Query/Integrations/Active_Directory_Query/Active_Directory_Query.py
@@ -400,6 +400,9 @@ def get_user_dn_by_email(default_base_dn, email):
def modify_user_ou(dn, new_ou):
assert connection is not None
cn = dn.split(',', 1)[0]
+ # removing // to fix customers bug
+ cn = cn.replace('\\', '')
+ dn = dn.replace('\\', '')
success = connection.modify_dn(dn, cn, new_superior=new_ou)
return success
diff --git a/Packs/Active_Directory_Query/ReleaseNotes/1_6_30.md b/Packs/Active_Directory_Query/ReleaseNotes/1_6_30.md
new file mode 100644
index 000000000000..261643f3215d
--- /dev/null
+++ b/Packs/Active_Directory_Query/ReleaseNotes/1_6_30.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Active Directory Query v2
+
+- Fixed an issue where the ***ad-modify-user-ou*** command changed the CN value.
\ No newline at end of file
diff --git a/Packs/Active_Directory_Query/pack_metadata.json b/Packs/Active_Directory_Query/pack_metadata.json
index c5b7d124933e..342196ddebde 100644
--- a/Packs/Active_Directory_Query/pack_metadata.json
+++ b/Packs/Active_Directory_Query/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Active Directory Query",
"description": "Active Directory Query integration enables you to access and manage Active Directory objects (users, contacts, and computers).",
"support": "xsoar",
- "currentVersion": "1.6.29",
+ "currentVersion": "1.6.30",
"author": "Cortex XSOAR",
"url": "",
"email": "",
From 026bd6f3aa8d95b4d7f58b281465414c863d1d02 Mon Sep 17 00:00:00 2001
From: eepstain <116078117+eepstain@users.noreply.github.com>
Date: Thu, 22 Feb 2024 09:50:58 +0200
Subject: [PATCH 065/272] Update MS DNS README (#33053)
* Updated README
* Update Packs/MicrosoftDNS/README.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---
Packs/MicrosoftDNS/README.md | 5 ++++-
1 file changed, 4 insertions(+), 1 deletion(-)
diff --git a/Packs/MicrosoftDNS/README.md b/Packs/MicrosoftDNS/README.md
index caa17d96cc6f..a585d9fbee1f 100644
--- a/Packs/MicrosoftDNS/README.md
+++ b/Packs/MicrosoftDNS/README.md
@@ -25,7 +25,10 @@ You can configure the vendor and product by replacing [vendor]\_[product]\_raw w
When configuring the instance, you should use a yml file that configures the vendor and product, as shown in the below configuration for the Microsoft DNS product.
**Pay Attention**:
-When using this pack there are two integrations available for it.
+* There are two integrations available in this content pack.
+* Timestamp log ingestion is supported in either of the following formats in UTC (00:00) time.
+ - *%m/%d/%Y %I:%M:%S %p*
+ - *%d/%m/%Y %H:%M:%S*
* ***As enrichment, forwarding DNS Audit logs is supported via Winlogbeat***
From 1e127860609ab84be4c9c10cf25b02da20f548a9 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Thu, 22 Feb 2024 10:45:21 +0200
Subject: [PATCH 066/272] Update `demisto/teams` 0-10 coverage rate (#32633)
* upgrade images
* update RN
* Bump pack from version Workday to 1.4.11.
---------
Co-authored-by: Content Bot
---
.../WorkdayIAMEventsGenerator/WorkdayIAMEventsGenerator.yml | 2 +-
Packs/Workday/ReleaseNotes/1_4_11.md | 6 ++++++
Packs/Workday/pack_metadata.json | 2 +-
3 files changed, 8 insertions(+), 2 deletions(-)
create mode 100644 Packs/Workday/ReleaseNotes/1_4_11.md
diff --git a/Packs/Workday/Integrations/WorkdayIAMEventsGenerator/WorkdayIAMEventsGenerator.yml b/Packs/Workday/Integrations/WorkdayIAMEventsGenerator/WorkdayIAMEventsGenerator.yml
index bf5d3e70830b..a70c55d83314 100644
--- a/Packs/Workday/Integrations/WorkdayIAMEventsGenerator/WorkdayIAMEventsGenerator.yml
+++ b/Packs/Workday/Integrations/WorkdayIAMEventsGenerator/WorkdayIAMEventsGenerator.yml
@@ -63,7 +63,7 @@ script:
name: workday-generate-terminate-event
- description: Reset the integration context to fetch the first run reports.
name: initialize-context
- dockerimage: demisto/teams:1.0.0.14902
+ dockerimage: demisto/teams:1.0.0.86482
longRunning: true
longRunningPort: true
script: '-'
diff --git a/Packs/Workday/ReleaseNotes/1_4_11.md b/Packs/Workday/ReleaseNotes/1_4_11.md
new file mode 100644
index 000000000000..e4b4c58d06ce
--- /dev/null
+++ b/Packs/Workday/ReleaseNotes/1_4_11.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### Workday IAM Event Generator (Beta)
+
+- Updated the Docker image to: *demisto/teams:1.0.0.86482*.
diff --git a/Packs/Workday/pack_metadata.json b/Packs/Workday/pack_metadata.json
index 122a314edc70..7ddaa7bf387a 100644
--- a/Packs/Workday/pack_metadata.json
+++ b/Packs/Workday/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Workday",
"description": "Workday offers enterprise-level software solutions for financial management, human resources, and planning.",
"support": "xsoar",
- "currentVersion": "1.4.10",
+ "currentVersion": "1.4.11",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From ea5c2e941ab1f5fbd9b24b2d2c75cb014d786703 Mon Sep 17 00:00:00 2001
From: Arad Carmi <62752352+AradCarmi@users.noreply.github.com>
Date: Thu, 22 Feb 2024 10:54:11 +0200
Subject: [PATCH 067/272] Updated repo name from the Github Context (#33055)
---
.github/workflows/trigger-contribution-build.yml | 2 +-
1 file changed, 1 insertion(+), 1 deletion(-)
diff --git a/.github/workflows/trigger-contribution-build.yml b/.github/workflows/trigger-contribution-build.yml
index b51464014b9f..018ff010b997 100644
--- a/.github/workflows/trigger-contribution-build.yml
+++ b/.github/workflows/trigger-contribution-build.yml
@@ -24,7 +24,7 @@ jobs:
PR_NUMBER: ${{ github.event.pull_request.number }}
BASE_BRANCH: ${{ github.event.pull_request.base.ref }}
CONTRIB_BRANCH: ${{ github.event.pull_request.head.label }}
- CONTRIB_REPO: ${{ github.event.repository.name }}
+ CONTRIB_REPO: ${{ github.event.pull_request.head.repo.name }}
USERNAME: ${{ secrets.SECRET_CHECK_USER_NG }}
PASSWORD: ${{ secrets.SECRET_CHECK_PASS_NG }}
GOLD_SERVER_URL: ${{ secrets.GOLD_SERVER_URL_NG }}
From 6922ab5967602043f8a9433b2e36d7787a3716f8 Mon Sep 17 00:00:00 2001
From: samuelFain <65926551+samuelFain@users.noreply.github.com>
Date: Thu, 22 Feb 2024 11:56:56 +0200
Subject: [PATCH 068/272] [EWSO365] Handle corrupt Message-ID header (#32776)
* Add handling of Message-ID header coming from attachment.item.headers
Add debug logs
* Update malformed Message-ID handling to also consider escape characters
* Update handle_incorrect_message_id to consider escape characters
Update RN; Update docker image
* Add UT; Update docker image ref
* Update release notes
* Replace string.find with regex search
* Remove XSUP-32660 debug logs
* Add test use cases
* Apply suggestions from code review
Co-authored-by: dorschw <81086590+dorschw@users.noreply.github.com>
* Remove redundant IndexError handling
* Update docker image
* Update release notes
---------
Co-authored-by: dorschw <81086590+dorschw@users.noreply.github.com>
---
.../Integrations/EWSO365/EWSO365.py | 43 ++++++++++++++-----
.../Integrations/EWSO365/EWSO365.yml | 2 +-
.../Integrations/EWSO365/EWSO365_test.py | 30 ++++++++++++-
.../ReleaseNotes/1_2_40.md | 8 ++++
.../pack_metadata.json | 2 +-
5 files changed, 71 insertions(+), 14 deletions(-)
create mode 100644 Packs/MicrosoftExchangeOnline/ReleaseNotes/1_2_40.md
diff --git a/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365.py b/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365.py
index 815b93e27440..45d4951a7f85 100644
--- a/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365.py
+++ b/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365.py
@@ -2037,7 +2037,7 @@ def get_item_as_eml(client: EWSClient, item_id, target_mailbox=None): # pra
return None
-def handle_attached_email_with_incorrect_id(attached_email: Message):
+def handle_attached_email_with_incorrect_message_id(attached_email: Message):
"""This function handles a malformed Message-ID value which can be returned in the header of certain email objects.
This issue happens due to a current bug in "email" library and further explained in XSUP-32074.
Public issue link: https://github.com/python/cpython/issues/105802
@@ -2053,12 +2053,14 @@ def handle_attached_email_with_incorrect_id(attached_email: Message):
for i in range(len(attached_email._headers)):
if attached_email._headers[i][0] == "Message-ID":
message_id = attached_email._headers[i][1]
+ demisto.debug(f'Handling Message-ID header, {message_id=}.')
try:
- if message_id.endswith("]>") and message_id.startswith("<["):
- demisto.debug(f"Fixing invalid {message_id=} attachment header by removing its square bracket \
- wrapper (see XSUP-32074 for further information)")
+ message_id_value = handle_incorrect_message_id(message_id)
+ if message_id_value != message_id:
+ # If the Message-ID header was fixed in the context of this function
+ # the header will be replaced in _headers list
attached_email._headers.pop(i)
- message_id_value = f"<{message_id[2:-2]}>"
+ attached_email._headers.append(("Message-ID", message_id_value))
except Exception as e:
# The function is designed to handle a specific format error for the Message-ID header
@@ -2069,12 +2071,24 @@ def handle_attached_email_with_incorrect_id(attached_email: Message):
demisto.debug(f"Invalid {message_id=}, Error: {e}")
break
break
- if message_id_value:
- # If the Message-ID header was fixed in the context of this function, it will be inserted again to the _headers list
- attached_email._headers.append(("Message-ID", message_id_value))
return attached_email
+def handle_incorrect_message_id(message_id: str) -> str:
+ """
+ Use regex to identify and correct one of the following invalid message_id formats:
+ 1. '<[message_id]>' --> ''
+ 2. '\r\n\t<[message_id]>' --> '\r\n\t'
+ If no necessary changes identified the original 'message_id' argument value is returned.
+ """
+ if re.search("\<\[.*\]\>", message_id):
+ # find and replace "<[" with "<" and "]>" with ">"
+ fixed_message_id = re.sub(r'<\[(.*?)\]>', r'<\1>', message_id)
+ demisto.debug('Fixed message id {message_id} to {fixed_message_id}')
+ return fixed_message_id
+ return message_id
+
+
def parse_incident_from_item(item): # pragma: no cover
"""
Parses an incident from an item
@@ -2184,7 +2198,7 @@ def parse_incident_from_item(item): # pragma: no cover
if attachment.item.headers:
# compare header keys case-insensitive
attached_email_headers = []
- attached_email = handle_attached_email_with_incorrect_id(attached_email)
+ attached_email = handle_attached_email_with_incorrect_message_id(attached_email)
for h, v in attached_email.items():
if not isinstance(v, str):
try:
@@ -2203,7 +2217,16 @@ def parse_incident_from_item(item): # pragma: no cover
and header.name.lower() != "content-type"
):
try:
- attached_email.add_header(header.name, header.value)
+ if header.name.lower() == "message-id":
+ """ Handle a case where a Message-ID header was NOT already in attached_email,
+ and instead is coming from attachment.item.headers.
+ Meaning it wasn't handled in handle_attached_email_with_incorrect_message_id function
+ and instead it is handled here using handle_incorrect_message_id function."""
+ correct_message_id = handle_incorrect_message_id(header.value)
+ if (header.name.lower(), correct_message_id) not in attached_email_headers:
+ attached_email.add_header(header.name, correct_message_id)
+ else:
+ attached_email.add_header(header.name, header.value)
except ValueError as err:
if "There may be at most" not in str(err):
raise err
diff --git a/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365.yml b/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365.yml
index dd04831bbd9b..f4a9c2b50362 100644
--- a/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365.yml
+++ b/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365.yml
@@ -959,7 +959,7 @@ script:
- description: Run this command if for some reason you need to rerun the authentication process.
name: ews-auth-reset
arguments: []
- dockerimage: demisto/py3ews:1.0.0.86480
+ dockerimage: demisto/py3ews:1.0.0.88266
isfetch: true
script: ''
subtype: python3
diff --git a/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365_test.py b/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365_test.py
index 4fd460a8f021..cd98f47b0513 100644
--- a/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365_test.py
+++ b/Packs/MicrosoftExchangeOnline/Integrations/EWSO365/EWSO365_test.py
@@ -18,8 +18,9 @@
get_expanded_group,
get_item_as_eml,
get_searchable_mailboxes,
- handle_attached_email_with_incorrect_id,
+ handle_attached_email_with_incorrect_message_id,
handle_html,
+ handle_incorrect_message_id,
handle_transient_files,
parse_incident_from_item,
parse_item_as_dict,
@@ -864,4 +865,29 @@ def test_handle_attached_email_with_incorrect_id(mocker, headers, expected_forma
email_policy = SMTP
attached_email = email.message_from_bytes(mime_content, policy=email_policy)
attached_email._headers = headers
- assert handle_attached_email_with_incorrect_id(attached_email)._headers == expected_formatted_headers
+ assert handle_attached_email_with_incorrect_message_id(attached_email)._headers == expected_formatted_headers
+
+
+@pytest.mark.parametrize("message_id, expected_message_id_output", [
+ pytest.param('', '', id="valid message_id 1"),
+ pytest.param('', '', id="valid message_id 2"),
+ pytest.param('<>]message_id>', '<>]message_id>', id="valid message_id 3"),
+ pytest.param('<[message_id]>', '', id="invalid message_id"),
+ pytest.param('\r\n\t', '\r\n\t', id="valid message_id with escape chars"),
+ pytest.param('\r\n\t<[message_id]>', '\r\n\t', id="invalid message_id with escape chars"),
+])
+def test_handle_incorrect_message_id(message_id, expected_message_id_output):
+ """
+ Given:
+ - case 1: valid Message-ID header value in attached email object
+ - case 1: invalid Message-ID header value in attached email object
+ - case 3: a Message-ID header value format which is not tested in the context of handle_attached_email_with_incorrect_id
+ When:
+ - fetching email which have an attached email with Message-ID header
+ Then:
+ - case 1: verify the header in the correct format
+ - case 2: correct the invalid Message-ID header value
+ - case 3: return the header value without without further handling
+
+ """
+ assert handle_incorrect_message_id(message_id) == expected_message_id_output
diff --git a/Packs/MicrosoftExchangeOnline/ReleaseNotes/1_2_40.md b/Packs/MicrosoftExchangeOnline/ReleaseNotes/1_2_40.md
new file mode 100644
index 000000000000..204221ee002f
--- /dev/null
+++ b/Packs/MicrosoftExchangeOnline/ReleaseNotes/1_2_40.md
@@ -0,0 +1,8 @@
+
+#### Integrations
+
+##### EWS O365
+- Updated the Docker image to: *demisto/py3ews:1.0.0.88266*.
+
+- Fixed an issue where fetching failed when email attachments had headers with an invalid format containing escape characters (`\r\n\t<[invalid_value]>` instead of `\r\n\t`), by removing the square brackets.
+
diff --git a/Packs/MicrosoftExchangeOnline/pack_metadata.json b/Packs/MicrosoftExchangeOnline/pack_metadata.json
index e6d3be3e88c5..aa78201704bd 100644
--- a/Packs/MicrosoftExchangeOnline/pack_metadata.json
+++ b/Packs/MicrosoftExchangeOnline/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Microsoft Exchange Online",
"description": "Exchange Online and Office 365 (mail)",
"support": "xsoar",
- "currentVersion": "1.2.39",
+ "currentVersion": "1.2.40",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 712bd0d3eaa042b26f45f575b97d19d6d7507697 Mon Sep 17 00:00:00 2001
From: samuelFain <65926551+samuelFain@users.noreply.github.com>
Date: Thu, 22 Feb 2024 14:12:40 +0200
Subject: [PATCH 069/272] [Native Image] Release py3-native 8.6 (#32977)
* Update native image versions
Reference for 8.6 will be updated once available
* Update native image 8.6 reference
* Update native image ref
* Apply suggestions from code review
Co-authored-by: Guy Afik <53861351+GuyAfik@users.noreply.github.com>
* Remove native:8.4
* Remove trailing comma in json file
---------
Co-authored-by: Guy Afik <53861351+GuyAfik@users.noreply.github.com>
---
Tests/docker_native_image_config.json | 62 +++++----------------------
1 file changed, 11 insertions(+), 51 deletions(-)
diff --git a/Tests/docker_native_image_config.json b/Tests/docker_native_image_config.json
index d884de2b1f26..471cd0dfc482 100644
--- a/Tests/docker_native_image_config.json
+++ b/Tests/docker_native_image_config.json
@@ -1,37 +1,6 @@
{
"native_images":{
- "native:8.3": {
- "supported_docker_images": [
- "python3",
- "python3-deb",
- "python3-ubi",
- "py3-tools",
- "py3-tools-ubi",
- "crypto",
- "readpdf",
- "parse-emails",
- "docxpy",
- "sklearn",
- "pandas",
- "ippysocks-py3",
- "oauthlib",
- "unzip",
- "py3ews",
- "taxii2",
- "pan-os-python",
- "slackv3",
- "google-api-py3",
- "boto3py3",
- "pyjwt3",
- "joe-security",
- "slack",
- "office-utils",
- "chromium",
- "tesseract"
- ],
- "docker_ref": "demisto/py3-native:8.3.0.73063"
- },
- "native:8.4":{
+ "native:8.6":{
"supported_docker_images":[
"python3",
"python3-deb",
@@ -62,7 +31,7 @@
"netutils",
"auth-utils"
],
- "docker_ref": "demisto/py3-native:8.4.0.75024"
+ "docker_ref": "demisto/py3-native:8.6.0.88042"
},
"native:dev":{
"supported_docker_images":[
@@ -133,8 +102,7 @@
"id":"Symantec MSS",
"reason":"issue: CIAC-9119 - [Symantec MSS] Module 'OpenSSL.crypto' has deprecated 'load_pkcs12' member",
"ignored_native_images":[
- "native:8.4",
- "native:8.3",
+ "native:8.6",
"native:dev",
"native:candidate"
]
@@ -143,8 +111,7 @@
"id":"FetchIndicatorsFromFile",
"reason":"issue: CIAC-5243 - ElementTree object (xml) in python3.9 has getiterator attribute while in python 3.10 this attribute does not exist - causing unit tests failures.",
"ignored_native_images":[
- "native:8.4",
- "native:8.3",
+ "native:8.6",
"native:dev",
"native:candidate"
]
@@ -153,8 +120,7 @@
"id":"Rasterize",
"reason":"Issue: CRTX-72338 and CIAC-7694",
"ignored_native_images":[
- "native:8.4",
- "native:8.3",
+ "native:8.6",
"native:candidate"
]
},
@@ -162,8 +128,7 @@
"id":"Intezer v2",
"reason":"Issue: CIAC-7861",
"ignored_native_images":[
- "native:8.4",
- "native:8.3",
+ "native:8.6",
"native:candidate"
]
},
@@ -171,8 +136,7 @@
"id":"RegexExtractAll",
"reason":"Issue: CIAC-6005",
"ignored_native_images":[
- "native:8.4",
- "native:8.3",
+ "native:8.6",
"native:dev",
"native:candidate"
]
@@ -181,16 +145,14 @@
"id":"ConvertFile",
"reason":"Issue: CIAC-7625",
"ignored_native_images":[
- "native:8.4",
- "native:8.3"
+ "native:8.6"
]
},
{
"id":"DockerHardeningCheck",
"reason":"This script is supposed to run inside a container, does not support podman",
"ignored_native_images":[
- "native:8.4",
- "native:8.3",
+ "native:8.6",
"native:dev",
"native:candidate"
]
@@ -199,8 +161,7 @@
"id":"Ping",
"reason":"see CIAC-8493",
"ignored_native_images":[
- "native:8.4",
- "native:8.3",
+ "native:8.6",
"native:dev",
"native:candidate"
]
@@ -208,8 +169,7 @@
],
"flags_versions_mapping":{
"native:dev":"native:dev",
- "native:ga":"native:8.4",
- "native:maintenance":"native:8.3",
+ "native:ga":"native:8.6",
"native:candidate":"native:candidate"
}
}
From fc03812c5915c2b0b9bea2f56358bd738d9613c2 Mon Sep 17 00:00:00 2001
From: Israel Lappe <79846863+ilappe@users.noreply.github.com>
Date: Thu, 22 Feb 2024 14:46:07 +0200
Subject: [PATCH 070/272] ServiceNow mirror: fix bug when mirror not started
(#33065)
* fix + RN
* fix
* Update Packs/ServiceNow/ReleaseNotes/2_5_55.md
Co-authored-by: Dean Arbel
---------
Co-authored-by: Dean Arbel
---
.../Integrations/ServiceNowv2/ServiceNowv2.py | 12 +++++++-----
Packs/ServiceNow/ReleaseNotes/2_5_55.md | 6 ++++++
Packs/ServiceNow/pack_metadata.json | 2 +-
3 files changed, 14 insertions(+), 6 deletions(-)
create mode 100644 Packs/ServiceNow/ReleaseNotes/2_5_55.md
diff --git a/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.py b/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.py
index dade0ad6689d..3e64ae867317 100644
--- a/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.py
+++ b/Packs/ServiceNow/Integrations/ServiceNowv2/ServiceNowv2.py
@@ -2400,7 +2400,7 @@ def get_remote_data_command(client: Client, args: dict[str, Any], params: dict)
result = client.get(ticket_type, ticket_id)
if not result or 'result' not in result:
- return 'Ticket was not found.'
+ return f'Ticket {ticket_id=} was not found.'
if isinstance(result['result'], list):
if len(result['result']) == 0:
@@ -2417,13 +2417,15 @@ def get_remote_data_command(client: Client, args: dict[str, Any], params: dict)
required=False
)
- demisto.debug(f'ticket_last_update is {ticket_last_update}')
-
- if last_update > ticket_last_update:
- demisto.debug('Nothing new in the ticket')
+ demisto.debug(f'ticket_last_update of {ticket_id=} is {ticket_last_update}')
+ is_fetch = demisto.params().get('isFetch')
+ if is_fetch and last_update > ticket_last_update:
+ demisto.debug(f'Nothing new in the ticket {ticket_id=}')
ticket = {}
else:
+ # in case we use SNOW just to mirror by setting the incident with mirror fields
+ # is_fetch will be false, so we will update even the XSOAR incident will be updated then SNOW ticket.
demisto.debug(f'ticket is updated: {ticket}')
parse_dict_ticket_fields(client, ticket)
diff --git a/Packs/ServiceNow/ReleaseNotes/2_5_55.md b/Packs/ServiceNow/ReleaseNotes/2_5_55.md
new file mode 100644
index 000000000000..a1ed48d107a9
--- /dev/null
+++ b/Packs/ServiceNow/ReleaseNotes/2_5_55.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### ServiceNow v2
+
+- Fixed an issue where mirroring did not update fields that were updated before adding the mirroring fields to the incident.
\ No newline at end of file
diff --git a/Packs/ServiceNow/pack_metadata.json b/Packs/ServiceNow/pack_metadata.json
index 876ef3d88ae7..9670be38aec3 100644
--- a/Packs/ServiceNow/pack_metadata.json
+++ b/Packs/ServiceNow/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "ServiceNow",
"description": "Use The ServiceNow IT Service Management (ITSM) solution to modernize the way you manage and deliver services to your users.",
"support": "xsoar",
- "currentVersion": "2.5.54",
+ "currentVersion": "2.5.55",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 0322acab5b49289fc3416e662888939918e50e14 Mon Sep 17 00:00:00 2001
From: Michael Yochpaz <8832013+MichaelYochpaz@users.noreply.github.com>
Date: Thu, 22 Feb 2024 16:47:23 +0200
Subject: [PATCH 071/272] [OpenCTI] Update Documentation (#33071)
* Update README.md
* Bump version
* ignore `RN112` validation error
---
Packs/OpenCTI/.pack-ignore | 3 +++
Packs/OpenCTI/Integrations/OpenCTI/README.md | 6 +++++-
Packs/OpenCTI/ReleaseNotes/1_0_10.md | 6 ++++++
Packs/OpenCTI/pack_metadata.json | 2 +-
4 files changed, 15 insertions(+), 2 deletions(-)
create mode 100644 Packs/OpenCTI/ReleaseNotes/1_0_10.md
diff --git a/Packs/OpenCTI/.pack-ignore b/Packs/OpenCTI/.pack-ignore
index ceea614384b3..a3713be3debe 100644
--- a/Packs/OpenCTI/.pack-ignore
+++ b/Packs/OpenCTI/.pack-ignore
@@ -1,5 +1,8 @@
[file:README.md]
ignore=RM106
+[file:Packs/OpenCTI/ReleaseNotes/1_0_10.md]
+ignore=RN112
+
[known_words]
OpenCTI
diff --git a/Packs/OpenCTI/Integrations/OpenCTI/README.md b/Packs/OpenCTI/Integrations/OpenCTI/README.md
index e6f0bf8d8a2f..39d0e075ef81 100644
--- a/Packs/OpenCTI/Integrations/OpenCTI/README.md
+++ b/Packs/OpenCTI/Integrations/OpenCTI/README.md
@@ -1,4 +1,8 @@
-Manages indicators from OpenCTI. Compatible with OpenCTI 4.X API and OpenCTI 5.X API versions.
+Manages indicators from OpenCTI.
+This integration is compatible with OpenCTI versions from 4.X to 5.11.X.
+
+**Note**: Due to [breaking changes to the OpenCTI API on version 5.12.0](https://github.com/OpenCTI-Platform/opencti/releases/tag/5.12.0), this integration is not currently compatible with OpenCTI versions 5.12.0 and above.
+
## Configure OpenCTI on Cortex XSOAR
1. Navigate to **Settings** > **Integrations** > **Servers & Services**.
diff --git a/Packs/OpenCTI/ReleaseNotes/1_0_10.md b/Packs/OpenCTI/ReleaseNotes/1_0_10.md
new file mode 100644
index 000000000000..608074fa83b5
--- /dev/null
+++ b/Packs/OpenCTI/ReleaseNotes/1_0_10.md
@@ -0,0 +1,6 @@
+
+#### Integrations
+
+##### OpenCTI
+
+- Updated the documentation to specify that versions 5.12.0 and above of OpenCTI are not currently supported due to [breaking changes to the API](https://github.com/OpenCTI-Platform/opencti/releases/tag/5.12.0).
diff --git a/Packs/OpenCTI/pack_metadata.json b/Packs/OpenCTI/pack_metadata.json
index 62b1957a7cf8..14fd62d7b658 100644
--- a/Packs/OpenCTI/pack_metadata.json
+++ b/Packs/OpenCTI/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "OpenCTI",
"description": "Manages indicators from OpenCTI.",
"support": "xsoar",
- "currentVersion": "1.0.9",
+ "currentVersion": "1.0.10",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 179b50e8979ffe3671f0499b4f7b1e281f05e38b Mon Sep 17 00:00:00 2001
From: Adi Bamberger Edri <72088126+BEAdi@users.noreply.github.com>
Date: Thu, 22 Feb 2024 18:23:35 +0200
Subject: [PATCH 072/272] Prisma Cloud Compute docs update (#32943)
* update README
* doc review
* RN
---
Packs/PrismaCloudCompute/README.md | 205 ++++++++++--------
.../PrismaCloudCompute/ReleaseNotes/1_6_1.md | 5 +
Packs/PrismaCloudCompute/pack_metadata.json | 2 +-
3 files changed, 121 insertions(+), 91 deletions(-)
create mode 100644 Packs/PrismaCloudCompute/ReleaseNotes/1_6_1.md
diff --git a/Packs/PrismaCloudCompute/README.md b/Packs/PrismaCloudCompute/README.md
index 1a1f2f682238..9cf86beb422a 100644
--- a/Packs/PrismaCloudCompute/README.md
+++ b/Packs/PrismaCloudCompute/README.md
@@ -2,79 +2,104 @@
This pack includes Cortex XSIAM content.
<~XSIAM>
-A step-by-step configuration process is available at Cortex XSIAM Administrator Guide- [Ingest Alerts from Prisma Cloud Compute](https://docs-cortex.paloaltonetworks.com/r/Cortex-XSIAM/Cortex-XSIAM-Administrator-Guide/Ingest-Alerts-from-Prisma-Cloud).
-
-## Configuration on XSIAM
-1. Click **Settings** > **Data Sources**.
-2. In the Prisma Cloud Compute Collector configuration, click **Add Instance** to begin a new alerts integration.
-3. Specify the name for the Prisma Cloud Compute Collector displayed in Cortex XSIAM.
-4. Save & Generate Token. The token is displayed in a blue box, which is blurred in the image below.
- * Click the Copy icon next to the Username and Password, and record them in a safe place, as you will need to provide them when you configure the Prisma Cloud Compute Collector for alerts integration. If you forget to record the key and close the window, you will need to generate a new key and repeat this process. When you are finished, click **Done** to close the window.
-5. Copy api url.
- * In the Data Sources page for the Prisma Cloud Compute Collector that you created, click **Copy api url**, and record it somewhere safe. You will need to provide this API URL when you set the Incoming Webhook URL as part of the configuration in Prisma Cloud Compute.
-
-**Note**:
-The URL format for the tenant is `https://api-.xdr.us.paloaltonetworks.com/logs/v1/prisma`.
-
-## Configuration on Prisma Cloud Compute
-1. In Prisma Cloud Compute, create a webhook as explained in the [Webhook Alerts](https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/alerts/webhook) section of the Prisma Cloud Administrator’s Guide (Compute).
- * Config file for Webhook:
-```json
-//{
- "type": "#type",
- "time": "#time",
- "container": "#container",
- "containerID": "#containerID",
- "image": "#image",
- "imageID": "#imageID",
- "tags": "#tags",
- "host": "#host",
- "fqdn": "#fqdn",
- "function": "#function",
- "region": "#region",
- "provider": "#provider",
- "osRelease": "#osRelease",
- "osDistro": "#osDistro",
- "runtime": "#runtime",
- "appID": "#appID",
- "rule": "#rule",
- "message": "#message",
- "aggregatedAlerts": #aggregatedAlerts,
- "dropped": #dropped,
- "forensics": "#forensics",
- "accountID": "#accountID",
- "category": "#category",
- "command": "#command",
- "startupProcess": "#startupProcess",
- "labels": #labels,
- "collections": #collections,
- "complianceIssues": #complianceIssues,
- "vulnerabilities": #vulnerabilities,
- "clusters": #clusters,
- "namespaces": #namespaces,
- "accountIDs": #accountIDs,
- "user": "#user"
-//}
-```
-2. Use the **Webhook** option to configure the webhook.
-3. In **Incoming Webhook URL**, paste the API URL that you copied and recorded from **Copy api url**.
-4. In **Credential Options**, select **Basic Authentication**, and use the Username and Password that you saved when you generated the token.
-5. Select **Container Runtime**.
-6. Click **Save**.
- * In Cortex XSIAM, once alerts start to come in, a green checkmark appears underneath the Prisma Cloud Compute Collector configuration with the amount of data received.
-7. After Cortex XSIAM begins receiving data from Prisma Cloud Compute, you can use XQL Search to search for specific data using the `prisma_cloud_compute_raw` dataset.
-
-
-**Pay Attention**:
-Timestamp parsing support is available for the **time** field in `%h %d, %Y %H:%M:%S UTC` format (E.g `Oct 14, 2023 09:16:04 UTC`)
+## Overview
+
+This integration lets you import **Palo Alto Networks - Prisma Cloud Compute** alerts into Cortex XSIAM.
+
+## Use Cases
+
+Manage Prisma Cloud Compute alerts in Cortex XSIAM.
+You can create new playbooks, or extend the default ones, to analyze alerts, assign tasks based on your analysis, and open tickets on other platforms.
+
+## Configure Prisma Cloud Compute
+
+Configure Prisma Cloud Compute to send alerts to Cortex XSIAM by creating an alert profile.
+
+1. Log in to your Prisma Cloud Compute console. On new Prisma Cloud versions, go to **Runtime Security**.
+1. Navigate to **Manage > Alerts**.
+1. Create a new alert profile by clicking **Add Profile**.
+1. Provide a name, select **Cortex** from the provider list, and select **XSOAR** under Application.
+1. Select the alert triggers. Alert triggers specify which alerts are sent to Cortex XSIAM.
+1. Click **Save** to save the alert profile.
+
+## Configure Cortex XSIAM
+
+1. Navigate to **Settings > Integrations > Instances**.
+1. Search for **Prisma Cloud Compute**.
+1. Click **Add instance** to create and configure a new integration.
+ * **Name**: Name for the integration.
+ * **Fetches incidents**: Configures this integration instance to fetch alerts from Prisma Cloud Compute.
+ * **Prisma Cloud Compute Console URL**: URL address of your Prisma Cloud Compute console. Copy the address from the alert profile created in Prisma Cloud Compute, or under **Runtime Security** copy the address from **System > Utilities > Path to Console**.
+ * **Prisma Cloud Compute Project Name (if applies)**: If using projects in Prisma Cloud Compute, enter the project name here. Copy the project name from the alert profile created in Prisma Cloud Compute.
+ * **Trust any certificate (not secure)**: Skips verification of the CA certificate (not recommended).
+ * **Use system proxy settings**: Uses the system's proxy settings.
+ * **Credentials**: Prisma Cloud Compute login credentials.
+ * **Prisma Cloud Compute CA Certificate**: CA Certificate used by Prisma Cloud Compute. Copy the certificate from the alert profile created in Prisma Cloud Compute.
+4. Click **Test** to validate the integration.
+5. Click **Done** to save the integration.
+
+
+## Using the integration and scripts
+
+The integration ships with four default playbooks:
+* **Prisma Cloud Compute - Audit Alert v3**
+* **Prisma Cloud Compute - Cloud Discovery Alert**
+* **Prisma Cloud Compute - Compliance Alert**
+* **Prisma Cloud Compute - Vulnerability Alert**
+
+Three of the above playbooks (all except _Audit Alert v3_) contain a single script. The script in each playbook encode the raw JSON alerts into Cortex XSIAM objects that can then be used in the playbooks. The scripts are:
+
+* **PrismaCloudComputeParseComplianceAlert**
+* **PrismaCloudComputeParseVulnerabilityAlert**
+* **PrismaCloudComputeParseCloudDiscoveryAlert**
+
+To better understand how playbooks and scripts interoperate, consider the _Prisma Cloud Compute - Vulnerability Alert_ playbook.
+
+* When the playbook is triggered, a task called **Parse Vulnerability Alert** runs.
+* The task runs the **PrismaCloudComputeParseVulnerabilityAlert** script, which takes the `prismacloudcomputerawalertjson` field of the incident (the raw JSON alert data) as input.
+
+
+
+* Click **outputs** to see how the script transformed the raw JSON input into a Cortex XSIAM object.
+
+
+
+
+At this point, you can add tasks that extend the playbook to check and respond to alerts depending on the properties of the Cortex XSIAM object.
+
+### Audit Alert v3 playbook
+This playbook is not similar to the other three playbooks. It is a default playbook for parsing and enrichment of Prisma Cloud Compute audit alerts.
+
+The playbook has the following sections:
+
+Enrichment:
+- Image details
+- Similar container events
+- Owner details
+- Vulnerabilities
+- Compliance details
+- Forensics
+- Defender logs
+Remediation:
+- Block Indicators - Generic v3
+- Cloud Response - Generic
+- Manual Remediation
+
+Currently, the playbook supports incidents created by **Runtime** and **WAAS** triggers.
+
+## Troubleshooting
+
+If any alerts are missing in Cortex XSIAM, check the status of the integration:
+
+
<~XSOAR>
## Overview
-This integration lets you import **Palo Alto Networks - Prisma Cloud Compute** alerts into XSOAR
+This integration lets you import **Palo Alto Networks - Prisma Cloud Compute** alerts into Cortex XSOAR.
## Use Cases
@@ -85,26 +110,26 @@ You can create new playbooks, or extend the default ones, to analyze alerts, ass
Configure Prisma Cloud Compute to send alerts to Cortex XSOAR by creating an alert profile.
-1. Login to your Prisma Cloud Compute console.
+1. Log in to your Prisma Cloud Compute console. On new Prisma Cloud versions, go to **Runtime Security**.
1. Navigate to **Manage > Alerts**.
1. Create a new alert profile by clicking **Add Profile**.
-1. On the left, select **XSOAR** from the provider list.
-1. On the right, select the alert triggers. Alert triggers specify which alerts are sent to Cortex XSOAR.
-1. Click **Save** to save the alert profile
+1. Provide a name, select **Cortex** from the provider list, and select **XSOAR** under Application.
+1. Select the alert triggers. Alert triggers specify which alerts are sent to Cortex XSOAR.
+1. Click **Save** to save the alert profile.
## Configure Cortex XSOAR
-1. Navigate to **Settings > Integrations > Servers & Services**.
+1. Navigate to **Settings > Integrations > Instances**.
1. Search for **Prisma Cloud Compute**.
1. Click **Add instance** to create and configure a new integration.
-* **Name**: Name for the integration.
-* **Fetches incidents**: Configures this integration instance to fetch alerts from Prisma Cloud Compute.
-* **Prisma Cloud Compute Console URL**: URL address of your Prisma Cloud Compute console. Copy the address from the alert profile created in Prisma Cloud Compute.
-* **Prisma Cloud Compute Project Name (if applies)**: If using projects in Prisma Cloud Compute, enter the project name here. Copy the project name from the alert profile created in Prisma Cloud Compute.
-* **Trust any certificate (not secure)**: Skips verification of the CA certificate (not recommended).
-* **Use system proxy settings**: Uses the system's proxy settings.
-* **Credentials**: Prisma Cloud Compute login credentials.
-* **Prisma Cloud Compute CA Certificate**: CA Certificate used by Prisma Cloud Compute. Copy the certificate from the alert profile created in Prisma Cloud Compute.
+ * **Name**: Name for the integration.
+ * **Fetches incidents**: Configures this integration instance to fetch alerts from Prisma Cloud Compute.
+ * **Prisma Cloud Compute Console URL**: URL address of your Prisma Cloud Compute console. Copy the address from the alert profile created in Prisma Cloud Compute, or under **Runtime Security** copy the address from **System > Utilities > Path to Console**.
+ * **Prisma Cloud Compute Project Name (if applies)**: If using projects in Prisma Cloud Compute, enter the project name here. Copy the project name from the alert profile created in Prisma Cloud Compute.
+ * **Trust any certificate (not secure)**: Skips verification of the CA certificate (not recommended).
+ * **Use system proxy settings**: Uses the system's proxy settings.
+ * **Credentials**: Prisma Cloud Compute login credentials.
+ * **Prisma Cloud Compute CA Certificate**: CA Certificate used by Prisma Cloud Compute. Copy the certificate from the alert profile created in Prisma Cloud Compute.
4. Click **Test** to validate the integration.
5. Click **Done** to save the integration.
@@ -112,16 +137,16 @@ Configure Prisma Cloud Compute to send alerts to Cortex XSOAR by creating an ale
## Using the integration and scripts
The integration ships with four default playbooks:
-* Prisma Cloud Compute - Audit Alert v3
-* Prisma Cloud Compute - Cloud Discovery Alert
-* Prisma Cloud Compute - Compliance Alert
-* Prisma Cloud Compute - Vulnerability Alert
+* **Prisma Cloud Compute - Audit Alert v3**
+* **Prisma Cloud Compute - Cloud Discovery Alert**
+* **Prisma Cloud Compute - Compliance Alert**
+* **Prisma Cloud Compute - Vulnerability Alert**
-3 of the above playbooks (all except _Audit Alert v3_) contain a single script. The script in each playbook encode the raw JSON alerts into Cortex XSOAR objects that can then be used in the playbooks. The scripts are:
+Three of the above playbooks (all except _Audit Alert v3_) contain a single script. The script in each playbook encode the raw JSON alerts into Cortex XSOAR objects that can then be used in the playbooks. The scripts are:
-* PrismaCloudComputeParseComplianceAlert
-* PrismaCloudComputeParseVulnerabilityAlert
-* PrismaCloudComputeParseCloudDiscoveryAlert
+* **PrismaCloudComputeParseComplianceAlert**
+* **PrismaCloudComputeParseVulnerabilityAlert**
+* **PrismaCloudComputeParseCloudDiscoveryAlert**
To better understand how playbooks and scripts interoperate, consider the _Prisma Cloud Compute - Vulnerability Alert_ playbook.
@@ -131,7 +156,7 @@ To better understand how playbooks and scripts interoperate, consider the _Prism

-* Click **outputs** to see how the script transformed the raw JSON input into a XSOAR object.
+* Click **outputs** to see how the script transformed the raw JSON input into a Cortex XSOAR object.

@@ -139,7 +164,7 @@ To better understand how playbooks and scripts interoperate, consider the _Prism
At this point, you can add tasks that extend the playbook to check and respond to alerts depending on the properties of the Cortex XSOAR object.
### Audit Alert v3 playbook
-This playbook is not similar to the other 3 playbooks. It is a default playbook for parsing and enrichment of Prisma Cloud Compute audit alerts.
+This playbook is not similar to the other three playbooks. It is a default playbook for parsing and enrichment of Prisma Cloud Compute audit alerts.
The playbook has the following sections:
@@ -150,7 +175,7 @@ Enrichment:
- Vulnerabilities
- Compliance details
- Forensics
-- Defender logs.
+- Defender logs
Remediation:
- Block Indicators - Generic v3
diff --git a/Packs/PrismaCloudCompute/ReleaseNotes/1_6_1.md b/Packs/PrismaCloudCompute/ReleaseNotes/1_6_1.md
new file mode 100644
index 000000000000..836a4947a987
--- /dev/null
+++ b/Packs/PrismaCloudCompute/ReleaseNotes/1_6_1.md
@@ -0,0 +1,5 @@
+#### Integrations
+
+##### Palo Alto Networks - Prisma Cloud Compute
+
+Documentation and metadata improvements.
\ No newline at end of file
diff --git a/Packs/PrismaCloudCompute/pack_metadata.json b/Packs/PrismaCloudCompute/pack_metadata.json
index 70e6f4099d14..007dae804f86 100644
--- a/Packs/PrismaCloudCompute/pack_metadata.json
+++ b/Packs/PrismaCloudCompute/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "Prisma Cloud Compute by Palo Alto Networks",
"description": "Use the Prisma Cloud Compute integration to fetch incidents from your Prisma Cloud Compute environment.",
"support": "xsoar",
- "currentVersion": "1.6.0",
+ "currentVersion": "1.6.1",
"author": "Cortex XSOAR",
"url": "https://www.paloaltonetworks.com/cortex",
"email": "",
From 7f540459515d83697041de072d31fa0ec377c58a Mon Sep 17 00:00:00 2001
From: samuelFain <65926551+samuelFain@users.noreply.github.com>
Date: Fri, 23 Feb 2024 03:35:40 +0200
Subject: [PATCH 073/272] [Native Image] Update native image tag (#33080)
* Update native image tag
* Add supported modules
* Remove redundant modules
---
Tests/docker_native_image_config.json | 2 +-
1 file changed, 1 insertion(+), 1 deletion(-)
diff --git a/Tests/docker_native_image_config.json b/Tests/docker_native_image_config.json
index 471cd0dfc482..550e1ae0f836 100644
--- a/Tests/docker_native_image_config.json
+++ b/Tests/docker_native_image_config.json
@@ -31,7 +31,7 @@
"netutils",
"auth-utils"
],
- "docker_ref": "demisto/py3-native:8.6.0.88042"
+ "docker_ref": "demisto/py3-native:8.6.0.88298"
},
"native:dev":{
"supported_docker_images":[
From 045cf8cb39c8334dcfbb9030fbcb3332dc2f398e Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Sun, 25 Feb 2024 10:36:49 +0200
Subject: [PATCH 074/272] SentinelOne V2 3.2.21 (#33005) (#33057)
* Removing the labels and details from incident
* Bumped the version
* fixed the unit tests
* Bumped the docker image
* Resolving the RN conflicts
---------
Co-authored-by: munna-metron <82433049+munna-metron@users.noreply.github.com>
Co-authored-by: merit-maita <49760643+merit-maita@users.noreply.github.com>
Co-authored-by: merit-maita
---
.../Integrations/SentinelOne-V2/SentinelOne-V2.py | 3 ---
.../Integrations/SentinelOne-V2/SentinelOne-V2.yml | 2 +-
.../SentinelOne-V2/test_data/incidents_2_0.json | 4 ----
.../SentinelOne-V2/test_data/incidents_2_1.json | 8 --------
Packs/SentinelOne/ReleaseNotes/3_2_22.md | 4 ++++
Packs/SentinelOne/pack_metadata.json | 2 +-
6 files changed, 6 insertions(+), 17 deletions(-)
create mode 100644 Packs/SentinelOne/ReleaseNotes/3_2_22.md
diff --git a/Packs/SentinelOne/Integrations/SentinelOne-V2/SentinelOne-V2.py b/Packs/SentinelOne/Integrations/SentinelOne-V2/SentinelOne-V2.py
index 90314079c712..80852daba63a 100644
--- a/Packs/SentinelOne/Integrations/SentinelOne-V2/SentinelOne-V2.py
+++ b/Packs/SentinelOne/Integrations/SentinelOne-V2/SentinelOne-V2.py
@@ -3483,10 +3483,7 @@ def fetch_handler(client: Client, args):
def to_incident(type, data):
incident = {
- 'details': json.dumps(data),
'rawJSON': json.dumps(data),
- 'labels': [{'type': _type, 'value': value if isinstance(value, str) else json.dumps(value)}
- for _type, value in data.items()]
}
if type == 'Threat':
diff --git a/Packs/SentinelOne/Integrations/SentinelOne-V2/SentinelOne-V2.yml b/Packs/SentinelOne/Integrations/SentinelOne-V2/SentinelOne-V2.yml
index b3de3d701262..608476f1bbfa 100644
--- a/Packs/SentinelOne/Integrations/SentinelOne-V2/SentinelOne-V2.yml
+++ b/Packs/SentinelOne/Integrations/SentinelOne-V2/SentinelOne-V2.yml
@@ -2385,7 +2385,7 @@ script:
- contextPath: SentinelOne.Notes.UpdatedAt
description: The note updated time.
type: string
- dockerimage: demisto/python3:3.10.13.85415
+ dockerimage: demisto/python3:3.10.13.87159
isfetch: true
ismappable: true
isremotesyncin: true
diff --git a/Packs/SentinelOne/Integrations/SentinelOne-V2/test_data/incidents_2_0.json b/Packs/SentinelOne/Integrations/SentinelOne-V2/test_data/incidents_2_0.json
index 6c45f5082ceb..40e5c1da23ca 100644
--- a/Packs/SentinelOne/Integrations/SentinelOne-V2/test_data/incidents_2_0.json
+++ b/Packs/SentinelOne/Integrations/SentinelOne-V2/test_data/incidents_2_0.json
@@ -1,15 +1,11 @@
[
{
"name": "Sentinel One Threat: Malware",
- "labels":[{"type": "accountId", "value": "433241117337583618"}, {"type": "accountName", "value": "SentinelOne"}, {"type": "agentComputerName", "value": "EC2AMAZ-AJ0KANC"}, {"type": "agentDomain", "value": "WORKGROUP"}, {"type": "agentId", "value": "657613730168123595"}, {"type": "agentInfected", "value": "false"}, {"type": "agentIp", "value": "3.122.240.42"}, {"type": "agentIsActive", "value": "false"}, {"type": "agentIsDecommissioned", "value": "true"}, {"type": "agentMachineType", "value": "server"}, {"type": "agentNetworkStatus", "value": "connecting"}, {"type": "agentOsType", "value": "windows"}, {"type": "agentVersion", "value": "3.1.3.38"}, {"type": "annotation", "value": "null"}, {"type": "automaticallyResolved", "value": "false"}, {"type": "browserType", "value": "null"}, {"type": "certId", "value": ""}, {"type": "classification", "value": "Malware"}, {"type": "classificationSource", "value": "Static"}, {"type": "classifierName", "value": "STATIC"}, {"type": "cloudVerdict", "value": "black"}, {"type": "collectionId", "value": "433377870883088367"}, {"type": "commandId", "value": "null"}, {"type": "createdAt", "value": "2019-09-15T12:05:49.095889Z"}, {"type": "createdDate", "value": "2019-09-15T12:05:49.095889Z"}, {"type": "description", "value": "malware detected - not mitigated yet (static engine)"}, {"type": "engines", "value": "[\"reputation\"]"}, {"type": "external_ticket_id", "value": "null"}, {"type": "fileContentHash", "value": "3395856ce81f2b7382dee72602f798b642f14140"}, {"type": "fileCreatedDate", "value": "null"}, {"type": "fileDisplayName", "value": "Unconfirmed 123490.crdownload"}, {"type": "fileExtensionType", "value":"Unknown"}, {"type": "fileIsDotNet", "value": "null"}, {"type":"fileIsExecutable", "value": "false"}, {"type": "fileIsSystem", "value": "false"},{"type": "fileMaliciousContent", "value": "null"}, {"type": "fileObjectId","value": "88FABEEE0F7FE18E"}, {"type": "filePath", "value": "\\Device\\HarddiskVolume1\\Users\\Administrator\\Downloads\\Unconfirmed 123490.crdownload"}, {"type": "fileSha256", "value": "null"}, {"type": "fileVerificationType", "value": "NotSigned"}, {"type": "fromCloud", "value":"false"}, {"type": "fromScan", "value": "false"}, {"type": "id", "value":"715718962991148224"}, {"type": "indicators", "value": "[]"}, {"type":"initiatedBy", "value": "agentPolicy"}, {"type": "initiatedByDescription","value": "Agent Policy"}, {"type": "initiatingUserId", "value": "null"}, {"type":"isCertValid", "value": "false"}, {"type": "isInteractiveSession", "value":"false"}, {"type": "isPartialStory", "value": "false"}, {"type":"maliciousGroupId", "value": "A8F6CB4CB9AE09A1"}, {"type":"maliciousProcessArguments", "value": "null"}, {"type": "markedAsBenign", "value":"false"}, {"type": "mitigationMode", "value": "protect"}, {"type": "mitigationReport", "value": "{\"kill\": {\"status\": \"success\"}, \"network_quarantine\": {\"status\": null}, \"quarantine\": {\"status\": \"success\"}, \"remediate\": {\"status\": null}, \"rollback\": {\"status\": null}, \"unquarantine\": {\"status\": null}}"}, {"type": "mitigationStatus", "value": "mitigated"}, {"type": "publisher", "value": ""}, {"type": "rank", "value": "7"}, {"type": "resolved","value": "true"}, {"type": "siteId", "value": "475482421366727779"}, {"type": "siteName", "value": "demisto"}, {"type": "threatAgentVersion", "value":"3.1.3.38"}, {"type": "threatName", "value": "Unconfirmed 123490.crdownload"}, {"type": "updatedAt", "value": "2020-04-02T14:52:28.528753Z"}, {"type":"username", "value": "EC2AMAZ-AJ0KANC\\Administrator"}, {"type":"whiteningOptions", "value": "[\"hash\"]"}, {"type": "mirror_direction", "value": "null"}, {"type": "mirror_instance", "value": ""}, {"type": "incident_type", "value": "SentinelOne Incident"}],
- "details": "{\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIp\": \"3.122.240.42\", \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentNetworkStatus\": \"connecting\", \"agentOsType\": \"windows\", \"agentVersion\": \"3.1.3.38\", \"annotation\": null, \"automaticallyResolved\": false, \"browserType\": null, \"certId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"classifierName\": \"STATIC\", \"cloudVerdict\": \"black\", \"collectionId\": \"433377870883088367\", \"commandId\": null, \"createdAt\": \"2019-09-15T12:05:49.095889Z\", \"createdDate\": \"2019-09-15T12:05:49.095889Z\", \"description\": \"malware detected - not mitigated yet (static engine)\", \"engines\": [\"reputation\"], \"external_ticket_id\": null, \"fileContentHash\": \"3395856ce81f2b7382dee72602f798b642f14140\", \"fileCreatedDate\": null, \"fileDisplayName\": \"Unconfirmed 123490.crdownload\", \"fileExtensionType\": \"Unknown\", \"fileIsDotNet\": null, \"fileIsExecutable\": false, \"fileIsSystem\": false, \"fileMaliciousContent\": null, \"fileObjectId\": \"88FABEEE0F7FE18E\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Unconfirmed 123490.crdownload\", \"fileSha256\": null, \"fileVerificationType\": \"NotSigned\", \"fromCloud\": false, \"fromScan\": false, \"id\": \"715718962991148224\", \"indicators\": [], \"initiatedBy\": \"agentPolicy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"isCertValid\": false, \"isInteractiveSession\": false, \"isPartialStory\": false, \"maliciousGroupId\": \"A8F6CB4CB9AE09A1\", \"maliciousProcessArguments\": null, \"markedAsBenign\": false, \"mitigationMode\": \"protect\", \"mitigationReport\": {\"kill\": {\"status\": \"success\"}, \"network_quarantine\": {\"status\": null}, \"quarantine\": {\"status\": \"success\"}, \"remediate\": {\"status\": null}, \"rollback\": {\"status\": null}, \"unquarantine\": {\"status\": null}}, \"mitigationStatus\": \"mitigated\", \"publisher\": \"\", \"rank\": 7, \"resolved\": true, \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"threatAgentVersion\": \"3.1.3.38\", \"threatName\": \"Unconfirmed 123490.crdownload\", \"updatedAt\": \"2020-04-02T14:52:28.528753Z\", \"username\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"whiteningOptions\": [\"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}",
"occurred": "2019-09-15T12:05:49.095889Z",
"rawJSON": "{\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIp\": \"3.122.240.42\", \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentNetworkStatus\": \"connecting\", \"agentOsType\": \"windows\", \"agentVersion\": \"3.1.3.38\", \"annotation\": null, \"automaticallyResolved\": false, \"browserType\": null, \"certId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"classifierName\": \"STATIC\", \"cloudVerdict\": \"black\", \"collectionId\": \"433377870883088367\", \"commandId\": null, \"createdAt\": \"2019-09-15T12:05:49.095889Z\", \"createdDate\": \"2019-09-15T12:05:49.095889Z\", \"description\": \"malware detected - not mitigated yet (static engine)\", \"engines\": [\"reputation\"], \"external_ticket_id\": null, \"fileContentHash\": \"3395856ce81f2b7382dee72602f798b642f14140\", \"fileCreatedDate\": null, \"fileDisplayName\": \"Unconfirmed 123490.crdownload\", \"fileExtensionType\": \"Unknown\", \"fileIsDotNet\": null, \"fileIsExecutable\": false, \"fileIsSystem\": false, \"fileMaliciousContent\": null, \"fileObjectId\": \"88FABEEE0F7FE18E\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Unconfirmed 123490.crdownload\", \"fileSha256\": null, \"fileVerificationType\": \"NotSigned\", \"fromCloud\": false, \"fromScan\": false, \"id\": \"715718962991148224\", \"indicators\": [], \"initiatedBy\": \"agentPolicy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"isCertValid\": false, \"isInteractiveSession\": false, \"isPartialStory\": false, \"maliciousGroupId\": \"A8F6CB4CB9AE09A1\", \"maliciousProcessArguments\": null, \"markedAsBenign\": false, \"mitigationMode\": \"protect\", \"mitigationReport\": {\"kill\": {\"status\": \"success\"}, \"network_quarantine\": {\"status\": null}, \"quarantine\": {\"status\": \"success\"}, \"remediate\": {\"status\": null}, \"rollback\": {\"status\": null}, \"unquarantine\": {\"status\": null}}, \"mitigationStatus\": \"mitigated\", \"publisher\": \"\", \"rank\": 7, \"resolved\": true, \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"threatAgentVersion\": \"3.1.3.38\", \"threatName\": \"Unconfirmed 123490.crdownload\", \"updatedAt\": \"2020-04-02T14:52:28.528753Z\", \"username\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"whiteningOptions\": [\"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}"
},
{
"name": "Sentinel One Threat: Malware",
- "labels": [{"type": "accountId", "value": "43324111733712345"}, {"type": "accountName", "value": "SentinelOne"}, {"type": "agentComputerName", "value": "EC2AMAZ-AJ0KANC"}, {"type": "agentDomain", "value": "WORKGROUP"}, {"type": "agentId", "value": "657613730168123595"}, {"type": "agentInfected", "value": "false"}, {"type": "agentIp", "value": "3.122.240.42"}, {"type": "agentIsActive", "value": "false"}, {"type": "agentIsDecommissioned", "value": "true"}, {"type": "agentMachineType", "value": "server"}, {"type": "agentNetworkStatus", "value": "connecting"}, {"type": "agentOsType", "value": "windows"}, {"type": "agentVersion", "value": "3.1.3.38"}, {"type": "annotation", "value": "null"}, {"type": "automaticallyResolved", "value": "false"}, {"type": "browserType", "value": "null"}, {"type": "certId", "value": ""}, {"type": "classification", "value": "Malware"}, {"type": "classificationSource", "value": "Static"}, {"type": "classifierName", "value": "STATIC"}, {"type": "cloudVerdict", "value": "black"}, {"type": "collectionId", "value": "433377870883088367"}, {"type": "commandId", "value": "null"}, {"type": "createdAt", "value": "2019-09-15T12:14:42.440985Z"}, {"type": "createdDate", "value": "2019-09-15T12:14:42.440985Z"}, {"type": "description", "value": "malware detected - not mitigated yet (static engine)"}, {"type": "engines", "value": "[\"reputation\"]"}, {"type": "external_ticket_id", "value": "null"}, {"type": "fileContentHash", "value": "3395856ce81f2b7382dee72602f798b642f14140"}, {"type": "fileCreatedDate", "value": "null"}, {"type": "fileDisplayName", "value": "Unconfirmed 123490.crdownload"}, {"type": "fileExtensionType", "value":"Unknown"}, {"type": "fileIsDotNet", "value": "null"}, {"type":"fileIsExecutable", "value": "false"}, {"type": "fileIsSystem", "value": "false"},{"type": "fileMaliciousContent", "value": "null"}, {"type": "fileObjectId","value": "88FABEEE0F7FE18E"}, {"type": "filePath", "value": "\\Device\\HarddiskVolume1\\Users\\Administrator\\Downloads\\Unconfirmed 123490.crdownload"}, {"type": "fileSha256", "value": "null"}, {"type": "fileVerificationType", "value": "NotSigned"}, {"type": "fromCloud", "value":"false"}, {"type": "fromScan", "value": "false"}, {"type": "id", "value":"1234518962991148224"}, {"type": "indicators", "value": "[]"}, {"type":"initiatedBy", "value": "agentPolicy"}, {"type": "initiatedByDescription","value": "Agent Policy"}, {"type": "initiatingUserId", "value": "null"}, {"type":"isCertValid", "value": "false"}, {"type": "isInteractiveSession", "value":"false"}, {"type": "isPartialStory", "value": "false"}, {"type":"maliciousGroupId", "value": "A8F6CB4CB9AE09A1"}, {"type":"maliciousProcessArguments", "value": "null"}, {"type": "markedAsBenign", "value":"false"}, {"type": "mitigationMode", "value": "protect"}, {"type": "mitigationReport", "value": "{\"kill\": {\"status\": \"success\"}, \"network_quarantine\": {\"status\": null}, \"quarantine\": {\"status\": \"success\"}, \"remediate\": {\"status\": null}, \"rollback\": {\"status\": null}, \"unquarantine\": {\"status\": null}}"}, {"type": "mitigationStatus", "value": "mitigated"}, {"type": "publisher", "value": ""}, {"type": "rank", "value": "4"}, {"type": "resolved","value": "true"}, {"type": "siteId", "value": "475482421366727779"}, {"type": "siteName", "value": "demisto"}, {"type": "threatAgentVersion", "value":"3.1.3.38"}, {"type": "threatName", "value": "Unconfirmed 123490.crdownload"}, {"type": "updatedAt", "value": "2020-04-02T14:52:28.528753Z"}, {"type":"username", "value": "EC2AMAZ-AJ0KANC\\Administrator"}, {"type":"whiteningOptions", "value": "[\"hash\"]"}, {"type": "mirror_direction", "value": "null"}, {"type": "mirror_instance", "value": ""}, {"type": "incident_type", "value": "SentinelOne Incident"}],
- "details": "{\"accountId\": \"43324111733712345\", \"accountName\": \"SentinelOne\", \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIp\": \"3.122.240.42\", \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentNetworkStatus\": \"connecting\", \"agentOsType\": \"windows\", \"agentVersion\": \"3.1.3.38\", \"annotation\": null, \"automaticallyResolved\": false, \"browserType\": null, \"certId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"classifierName\": \"STATIC\", \"cloudVerdict\": \"black\", \"collectionId\": \"433377870883088367\", \"commandId\": null, \"createdAt\": \"2019-09-15T12:14:42.440985Z\", \"createdDate\": \"2019-09-15T12:14:42.440985Z\", \"description\": \"malware detected - not mitigated yet (static engine)\", \"engines\": [\"reputation\"], \"external_ticket_id\": null, \"fileContentHash\": \"3395856ce81f2b7382dee72602f798b642f14140\", \"fileCreatedDate\": null, \"fileDisplayName\": \"Unconfirmed 123490.crdownload\", \"fileExtensionType\": \"Unknown\", \"fileIsDotNet\": null, \"fileIsExecutable\": false, \"fileIsSystem\": false, \"fileMaliciousContent\": null, \"fileObjectId\": \"88FABEEE0F7FE18E\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Unconfirmed 123490.crdownload\", \"fileSha256\": null, \"fileVerificationType\": \"NotSigned\", \"fromCloud\": false, \"fromScan\": false, \"id\": \"1234518962991148224\", \"indicators\": [], \"initiatedBy\": \"agentPolicy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"isCertValid\": false, \"isInteractiveSession\": false, \"isPartialStory\": false, \"maliciousGroupId\": \"A8F6CB4CB9AE09A1\", \"maliciousProcessArguments\": null, \"markedAsBenign\": false, \"mitigationMode\": \"protect\", \"mitigationReport\": {\"kill\": {\"status\": \"success\"}, \"network_quarantine\": {\"status\": null}, \"quarantine\": {\"status\": \"success\"}, \"remediate\": {\"status\": null}, \"rollback\": {\"status\": null}, \"unquarantine\": {\"status\": null}}, \"mitigationStatus\": \"mitigated\", \"publisher\": \"\", \"rank\": 4, \"resolved\": true, \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"threatAgentVersion\": \"3.1.3.38\", \"threatName\": \"Unconfirmed 123490.crdownload\", \"updatedAt\": \"2020-04-02T14:52:28.528753Z\", \"username\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"whiteningOptions\": [\"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}",
"occurred": "2019-09-15T12:14:42.440985Z",
"rawJSON": "{\"accountId\": \"43324111733712345\", \"accountName\": \"SentinelOne\", \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIp\": \"3.122.240.42\", \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentNetworkStatus\": \"connecting\", \"agentOsType\": \"windows\", \"agentVersion\": \"3.1.3.38\", \"annotation\": null, \"automaticallyResolved\": false, \"browserType\": null, \"certId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"classifierName\": \"STATIC\", \"cloudVerdict\": \"black\", \"collectionId\": \"433377870883088367\", \"commandId\": null, \"createdAt\": \"2019-09-15T12:14:42.440985Z\", \"createdDate\": \"2019-09-15T12:14:42.440985Z\", \"description\": \"malware detected - not mitigated yet (static engine)\", \"engines\": [\"reputation\"], \"external_ticket_id\": null, \"fileContentHash\": \"3395856ce81f2b7382dee72602f798b642f14140\", \"fileCreatedDate\": null, \"fileDisplayName\": \"Unconfirmed 123490.crdownload\", \"fileExtensionType\": \"Unknown\", \"fileIsDotNet\": null, \"fileIsExecutable\": false, \"fileIsSystem\": false, \"fileMaliciousContent\": null, \"fileObjectId\": \"88FABEEE0F7FE18E\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Unconfirmed 123490.crdownload\", \"fileSha256\": null, \"fileVerificationType\": \"NotSigned\", \"fromCloud\": false, \"fromScan\": false, \"id\": \"1234518962991148224\", \"indicators\": [], \"initiatedBy\": \"agentPolicy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"isCertValid\": false, \"isInteractiveSession\": false, \"isPartialStory\": false, \"maliciousGroupId\": \"A8F6CB4CB9AE09A1\", \"maliciousProcessArguments\": null, \"markedAsBenign\": false, \"mitigationMode\": \"protect\", \"mitigationReport\": {\"kill\": {\"status\": \"success\"}, \"network_quarantine\": {\"status\": null}, \"quarantine\": {\"status\": \"success\"}, \"remediate\": {\"status\": null}, \"rollback\": {\"status\": null}, \"unquarantine\": {\"status\": null}}, \"mitigationStatus\": \"mitigated\", \"publisher\": \"\", \"rank\": 4, \"resolved\": true, \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"threatAgentVersion\": \"3.1.3.38\", \"threatName\": \"Unconfirmed 123490.crdownload\", \"updatedAt\": \"2020-04-02T14:52:28.528753Z\", \"username\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"whiteningOptions\": [\"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}"
}
diff --git a/Packs/SentinelOne/Integrations/SentinelOne-V2/test_data/incidents_2_1.json b/Packs/SentinelOne/Integrations/SentinelOne-V2/test_data/incidents_2_1.json
index 1f82fac5ad38..d77f58b9f266 100644
--- a/Packs/SentinelOne/Integrations/SentinelOne-V2/test_data/incidents_2_1.json
+++ b/Packs/SentinelOne/Integrations/SentinelOne-V2/test_data/incidents_2_1.json
@@ -1,29 +1,21 @@
[
{
"name": "Sentinel One Threat: Malware",
- "labels": [{"type": "agentDetectionInfo", "value": "{\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}"}, {"type": "agentRealtimeInfo", "value": "{\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}"}, {"type": "containerInfo", "value": "{\"id\": null, \"image\": null, \"labels\": null, \"name\": null}"}, {"type": "id", "value": "715718962991148224"}, {"type": "indicators", "value": "[]"}, {"type": "kubernetesInfo", "value": "{\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}"}, {"type": "mitigationStatus", "value": "[{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:05:49.228950Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:05:49.339327Z\", \"latestReport\": null, \"status\": \"success\"}]"}, {"type": "threatInfo", "value": "{\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"black\", \"collectionId\": \"433377870883088367\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:05:49.095889Z\", \"detectionType\": \"static\", \"engines\": [\"Reputation\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"CRDOWNLOAD\", \"fileExtensionType\": \"Unknown\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Unconfirmed 123490.crdownload\", \"fileSize\": 0, \"fileVerificationType\": \"NotSigned\", \"identifiedAt\": \"2019-09-15T12:05:49.009000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": false, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"publisherName\": \"\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"3395856ce81f2b7382dee72602f798b642f14140\", \"sha256\": null, \"storyline\": \"A8F6CB4CB9AE09A1\", \"threatId\": \"715718962991148224\", \"threatName\": \"Unconfirmed 123490.crdownload\", \"updatedAt\": \"2020-04-02T14:52:28.528753Z\"}"}, {"type": "whiteningOptions", "value": "[\"hash\"]"}, {"type": "mirror_direction", "value": "null"}, {"type": "mirror_instance", "value": ""}, {"type": "incident_type", "value": "SentinelOne Incident"}],
- "details": "{\"agentDetectionInfo\": {\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}, \"agentRealtimeInfo\": {\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}, \"containerInfo\": {\"id\": null, \"image\": null, \"labels\": null, \"name\": null}, \"id\": \"715718962991148224\", \"indicators\": [], \"kubernetesInfo\": {\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}, \"mitigationStatus\": [{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:05:49.228950Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:05:49.339327Z\", \"latestReport\": null, \"status\": \"success\"}], \"threatInfo\": {\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"black\", \"collectionId\": \"433377870883088367\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:05:49.095889Z\", \"detectionType\": \"static\", \"engines\": [\"Reputation\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"CRDOWNLOAD\", \"fileExtensionType\": \"Unknown\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Unconfirmed 123490.crdownload\", \"fileSize\": 0, \"fileVerificationType\": \"NotSigned\", \"identifiedAt\": \"2019-09-15T12:05:49.009000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": false, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"publisherName\": \"\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"3395856ce81f2b7382dee72602f798b642f14140\", \"sha256\": null, \"storyline\": \"A8F6CB4CB9AE09A1\", \"threatId\": \"715718962991148224\", \"threatName\": \"Unconfirmed 123490.crdownload\", \"updatedAt\": \"2020-04-02T14:52:28.528753Z\"}, \"whiteningOptions\": [\"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}",
"occurred": "2019-09-15T12:05:49.095889Z",
"rawJSON": "{\"agentDetectionInfo\": {\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}, \"agentRealtimeInfo\": {\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}, \"containerInfo\": {\"id\": null, \"image\": null, \"labels\": null, \"name\": null}, \"id\": \"715718962991148224\", \"indicators\": [], \"kubernetesInfo\": {\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}, \"mitigationStatus\": [{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:05:49.228950Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:05:49.339327Z\", \"latestReport\": null, \"status\": \"success\"}], \"threatInfo\": {\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"black\", \"collectionId\": \"433377870883088367\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:05:49.095889Z\", \"detectionType\": \"static\", \"engines\": [\"Reputation\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"CRDOWNLOAD\", \"fileExtensionType\": \"Unknown\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Unconfirmed 123490.crdownload\", \"fileSize\": 0, \"fileVerificationType\": \"NotSigned\", \"identifiedAt\": \"2019-09-15T12:05:49.009000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": false, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"publisherName\": \"\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"3395856ce81f2b7382dee72602f798b642f14140\", \"sha256\": null, \"storyline\": \"A8F6CB4CB9AE09A1\", \"threatId\": \"715718962991148224\", \"threatName\": \"Unconfirmed 123490.crdownload\", \"updatedAt\": \"2020-04-02T14:52:28.528753Z\"}, \"whiteningOptions\": [\"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}"
},
{
"name": "Sentinel One Threat: Malware",
- "labels": [{"type": "agentDetectionInfo", "value": "{\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}"}, {"type": "agentRealtimeInfo", "value": "{\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}"}, {"type": "containerInfo", "value": "{\"id\": null, \"image\": null, \"labels\": null, \"name\": null}"}, {"type": "id", "value": "715723437013282014"}, {"type": "indicators", "value": "[{\"category\": \"General\", \"description\": \"This is an AutoIT script compiled to an exe file.\", \"ids\": [25], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports functions used to raise kernel exceptions.\", \"ids\": [24], \"tactics\": []}, {\"category\": \"InfoStealer\", \"description\": \"This binary has keylogging capabilities.\", \"ids\": [23], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports debugger functions.\", \"ids\": [6], \"tactics\": []}]"}, {"type": "kubernetesInfo", "value": "{\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}"}, {"type": "mitigationStatus", "value": "[{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:42.631216Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:42.977017Z\", \"latestReport\": null, \"status\": \"success\"}]"}, {"type": "threatInfo", "value": "{\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"CHIP DIGITAL GMBH\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"provider_unknown\", \"collectionId\": \"715723437055225055\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:14:42.440985Z\", \"detectionType\": \"static\", \"engines\": [\"On-Write DFI\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"EXE\", \"fileExtensionType\": \"Executable\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Ncat Netcat Portable - CHIP-Installer.exe\", \"fileSize\": 0, \"fileVerificationType\": \"SignedVerified\", \"identifiedAt\": \"2019-09-15T12:14:41.260000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": true, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"publisherName\": \"CHIP DIGITAL GMBH\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"d8757a0396d05a1d532422827a70a7966c361366\", \"sha256\": null, \"storyline\": \"8BF4207AFA583317\", \"threatId\": \"715723437013282014\", \"threatName\": \"Ncat Netcat Portable - CHIP-Installer.exe\", \"updatedAt\": \"2020-04-02T14:52:28.534110Z\"}"}, {"type": "whiteningOptions", "value": "[\"path\", \"certificate\", \"hash\"]"}, {"type": "mirror_direction", "value": "null"}, {"type": "mirror_instance", "value": ""}, {"type": "incident_type", "value": "SentinelOne Incident"}],
- "details": "{\"agentDetectionInfo\": {\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}, \"agentRealtimeInfo\": {\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}, \"containerInfo\": {\"id\": null, \"image\": null, \"labels\": null, \"name\": null}, \"id\": \"715723437013282014\", \"indicators\": [{\"category\": \"General\", \"description\": \"This is an AutoIT script compiled to an exe file.\", \"ids\": [25], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports functions used to raise kernel exceptions.\", \"ids\": [24], \"tactics\": []}, {\"category\": \"InfoStealer\", \"description\": \"This binary has keylogging capabilities.\", \"ids\": [23], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports debugger functions.\", \"ids\": [6], \"tactics\": []}], \"kubernetesInfo\": {\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}, \"mitigationStatus\": [{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:42.631216Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:42.977017Z\", \"latestReport\": null, \"status\": \"success\"}], \"threatInfo\": {\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"CHIP DIGITAL GMBH\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"provider_unknown\", \"collectionId\": \"715723437055225055\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:14:42.440985Z\", \"detectionType\": \"static\", \"engines\": [\"On-Write DFI\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"EXE\", \"fileExtensionType\": \"Executable\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Ncat Netcat Portable - CHIP-Installer.exe\", \"fileSize\": 0, \"fileVerificationType\": \"SignedVerified\", \"identifiedAt\": \"2019-09-15T12:14:41.260000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": true, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"publisherName\": \"CHIP DIGITAL GMBH\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"d8757a0396d05a1d532422827a70a7966c361366\", \"sha256\": null, \"storyline\": \"8BF4207AFA583317\", \"threatId\": \"715723437013282014\", \"threatName\": \"Ncat Netcat Portable - CHIP-Installer.exe\", \"updatedAt\": \"2020-04-02T14:52:28.534110Z\"}, \"whiteningOptions\": [\"path\", \"certificate\", \"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}",
"occurred": "2019-09-15T12:14:42.440985Z",
"rawJSON": "{\"agentDetectionInfo\": {\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}, \"agentRealtimeInfo\": {\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}, \"containerInfo\": {\"id\": null, \"image\": null, \"labels\": null, \"name\": null}, \"id\": \"715723437013282014\", \"indicators\": [{\"category\": \"General\", \"description\": \"This is an AutoIT script compiled to an exe file.\", \"ids\": [25], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports functions used to raise kernel exceptions.\", \"ids\": [24], \"tactics\": []}, {\"category\": \"InfoStealer\", \"description\": \"This binary has keylogging capabilities.\", \"ids\": [23], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports debugger functions.\", \"ids\": [6], \"tactics\": []}], \"kubernetesInfo\": {\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}, \"mitigationStatus\": [{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:42.631216Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:42.977017Z\", \"latestReport\": null, \"status\": \"success\"}], \"threatInfo\": {\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"CHIP DIGITAL GMBH\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"provider_unknown\", \"collectionId\": \"715723437055225055\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:14:42.440985Z\", \"detectionType\": \"static\", \"engines\": [\"On-Write DFI\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"EXE\", \"fileExtensionType\": \"Executable\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Ncat Netcat Portable - CHIP-Installer.exe\", \"fileSize\": 0, \"fileVerificationType\": \"SignedVerified\", \"identifiedAt\": \"2019-09-15T12:14:41.260000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": true, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"publisherName\": \"CHIP DIGITAL GMBH\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"d8757a0396d05a1d532422827a70a7966c361366\", \"sha256\": null, \"storyline\": \"8BF4207AFA583317\", \"threatId\": \"715723437013282014\", \"threatName\": \"Ncat Netcat Portable - CHIP-Installer.exe\", \"updatedAt\": \"2020-04-02T14:52:28.534110Z\"}, \"whiteningOptions\": [\"path\", \"certificate\", \"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}"
},
{
"name": "Sentinel One Threat: Malware",
- "labels": [{"type": "agentDetectionInfo", "value": "{\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}"}, {"type": "agentRealtimeInfo", "value": "{\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}"}, {"type": "containerInfo", "value": "{\"id\": null, \"image\": null, \"labels\": null, \"name\": null}"}, {"type": "id", "value": "715723444638526700"}, {"type": "indicators", "value": "[{\"category\": \"General\", \"description\": \"This is an AutoIT script compiled to an exe file.\", \"ids\": [25], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports functions used to raise kernel exceptions.\", \"ids\": [24], \"tactics\": []}, {\"category\": \"InfoStealer\", \"description\": \"This binary has keylogging capabilities.\", \"ids\": [23], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports debugger functions.\", \"ids\": [6], \"tactics\": []}]"}, {"type": "kubernetesInfo", "value": "{\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}"}, {"type": "mitigationStatus", "value": "[{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:43.507091Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:43.787095Z\", \"latestReport\": null, \"status\": \"success\"}]"}, {"type": "threatInfo", "value": "{\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"provider_unknown\", \"collectionId\": \"715723437055225055\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:14:43.349807Z\", \"detectionType\": \"static\", \"engines\": [\"On-Write DFI\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"EXE\", \"fileExtensionType\": \"Executable\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Ncat Netcat Portable - CHIP-Installer.exe\", \"fileSize\": 0, \"fileVerificationType\": \"PathNotFound\", \"identifiedAt\": \"2019-09-15T12:14:41.620000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": false, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"\", \"publisherName\": \"\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"d8757a0396d05a1d532422827a70a7966c361366\", \"sha256\": null, \"storyline\": \"3E41618589D5CB3E\", \"threatId\": \"715723444638526700\", \"threatName\": \"Ncat Netcat Portable - CHIP-Installer.exe\", \"updatedAt\": \"2020-04-02T14:52:28.535860Z\"}"}, {"type": "whiteningOptions", "value": "[\"path\", \"hash\"]"}, {"type": "mirror_direction", "value": "null"}, {"type": "mirror_instance", "value": ""}, {"type": "incident_type", "value": "SentinelOne Incident"}],
- "details": "{\"agentDetectionInfo\": {\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}, \"agentRealtimeInfo\": {\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}, \"containerInfo\": {\"id\": null, \"image\": null, \"labels\": null, \"name\": null}, \"id\": \"715723444638526700\", \"indicators\": [{\"category\": \"General\", \"description\": \"This is an AutoIT script compiled to an exe file.\", \"ids\": [25], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports functions used to raise kernel exceptions.\", \"ids\": [24], \"tactics\": []}, {\"category\": \"InfoStealer\", \"description\": \"This binary has keylogging capabilities.\", \"ids\": [23], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports debugger functions.\", \"ids\": [6], \"tactics\": []}], \"kubernetesInfo\": {\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}, \"mitigationStatus\": [{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:43.507091Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:43.787095Z\", \"latestReport\": null, \"status\": \"success\"}], \"threatInfo\": {\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"provider_unknown\", \"collectionId\": \"715723437055225055\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:14:43.349807Z\", \"detectionType\": \"static\", \"engines\": [\"On-Write DFI\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"EXE\", \"fileExtensionType\": \"Executable\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Ncat Netcat Portable - CHIP-Installer.exe\", \"fileSize\": 0, \"fileVerificationType\": \"PathNotFound\", \"identifiedAt\": \"2019-09-15T12:14:41.620000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": false, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"\", \"publisherName\": \"\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"d8757a0396d05a1d532422827a70a7966c361366\", \"sha256\": null, \"storyline\": \"3E41618589D5CB3E\", \"threatId\": \"715723444638526700\", \"threatName\": \"Ncat Netcat Portable - CHIP-Installer.exe\", \"updatedAt\": \"2020-04-02T14:52:28.535860Z\"}, \"whiteningOptions\": [\"path\", \"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}",
"occurred": "2019-09-15T12:14:43.349807Z",
"rawJSON": "{\"agentDetectionInfo\": {\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}, \"agentRealtimeInfo\": {\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}, \"containerInfo\": {\"id\": null, \"image\": null, \"labels\": null, \"name\": null}, \"id\": \"715723444638526700\", \"indicators\": [{\"category\": \"General\", \"description\": \"This is an AutoIT script compiled to an exe file.\", \"ids\": [25], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports functions used to raise kernel exceptions.\", \"ids\": [24], \"tactics\": []}, {\"category\": \"InfoStealer\", \"description\": \"This binary has keylogging capabilities.\", \"ids\": [23], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports debugger functions.\", \"ids\": [6], \"tactics\": []}], \"kubernetesInfo\": {\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}, \"mitigationStatus\": [{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:43.507091Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:43.787095Z\", \"latestReport\": null, \"status\": \"success\"}], \"threatInfo\": {\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"provider_unknown\", \"collectionId\": \"715723437055225055\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:14:43.349807Z\", \"detectionType\": \"static\", \"engines\": [\"On-Write DFI\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"EXE\", \"fileExtensionType\": \"Executable\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Ncat Netcat Portable - CHIP-Installer.exe\", \"fileSize\": 0, \"fileVerificationType\": \"PathNotFound\", \"identifiedAt\": \"2019-09-15T12:14:41.620000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": false, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"\", \"publisherName\": \"\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"d8757a0396d05a1d532422827a70a7966c361366\", \"sha256\": null, \"storyline\": \"3E41618589D5CB3E\", \"threatId\": \"715723444638526700\", \"threatName\": \"Ncat Netcat Portable - CHIP-Installer.exe\", \"updatedAt\": \"2020-04-02T14:52:28.535860Z\"}, \"whiteningOptions\": [\"path\", \"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}"
},
{
"name": "Sentinel One Threat: Malware",
- "labels": [{"type": "agentDetectionInfo", "value": "{\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}"}, {"type": "agentRealtimeInfo", "value": "{\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}"}, {"type": "containerInfo", "value": "{\"id\": null, \"image\": null, \"labels\": null, \"name\": null}"}, {"type": "id", "value": "715723450678324472"}, {"type": "indicators", "value": "[{\"category\": \"General\", \"description\": \"This is an AutoIT script compiled to an exe file.\", \"ids\": [25], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports functions used to raise kernel exceptions.\", \"ids\": [24], \"tactics\": []}, {\"category\": \"InfoStealer\", \"description\": \"This binary has keylogging capabilities.\", \"ids\": [23], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports debugger functions.\", \"ids\": [6], \"tactics\": []}]"}, {"type": "kubernetesInfo", "value": "{\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}"}, {"type": "mitigationStatus", "value": "[{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:44.336124Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:44.469734Z\", \"latestReport\": null, \"status\": \"success\"}]"}, {"type": "threatInfo", "value": "{\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"CHIP DIGITAL GMBH\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"provider_unknown\", \"collectionId\": \"715723450695101689\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:14:44.069617Z\", \"detectionType\": \"static\", \"engines\": [\"On-Write DFI\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"EXE\", \"fileExtensionType\": \"Executable\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Ncat Netcat Portable - CHIP-Installer (1).exe\", \"fileSize\": 0, \"fileVerificationType\": \"SignedVerified\", \"identifiedAt\": \"2019-09-15T12:14:43.215000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": true, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"publisherName\": \"CHIP DIGITAL GMBH\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"ccce727e39cb8d955a323bf2c0419f31fb917e5a\", \"sha256\": null, \"storyline\": \"5F18360CAB4D45B7\", \"threatId\": \"715723450678324472\", \"threatName\": \"Ncat Netcat Portable - CHIP-Installer (1).exe\", \"updatedAt\": \"2020-04-02T14:52:28.537685Z\"}"}, {"type": "whiteningOptions", "value": "[\"path\", \"certificate\", \"hash\"]"}, {"type": "mirror_direction", "value": "null"}, {"type": "mirror_instance", "value": ""}, {"type": "incident_type", "value": "SentinelOne Incident"}],
- "details": "{\"agentDetectionInfo\": {\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}, \"agentRealtimeInfo\": {\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}, \"containerInfo\": {\"id\": null, \"image\": null, \"labels\": null, \"name\": null}, \"id\": \"715723450678324472\", \"indicators\": [{\"category\": \"General\", \"description\": \"This is an AutoIT script compiled to an exe file.\", \"ids\": [25], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports functions used to raise kernel exceptions.\", \"ids\": [24], \"tactics\": []}, {\"category\": \"InfoStealer\", \"description\": \"This binary has keylogging capabilities.\", \"ids\": [23], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports debugger functions.\", \"ids\": [6], \"tactics\": []}], \"kubernetesInfo\": {\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}, \"mitigationStatus\": [{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:44.336124Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:44.469734Z\", \"latestReport\": null, \"status\": \"success\"}], \"threatInfo\": {\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"CHIP DIGITAL GMBH\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"provider_unknown\", \"collectionId\": \"715723450695101689\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:14:44.069617Z\", \"detectionType\": \"static\", \"engines\": [\"On-Write DFI\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"EXE\", \"fileExtensionType\": \"Executable\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Ncat Netcat Portable - CHIP-Installer (1).exe\", \"fileSize\": 0, \"fileVerificationType\": \"SignedVerified\", \"identifiedAt\": \"2019-09-15T12:14:43.215000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": true, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"publisherName\": \"CHIP DIGITAL GMBH\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"ccce727e39cb8d955a323bf2c0419f31fb917e5a\", \"sha256\": null, \"storyline\": \"5F18360CAB4D45B7\", \"threatId\": \"715723450678324472\", \"threatName\": \"Ncat Netcat Portable - CHIP-Installer (1).exe\", \"updatedAt\": \"2020-04-02T14:52:28.537685Z\"}, \"whiteningOptions\": [\"path\", \"certificate\", \"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}",
"occurred": "2019-09-15T12:14:44.069617Z",
"rawJSON": "{\"agentDetectionInfo\": {\"accountId\": null, \"accountName\": null, \"agentDomain\": null, \"agentIpV4\": null, \"agentIpV6\": null, \"agentLastLoggedInUserName\": null, \"agentMitigationMode\": \"protect\", \"agentOsName\": null, \"agentOsRevision\": null, \"agentRegisteredAt\": null, \"agentUuid\": null, \"agentVersion\": \"3.1.3.38\", \"externalIp\": null, \"groupId\": null, \"groupName\": null, \"siteId\": null, \"siteName\": null}, \"agentRealtimeInfo\": {\"accountId\": \"433241117337583618\", \"accountName\": \"SentinelOne\", \"activeThreats\": 0, \"agentComputerName\": \"EC2AMAZ-AJ0KANC\", \"agentDecommissionedAt\": true, \"agentDomain\": \"WORKGROUP\", \"agentId\": \"657613730168123595\", \"agentInfected\": false, \"agentIsActive\": false, \"agentIsDecommissioned\": true, \"agentMachineType\": \"server\", \"agentMitigationMode\": \"protect\", \"agentNetworkStatus\": \"connecting\", \"agentOsName\": \"Windows Server 2016\", \"agentOsRevision\": \"14393\", \"agentOsType\": \"windows\", \"agentUuid\": \"f431b0a1a8744d2a8a92fc88fa3c13bc\", \"agentVersion\": \"3.1.3.38\", \"groupId\": \"475482421375116388\", \"groupName\": \"Default Group\", \"networkInterfaces\": [{\"id\": \"657613730176512204\", \"inet\": [\"8.8.8.8\"], \"inet6\": [\"fe80::1da3:1ca8:b311:af32\"], \"name\": \"Ethernet 2\", \"physical\": \"06:35:e6:62:53:2e\"}], \"operationalState\": \"na\", \"rebootRequired\": false, \"scanAbortedAt\": null, \"scanFinishedAt\": \"2019-06-30T15:34:52.505374Z\", \"scanStartedAt\": \"2019-06-30T15:01:17.500397Z\", \"scanStatus\": \"finished\", \"siteId\": \"475482421366727779\", \"siteName\": \"demisto\", \"userActionsNeeded\": []}, \"containerInfo\": {\"id\": null, \"image\": null, \"labels\": null, \"name\": null}, \"id\": \"715723450678324472\", \"indicators\": [{\"category\": \"General\", \"description\": \"This is an AutoIT script compiled to an exe file.\", \"ids\": [25], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports functions used to raise kernel exceptions.\", \"ids\": [24], \"tactics\": []}, {\"category\": \"InfoStealer\", \"description\": \"This binary has keylogging capabilities.\", \"ids\": [23], \"tactics\": []}, {\"category\": \"General\", \"description\": \"This binary imports debugger functions.\", \"ids\": [6], \"tactics\": []}], \"kubernetesInfo\": {\"cluster\": null, \"controllerKind\": null, \"controllerLabels\": null, \"controllerName\": null, \"namespace\": null, \"namespaceLabels\": null, \"node\": null, \"pod\": null, \"podLabels\": null}, \"mitigationStatus\": [{\"action\": \"kill\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:44.336124Z\", \"latestReport\": null, \"status\": \"success\"}, {\"action\": \"quarantine\", \"actionsCounters\": null, \"groupNotFound\": false, \"lastUpdate\": \"2019-09-15T12:14:44.469734Z\", \"latestReport\": null, \"status\": \"success\"}], \"threatInfo\": {\"analystVerdict\": \"undefined\", \"analystVerdictDescription\": \"Undefined\", \"automaticallyResolved\": false, \"browserType\": null, \"certificateId\": \"CHIP DIGITAL GMBH\", \"classification\": \"Malware\", \"classificationSource\": \"Static\", \"cloudFilesHashVerdict\": \"provider_unknown\", \"collectionId\": \"715723450695101689\", \"confidenceLevel\": \"malicious\", \"createdAt\": \"2019-09-15T12:14:44.069617Z\", \"detectionType\": \"static\", \"engines\": [\"On-Write DFI\"], \"externalTicketExists\": false, \"externalTicketId\": null, \"failedActions\": false, \"fileExtension\": \"EXE\", \"fileExtensionType\": \"Executable\", \"filePath\": \"\\\\Device\\\\HarddiskVolume1\\\\Users\\\\Administrator\\\\Downloads\\\\Ncat Netcat Portable - CHIP-Installer (1).exe\", \"fileSize\": 0, \"fileVerificationType\": \"SignedVerified\", \"identifiedAt\": \"2019-09-15T12:14:43.215000Z\", \"incidentStatus\": \"resolved\", \"incidentStatusDescription\": \"Resolved\", \"initiatedBy\": \"agent_policy\", \"initiatedByDescription\": \"Agent Policy\", \"initiatingUserId\": null, \"initiatingUsername\": null, \"isFileless\": false, \"isValidCertificate\": true, \"maliciousProcessArguments\": null, \"md5\": null, \"mitigatedPreemptively\": false, \"mitigationStatus\": \"mitigated\", \"mitigationStatusDescription\": \"Mitigated\", \"originatorProcess\": null, \"pendingActions\": false, \"processUser\": \"EC2AMAZ-AJ0KANC\\\\Administrator\", \"publisherName\": \"CHIP DIGITAL GMBH\", \"reachedEventsLimit\": false, \"rebootRequired\": false, \"sha1\": \"ccce727e39cb8d955a323bf2c0419f31fb917e5a\", \"sha256\": null, \"storyline\": \"5F18360CAB4D45B7\", \"threatId\": \"715723450678324472\", \"threatName\": \"Ncat Netcat Portable - CHIP-Installer (1).exe\", \"updatedAt\": \"2020-04-02T14:52:28.537685Z\"}, \"whiteningOptions\": [\"path\", \"certificate\", \"hash\"], \"mirror_direction\": null, \"mirror_instance\": \"\", \"incident_type\": \"SentinelOne Incident\"}"
}
diff --git a/Packs/SentinelOne/ReleaseNotes/3_2_22.md b/Packs/SentinelOne/ReleaseNotes/3_2_22.md
new file mode 100644
index 000000000000..829f13f4b195
--- /dev/null
+++ b/Packs/SentinelOne/ReleaseNotes/3_2_22.md
@@ -0,0 +1,4 @@
+#### Integrations
+##### SentinelOne v2
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
+- Updated the incident context data by removing the both details and labels.
diff --git a/Packs/SentinelOne/pack_metadata.json b/Packs/SentinelOne/pack_metadata.json
index f3ecb46894a6..227b88c6e7ac 100644
--- a/Packs/SentinelOne/pack_metadata.json
+++ b/Packs/SentinelOne/pack_metadata.json
@@ -2,7 +2,7 @@
"name": "SentinelOne",
"description": "Endpoint protection",
"support": "partner",
- "currentVersion": "3.2.21",
+ "currentVersion": "3.2.22",
"author": "SentinelOne",
"url": "https://www.sentinelone.com/support/",
"email": "support@sentinelone.com",
From b2ec6f4cc6dcfe029cd6cbcc6a15b4b15aa1e39a Mon Sep 17 00:00:00 2001
From: Moshe Eichler <78307768+MosheEichler@users.noreply.github.com>
Date: Sun, 25 Feb 2024 12:53:05 +0200
Subject: [PATCH 075/272] Exclude nightly ok in contribution PRs (#33087)
* Exclude nightly ok in contrib PRs
* change name
* space
* more space
---
...eck-nightly-ok-label.yml => check-nightly-ok-label.yml} | 7 ++++---
1 file changed, 4 insertions(+), 3 deletions(-)
rename .github/workflows/{ckeck-nightly-ok-label.yml => check-nightly-ok-label.yml} (85%)
diff --git a/.github/workflows/ckeck-nightly-ok-label.yml b/.github/workflows/check-nightly-ok-label.yml
similarity index 85%
rename from .github/workflows/ckeck-nightly-ok-label.yml
rename to .github/workflows/check-nightly-ok-label.yml
index 70959ad08eac..f2a52c95c594 100644
--- a/.github/workflows/ckeck-nightly-ok-label.yml
+++ b/.github/workflows/check-nightly-ok-label.yml
@@ -7,6 +7,7 @@ on:
jobs:
check_label:
runs-on: ubuntu-latest
+ if: github.repository == 'demisto/content' && github.event.pull_request.head.repo.fork == false
steps:
- name: Checkout repo
@@ -21,12 +22,12 @@ jobs:
echo "All changed files:"
echo "${CHANGED_FILES}"
GITLAB_CHANGED_FILES=$( [[ $CHANGED_FILES == *".gitlab/ci"* ]] && echo true || echo false)
- echo "Files in the.gitlab folder have changed: ${GITLAB_CHANGED_FILES}"
+ echo "Files in the .gitlab folder have changed: ${GITLAB_CHANGED_FILES}"
echo "gitlab_changed_files=$GITLAB_CHANGED_FILES" >> $GITHUB_OUTPUT
if [[ $GITLAB_CHANGED_FILES == true ]]; then
echo 'Files under .gitlab folder has changed, Will check if the PR has the `nightly-ok` label.'
else
- echo 'Files in the.gitlab folder have not been changed.'
+ echo 'Files in the .gitlab folder have not been changed.'
fi
- name: Check if PR has the nightly-ok label
@@ -46,5 +47,5 @@ jobs:
process.exit(1); // Exit with failure status if label is missing
}
} else {
- console.log('Files in the.gitlab folder have not been changed.');
+ console.log('Files in the .gitlab folder have not been changed.');
}
From 57e6a1d7a10dbe8da8ff975b3dc39228a839a936 Mon Sep 17 00:00:00 2001
From: content-bot <55035720+content-bot@users.noreply.github.com>
Date: Sun, 25 Feb 2024 13:53:19 +0200
Subject: [PATCH 076/272] [Marketplace Contribution] XSOAR File Management -
Content Pack Update (#32961) (#33086)
* "contribution update to pack "XSOAR File Management""
* Update Packs/XSOARFileManagement/Integrations/XSOARFileManagement/XSOARFileManagement.py
* Update Packs/XSOARFileManagement/ReleaseNotes/1_1_0.md
* Update Packs/XSOARFileManagement/ReleaseNotes/1_1_0.md
---------
Co-authored-by: xsoar-bot <67315154+xsoar-bot@users.noreply.github.com>
Co-authored-by: amontminypa <118302525+amontminypa@users.noreply.github.com>
Co-authored-by: JudithB <132264628+jbabazadeh@users.noreply.github.com>
---
.../XSOARFileManagement/XSOARFileManagement.py | 16 +++++++++++-----
.../XSOARFileManagement/XSOARFileManagement.yml | 8 +++++++-
Packs/XSOARFileManagement/ReleaseNotes/1_1_0.md | 9 +++++++++
Packs/XSOARFileManagement/pack_metadata.json | 12 ++++++++----
4 files changed, 35 insertions(+), 10 deletions(-)
create mode 100644 Packs/XSOARFileManagement/ReleaseNotes/1_1_0.md
diff --git a/Packs/XSOARFileManagement/Integrations/XSOARFileManagement/XSOARFileManagement.py b/Packs/XSOARFileManagement/Integrations/XSOARFileManagement/XSOARFileManagement.py
index 010fd0c2eeb4..63721ac4359f 100644
--- a/Packs/XSOARFileManagement/Integrations/XSOARFileManagement/XSOARFileManagement.py
+++ b/Packs/XSOARFileManagement/Integrations/XSOARFileManagement/XSOARFileManagement.py
@@ -1,5 +1,7 @@
import demistomock as demisto # noqa: F401
from CommonServerPython import * # noqa: F401
+
+
import re
import time
from typing import Tuple
@@ -63,7 +65,7 @@ def delete_context(self, incident_id: str, key_to_delete: str):
)
return response
- def delete_file(self, entry_id: str, delete_artifact=True):
+ def delete_file(self, incident_id, entry_id: str, delete_artifact=True):
"""Delete file by entry ID
Arguments:
client: (Client) The client class.
@@ -74,7 +76,9 @@ def delete_file(self, entry_id: str, delete_artifact=True):
"""
body_content = {
"id": entry_id,
- "deleteArtifact": delete_artifact
+ "deleteArtifact": delete_artifact,
+ "version": 0,
+ "investigationId": incident_id
}
response = self._http_request(
method='POST',
@@ -297,13 +301,13 @@ def delete_attachment_command(client: Client, args: dict) -> CommandResults:
def delete_file(client: Client, entry_id: str):
files = demisto.context().get('File', [])
files = [files] if not isinstance(files, list) else files
+ incident_id = get_incident_id(entry_id)
# delete old file
try:
- client.delete_file(entry_id)
+ client.delete_file(incident_id, entry_id)
except DemistoException as error:
return_error(f"File already deleted or not found !\n{str(error)}")
# output
- incident_id = get_incident_id(entry_id)
client.delete_context(incident_id, "File")
time.sleep(1) # to let the API execute the request
new_files = [file for file in files if file.get("EntryID") != entry_id]
@@ -432,6 +436,7 @@ def main() -> None:
command = demisto.command()
api_key = demisto.get(demisto.params(), 'creds_apikey.password')
+ api_key_id = demisto.params().get("creds_apikey_id", {}).get("password")
server_url = demisto.demistoUrls()["server"]
base_url = params.get('url', server_url)
verify_certificate = not params.get('insecure', False)
@@ -439,7 +444,8 @@ def main() -> None:
try:
headers = {
- 'Authorization': api_key
+ 'Authorization': api_key,
+ 'x-xdr-auth-id': api_key_id
}
client = Client(
base_url=base_url,
diff --git a/Packs/XSOARFileManagement/Integrations/XSOARFileManagement/XSOARFileManagement.yml b/Packs/XSOARFileManagement/Integrations/XSOARFileManagement/XSOARFileManagement.yml
index 6141652c57d9..45b6f7823332 100644
--- a/Packs/XSOARFileManagement/Integrations/XSOARFileManagement/XSOARFileManagement.yml
+++ b/Packs/XSOARFileManagement/Integrations/XSOARFileManagement/XSOARFileManagement.yml
@@ -22,6 +22,12 @@ configuration:
name: proxy
type: 8
required: false
+- display: ''
+ displaypassword: XSOAR Server API Key ID
+ hiddenusername: true
+ name: creds_apikey_id
+ required: false
+ type: 9
description: This integration uses the XSOAR API to perform basic but essentials actions on files.
display: XSOAR File Management
name: XSOAR File Management
@@ -85,7 +91,7 @@ script:
required: true
description: 'Rename a file. Warning: use this only if necessary, it''s HEAVY to run, this will delete and recreate the file with another name.'
name: file-management-rename-file
- dockerimage: demisto/python3:3.10.13.78960
+ dockerimage: demisto/python3:3.10.13.87159
runonce: false
script: ''
subtype: python3
diff --git a/Packs/XSOARFileManagement/ReleaseNotes/1_1_0.md b/Packs/XSOARFileManagement/ReleaseNotes/1_1_0.md
new file mode 100644
index 000000000000..bbbef95b275f
--- /dev/null
+++ b/Packs/XSOARFileManagement/ReleaseNotes/1_1_0.md
@@ -0,0 +1,9 @@
+
+#### Integrations
+
+##### XSOAR File Management
+
+- Added an additional parameter **XSOAR Server API Key ID** for XSOAR 8.
+- Updated the **file-management-delete-file** command to support delete file in XSOAR 8.
+
+- Updated the Docker image to: *demisto/python3:3.10.13.87159*.
diff --git a/Packs/XSOARFileManagement/pack_metadata.json b/Packs/XSOARFileManagement/pack_metadata.json
index bae4301d70c5..8aecf97cba16 100644
--- a/Packs/XSOARFileManagement/pack_metadata.json
+++ b/Packs/XSOARFileManagement/pack_metadata.json
@@ -2,15 +2,19 @@
"name": "XSOAR File Management",
"description": "This pack let user manipulate file inside XSOAR more easily than with the builtin functions.",
"support": "community",
- "currentVersion": "1.0.2",
+ "currentVersion": "1.1.0",
"author": "Pierre",
"url": "",
"email": "",
"created": "2023-02-07T13:03:55Z",
- "categories": ["Utilities"],
+ "categories": [
+ "Utilities"
+ ],
"tags": [],
"useCases": [],
- "keywords": ["File"],
+ "keywords": [
+ "File"
+ ],
"marketplaces": [
"xsoar",
"marketplacev2"
@@ -18,4 +22,4 @@
"githubUser": [
"Winultimatum"
]
-}
+}
\ No newline at end of file
From b05bbd3fe6232578d5e975b3590a837fa1a0ebca Mon Sep 17 00:00:00 2001
From: Karina Fishman <147307864+karinafishman@users.noreply.github.com>
Date: Sun, 25 Feb 2024 14:32:40 +0200
Subject: [PATCH 077/272] Convert file hash to corresponding hash improvement
(#33001)
* added another method to search for indicators
* release notes updated
* added length check for hashes
* RM update
* Update Packs/CommonPlaybooks/ReleaseNotes/2_6_14.md
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
* Update Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes.yml
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---------
Co-authored-by: ShirleyDenkberg <62508050+ShirleyDenkberg@users.noreply.github.com>
---
...vert_file_hash_to_corresponding_hashes.yml | 531 ++++++++++++++++--
...ile_hash_to_corresponding_hashes_README.md | 43 +-
Packs/CommonPlaybooks/ReleaseNotes/2_6_14.md | 6 +
...vert_file_hash_to_corresponding_hashes.png | Bin 0 -> 194615 bytes
Packs/CommonPlaybooks/pack_metadata.json | 2 +-
5 files changed, 509 insertions(+), 73 deletions(-)
create mode 100644 Packs/CommonPlaybooks/ReleaseNotes/2_6_14.md
create mode 100644 Packs/CommonPlaybooks/doc_files/Convert_file_hash_to_corresponding_hashes.png
diff --git a/Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes.yml b/Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes.yml
index d17009150973..efde48091457 100644
--- a/Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes.yml
+++ b/Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes.yml
@@ -35,6 +35,10 @@ tasks:
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"2":
id: "2"
taskid: d0c581d2-789c-4a12-8940-37f17a47b4f6
@@ -51,13 +55,17 @@ tasks:
view: |-
{
"position": {
- "x": 520,
- "y": 970
+ "x": 530,
+ "y": 950
}
}
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"4":
id: "4"
taskid: b797fdc7-1704-442a-8605-ee06bfb0bf54
@@ -74,7 +82,7 @@ tasks:
'#default#':
- "2"
"yes":
- - "18"
+ - "44"
separatecontext: false
conditions:
- label: "yes"
@@ -88,13 +96,17 @@ tasks:
view: |-
{
"position": {
- "x": 970,
- "y": 240
+ "x": 1080,
+ "y": 200
}
}
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"9":
id: "9"
taskid: f7142eb2-9483-4546-8d07-a828d636d0ad
@@ -111,7 +123,7 @@ tasks:
'#default#':
- "2"
"yes":
- - "16"
+ - "46"
separatecontext: false
conditions:
- label: "yes"
@@ -125,13 +137,17 @@ tasks:
view: |-
{
"position": {
- "x": -250,
- "y": 240
+ "x": -40,
+ "y": 190
}
}
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"10":
id: "10"
taskid: eff5d9b7-ea36-4310-8650-5e26fa38209e
@@ -148,7 +164,7 @@ tasks:
'#default#':
- "2"
"yes":
- - "15"
+ - "45"
separatecontext: false
conditions:
- label: "yes"
@@ -159,16 +175,23 @@ tasks:
complex:
root: inputs.SHA1
iscontext: true
+ right:
+ value: {}
+ continueonerrortype: ""
view: |-
{
"position": {
"x": 520,
- "y": 230
+ "y": 190
}
}
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"15":
id: "15"
taskid: 65ff1c51-6bc1-4171-8bde-eb6ecb862f4e
@@ -186,32 +209,26 @@ tasks:
'#none#':
- "2"
scriptarguments:
- confidenceThreshold: {}
file:
complex:
root: inputs.SHA1
- include_inactive: {}
- long: {}
- md5: {}
- owners: {}
- ratingThreshold: {}
- retries: {}
- sha256: {}
- threshold: {}
- wait: {}
reputationcalc: 2
continueonerror: true
separatecontext: false
view: |-
{
"position": {
- "x": 310,
- "y": 410
+ "x": 300,
+ "y": 750
}
}
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"16":
id: "16"
taskid: 9e3c8b51-dbc6-464a-8af7-f5d43b663bd4
@@ -233,28 +250,23 @@ tasks:
file:
complex:
root: inputs.MD5
- include_inactive: {}
- long: {}
- md5: {}
- owners: {}
- ratingThreshold: {}
- retries: {}
- sha256: {}
- threshold: {}
- wait: {}
reputationcalc: 2
continueonerror: true
separatecontext: false
view: |-
{
"position": {
- "x": -490,
- "y": 410
+ "x": -550,
+ "y": 750
}
}
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"18":
id: "18"
taskid: 29ef7703-de75-4ff3-844c-a852e333bdbe
@@ -276,28 +288,23 @@ tasks:
file:
complex:
root: inputs.SHA256
- include_inactive: {}
- long: {}
- md5: {}
- owners: {}
- ratingThreshold: {}
- retries: {}
- sha256: {}
- threshold: {}
- wait: {}
reputationcalc: 2
continueonerror: true
separatecontext: false
view: |-
{
"position": {
- "x": 1230,
- "y": 410
+ "x": 1180,
+ "y": 750
}
}
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"35":
id: "35"
taskid: fdfd1cd9-3095-455b-8481-072b140ee5de
@@ -317,13 +324,17 @@ tasks:
view: |-
{
"position": {
- "x": -250,
- "y": 115
+ "x": -40,
+ "y": 60
}
}
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"36":
id: "36"
taskid: a75bc19c-d514-44ab-885d-fb6664dd0b29
@@ -344,12 +355,16 @@ tasks:
{
"position": {
"x": 520,
- "y": 115
+ "y": 60
}
}
note: false
timertriggers: []
ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
"37":
id: "37"
taskid: a2d56e80-d468-46a0-891d-3792a6bf0bd9
@@ -369,25 +384,425 @@ tasks:
view: |-
{
"position": {
- "x": 970,
- "y": 110
+ "x": 1080,
+ "y": 60
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "39":
+ id: "39"
+ taskid: 336d7e69-334b-490c-81c4-4b48788a56be
+ type: condition
+ task:
+ id: 336d7e69-334b-490c-81c4-4b48788a56be
+ version: -1
+ name: Have the hashes been retrieved?
+ type: condition
+ iscommand: false
+ brand: ""
+ description: ""
+ nexttasks:
+ '#default#':
+ - "18"
+ "yes":
+ - "40"
+ separatecontext: false
+ conditions:
+ - label: "yes"
+ condition:
+ - - operator: isNotEmpty
+ left:
+ value:
+ simple: foundIndicators.value
+ iscontext: true
+ right:
+ value: {}
+ - - operator: stringHasLength
+ left:
+ value:
+ complex:
+ root: foundIndicators
+ accessor: value
+ iscontext: true
+ right:
+ value:
+ simple: "64"
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 1350,
+ "y": 540
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "40":
+ id: "40"
+ taskid: 4cbe3c2a-dc3d-46fc-8b6a-b589accfdba3
+ type: regular
+ task:
+ id: 4cbe3c2a-dc3d-46fc-8b6a-b589accfdba3
+ version: -1
+ name: Enrich indicators
+ description: commands.local.cmd.enrich.indicators
+ script: Builtin|||enrichIndicators
+ type: regular
+ iscommand: true
+ brand: Builtin
+ nexttasks:
+ '#none#':
+ - "2"
+ scriptarguments:
+ indicatorsValues:
+ complex:
+ root: foundIndicators
+ accessor: value
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 1600,
+ "y": 750
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "44":
+ id: "44"
+ taskid: b27dc11a-1b9f-4056-8288-776eaa57bd63
+ type: regular
+ task:
+ id: b27dc11a-1b9f-4056-8288-776eaa57bd63
+ version: -1
+ name: Search indicators
+ description: |-
+ Searches Cortex XSOAR indicators.
+
+ Searches for Cortex XSOAR indicators and returns the id, indicator_type, value, and score/verdict.
+
+ You can add additional fields from the indicators using the add_field_to_context argument.
+ scriptName: SearchIndicator
+ type: regular
+ iscommand: false
+ brand: ""
+ nexttasks:
+ '#none#':
+ - "39"
+ scriptarguments:
+ query:
+ simple: value:${inputs.SHA256}
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 1350,
+ "y": 370
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "45":
+ id: "45"
+ taskid: 1b49a035-86f4-4e1d-81ac-add593725d88
+ type: regular
+ task:
+ id: 1b49a035-86f4-4e1d-81ac-add593725d88
+ version: -1
+ name: Search indicators
+ description: |-
+ Searches Cortex XSOAR indicators.
+
+ Searches for Cortex XSOAR Indicators and returns the id, indicator_type, value, and score/verdict.
+
+ You can add additional fields from the indicators using the add_field_to_context argument.
+ scriptName: SearchIndicator
+ type: regular
+ iscommand: false
+ brand: ""
+ nexttasks:
+ '#none#':
+ - "47"
+ scriptarguments:
+ query:
+ simple: value:${inputs.SHA1}
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 520,
+ "y": 370
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "46":
+ id: "46"
+ taskid: f9974076-074f-4bf4-82a5-0c804fb7875b
+ type: regular
+ task:
+ id: f9974076-074f-4bf4-82a5-0c804fb7875b
+ version: -1
+ name: Search indicators
+ description: |-
+ Searches Cortex XSOAR indicators.
+
+ Searches for Cortex XSOAR Indicators and returns the id, indicator_type, value, and score/verdict.
+
+ You can add additional fields from the indicators using the add_field_to_context argument.
+ scriptName: SearchIndicator
+ type: regular
+ iscommand: false
+ brand: ""
+ nexttasks:
+ '#none#':
+ - "48"
+ scriptarguments:
+ query:
+ simple: value:${inputs.MD5}
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": -330,
+ "y": 370
}
}
note: false
timertriggers: []
ignoreworker: false
-system: true
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "47":
+ id: "47"
+ taskid: 0161e3d5-ca7c-4e0e-86d4-f767f1c7b64c
+ type: condition
+ task:
+ id: 0161e3d5-ca7c-4e0e-86d4-f767f1c7b64c
+ version: -1
+ name: Have the hashes been retrieved?
+ type: condition
+ iscommand: false
+ brand: ""
+ description: ""
+ nexttasks:
+ '#default#':
+ - "15"
+ "yes":
+ - "49"
+ separatecontext: false
+ conditions:
+ - label: "yes"
+ condition:
+ - - operator: isNotEmpty
+ left:
+ value:
+ simple: foundIndicators.value
+ iscontext: true
+ right:
+ value: {}
+ - - operator: stringHasLength
+ left:
+ value:
+ complex:
+ root: foundIndicators
+ accessor: value
+ iscontext: true
+ right:
+ value:
+ simple: "40"
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 520,
+ "y": 540
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "48":
+ id: "48"
+ taskid: 9fb9988f-d614-4a30-8eb9-09c8a05ad461
+ type: condition
+ task:
+ id: 9fb9988f-d614-4a30-8eb9-09c8a05ad461
+ version: -1
+ name: Have the hashes been retrieved?
+ type: condition
+ iscommand: false
+ brand: ""
+ description: ""
+ nexttasks:
+ '#default#':
+ - "16"
+ "yes":
+ - "50"
+ separatecontext: false
+ conditions:
+ - label: "yes"
+ condition:
+ - - operator: isNotEmpty
+ left:
+ value:
+ simple: foundIndicators.value
+ iscontext: true
+ right:
+ value: {}
+ - - operator: stringHasLength
+ left:
+ value:
+ complex:
+ root: foundIndicators
+ accessor: value
+ iscontext: true
+ right:
+ value:
+ simple: "32"
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": -330,
+ "y": 540
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "49":
+ id: "49"
+ taskid: 620476dc-83d3-40fe-8d2f-8f978fcdfa23
+ type: regular
+ task:
+ id: 620476dc-83d3-40fe-8d2f-8f978fcdfa23
+ version: -1
+ name: Enrich indicators
+ description: commands.local.cmd.enrich.indicators
+ script: Builtin|||enrichIndicators
+ type: regular
+ iscommand: true
+ brand: Builtin
+ nexttasks:
+ '#none#':
+ - "2"
+ scriptarguments:
+ indicatorsValues:
+ complex:
+ root: foundIndicators
+ accessor: value
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": 750,
+ "y": 750
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
+ "50":
+ id: "50"
+ taskid: e4213b2e-29ba-40d3-8ae3-6deec5436549
+ type: regular
+ task:
+ id: e4213b2e-29ba-40d3-8ae3-6deec5436549
+ version: -1
+ name: Enrich indicators
+ description: commands.local.cmd.enrich.indicators
+ script: Builtin|||enrichIndicators
+ type: regular
+ iscommand: true
+ brand: Builtin
+ nexttasks:
+ '#none#':
+ - "2"
+ scriptarguments:
+ indicatorsValues:
+ complex:
+ root: foundIndicators
+ accessor: value
+ separatecontext: false
+ continueonerrortype: ""
+ view: |-
+ {
+ "position": {
+ "x": -120,
+ "y": 750
+ }
+ }
+ note: false
+ timertriggers: []
+ ignoreworker: false
+ skipunavailable: false
+ quietmode: 0
+ isoversize: false
+ isautoswitchedtoquietmode: false
view: |-
{
"linkLabelsPosition": {
- "10_15_yes": 0.55,
- "9_16_yes": 0.48
+ "10_2_#default#": 0.39,
+ "10_45_yes": 0.46,
+ "47_15_#default#": 0.44,
+ "47_49_yes": 0.41,
+ "48_16_#default#": 0.57,
+ "48_50_yes": 0.61,
+ "4_2_#default#": 0.15,
+ "9_2_#default#": 0.19,
+ "9_46_yes": 0.51
},
"paper": {
"dimensions": {
- "height": 1135,
- "width": 2100,
- "x": -490,
+ "height": 1115,
+ "width": 2530,
+ "x": -550,
"y": -100
}
}
@@ -400,6 +815,7 @@ inputs:
accessor: SHA256
required: false
description: The SHA256 hash on which to search.
+ playbookInputQuery:
- key: SHA1
value:
complex:
@@ -407,6 +823,7 @@ inputs:
accessor: SHA1
required: false
description: The SHA1 hash on which to search.
+ playbookInputQuery:
- key: MD5
value:
complex:
@@ -414,6 +831,7 @@ inputs:
accessor: MD5
required: false
description: The MD5 hash on which to search.
+ playbookInputQuery:
outputs:
- contextPath: File.SHA256
description: Output for detected SHA256 hash.
@@ -424,6 +842,7 @@ outputs:
- contextPath: File.MD5
description: Output for detected MD5 hash.
type: string
-
+- contextPath: Indicators.Value
+ description: Output for detected hashes.
tests:
- Test Convert file hash to corresponding hashes
diff --git a/Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes_README.md b/Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes_README.md
index cdb0d2320e98..5eaeb105ee68 100644
--- a/Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes_README.md
+++ b/Packs/CommonPlaybooks/Playbooks/playbook-Convert_file_hash_to_corresponding_hashes_README.md
@@ -1,41 +1,52 @@
-Gets all of the corresponding hashes for a file even if there is only one hash type available.
-For example, if we have only the SHA256 hash, the playbook will get the SHA1 hash and MD5 hash as long as the
+The playbook enables you to get all of the corresponding file hashes for a file even if there is only one hash type available.
+For example, if we have only the SHA256 hash, the playbook will get the SHA1 and MD5 hashes as long as the
original searched hash is recognized by any our the threat intelligence integrations.
## Dependencies
+
This playbook uses the following sub-playbooks, integrations, and scripts.
-## Sub-playbooks
+### Sub-playbooks
+
This playbook does not use any sub-playbooks.
-## Integrations
+### Integrations
+
This playbook does not use any integrations.
-## Scripts
-This playbook does not use any scripts.
+### Scripts
+
+* SearchIndicator
+
+### Commands
-## Commands
+* enrichIndicators
* file
## Playbook Inputs
+
---
-| **Name** | **Description** | **Default Value** | **Source** | **Required** |
-| --- | --- | --- | --- | --- |
-| SHA256 | The SHA256 hash on which to search. | SHA256 | File | Optional |
-| SHA1 | The SHA1 hash on which to search. | SHA1 | File | Optional |
-| MD5 | The MD5 hash on which to search. | MD5 | File | Optional |
+| **Name** | **Description** | **Default Value** | **Required** |
+| --- | --- | --- | --- |
+| SHA256 | The SHA256 hash on which to search. | File.SHA256 | Optional |
+| SHA1 | The SHA1 hash on which to search. | File.SHA1 | Optional |
+| MD5 | The MD5 hash on which to search. | File.MD5 | Optional |
## Playbook Outputs
+
---
| **Path** | **Description** | **Type** |
| --- | --- | --- |
-| File.SHA256 | The output for detected SHA256 hash of the file. | string |
-| File.SHA1 | The output for detected SHA1 hash of the file. | string |
-| File.MD5 | The output for detected MD5 hash of the file. | string |
+| File.SHA256 | Output for detected SHA256 hash. | string |
+| File.SHA1 | Output for detected SHA1 hash. | string |
+| File.MD5 | Output for detected MD5 hash. | string |
+| Indicators.Value | Output for detected hashes. | unknown |
## Playbook Image
+
---
-
+
+
diff --git a/Packs/CommonPlaybooks/ReleaseNotes/2_6_14.md b/Packs/CommonPlaybooks/ReleaseNotes/2_6_14.md
new file mode 100644
index 000000000000..8de82ff6685c
--- /dev/null
+++ b/Packs/CommonPlaybooks/ReleaseNotes/2_6_14.md
@@ -0,0 +1,6 @@
+
+#### Playbooks
+
+##### Convert file hash to corresponding hashes
+
+Added local search for hashes in Cortex XSOAR before the enrichment.
diff --git a/Packs/CommonPlaybooks/doc_files/Convert_file_hash_to_corresponding_hashes.png b/Packs/CommonPlaybooks/doc_files/Convert_file_hash_to_corresponding_hashes.png
new file mode 100644
index 0000000000000000000000000000000000000000..a0c0a06d6e546c62d2acccfb4749a541f5fa1073
GIT binary patch
literal 194615
zcmb4rcOcc@|9^=R4P}lKL>%5-lxyR$2SE|bLM=4HI?Ay2R=of+S^k9FVe8`ti^AyYkv0wEfXd>iu3@~|rtIvGYC
z8RkP4hF^Rs4>BqW>?esUA-hfz+)Z_|G+)WG7?zmULVw^8Cx7FIo0>|#i4K4p6%OD
zLP}1>D)Ybov2a^2gcTCit$pKv{pp|OF7Ll4L5cW3zajjeXRMgpeffd^=O@SqG!OjW
zs0SqVog*d1DU;O4|DT_bp{hTSsa;<2@U^xlK96?T&!O03Y>{2h`xxwWM$OH
zyD7E&=5eHyB@|lgrX;VWrDggegb9e#iA_~qotn!Ya$^Jr!L@5{X
z))6sORAt=WmrtD|QUiWfl6*a#>Grg=wCM(&HJAEG$)5e_?&YR@EEaqB{(T|UZ#KF>
zb7-<;*2KS{P-2XRZhgFDa}$%3nR<{lAy;HfOiZO}B-V@)Rdx_;bl3Xf(LmCNpNmH9
z{+NpMC}LwDWKF_jO0BY>r@+A^YNoeX+J4&nm2X#=L04K&dZwxSRAgV$;nsvYo3FZI5_!JV$Od4e9_QI2j+7I!f1H&xPOJfqJaKXNJx{&#nX&0<&BMv
zeNG8ppd5(TZJzNzG7?`&F%-dC)O`4l&TiWR;yDfA%l8Zhnq72LvGNCytajCnTzBAl
z7F_BuDLmtSe=@hc(^uTECy1%Bv#n7wu&Rn)tndDqr*Ob|8%q*W?;Fv{gAKiJA|m)U
zbTl=zXq!3wd_SmHR-~8?8m`3&XdY^$sW5x;wBKquy4E?>D0O-l&Co)t-
z#)!CiQ4=igvSzUx1-dnkokXFe>Cug#Y
z6^Nl^9c@jNy*v^X{RBrh3*&Cjjn(&_JM14w2GrUPqzXPlRV#D#gj^8d`
z97u6|XV^I2Y}nRP!4n{CKlPKxC%BhM#RR>d^SKr=?+;vL^%9OoTPPDL@sVs9-hbLV
zIzD*J=2-SJAD2wO!0cuNHSfyjn0%(8C2jNR<@hS#IVUATo7K|g+jo)C1yk##=Sc$A
z17$n`!8s{P`sjr>&*7zT-bAC
z9_N7=Q$DKp0ME;EHslnGiiwL4bbAO6yv-ab^Evg-pgYf6lYy_DNrl0ZoN}m<$On`h
zrX(MT;Qv5L{2~LY?;f*{9zBXlO5zGab}%eUWu1+Dlzx{UZNM2VaFSJZjwF8?o>(7A
zL(dyZYiq(xG3a|*=neyNDB1G)?w3R_0M~m5nedn>c2q(7zAMA)Q#)yLrM_H=)XKc{
z*=#Zfg-V<9-3L@Jnu^p$A1&Ig?8!(UT~&2Q2ggHCEDk*~QXECjm4m;m?_Y0Qc);qe(5X{kUp|niQRd!*I%hv+
z@v3v}O<|$$JYnC_`$*LokorbY^xWH30r$GV5GhxumbSK=Fc|D-OwK+EBl3SON05n(
zKM+0L!QE10Rb3!i)oPmlna*ypwi=6D$ygL{F_LYpuO&RKYC)nC!PJN<7OfL8Rzpu1
z&u6kiWMyAmdRh%-3*pKn=P%a#yU9jyITK{2^sC?n(9HY5o1*&bz=X=
z6ENu+d>!7E1AT3YnX{6}bxO8?$7|c!vdcvCkUk0xGg!*1fMet54VR`mG&Rs!a?tzt
z?=RD38}HYDOU$ji(T6&|+j~-yJSU{n#5?TWQDHp$h9|P4{uFEZy`Gcas<+-^&6EIC{{GRmmo(bj&r45dh=A#@q$|5E4^y$-#GwraO|>39GH6av!Y#5$P*t~EWM6_h@=<1T$V8KpH7#XjCi?hJ>RLPH
zNJ0$_4Z(l!-+zxaRrrEQAo91~_hqP%54laccWXp+4VfAhGBZ=KE6Bdw`zQ`6j5!f;
z*I29bvMzms$}^eq!*N*C^e#|lZ~hK$#C{>p{_6&w);)PQd}
z-lvGHh&AA_9SmlC4Sh)~r|gA4(u>i3$?9Hv8?6hKW!=Kz#>Ng>kWeuM+<9>SK^d1I
zM@3zND{dpL@W7nUV9ym{PbQ_>bVH4KobvLf6h%##5Z6*JvzM=y!y@h&FT3g)l6_nz;;Yt$%$+lW1MzweqqU
zF5hiaIj}OV!g4ymoRDKbjOhXdcW<)p!*n=Oj(ua@Sn=w}o}P@lZj)eNy3S;#YLObHRTgb-4t
zuE?wHCuZR84&e>o!WI9;{$I*E_5uVFmIm$XL|+_9mErYjZ)`ll<>fG_!s5#jsUv;v
z8oHyova)xh|0o|xN4B$W_xjk}%8v+zj5OnXS*n>avr%1XeBCExvgpWwlhu!^m3B*v
zeTyw!q}V0=LLu^1VpJDZ6uwl&)BfYJ*=91_L581L$~&xNz?vf&kWS;>)2t939UY*U
z6#a(>Xz%48@g#B#@qk**pq@A)KVnS@qF!gHeQ%L#x@mL5N~!O1SpwEMHpgu!T7`$c
ztN>e-I9OB}`MRow&2nf~WIk)$x`QmSyor`^P*8Wx)DFf}Q*pt|Vc}$ifaRlm56}%K
zW@NXpoevB3oi|vK$&hBuW@S&C!$e$qx?wx!iFkv+*rYx`3#XTGNN1!_3kh^R%y8i6
zT3-KWL4yjPQvw#J4v;j%hx^&GoR7$i9&sr7qQ{T
zrOgXF-#waOUFi@_jPwSW`UH;pOYsKx=Q5x!6nIXbTtvD-It2mD>N)n9Kdum
zujWKPhr_a4ty>l7E5>aT%Y3*7V~pLkB<5NsR=)DFV5j4jBXiMbJH^EYl7)NMV?+~X
zu$`HF7Hb{f8bu!8*!ZT4W_N>68sfS;Q*l+nmwZ6sWb!ehi{;_zaJ
ze5uLL`*J`(G8vvY1~Q6nl$(tT*F(5<;G;fa}aivThkE8{Xfnfo|O~;MIdJXL?)(a{O)QmY(RW-fKIoyUl38Q2h9gsA|G5hY3ys5luAG-Z=hQ$93hU1&#JmpRH}ACOT!ryS6+YU9EodW*#H
z!^y>C$Ep`-%GS$XVrXLJfrE{oG?-sX5OJMu;o-NhW_mqXAnnR&TMuhr&s1?0&zb(&
ztn>QzU}agN)Lh$2#c?;L1~Wx%d41;-Z%}k^Rw_AE>Krek
zT6hEpd}oxq3S4IW#O+2qrxV(}-XcMo(-2hK%soUA5jA
z%UjrJHozu~4q8fYeVg9*NaY$jI9!TdY9URd(%-^af--q=MC1__pTpJ`YB4=;?X5?;
zO-~z7*;14=O8WH8qxH|dR_))@(&9#E+;tS0r7twmm3BE`YtzDnpe{@6L+`HpkHaU;
zc>OeVoE~(qf6v4%*fI{rWR5=8&#w$l^S#s+Heli)eX3wNr>s;xv3v_Ynrwir7#&1Z
zYLsh$k;t)Aikr6J6JKsgd7yGhm(Q#Hb@`Q$YiLoy
z3uUV&b>sNVuGjsrsJD3LyotAh1M9^iS7k1>-}j|ZjqnJM1^k%1EBmBgFlADFLz}ew;%K_ra?zAq5_@;$)|ls~w9nqs
zs|A+EAMPKIu
zu)H$h>%iRR$g@1P!3v?+kH@(eT&27jj~pFY8TZGJ=zq*bg-)!rtDprVoh%GpMqW$*
zsAIg!GtkW9s%7r#rs7bNhWdP2YL&y%4=TP?(d&-m=%M5Kvi!2xS;=LMQu>Ej-|$3)
zSa1&^Ul?$ho{F^pjIESjNVuh6+EU2xfZl`!ml@MX(y@S~re@+z9k5q7_Mp^mhOL$1
zD3}BD8DV=PmkE{L(+V2q!0O8ls*VrDOH;NN8r+rGDEkcWaGW<>*}?{eJP*pRv$0K3
z@oE{rOje`DpOHDKCy`}jERnsTs#G5$d?`VZfjYOR_{#d`&qnr)b=Ucq%jIaG>vNPU
z^>{Sa0>e_R0riuQdPLo>?ew?}dl{CmpmWZ@t$cclEHh?OPlL{`R+`u42bXnK%_|(1
zMcQhmoxavr{juU0eyuAFXk<+_3|+7h(`;CoHex=NG-*6>rlY$ls1{ow?Z}^?_+)He
zTiu~BQ#tHI>Q+$O0qc6%dZV7x&f@KmKtpm6W_eQHJ-5(Zsf)ms4A7(G7HP`F
zPjW;3*Saj>nmKY4TPtP4C|MU4w|bbSMy|ihgjSD!4vm$WDYUv&cYKV?E2v>TXi^{&Xy50vo+@+bD-|K=c$4yj2PO@w+
z_-dNuZLq@@7zNP0_!Y}y$Da&pB~ytG(kHg&i;LNgof-QsHpP_RGm=hMg?kR?(hhuX
zwJNVNuc9?xGzb(!7yoV9;9C&A7{Yb#n`NCCmD`e8agD{B>vy;of+l%G3T7;eal_WQ
zn0y?fc=hR0yd34@$32_)UibC8ZT-9sEp7M8N2QkPc&36W6%w2hRY&BdHzS^OxJR#d
zw>a{_q@1^O-50;4nybGom3EzhY3{S>s8Yg#rK_$(+&AlmO?sB+{N2}eXR4kpF$A9lo9ZaHevc}i{ua#=4{*VTy8C!CJs
zH|lH?A;YSD!lDIDOg^HtXRp8#oVyn3O(r=#uGC8zKB$Qh6>xK@9C%_m^Ic3k;gYsG
z$M?@w-nZDQe6^e~p{t%6I#k7Zqd%TlIO>ZJ4Y^~7U&lD=PU?4EN<=0`&j9hbfmGsU
z+w38?$q629l=1rX)N;G7qjF9Ki=z$9=M&Pm*XdjJfZw5@iUg=qIx_x}a+qL#y{*#Z
zT4-?8`_0XTv1YTF>}*N8x~R6v{Kzp>6&Vh*USXR-70HTuMIjbN6q*^HfXIxXvnO__
z(Y<680$#yl^;k@S^yIN@v-%=)g?5mNg_1eU`Nsl>Nj{Z9sqEi8s{8|W?`SduovA|W
z*657o6oz>TEjU_s$bIyE&;BnotZOw<#gavKgE~F?BMixK5T`mcytgaOr`~n54ZiZ@
z{u|VI;VO!9&~R&R6Qt_v`h)19ZuP-sw|VcCQRIfiB;8WKgD&IzsN$>T&Ea6(d-V>*
zt8?b!UD7Mb$TED}fgb&mtip)}E?-a!W*(aiY40MlMzccP+6%fRokO=aMBfe8Z}q`&
ztCpBhXls}s&Dpg|P`c5{pm7|>AL}ZxCDprcL}-dkn)MdvI)|{h_L^lv-K6myEJnK3
z`SH#$JA3A<5m(xW7Tt?n<(C#?Tg4sgB1F09__UmVF1EJ5f0J_s-{dgk?ab_UmGVxc
z<3tvGM%N|3U>-6}0@9weI9V-mq;`Q2cz~YEYZ;RZIT5v9!53S&sk+&8x(JI;%*48@
zQ_X~XWDaUcql(w}TcStMJQB+d)X9FQ$`t6sVVyox%=ysx=21S$1hZ3+AiB
z7ga-*y1Me0ifs78JJhL=MMYAeS#ez+UF3x#D%GgQEP;C9>0r`C@m8;dpdQN+TFf;h
zyp`fk6p!NrR426GU%$F6xul))sQ41Zy7766vyK}TAKARx>@-Ms%Y%y@9NN-(VT$X0
zmBo={eNEOWte_Jc6$K+%4@Tn8cAcJALZVpHiYLNXUe~(_U$u}#%W6=(aP7-Q`nhkl
zVKu*x@L{%4Arc?iq*l_Ag-^VboO|yF^Y|R!#0qDoTG<-j(i%=E>1rCiT2Z>%Jjf?K
z-}4h?Sda5U75D01L+gL@EN3ZR?+g)*7bsecJrpy(Wj~9;S7jR3Exf`>Z{eKNW5+$d
z7|q?97T%odhg;NwEHOpYx;EYfcIaetpN)lsR9;G#q`Mkd&0^o%_Z`8YfKZ4uE$FrL
zkMyINQ|SLL?Y=b$x^p-jzIg4cZFwp7Pz@`{FX!@;~jMUoD1l)dcg!u)0
zy#A4vvwZhrpCHE>5W!Wt=%SoQrhaBRxYLCyUF%`@Z&vy$ZUuN3WraZtW2#11G`S-@_LX_uWu(%&>
zne%)$eT7+?NP&2_1FmC!V7b@L*nyv~SPxk^Fty@q#^+PKmKbKxlfZUAWqoa>;%-NXyHh(gAvs3X=dXl2;?^w-
zE*If9od~1g~y5?>v}5^@$Nb_
zNqu-J!ddr9dX_P++@#)jD{p*yY(nhk<|fTEC9OLAY))kcG9Knw9r1d5Jr?KS6MwJ(
zVMV=ResGS*eqYy{YiOFa)dhKX
z!J^p+@l5QMt4rCd)m0CR
zoD?=T>D`+ou~k*xE1&{X$Pt>Bms-T8P-|Ieb+aFM@s7jim5STSB~9VttVJ_C!!%sa
z)Mar*RtpWWTk2kUk*f>)c@+04B~>ciN1zC&p+Yr|tX`+h^L(A1x#{{wZBWZ`
zTgCyFqK(YKyFr`F&fTF)3`{tP8{V`ds5~jzu=A=InPIbix#{}&tHGP{6xj*b7tL)s
zglv(}YLr^f)_q)O$~{!gCm~q`AJplvFIDI8_3d$fWB@XEo-3e_QFOLw7Aqbz+^)mZ
zEJREDZ2;S@d$M;0sk`_vd115Haj@F(TTq1c=z;1C>350s5vMhDGx&>as}J<_7q;uV
zT1XTpi@Gh2%}wQxFCUjq|Lm;LW#^y8G)G;ZQXly)=dI+2e8_5(U`AT7bpE`ma08|$
z8~Iv*zRbCvv91o)uk_*adC%i4%&o1hph?92d2&}d1p3}?v{Yr28p^`N&GLh?tn_7O
z78ZVslkJsT_$I#CSiu<3V$+kre=!MvLNyaR;|z_{`&lWqzR5H6uJp>d85e_Xb3Kb6
zO^5>1Or5x`{k{A5nRA4o(_aa>W`}(|2!XhlEbC5Zp3ICftMh^i%brkh6H@k;_SP~+
zq$uCyqu|o({!-bf^^F!bJ`eAvrOaIXMAE0EG;czQ$rB>JC>Jr;WJ_Nc226aIJsm!d
z3c2EDhsLf2Kkko_-dblg9G!OUaJ4mD=}+}9uPuhht!w_O<3N+h*!GUCG^P=F_#|q^
zfp_k6K|JAhy@uRCSZ%j@)|RrfjJ3w??P0Lv!@Bs1+)Pz<3Oei)v6c_!?q<&RkfM1r
zh_yW$Bq5p58|op`s(NPHanE!pp1|yxQKOB(E}dE2mb0xZ(59LkWi&>LgSR5u)P7!0
z^{|U`igWg1fP|5KQ+smx6uu&v&+E;%$qZ#zP>pKcekpc4Z9DD